Security interception method and device
An interception device and safety technology, applied in the direction of safety devices, electrical components, wireless communication, etc., to achieve the effect of improving safety protection capability and avoiding economic losses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
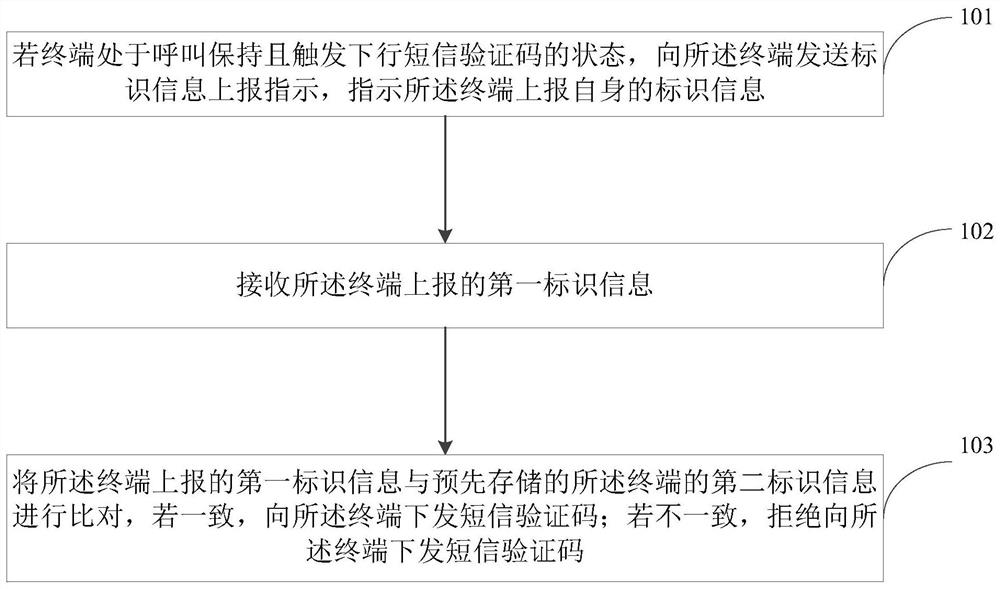
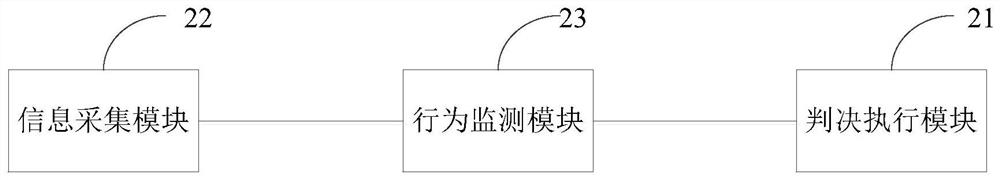
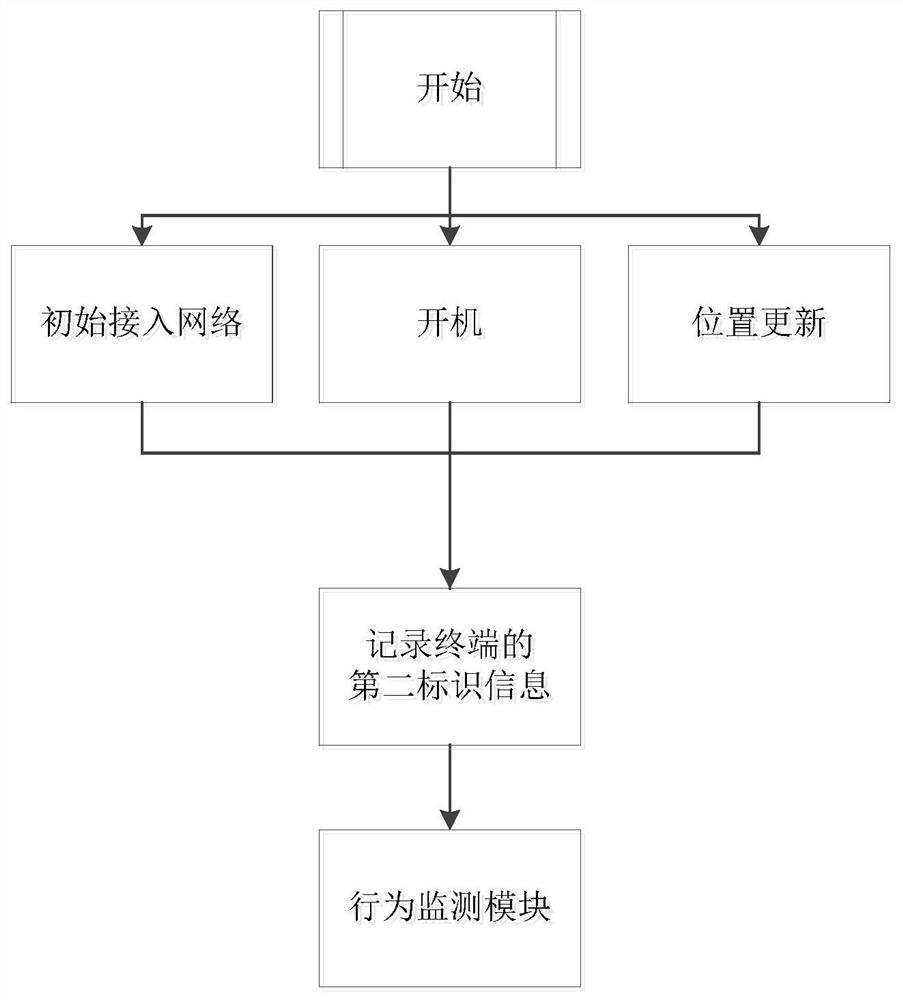
[0042] In order to make the technical problems, technical solutions and advantages to be solved by the embodiments of the present invention clearer, the following will describe in detail with reference to the drawings and specific embodiments.
[0043] The process of hijacking and fraudulent brushing is: B calls the hijacked user A; the hijacked user A has a voice call in, the hijacker A' counterfeit the hijacked user A's response to the called voice process of the network, and the network side is interacting with the called party of A' During the process, authentication (Authentication) and identification (Identification) processes will be executed to confirm whether the response is a real user A. Since the core network system has defects in the processing of authentication and identification processes, the hijacker A' can impersonate the hijacked user A responds to the called voice process of the network, and uses the relevant information in the user card of A' or the relevan...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com