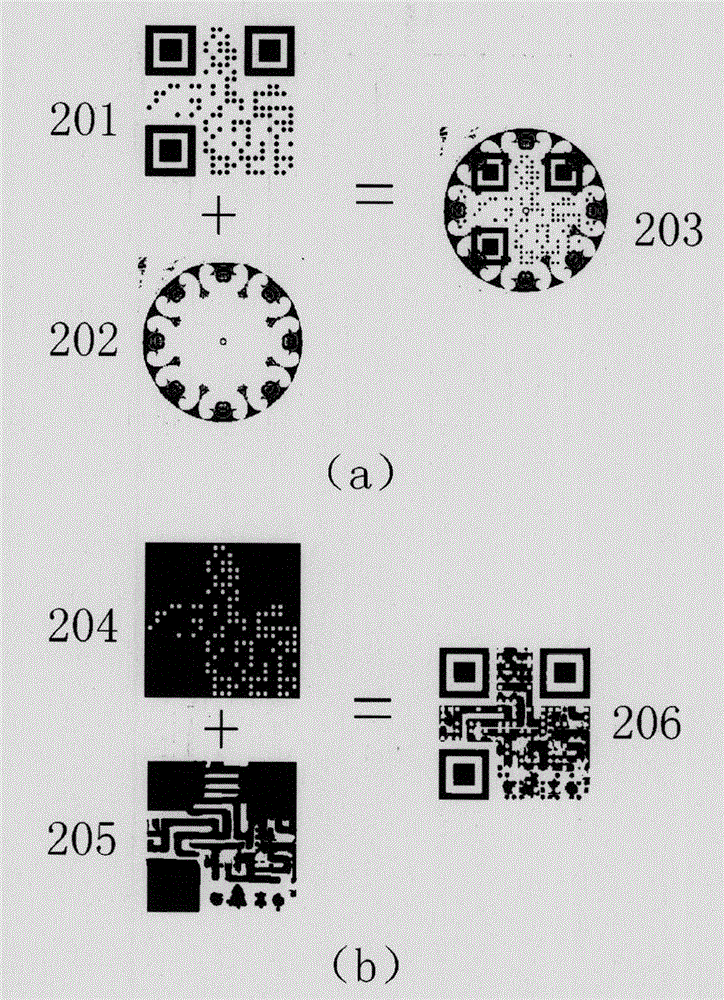
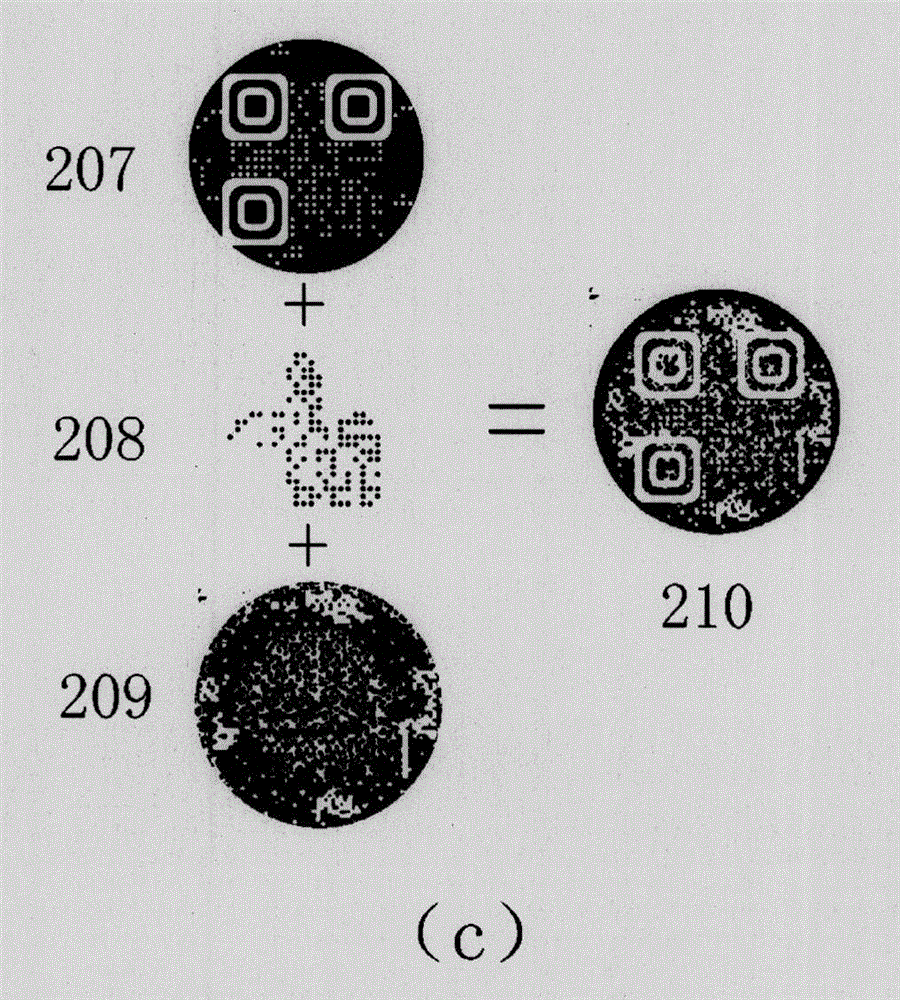
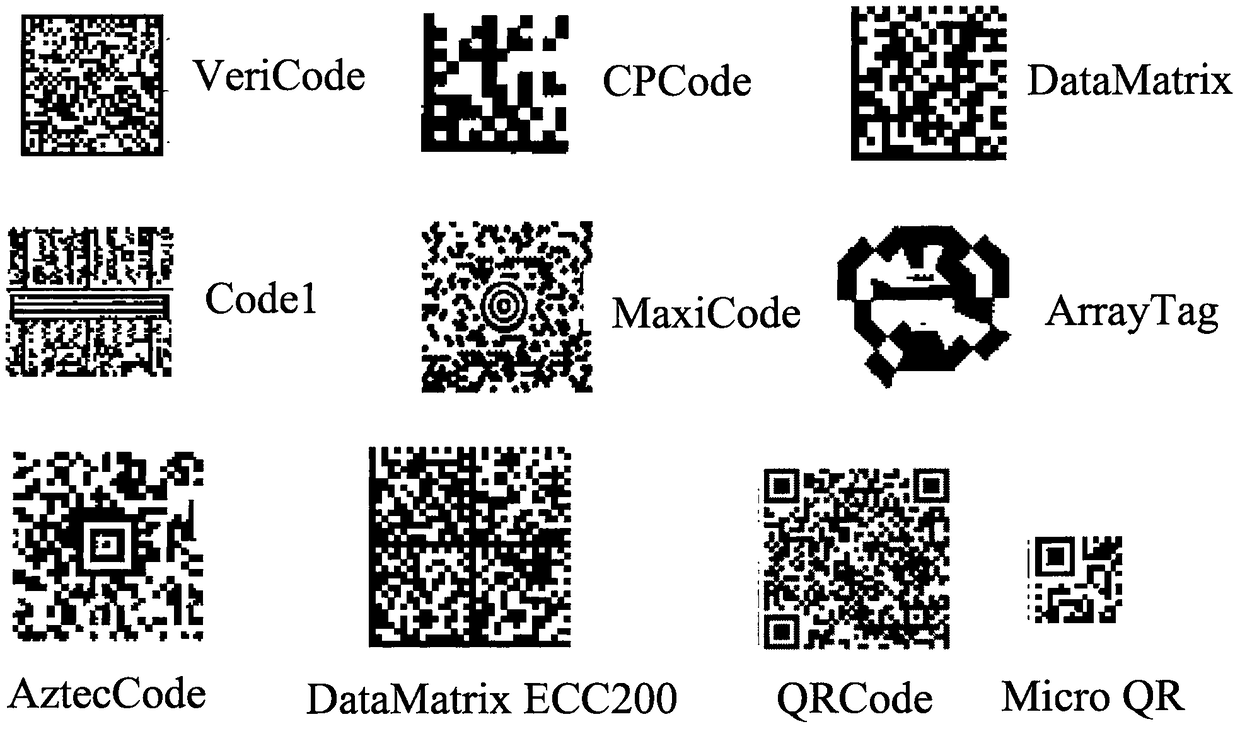
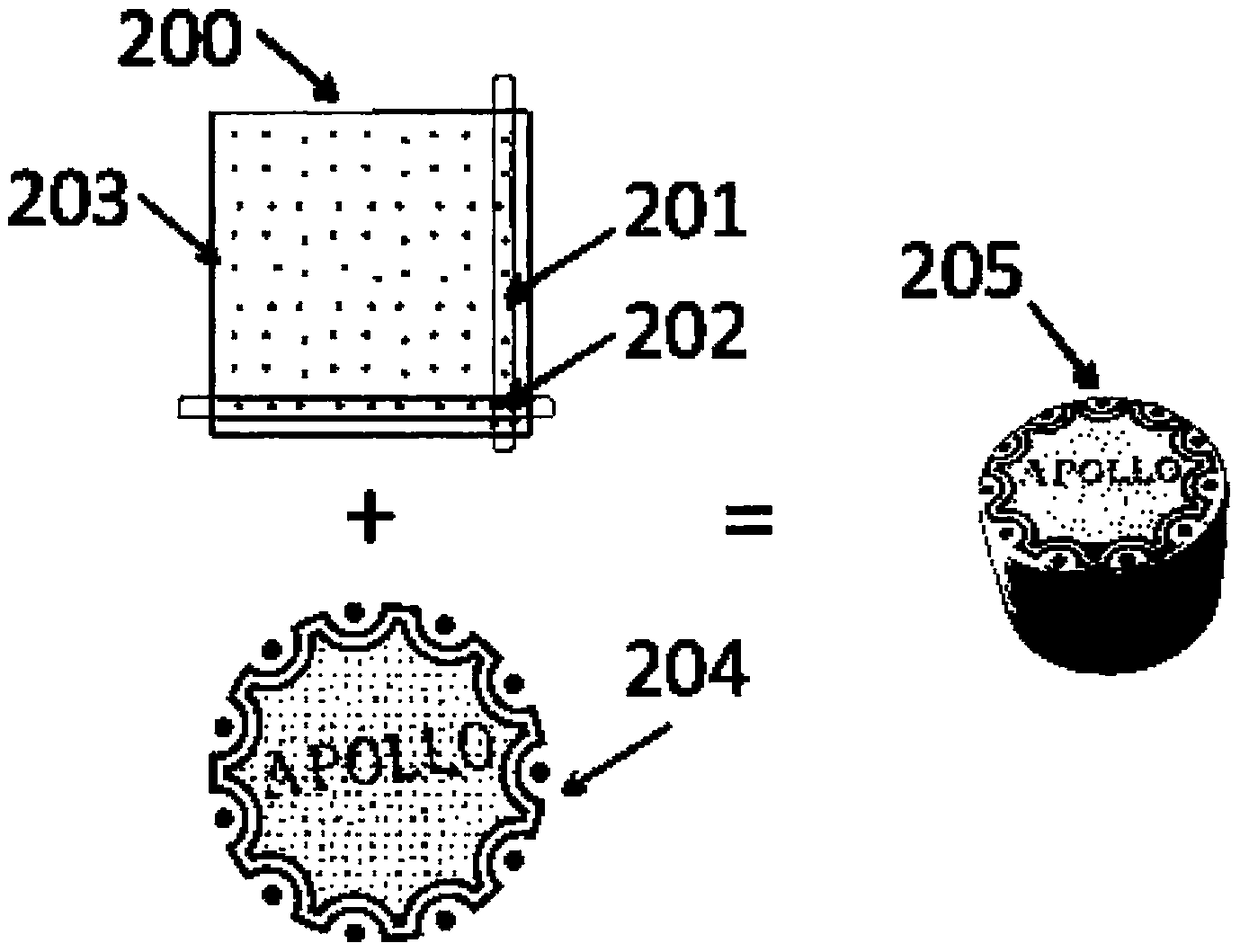
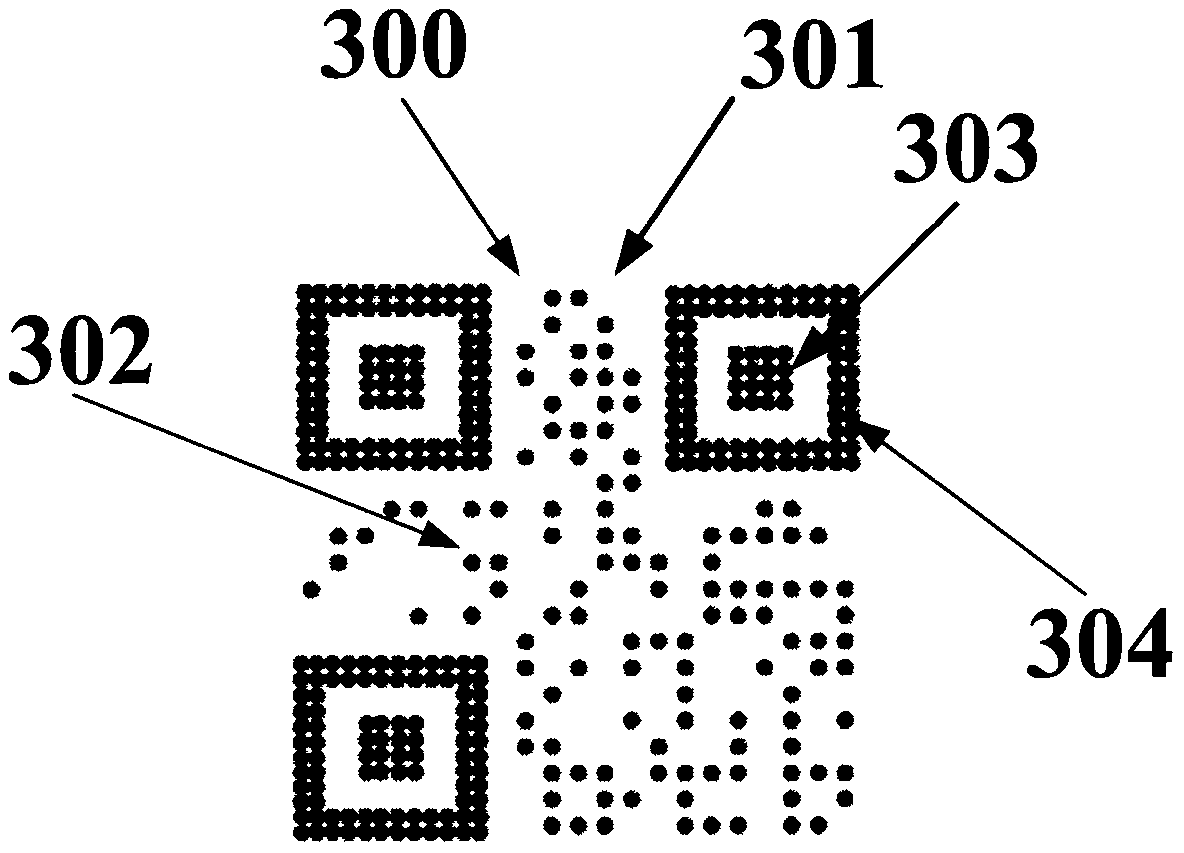
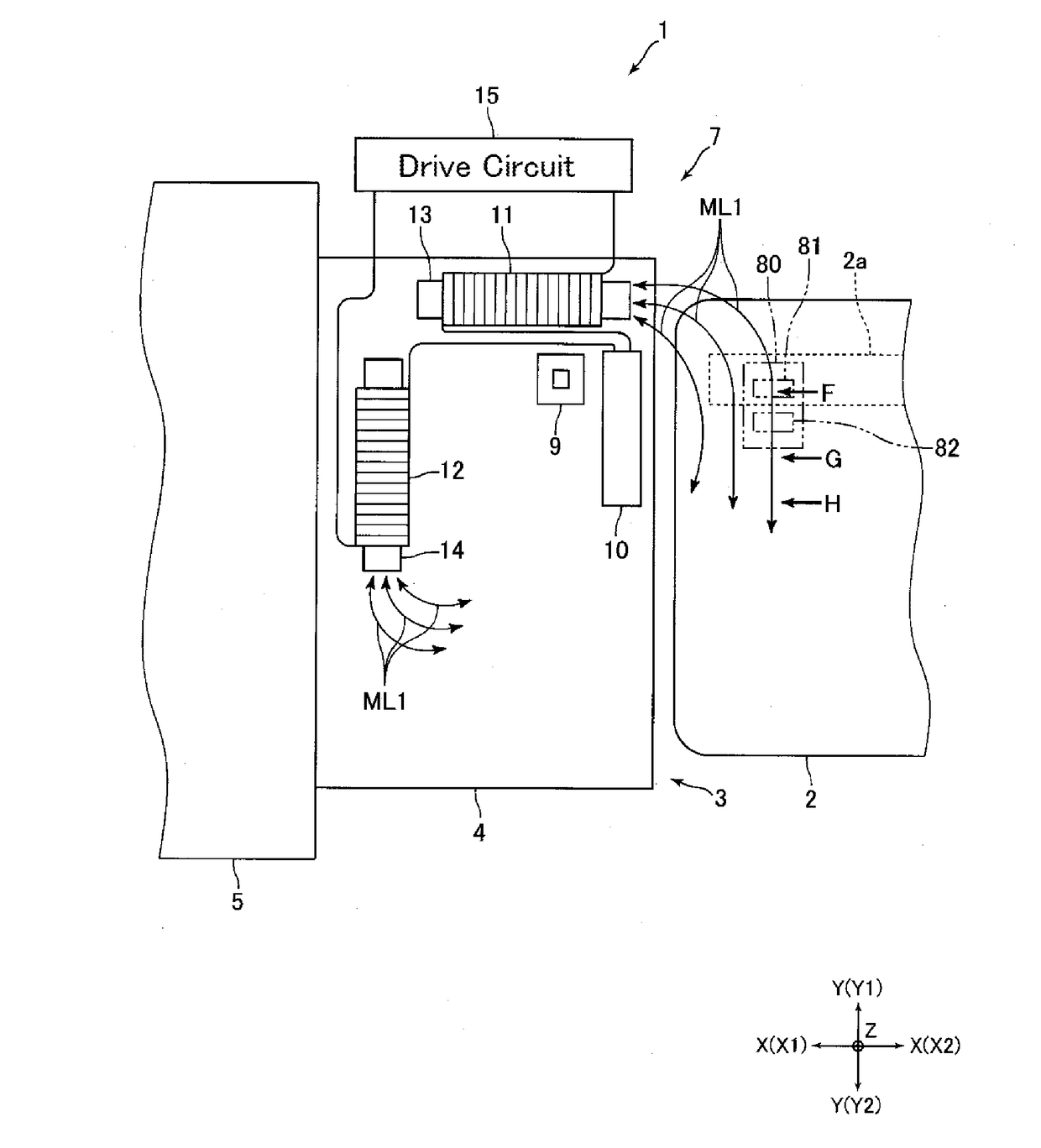
Patents
Literature
30results about How to "Prevent skimming" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
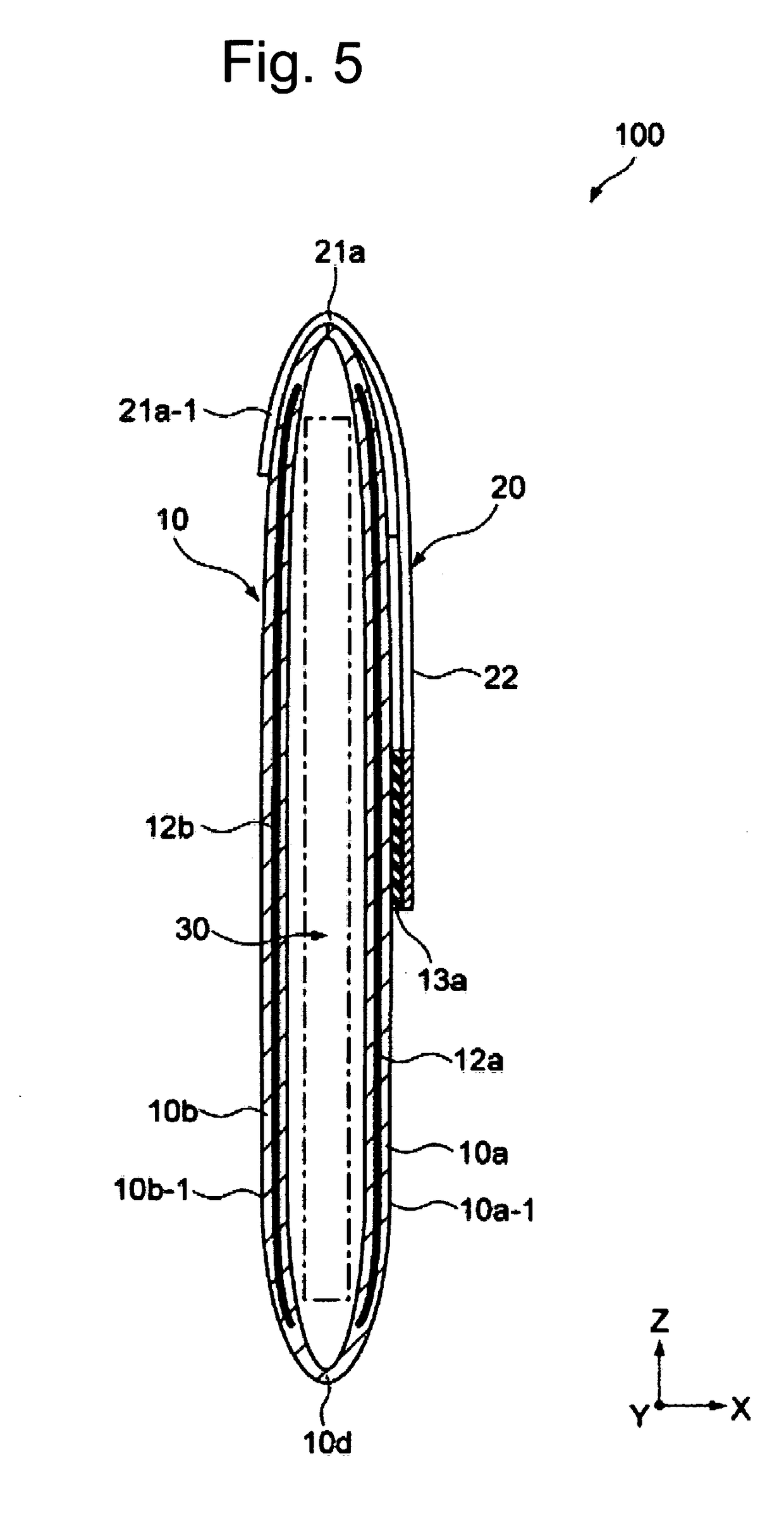
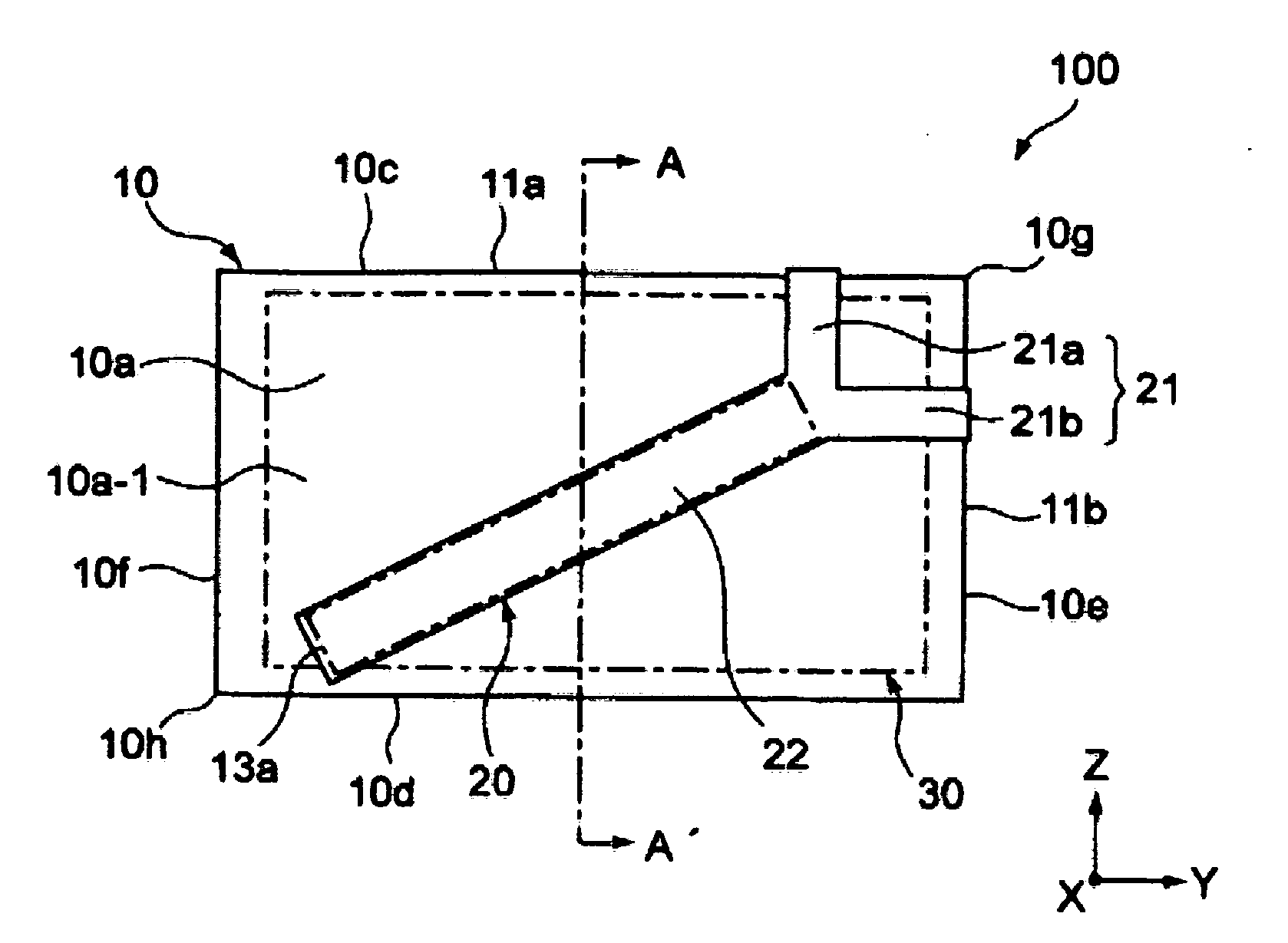
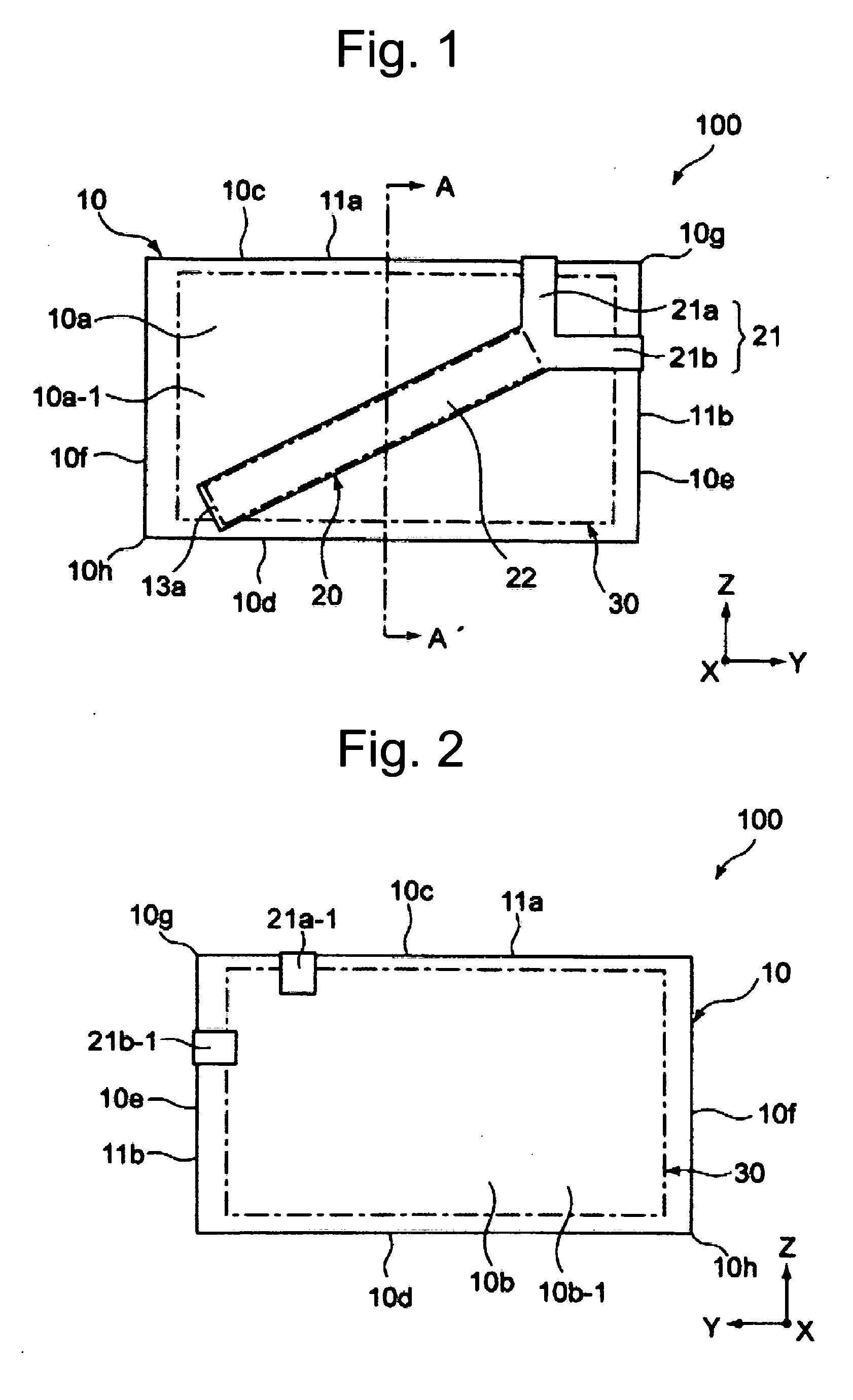
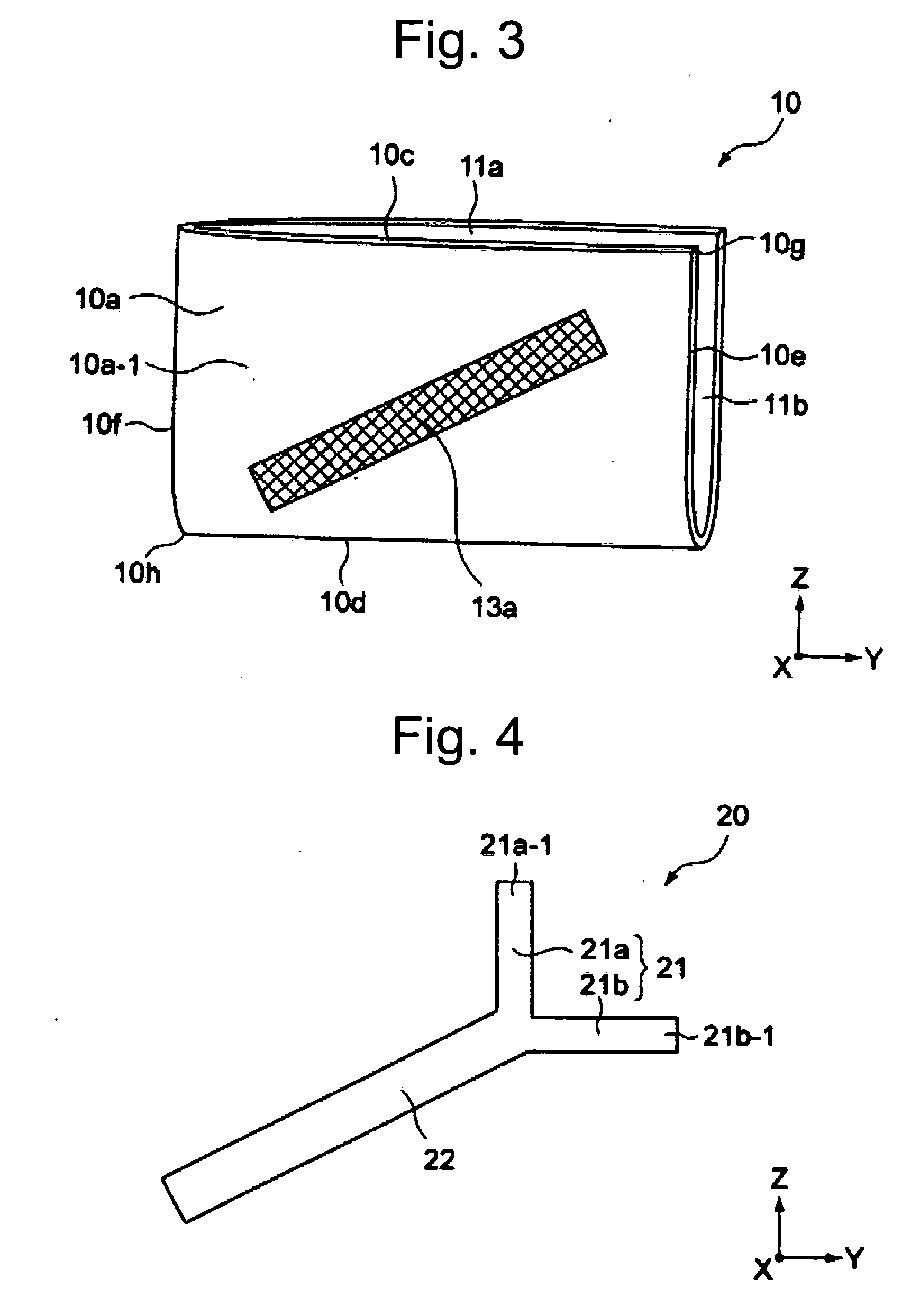
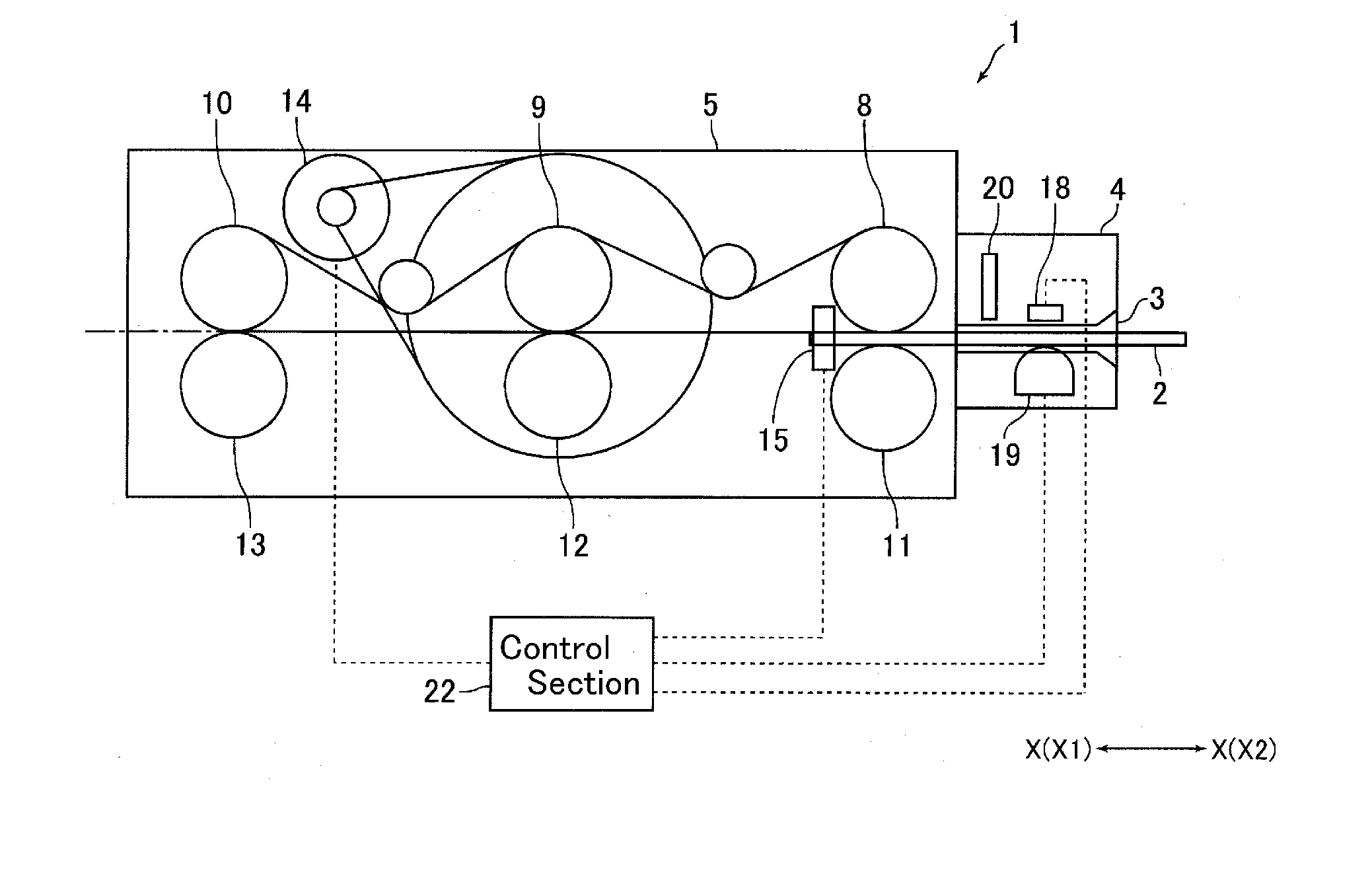
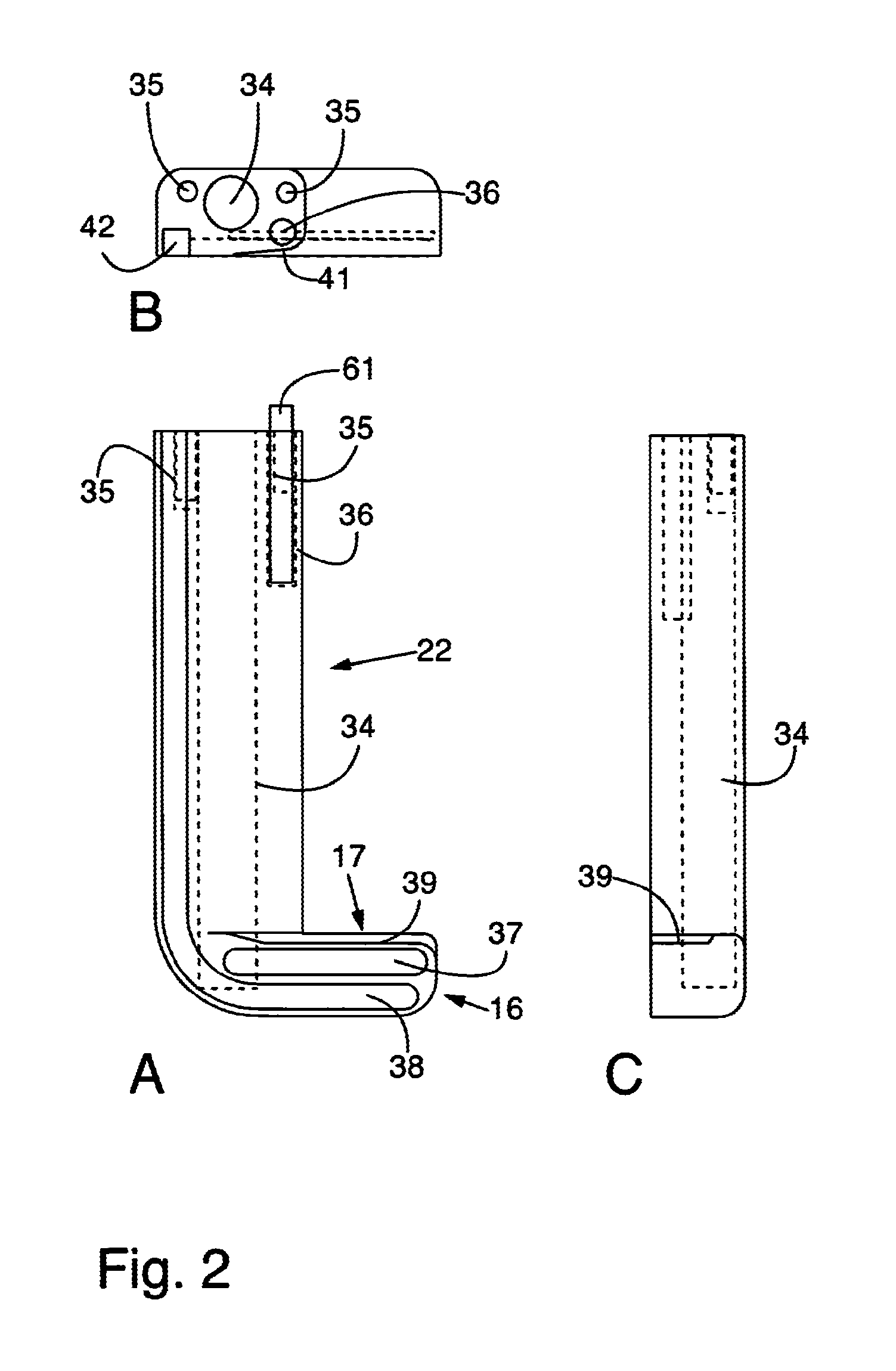
Card reader and writer
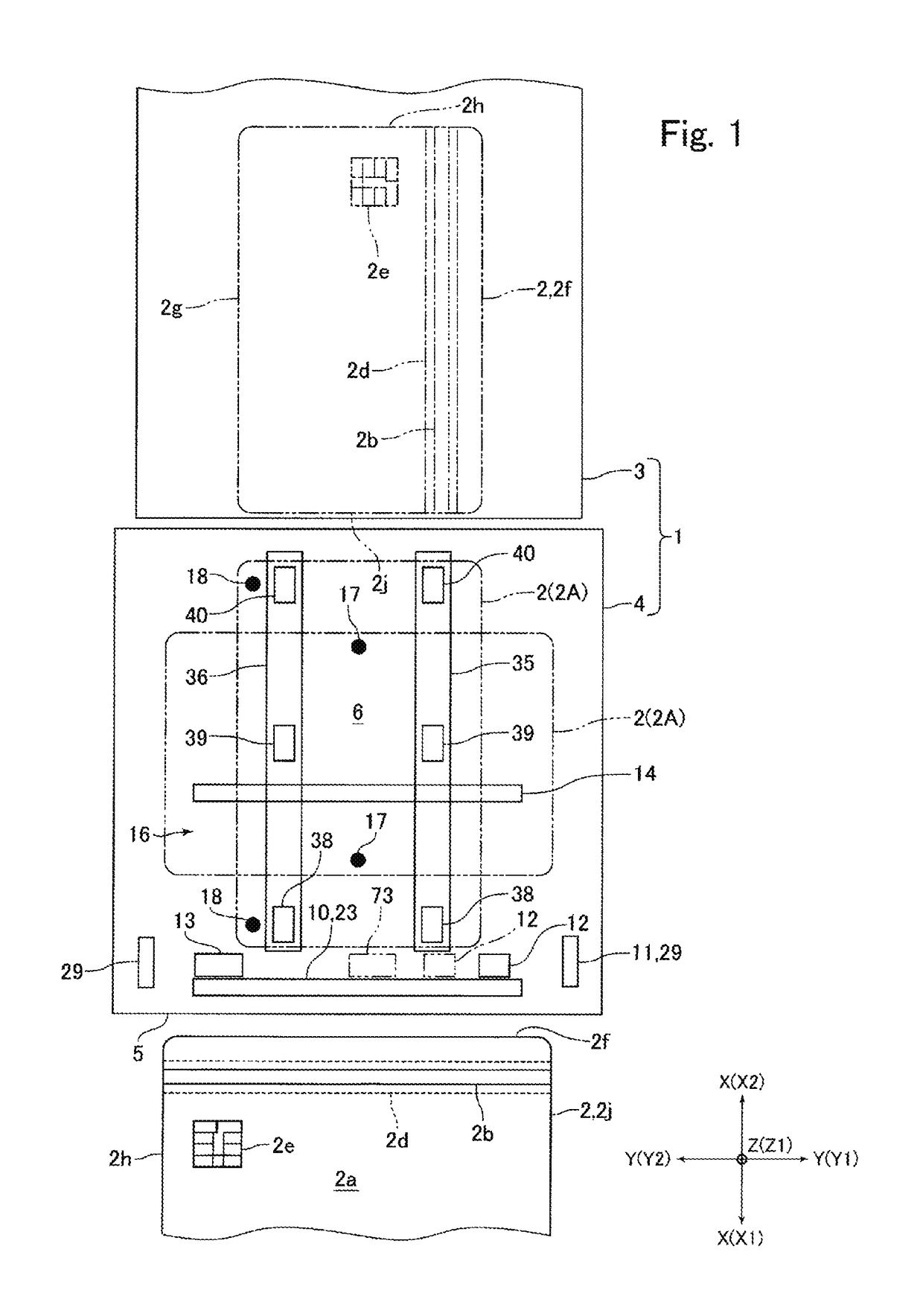
InactiveUS20060211288A1Prevent phishingPrevent card jamEngagement/disengagement of coupling partsConveying record carriersEngineeringCard reader
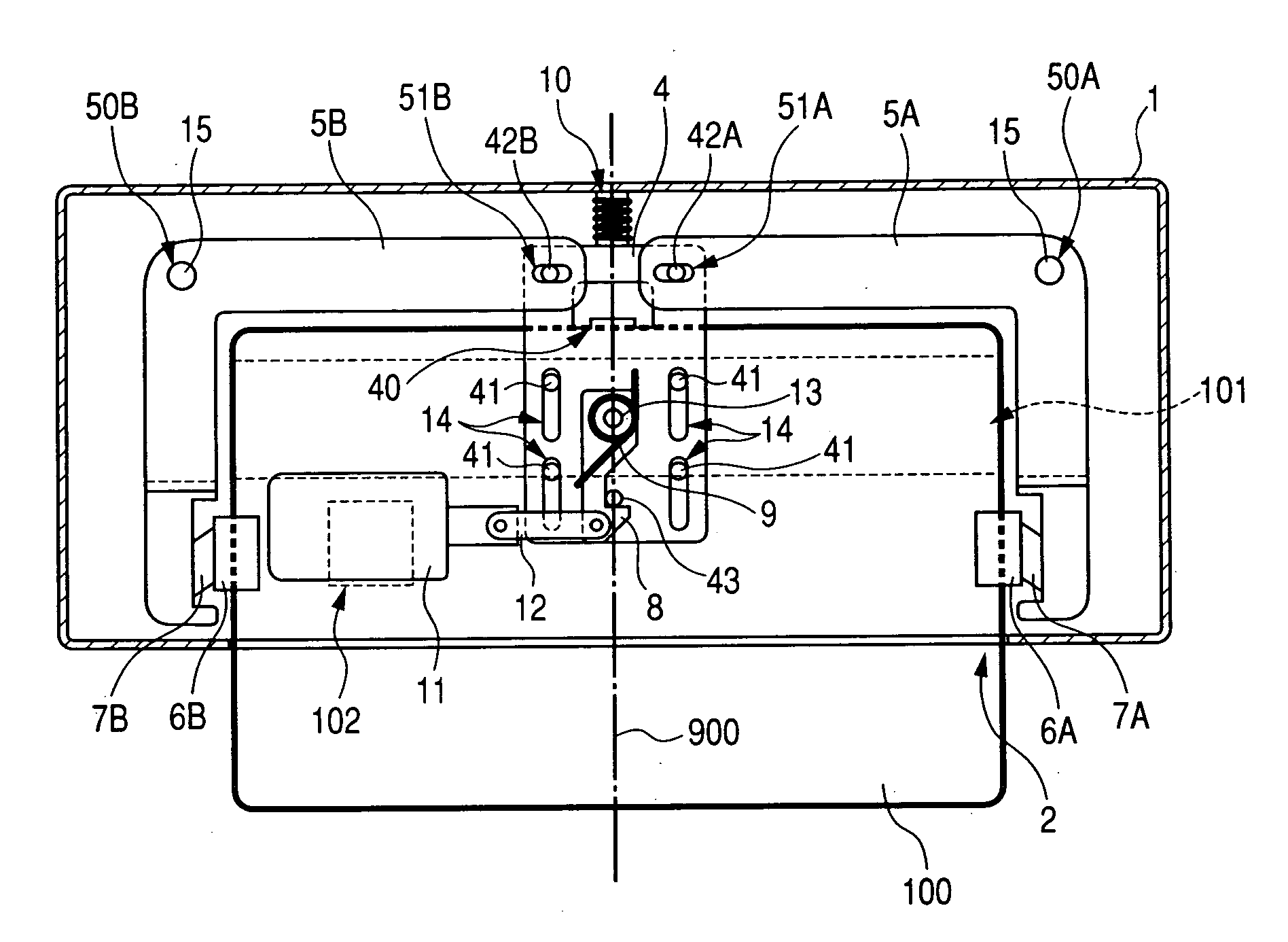
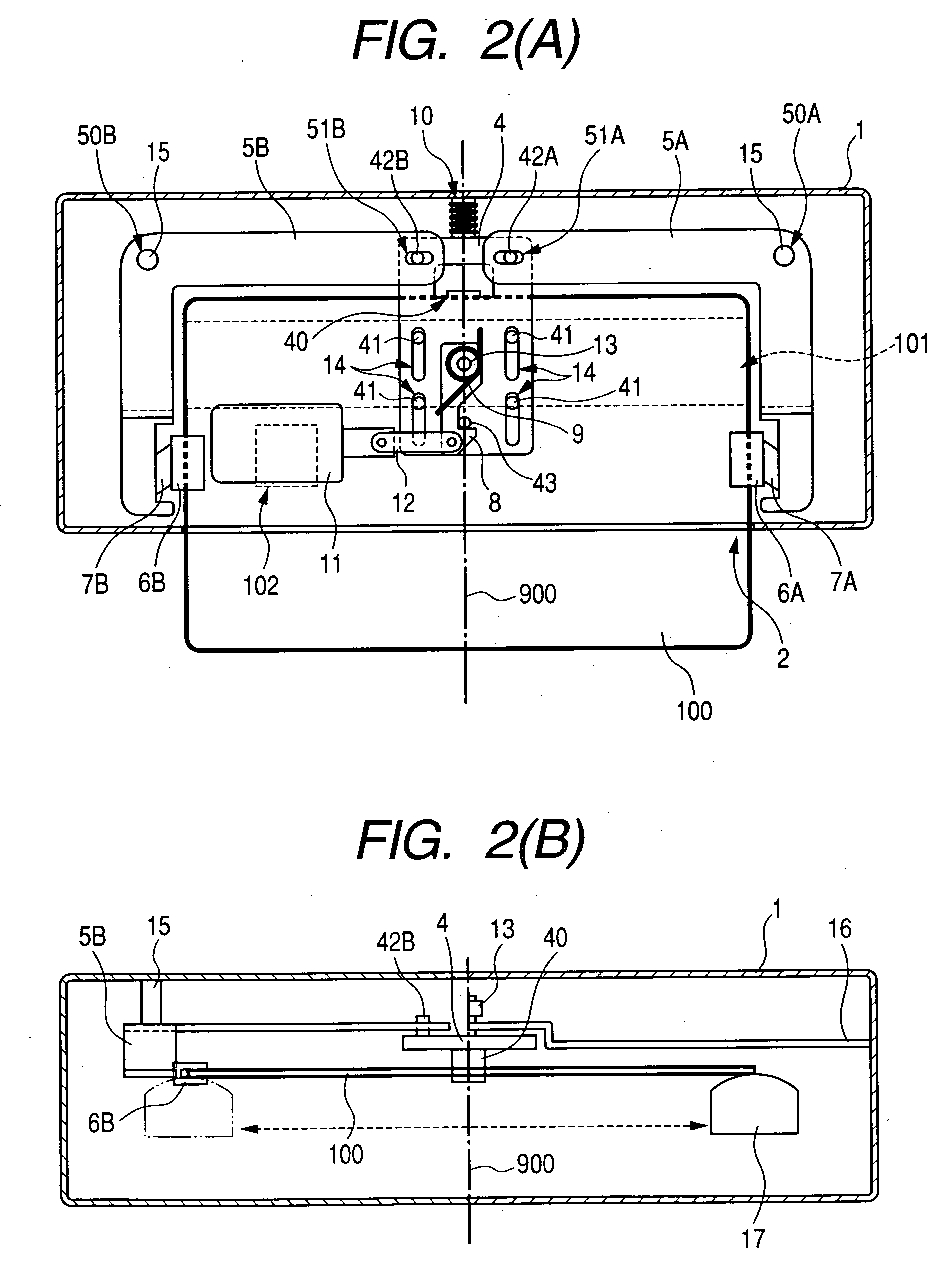
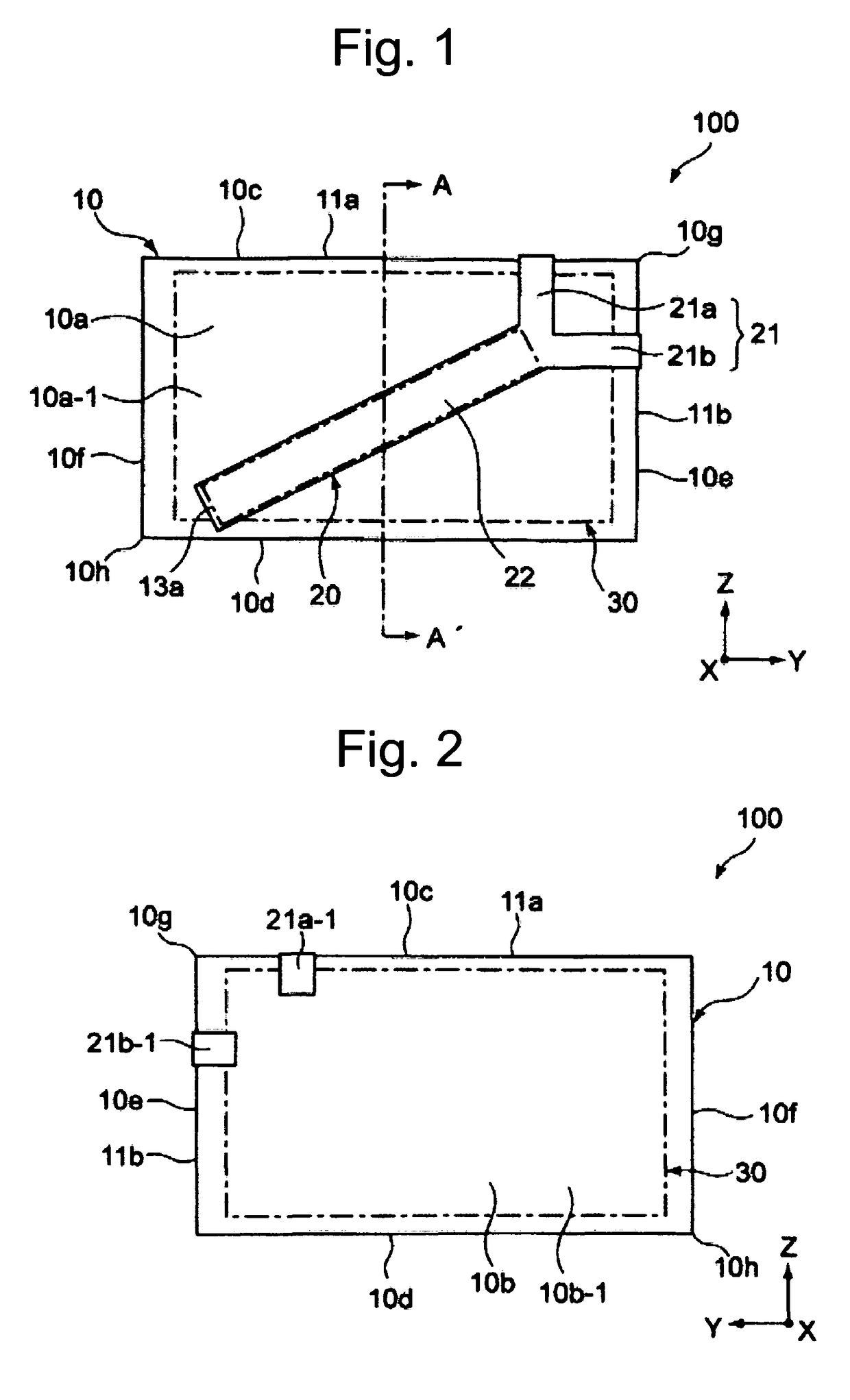
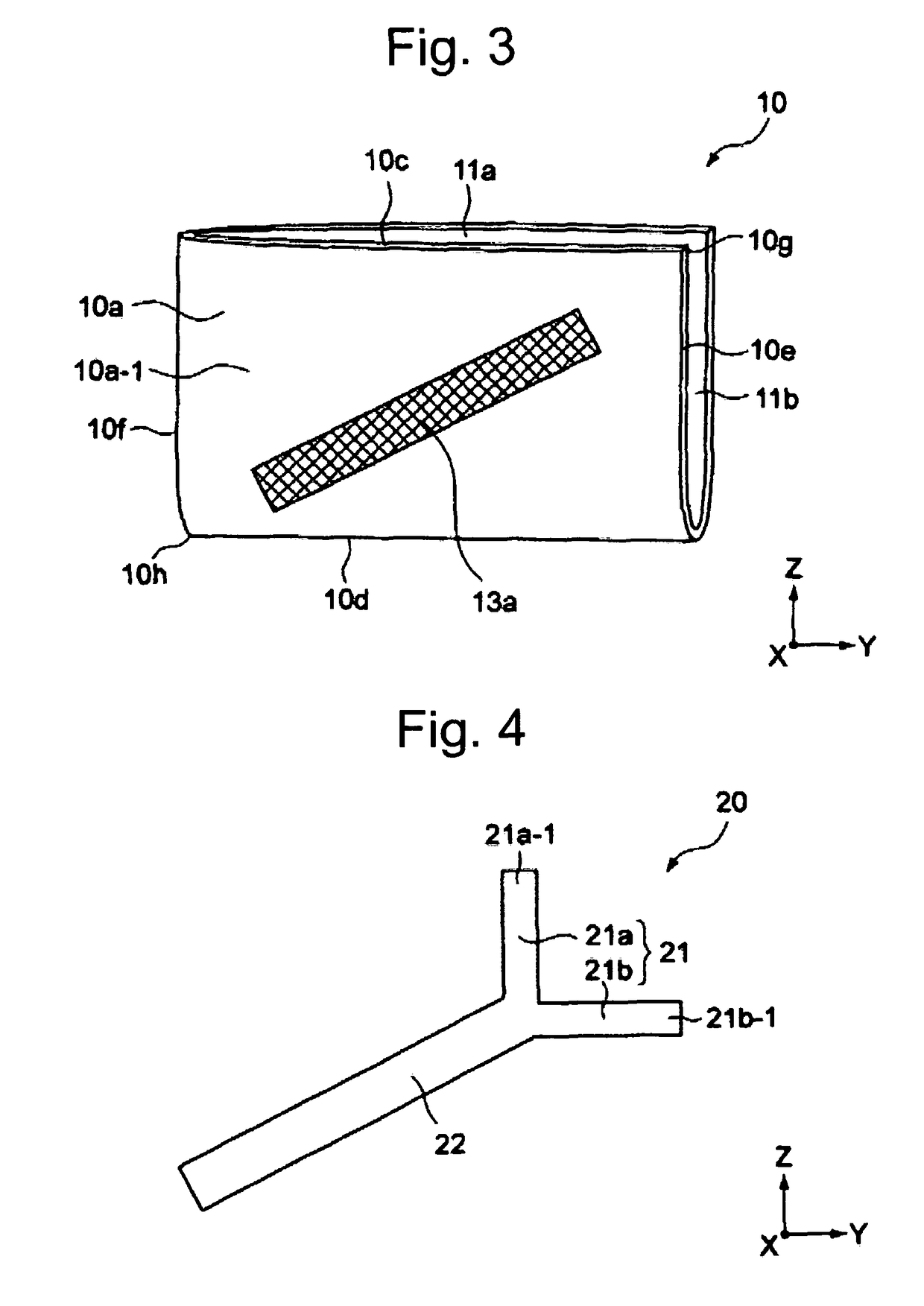
A card reader and writer is provided which can perform read and write operation on a card in a stable manner although it is configured such that a card inserting direction is perpendicular to a head moving direction and the card is partially inserted into the device. When a card 100 is inserted into a case 1 and comes into abutment against a depth abutment member 40 of a slider 4, the slider 4 moves in the depth direction. With this movement, pivotal levers 5A and 5B pivot and holders 6A and 6B come into abutment against end faces of the card 100 in the width direction to grip the card in the width direction. At the same time, in accordance with the movement of the slider 4, an engaging shaft 43 of the slider causes a pivotal engaging member 8 to pivot and comes into engagement with an engaging recess 82 after a predetermined amount of the pivotal movement.
Owner:HITACHI OMRON TERMINAL SOLUTIONS CORP
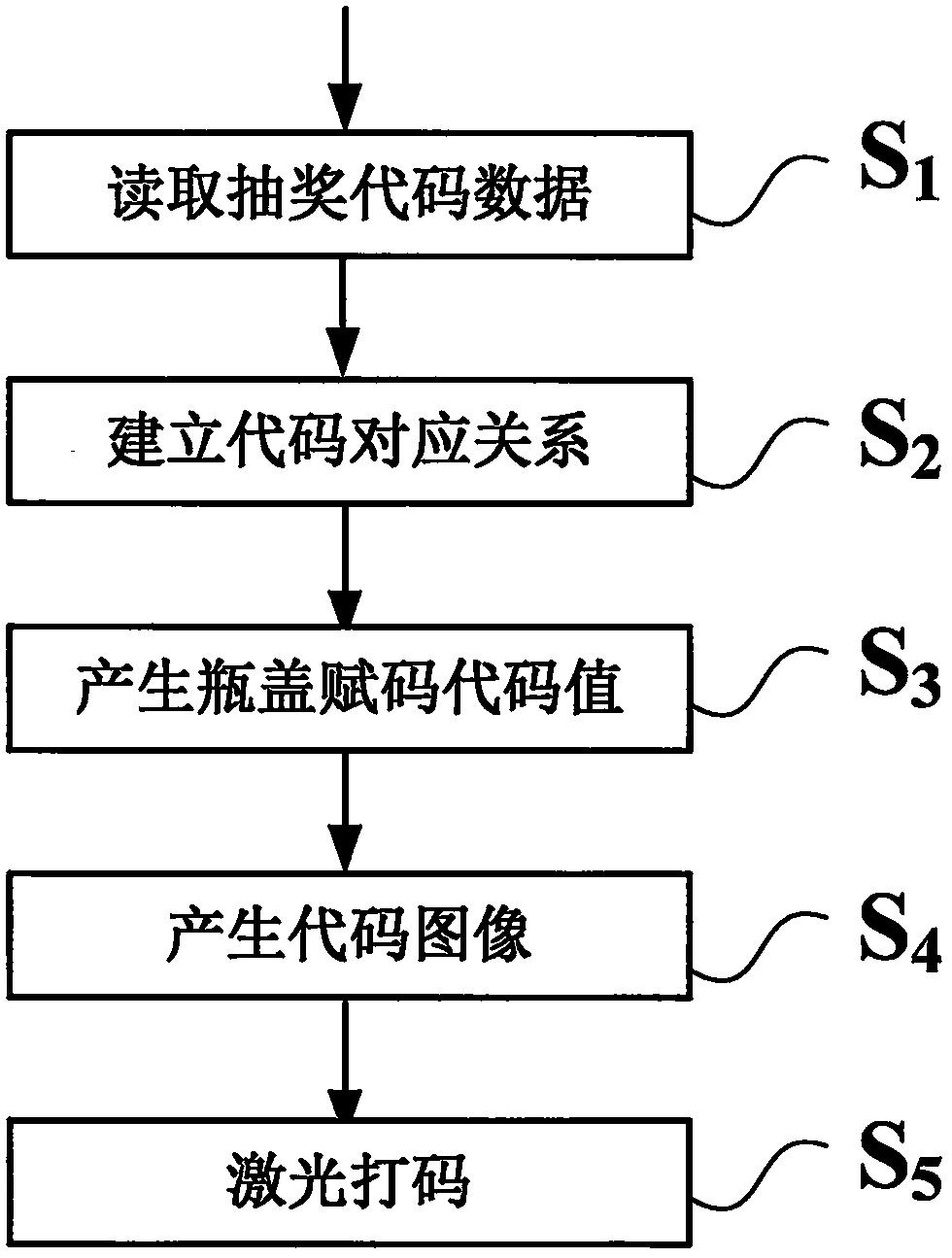
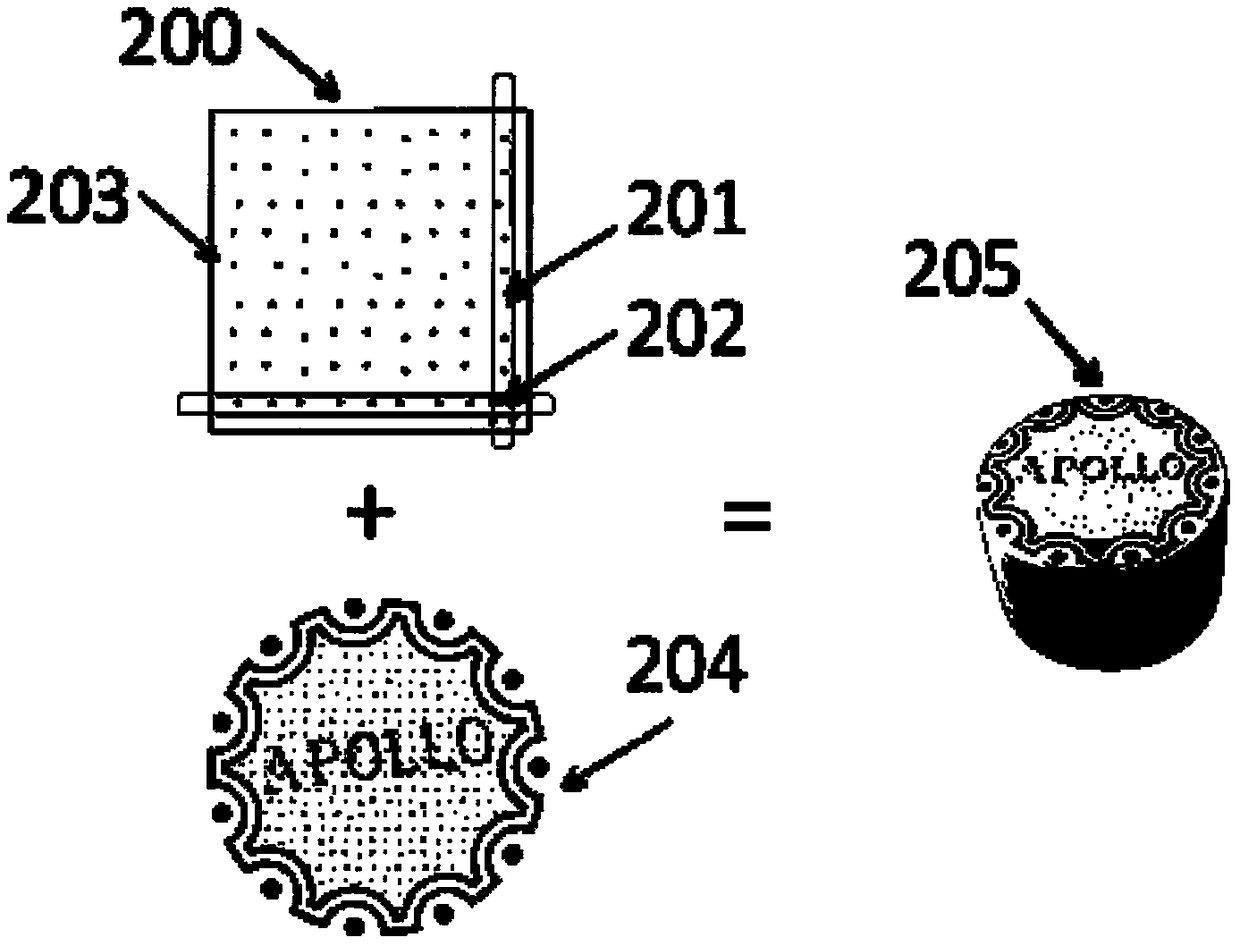
Bottle cap variable information on-line tagging device and identification method
InactiveCN106886808ALow costPrevent skimmingCo-operative working arrangementsTypewritersInformation processingBurn units
The invention relates to a bottle cap variable information on-line tagging device and identification method in the field of information processing, and is characterized in that the device stacks scattered bottle caps through a cap sorting unit, the bottle caps are sent to a conveying unit to sent to the following units, the bottle caps pass through a bottle cap burning unit, surface tension processing is performed on surfaces to be subjected to jet printing, the processed bottle caps are sent to a jet printing unit to be subjected to one-cap one-code tapping of all codes with optical readability including but not limited to a common QR two-dimensional code, a DM two-dimensional code, a decorative novel two-dimensional code, a color two-dimensional code, a vision code and an invisible code, the bottle caps after tapping are sent to an offset printing unit to perform printing of bottle cap images, the printed bottle caps are subjected to on-line detection and bad bottle caps are identified to be rejected, and the bottle caps that satisfy quality requirements are sent to the next process. The implementation effects of the bottle cap variable information on-line tagging device and identification method are that high-speed tapping can be performed on the bottle caps, the tapping cost is reduced, reading through stealing can be prevented, and a promotion activity of red envelope grabbing can be performed.
Owner:顾泽苍
Novel non-contact type smart IC card and implementation method thereof
InactiveCN103679254AHas masteryImprove securityRecord carriers used with machinesShortest distanceSmart card
The invention relates to the field of radio frequency cards, and particularly discloses a novel non-contact type smart IC card and an implementation method thereof. The implementation method comprises the steps that one end of an antenna coil is connected with an IC smart chip, and the other end of the antenna coil is connected with a goldfinger; the IC smart chip, the antenna coil and the goldfinger are respectively placed in a groove, and the groove, the IC smart card, the antenna coil and the goldfinger are of an integral structure; a PVC card is composed of an upper PVC layer, an insulation isolating layer and a lower PVC layer; a key identification is arranged at one end of the outer surface of the upper PVC card, a conductive film corresponds to the key identification in position, a through hole is formed in one end of the insulation isolating layer, the conductive film penetrates through the through hole and is connected with the goldfinger, and the conductive film and the through hole correspond to the goldfinger in position; the insulation isolating layer is placed between the upper PVC layer and the lower PVC layer. The non-contact type smart IC card can be controlled subjectively, data in the non-contact card are effectively prevented from being stolen to read or misread in a short-distance high-frequency wireless communication technology, and using of the IC card is safer.
Owner:AITIWEIER ELECTRONICS TECH BEIJING
Manually operated card reader
ActiveCN103824042APrevent skimmingCo-operative working arrangementsSensing by electromagnetic radiationCard readerActuator
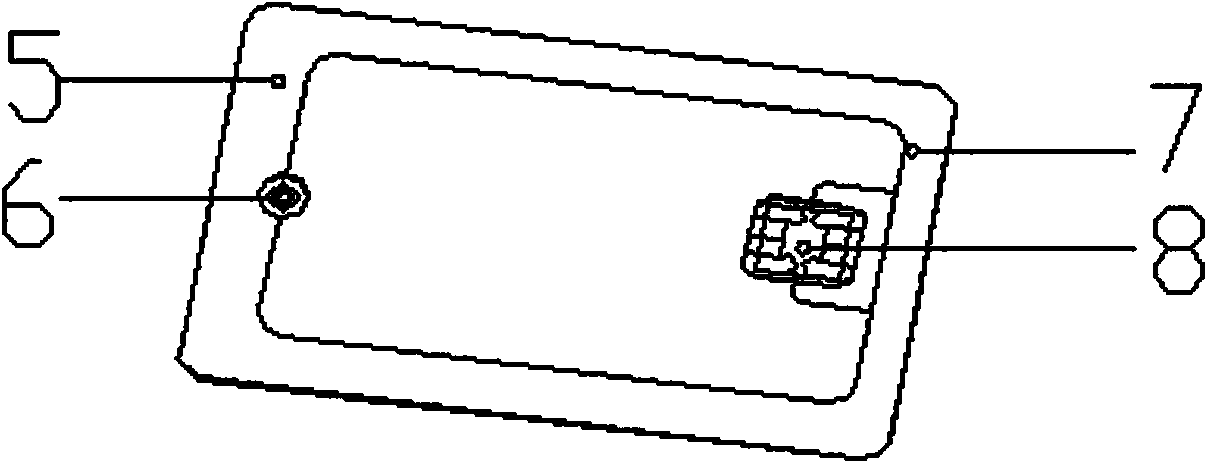
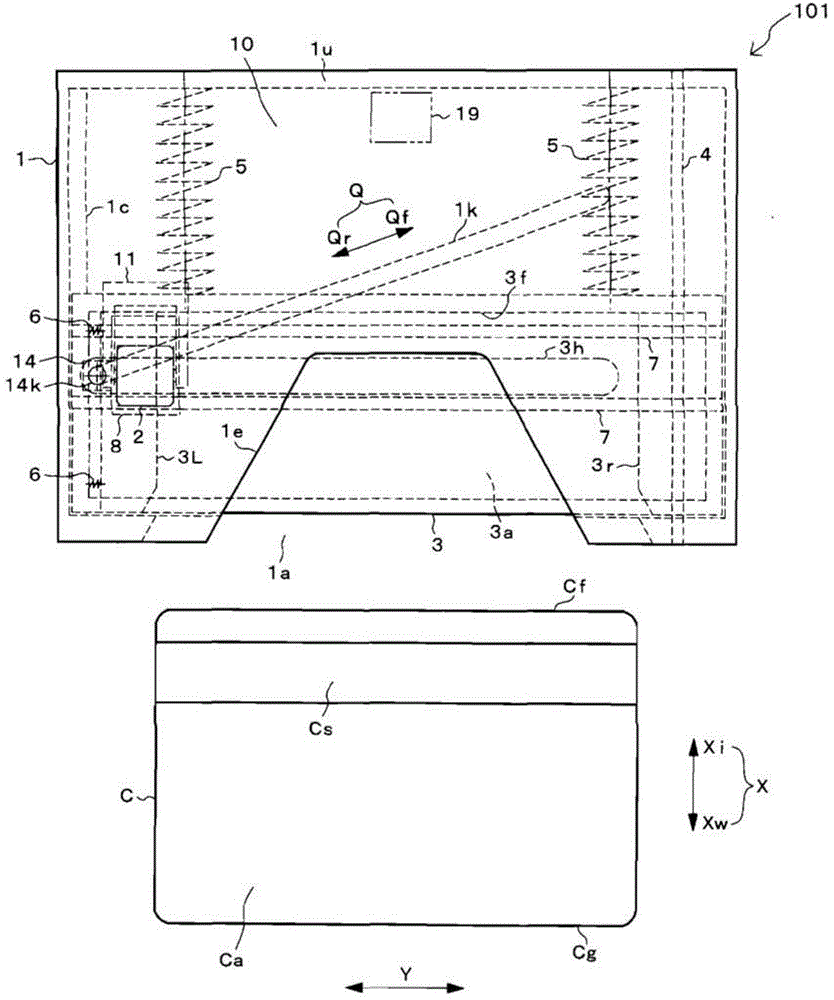
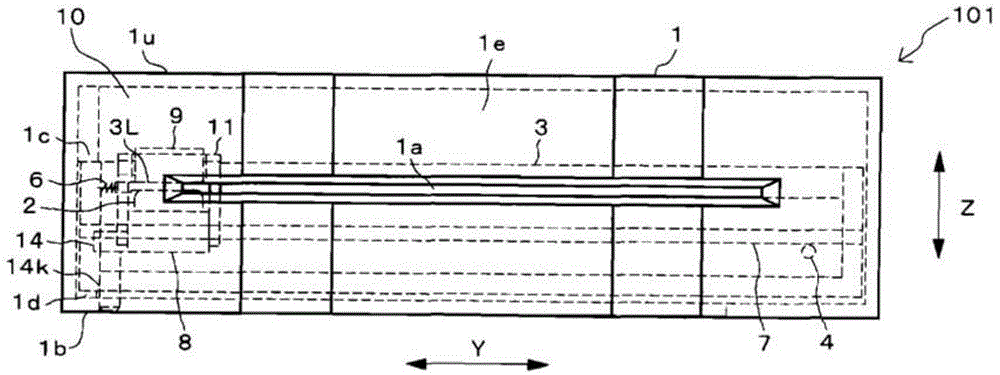
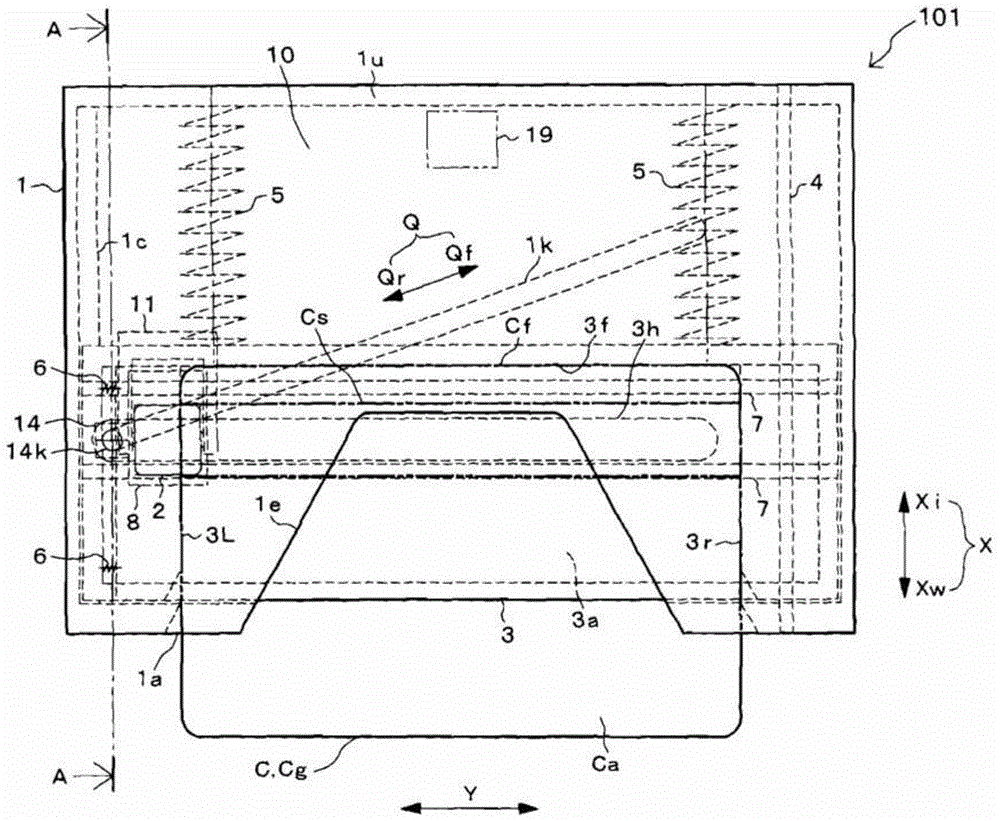
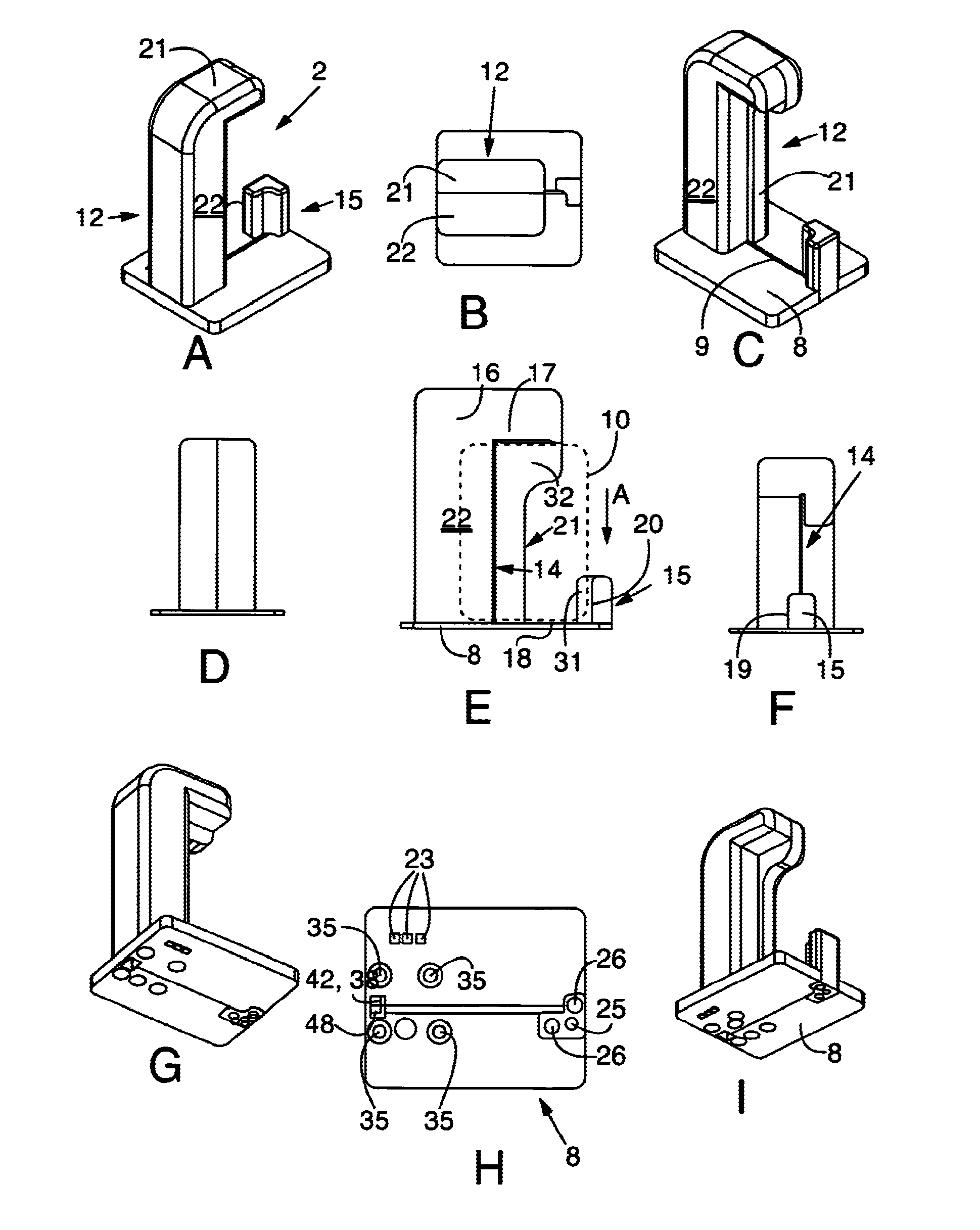
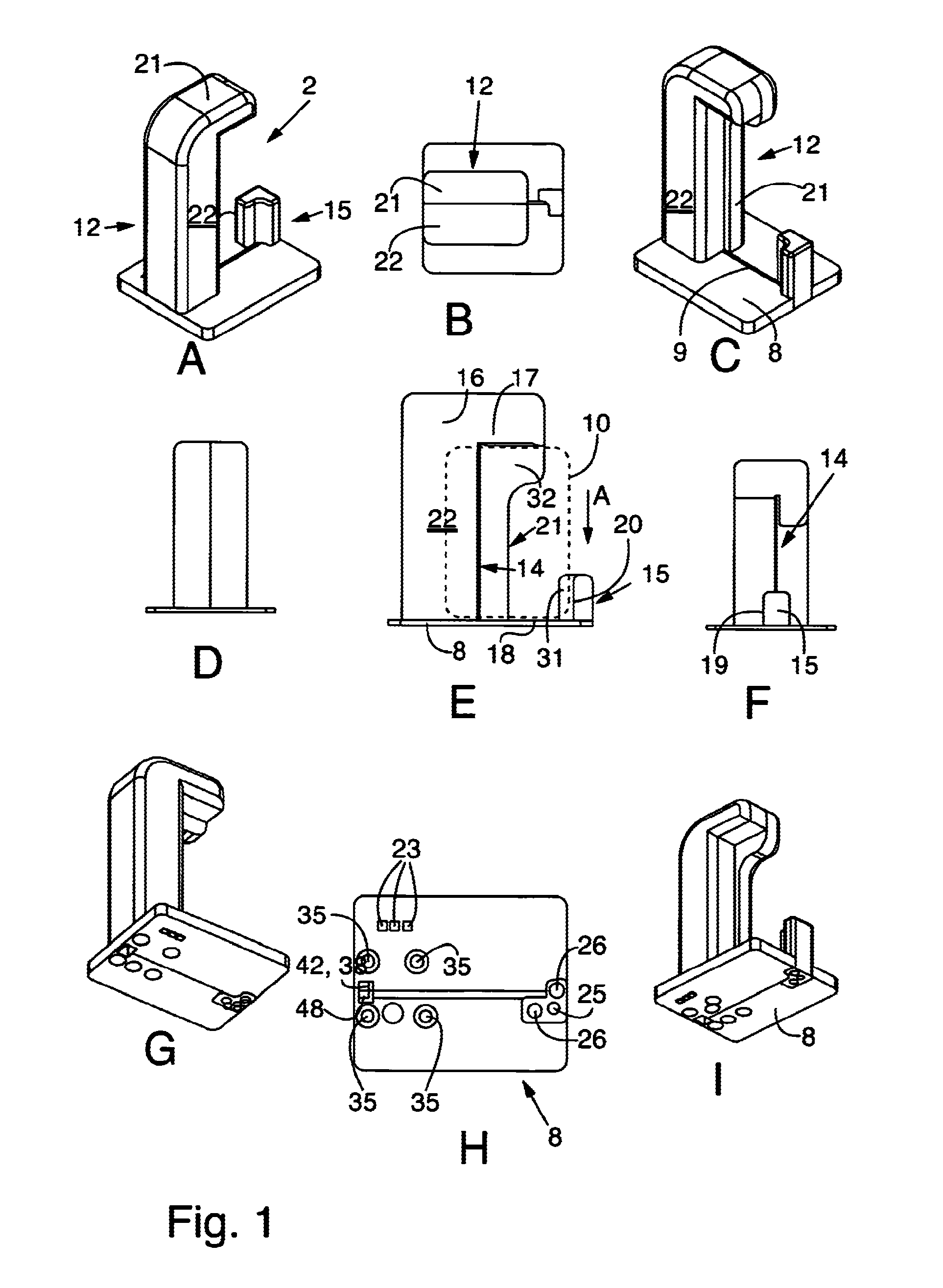
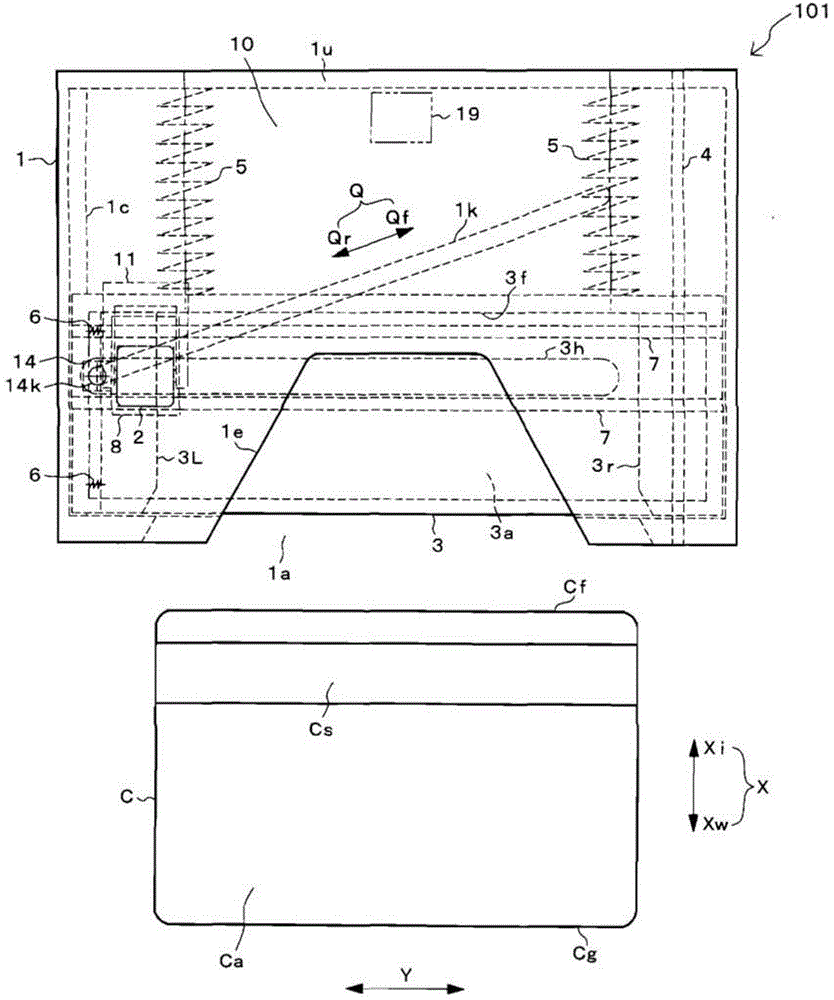
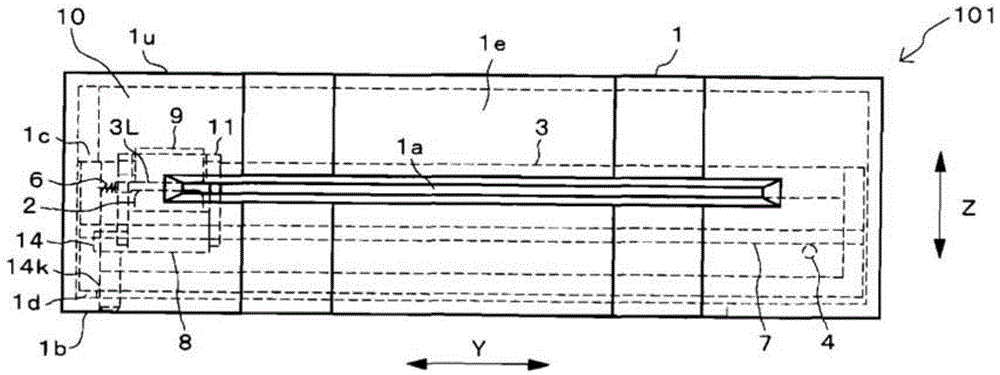
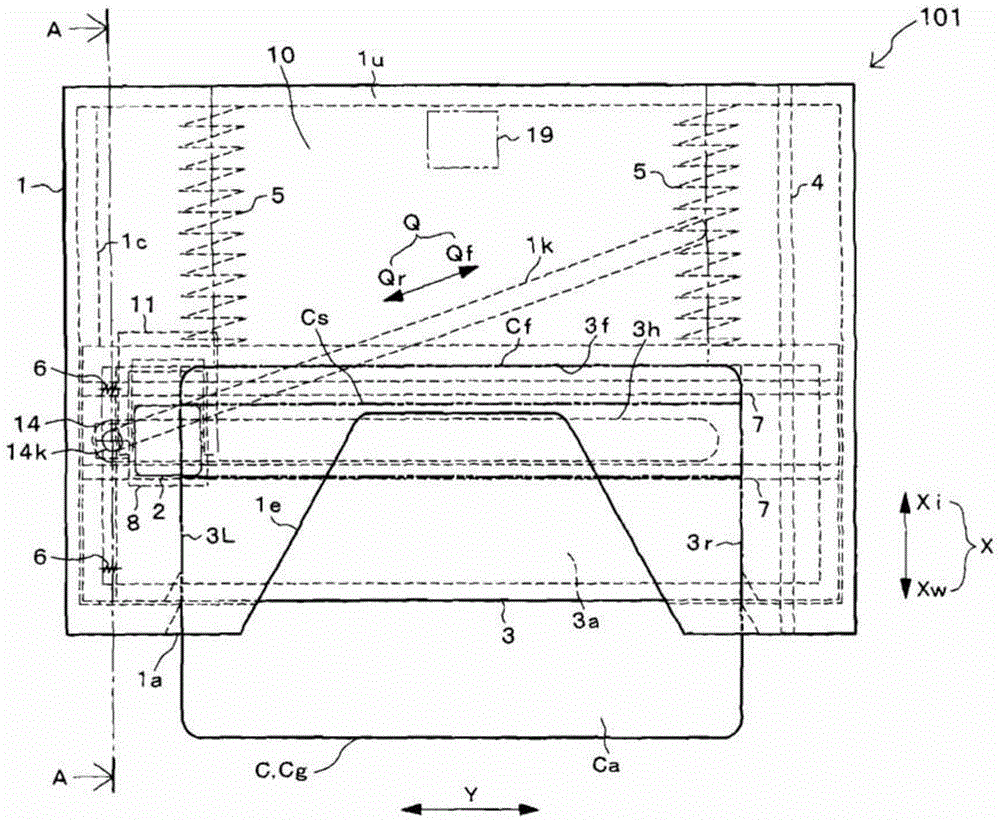
A manually operated card reader can prevent skimming when a card is inserted and can move a magnetic head to read magnetic information of the card without using an actuator. The manually operated card reader (101) has an insertion opening (1a) allowing a card (C) to be inserted in a short edge direction (X), a magnetic head (2) reads magnetic information from a magnetic stripe (Cs) which is configured to extend in a long edge direction (Y) in the card (C), and a magnetic head moving mechanism (10). The magnetic head moving mechanism (10), through an inserting force when the card (C) is inserted in the short edge direction (X) from the insertion opening (1a), enables the magnetic head (2), in a state of being in contact with the magnetic stripe (Cs), to be moved from one end of the magnetic stripe (Cs) in the long edge direction (Y) in the card (C) to the other end.
Owner:HITACHI OMRON TERMINAL SOLUTIONS CORP
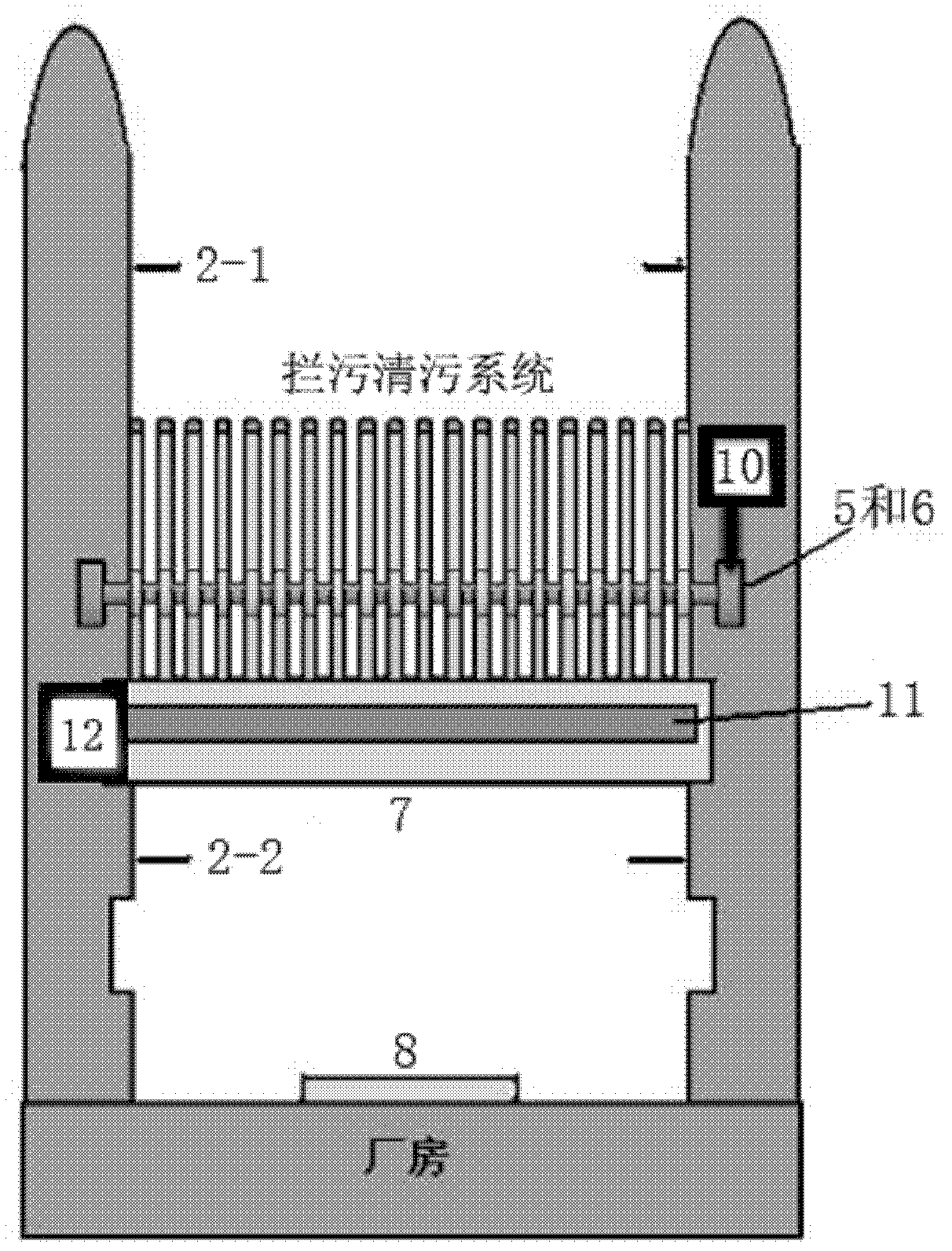
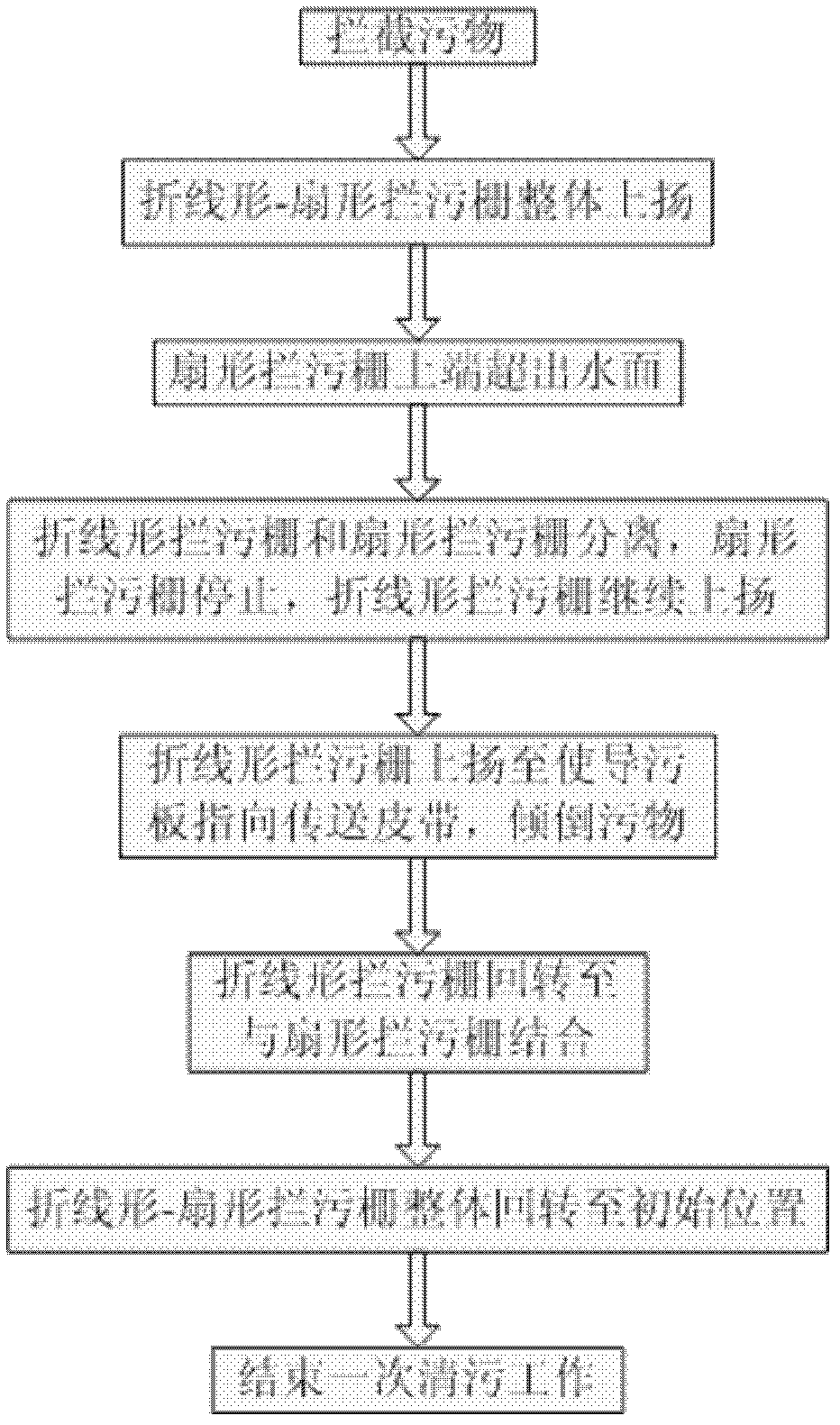
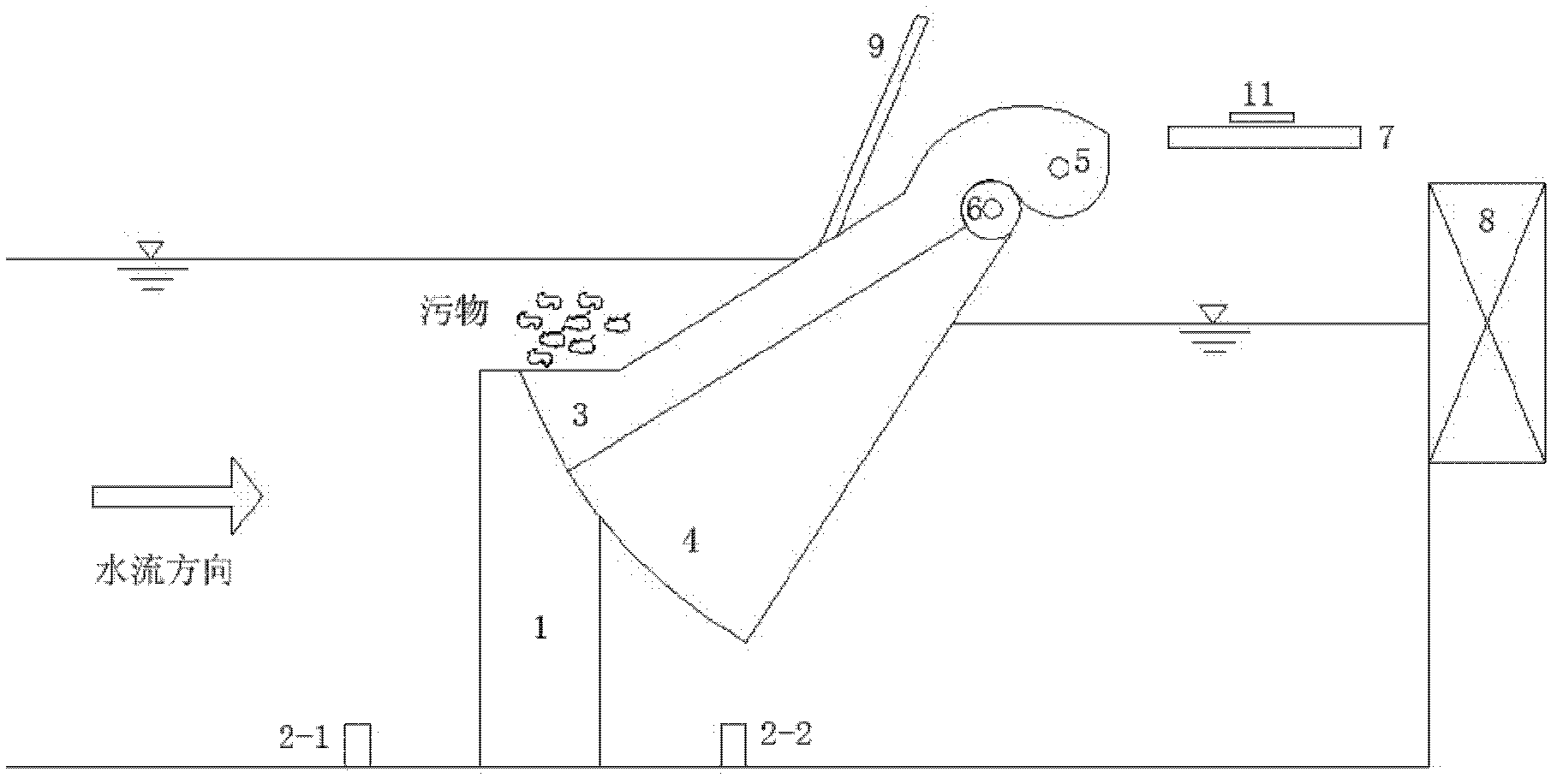
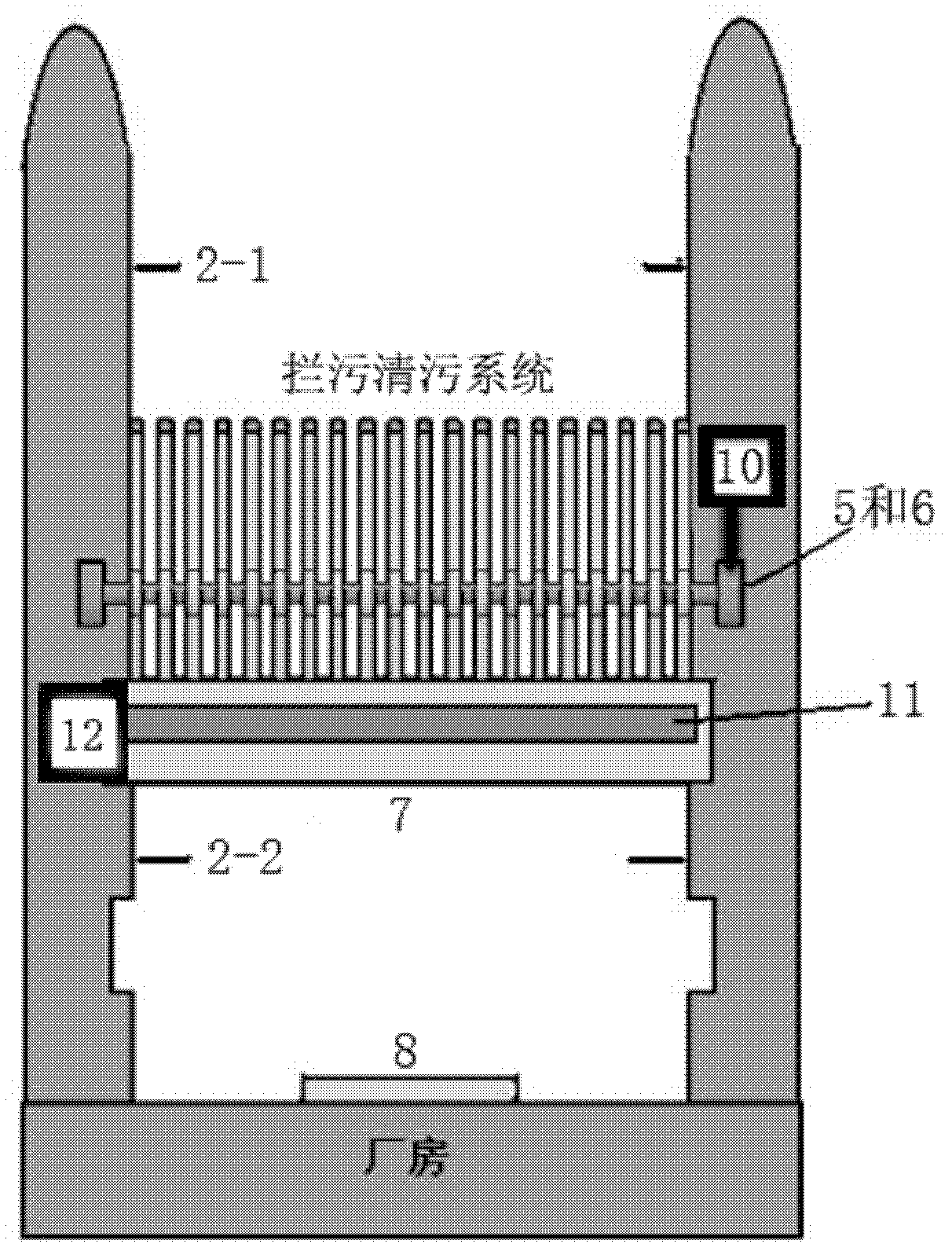
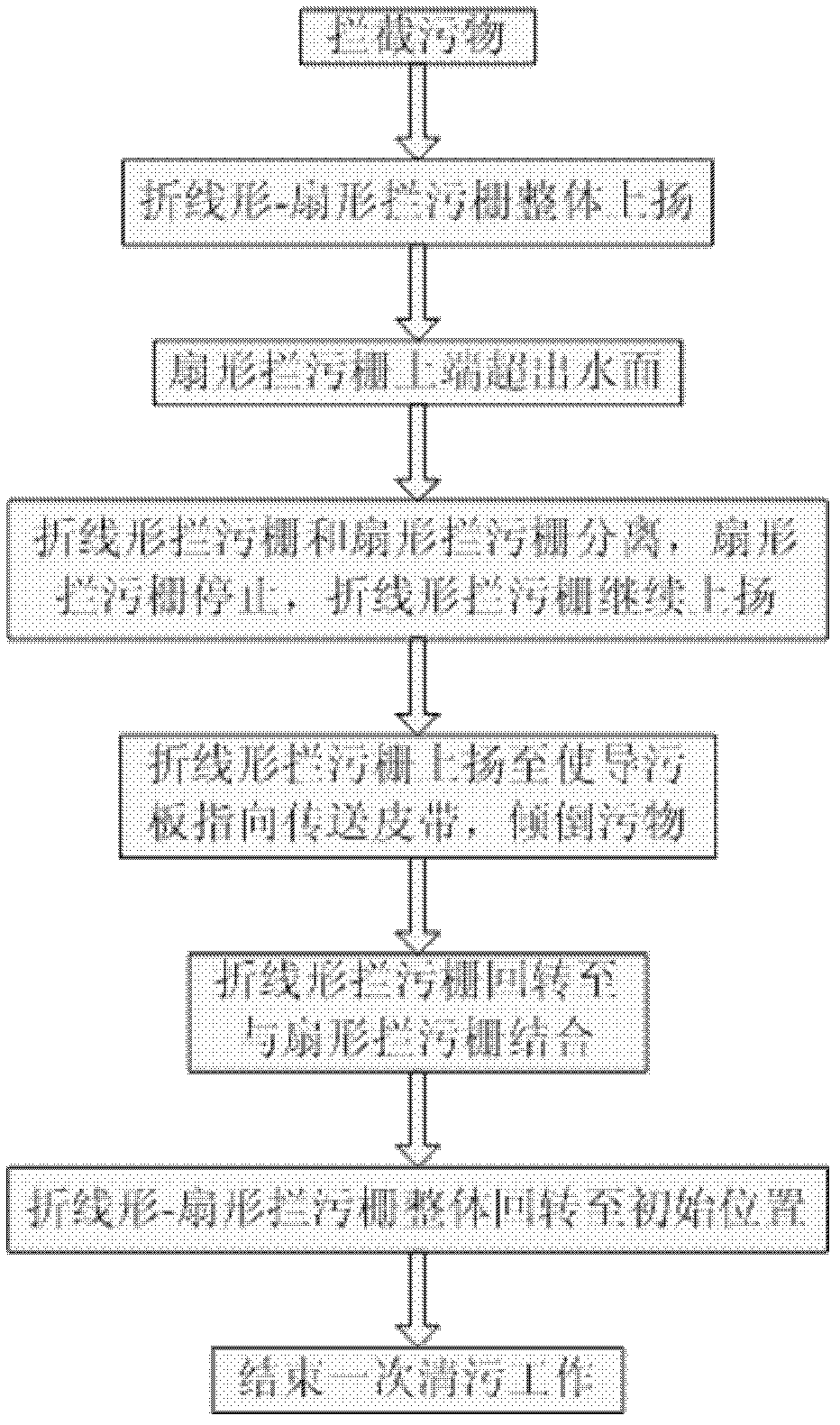
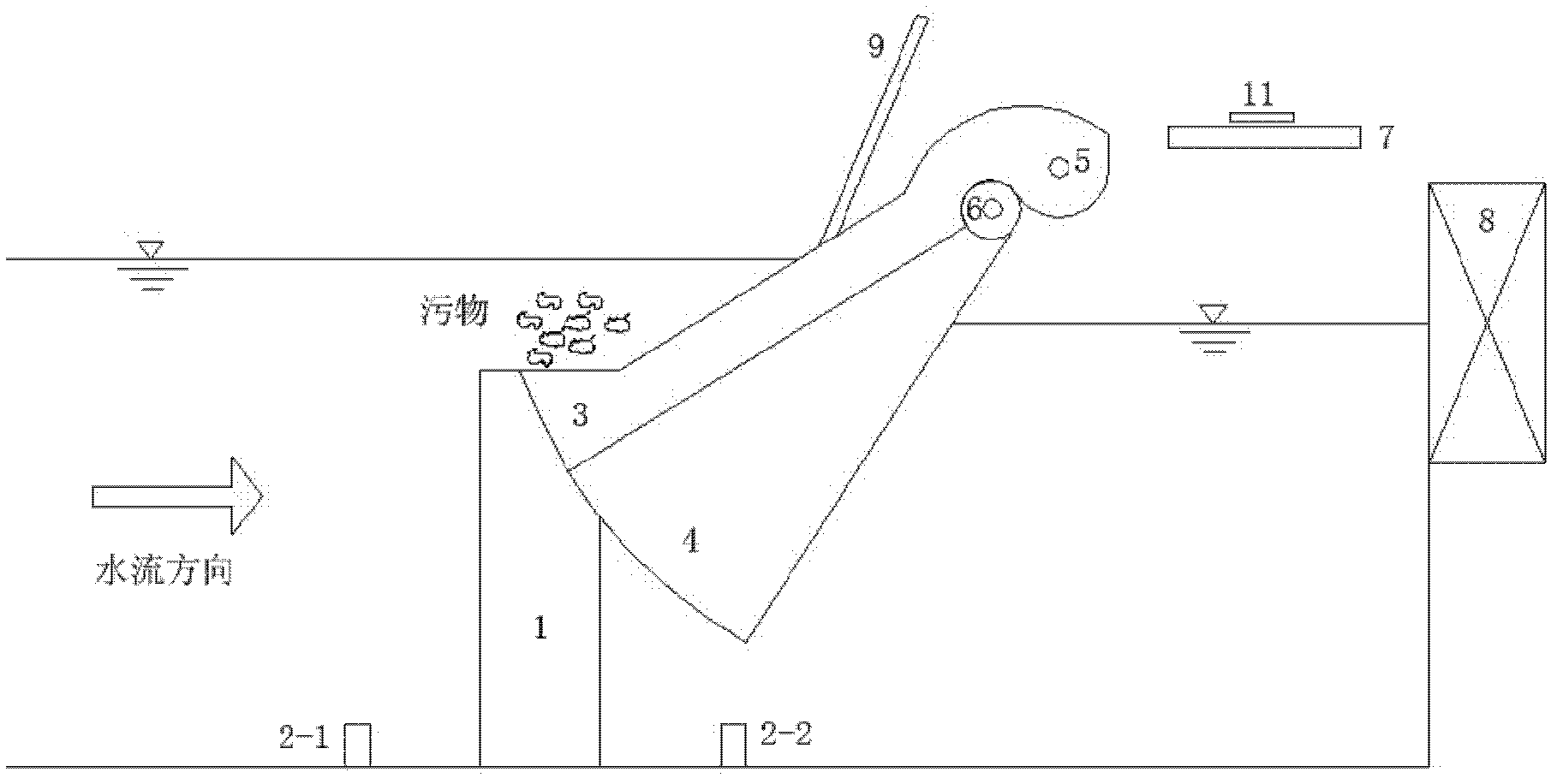
Fold-line-shaped and fan-shaped biaxial rotary sewage blocking and sewage cleaning system
InactiveCN102535407APrevent skimmingGuaranteed normal water flowArtificial water canalsTransmission beltMonitoring system
The invention relates to a fold-line-shaped and fan-shaped biaxial rotary sewage blocking and sewage cleaning system, which belongs to the field of water conservancy project facilities and comprises a vertical sewage blocking fence, a fold-line-shaped sewage blocking fence, a fan-shaped sewage blocking fence, a fence difference monitoring system a motive power device, a transmission belt, a work bridge, a sewage guide plate and bearings, wherein the fence difference monitoring system consists of an upstream water level sensor and a downstream water level sensor, and the bearings are used for respectively controlling the fold-line-shaped sewage blocking fence and the fan-shaped sewage blocking fence. The upstream water level sensor and the downstream water level sensor arranged in the fence difference monitoring system are respectively connected with a remote computer system through data wires, and the remote computer system is used for automatically or manually controlling the motive power device for monitoring the water level differences in front of the vertical sewage blocking fence and behind the vertical sewage blocking fence. The sewage blocking and sewage cleaning system provided by the invention has the advantages that the sewage collection, the sewage blocking and the sewage cleaning are integrated, the problem of sewage blocking fence blockage caused by sewage blockage at water taking openings in the water conservancy project operation process is solved, the manufacture is simple, the use is convenient and reliable, in addition, the cost is low, economy and applicability are realized, the sewage collection, sewage blocking and sewage cleaning effects are ideal, and the sewage blocking and sewage cleaning system is suitable for being popularized and applied.
Owner:SICHUAN UNIV
Method for direct ink jet printing of variable information
InactiveCN108357227APrevent skimmingSolve the urgent needs of printingDuplicating/marking methodsOther printing apparatusEngineeringElectrical and Electronics engineering
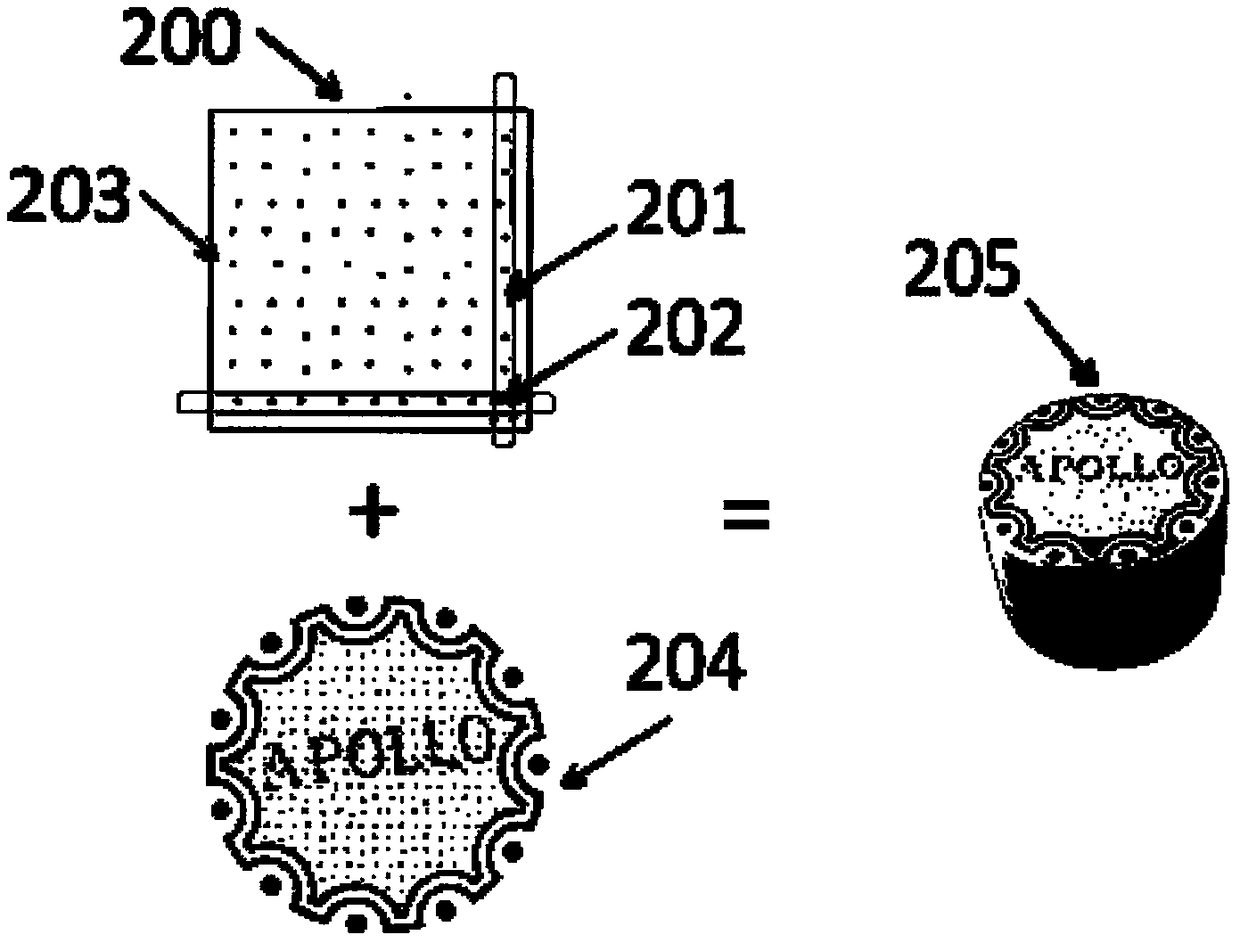
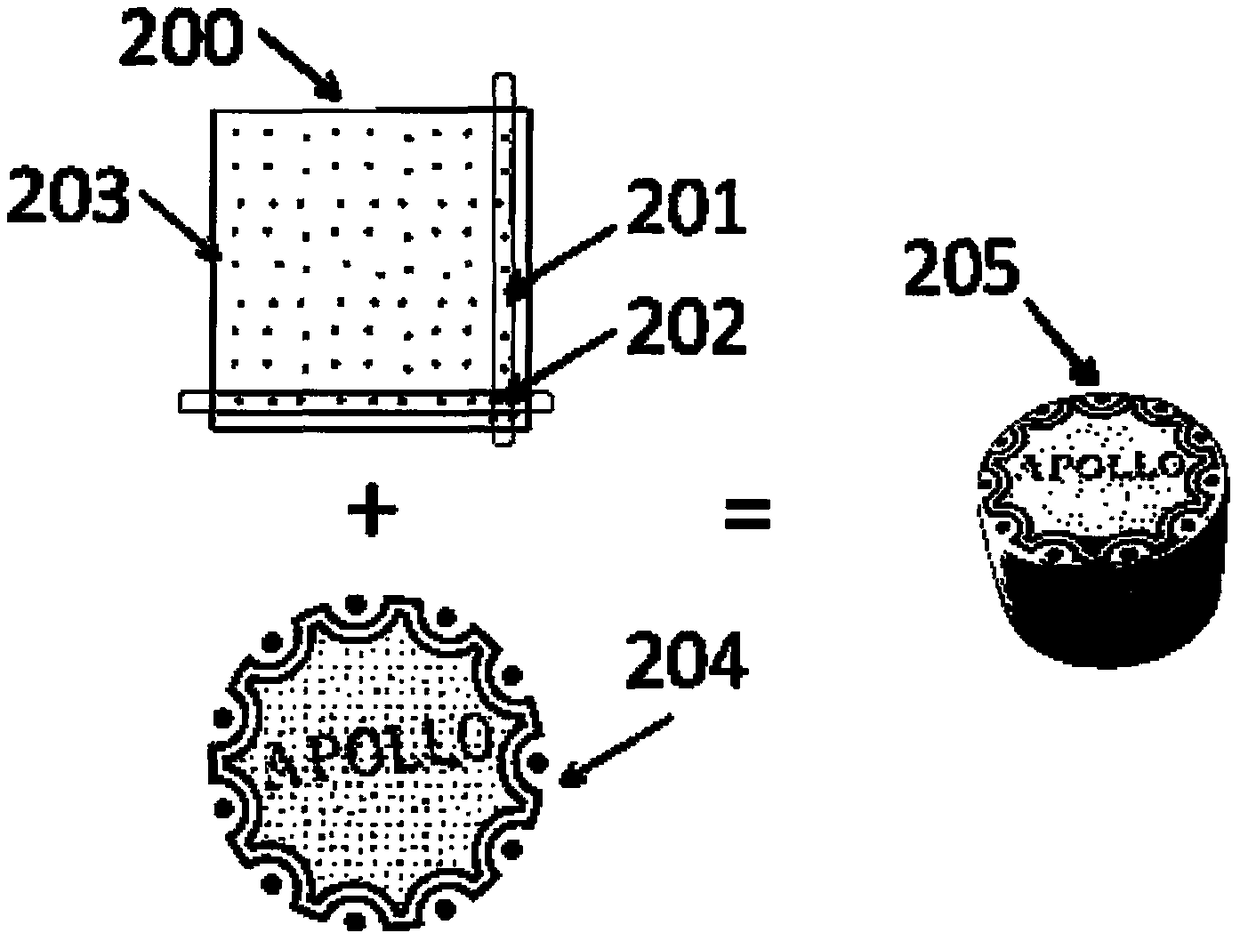
the invention relates to a method for direct ink jet printing of variable information. According to the method, the phenomenon that a two-dimensional code on a packaging container is read in an unauthorized mode before a consumer purchases a commodity can be avoided, the urgent need of carrying out ink jet printing of a code on the bottom of the inner side of a bottle cap or a concave and deep container can be met, and meanwhile, the safety of food can be considered. The method is characterized by comprising the steps that a background image of an optical readable computer graphic code is formed at a low-lying part of the concave and deep container through a spraying mode or an ink jet printing mode; coding of the optical readable computer graphic code is directly carried out on the low-lying part of the concave and deep container through a continuous ink jet printing device; and after ink jet printing of the optical readable computer graphic code is carried out on the low-lying part of the concave and deep container, a protective film is sprayed. The method has the advantages that high-speed and large-scale coding can be realized on common bottle caps or concave and deep containers which are not likely to be subjected to coding.
Owner:天津市阿波罗信息技术有限公司
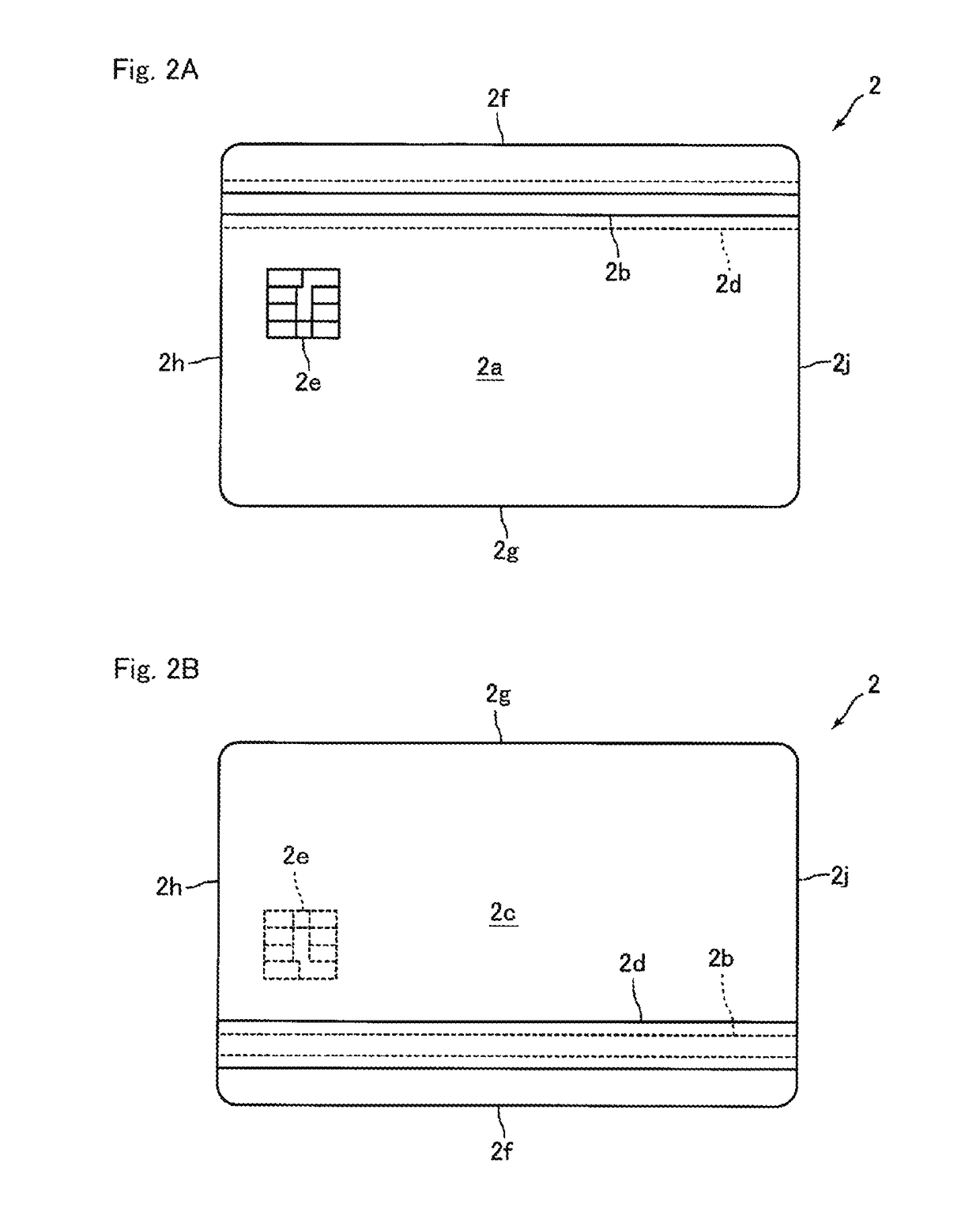
Card case
The present invention provides a card case that can prevent skimming, when a noncontact IC card is sent to a card user from an issuer of it, or carried by the card user. Since metal films, which shield from an electromagnetic wave, are provided in a card main body, it makes prevention of skimming possible, when the noncontact IC card is sent to the card user from the card issuer. The card user peels off a peeling the section by taking off the seal of openings from an adhesive section, and then insert the card main body having the exposed the adhesive section into a card storing section formed in his wallet or commuter pass holder. As a result, skimming of the IC card can be prevented even when it is carried by the card user in his wallet or the commuter pass holder.
Owner:TOKUYAMA KENICHI
Card case
The present invention provides a card case that can prevent skimming, when a noncontact IC card is sent to a card user from an issuer of it, or carried by the card user. Since metal films, which shield from an electromagnetic wave, are provided in a card main body, it makes prevention of skimming possible, when the noncontact IC card is sent to the card user from the card issuer. The card user peels off a peeling the section by taking off the seal of openings from an adhesive section, and then insert the card main body having the exposed the adhesive section into a card storing section formed in his wallet or commuter pass holder. As a result, skimming of the IC card can be prevented even when it is carried by the card user in his wallet or the commuter pass holder.
Owner:TOKUYAMA KENICHI
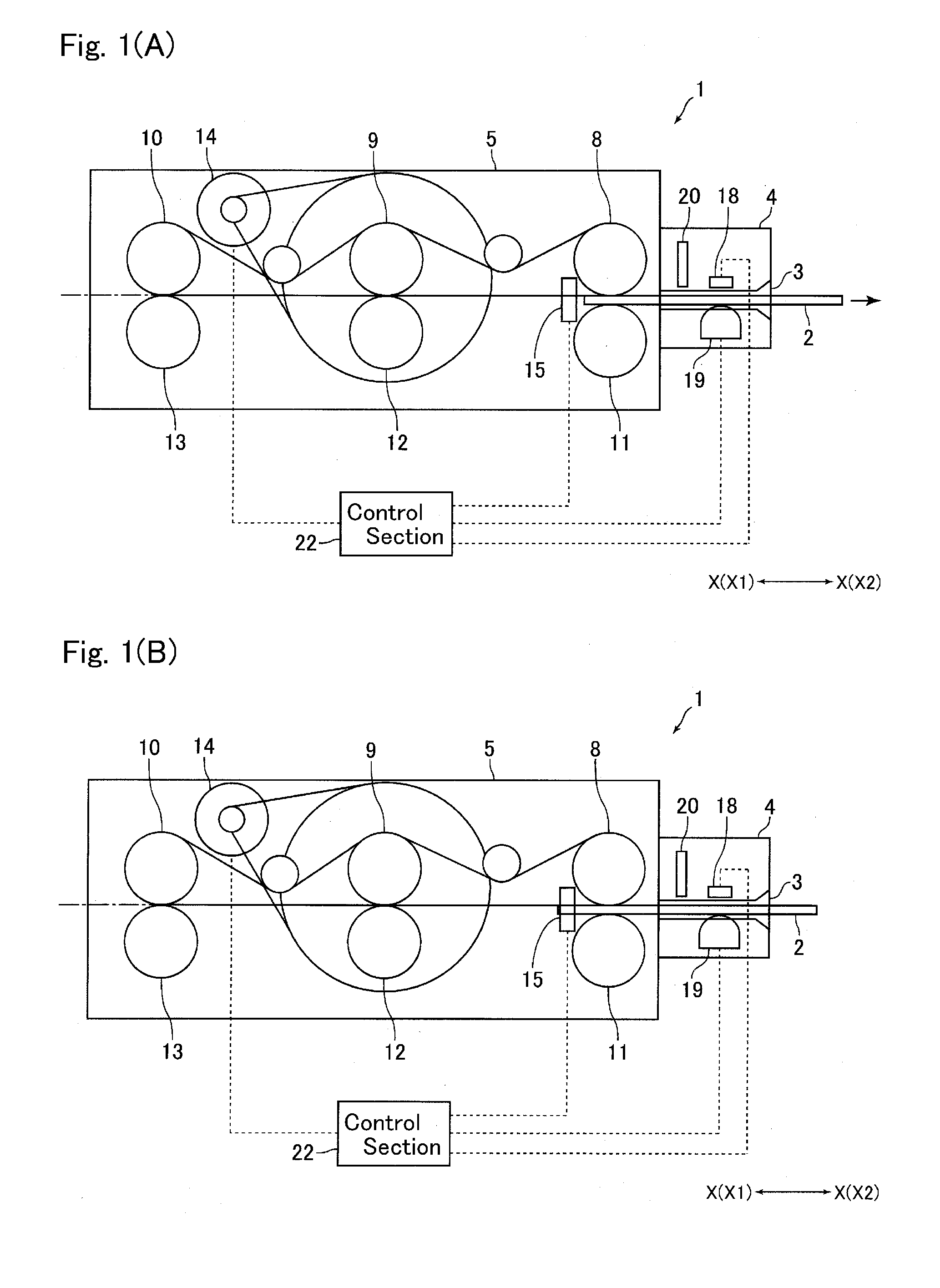
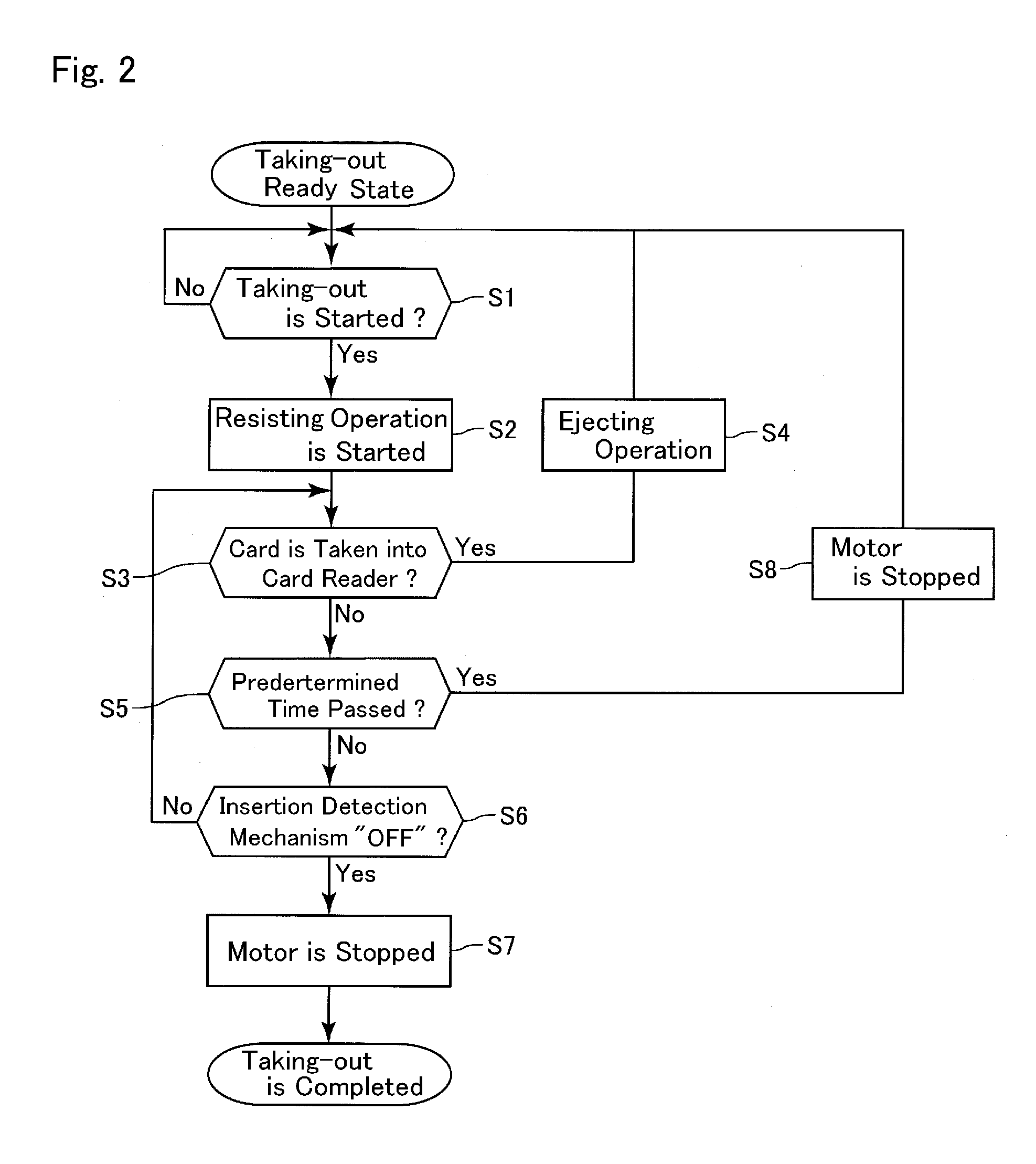
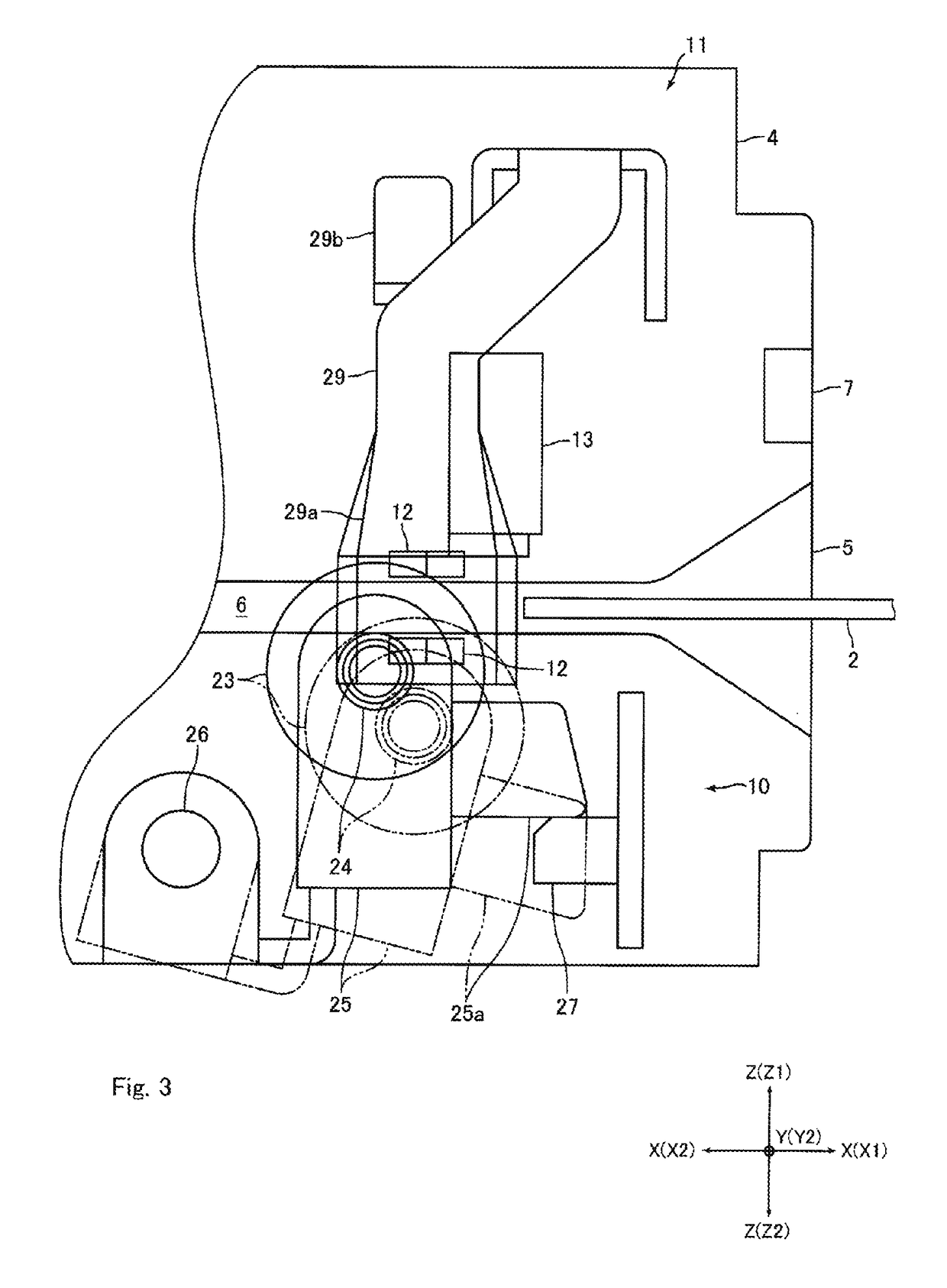
Card reader and control method therefor
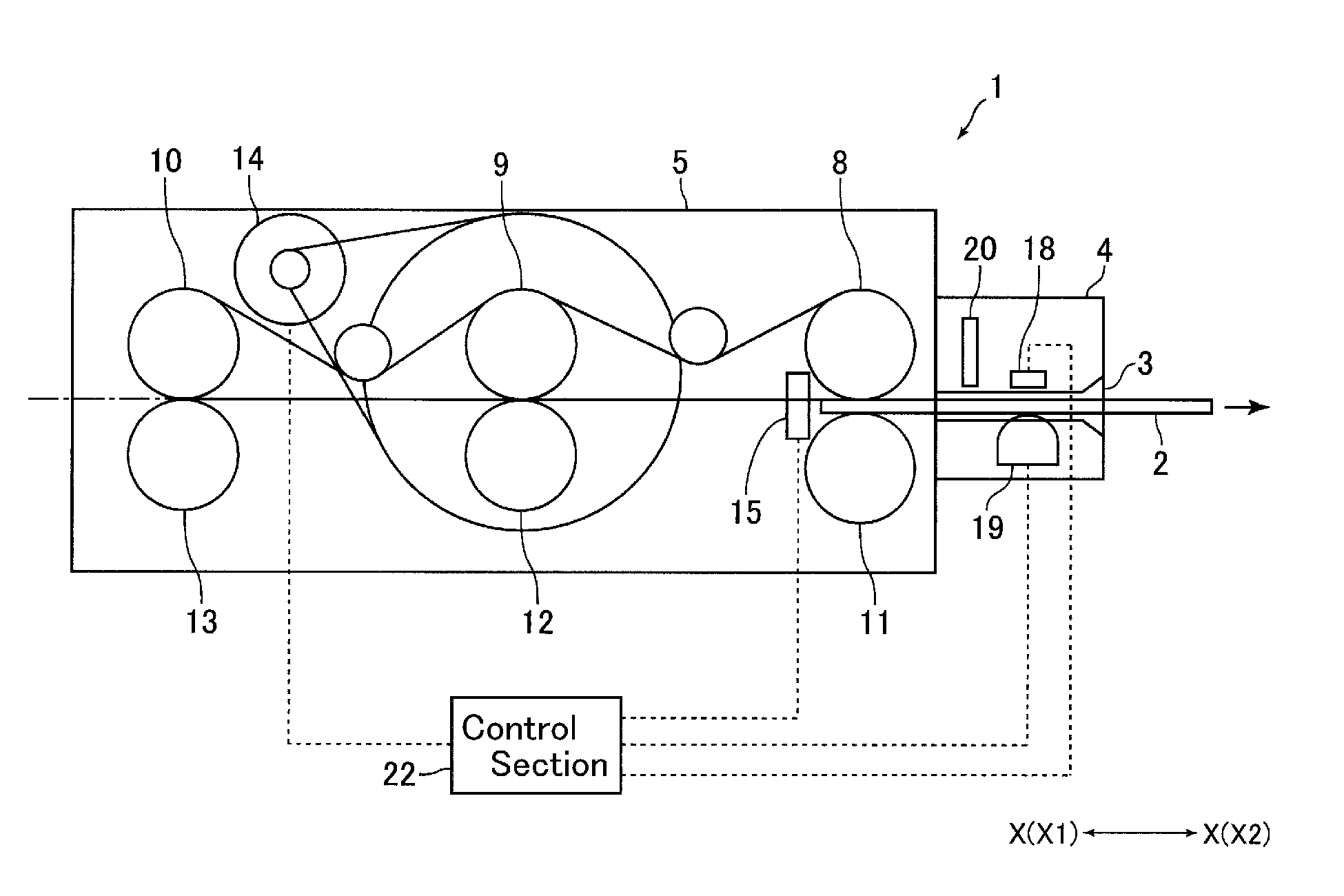
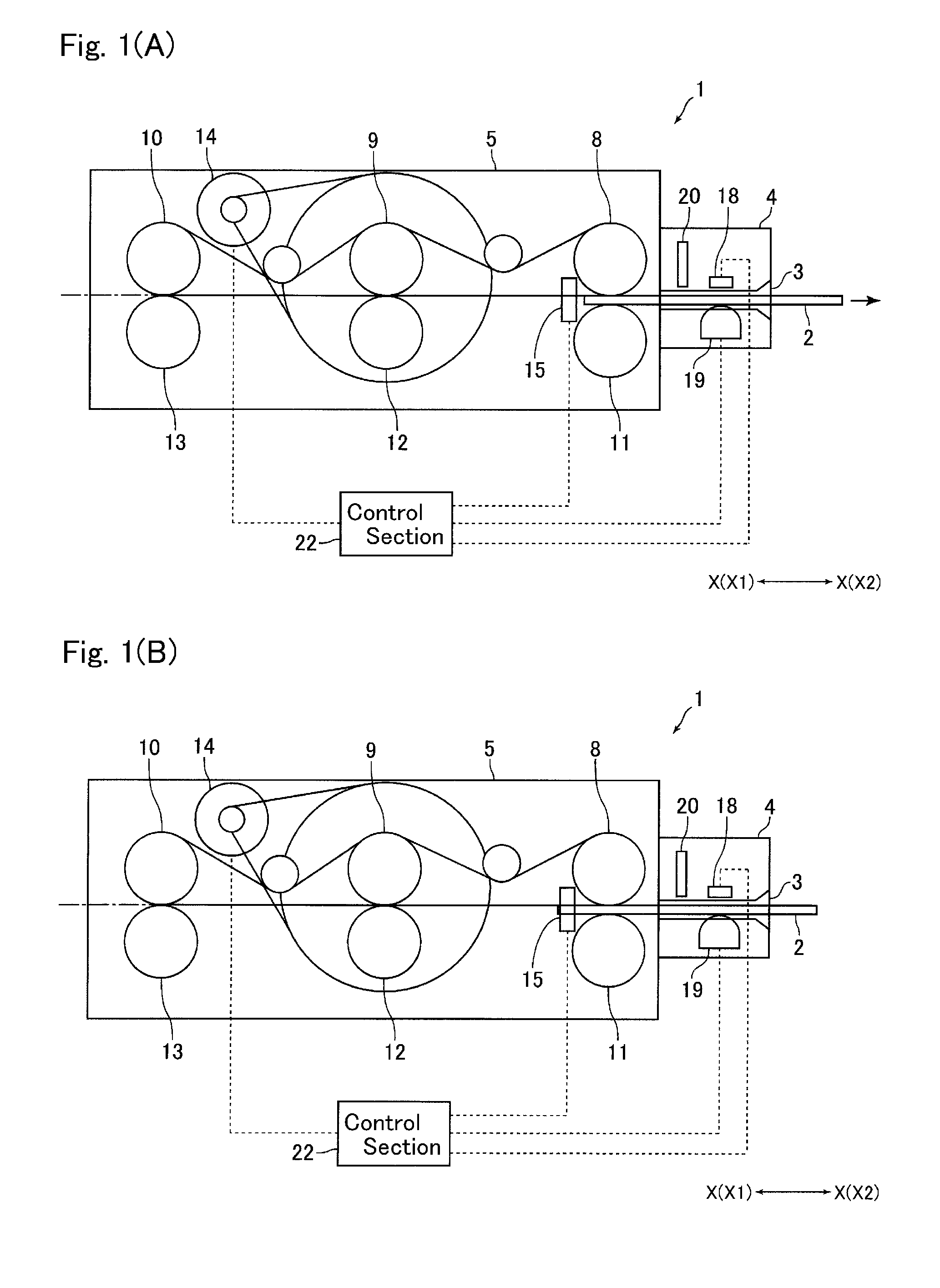
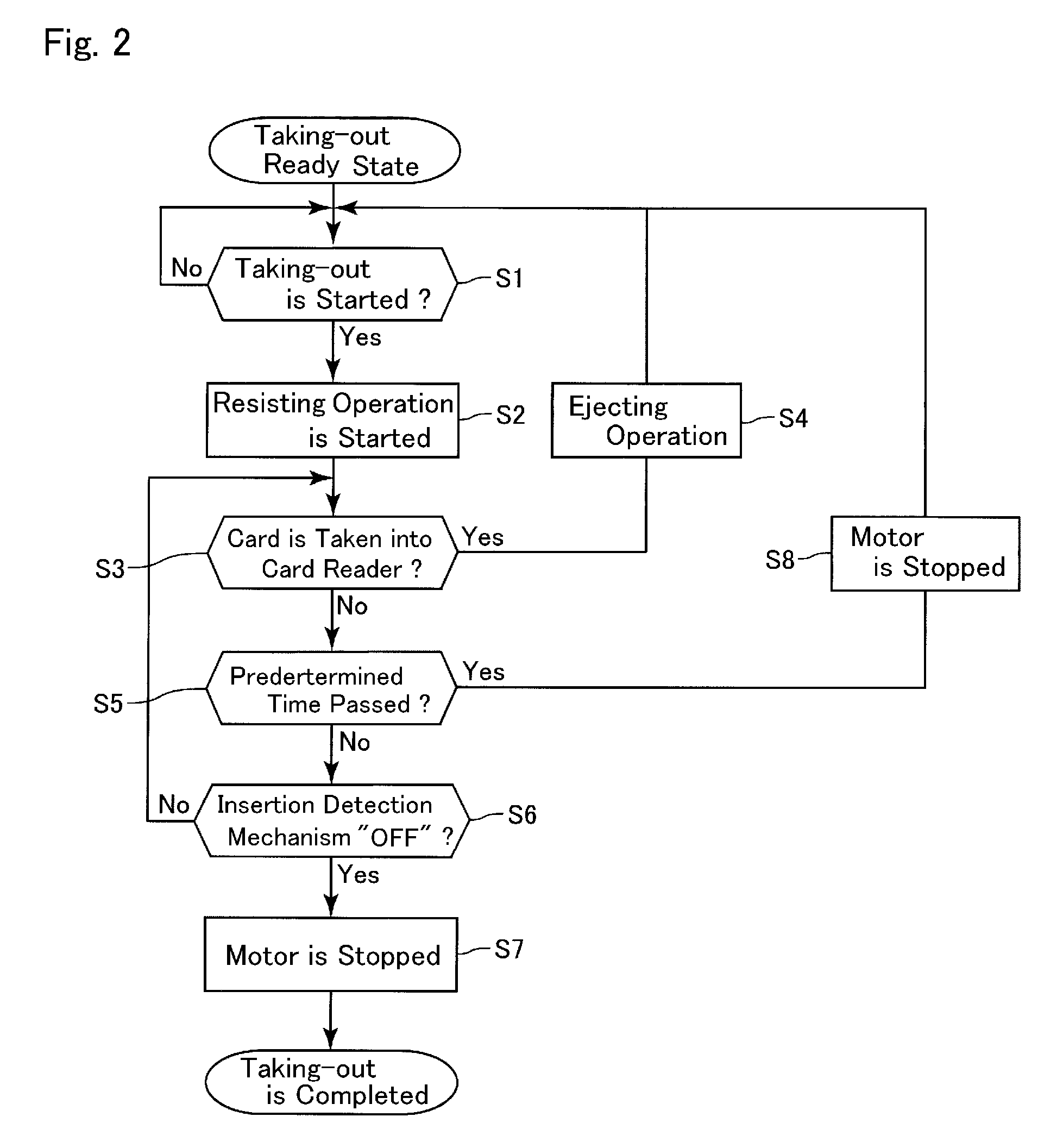
ActiveUS20140008438A1Significant data is preventedAvoid timeConveying record carriersSensing record carriersSoftware engineeringCard reader
A card reader includes a taking-out detection mechanism for detecting taking-out of a card from a taking-out ready state, which is a state that a part of the card is protruded from the card insertion-and-ejection port to an outer side of the card reader so that the card is capable of being taken out from the card reader, and a resistance applying mechanism structured to abut with the card taken out from the card reader to apply a frictional resistance to the card so as to disturb taking-out of the card. The resistance applying mechanism may include a feed roller configured to feed the card in a direction ejecting the card from an inside of the card reader until the taking-out ready state and, when start of taking-out of the card from the taking-out ready state is detected by the taking-out detection mechanism, the feed roller may be temporarily rotated in a direction taking the card into the card reader.
Owner:SANKYO SEIKI MFG CO LTD
Processing method for drawing lottery safely by a two-dimensional code
InactiveCN109492718APrevent skimmingRun Promotions SafelyLottery apparatusCo-operative working arrangementsWeb siteProgramming language
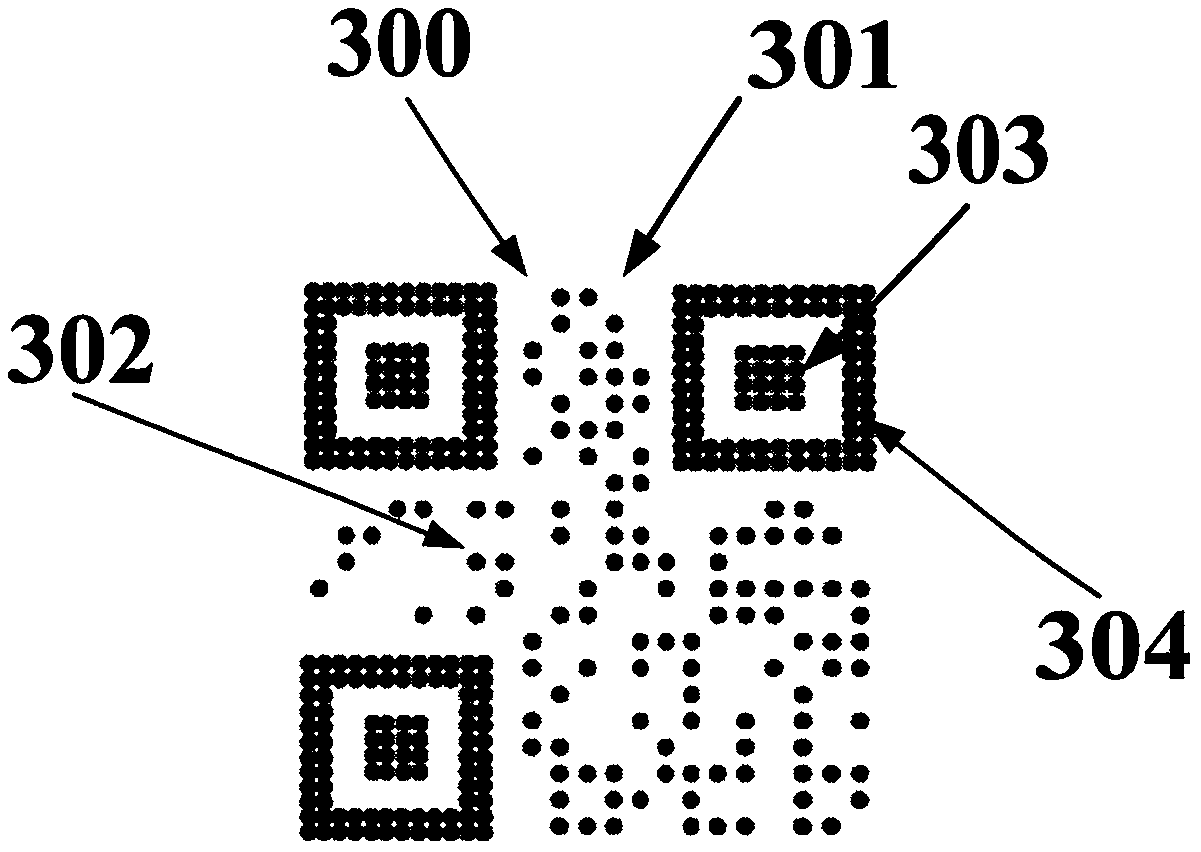
The invention relates to a processing method for drawing lottery safely by a two-dimensional code in the information processing field, characterized in that: the lottery code value is separated from the two-dimensional code image, the lottery code value is stored in the web site of the server guided by the two-dimensional code image by the user through a program after the two-dimensional code image is processed, and the correspondence between the lottery code value and the two-dimensional code image is realized through random binding of the program at least once. The advantages and positive effects of the present invention are: the method can enable consumers to read the two-dimensional code by using a mobile phone, the invention can prevent the code from being illegally read in the code assignment link, can also prevent the merchant from suffering losses due to the internal leakage of the code information, and can prevent the lawless from extrapolating a large number of lottery codesthrough a small number of code values to carry out the illegal behavior of network sales, so as to ensure that the merchant can safely carry out the promotion activities.
Owner:天津市阿波罗信息技术有限公司
Label constructing method for labeling at low-lying parts of deeply recessed containers
InactiveCN108364056APrevent skimmingAvoid pollutionVisual representatino by photographic printingRecord carriers used with machinesAdhesiveEngineering
The invention relates to a label constructing method for labeling at low-lying parts of deeply recessed containers. The label constructing method is characterized in that in order to prevent a two-dimensional code on a packaging container from being read through stealing before a consumer purchases a product, improve code identification sensitivity and prevent the product in the container from being contaminated by printing ink, the adopted label structure for the deeply recessed containers is formed by the steps of: arranging optically readable code on the back surface of a transparent thin film, and printing a background printing ink layer on the code, wherein the size of the background printing ink is larger than the code area and is smaller than a die cutting portion or the low-lying parts of the deeply recessed containers; spraying a non-setting adhesive layer larger than the background area on the background printing ink layer; and spraying a silicone oil on the non-setting adhesive, and adhering a protective layer on the silicone oil. The label constructing method can realize high-speed mass tagging on bottle caps or deeply recessed containers which are generally impossibleto be tagged, and can prevent the food and beverage from being contaminated by the printing ink.
Owner:天津市阿波罗信息技术有限公司
System And Method For Protection Against Skimming Of Information From Contactless Cards
InactiveUS20110042134A1Opportunities decreasePrevent intrusionEnvelopesConnecting packagesPaymentEngineering
Contactless payment cards with on-card microchips are transported in mailers with RF shielding. The RF shielding is designed to prevent communication with and skimming of information from the contactless cards enclosed in the mailers while in transit.
Owner:MASTERCARD INT INC
Card feed unit, read out unit, ATM and method
InactiveUS8870072B2Effective preventionAvoid creatingComplete banking machinesConveying record carriersCredit cardComputer hardware
The present invention relates to a card feed unit for transferring a data carrier of card information of a multi-services cards, such as a bank card or credit card, to a reading head of a reading unit for at least reading out of card information, the card feed unit comprising: attachment means for attaching the card feed unit in an arrangement respective of the reading head that is suitable for transporting the data carrier of the card in the direction of the meeting head, a receipt position for receipt of the card, a transfer assembly for transferring the card by means of the transfer assembly in the direction of the reading head, in which: the card feed unit is suitable for, during insertion of the card in the receipt position, receiving the card in the receipt position by means of an insertion operation with a direction of movement that, at least as seen in one direction, is substantially perpendicular to the readout direction of the card for preventing that the card is readable during the insertion operation.
Owner:CARD SWIPE PROTECTION TECH
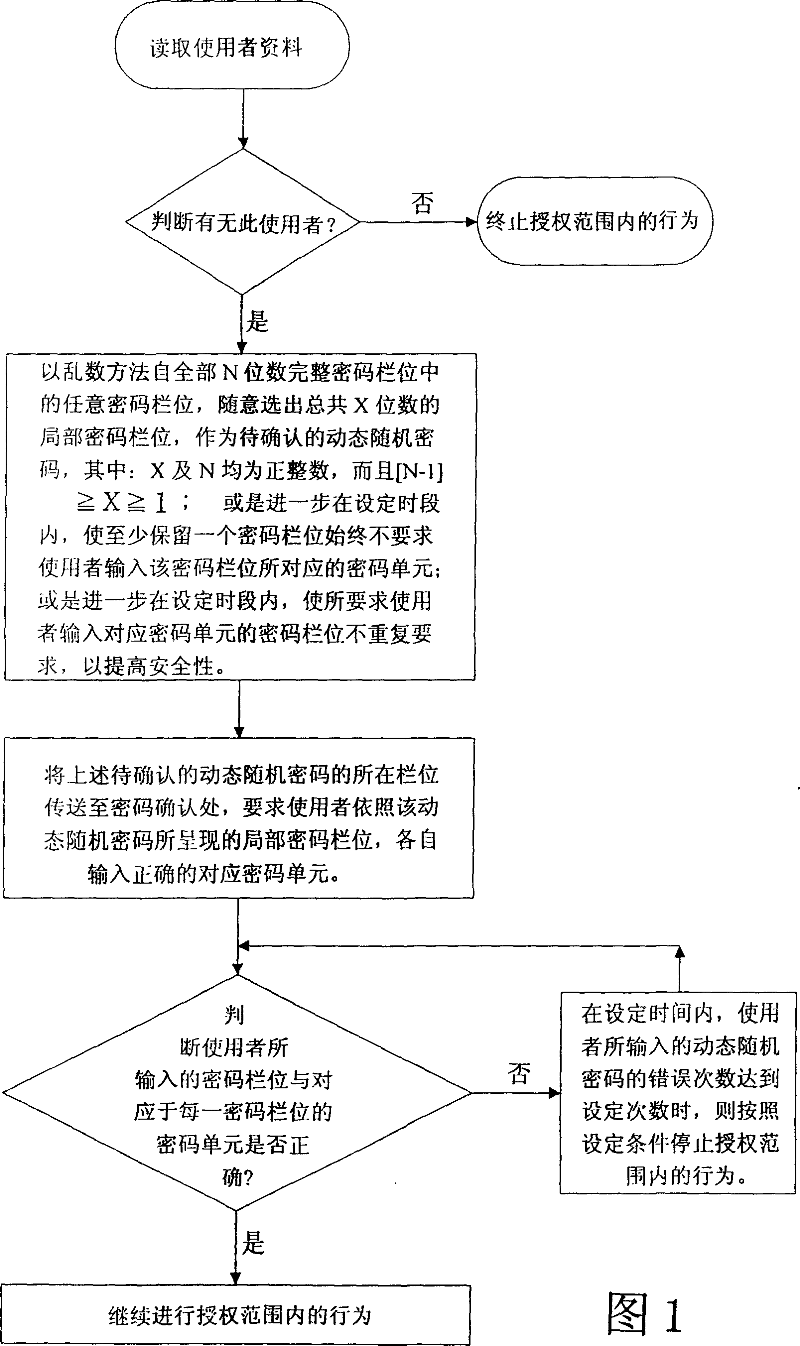
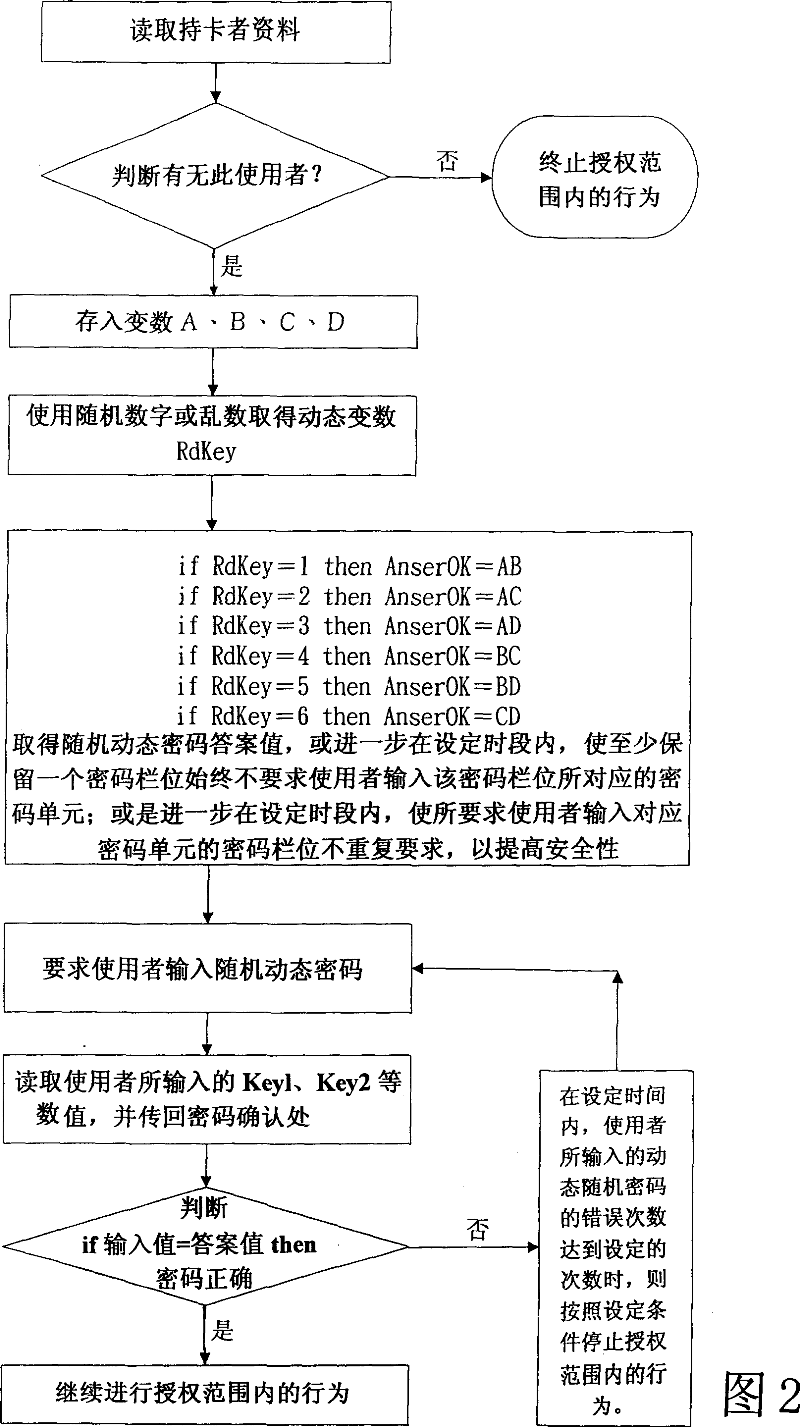
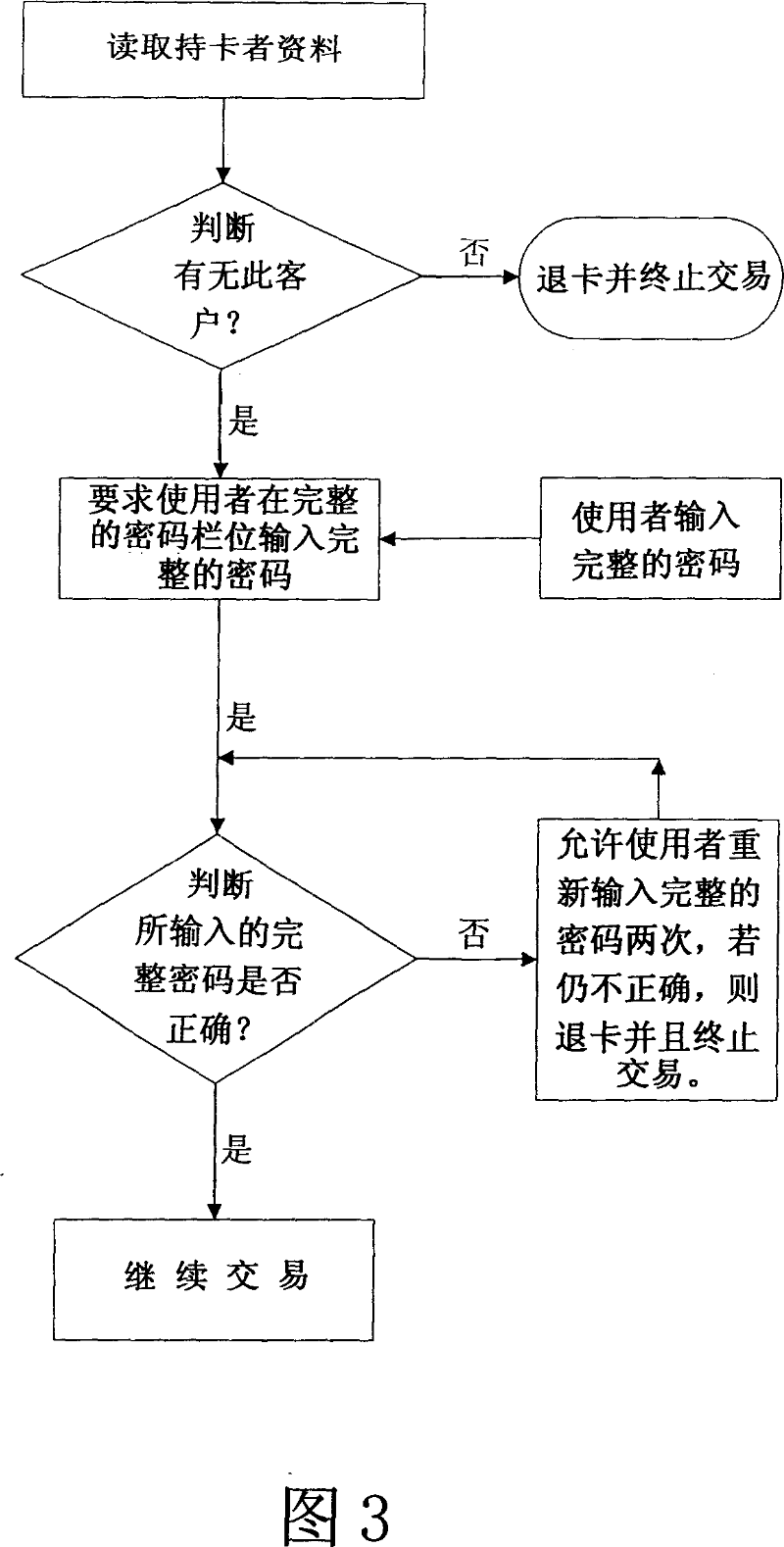
Dynamic safe identification/behavior confirming method
InactiveCN101038609AImprove securityPrevent skimmingAcutation objectsDigital data authenticationHabitPassword
A dynamic safety identity / behavior confirming method comprising the steps of: selecting an X-bit password column from an N-bit complete password column arbitrarily as a dynamic random password to be confirmed, then transmitting the dynamic random password column to be confirmed to the password comparison unit and demand the user the input the correct correspondent password according to the presented local password column, judging the input password column is correct or not, if correct, then the behavior inside the authoritative range will be allowed to conduct, if not, the n the behavior inside the authoritative range will be declined. The invention can increase the safety on the identity / behavior confirmation greatly and prevent against the theft, the using habit does not change greatly thus it is easy to implement and promote.
Owner:詹万均 +1
Method for directly spraying codes at low-lying parts of deeply recessed containers
InactiveCN108364040APrevent skimmingSolve the urgent needs of printingDuplicating/marking methodsVisual presentation using printersFood safetyEngineering
The invention relates to a method for directly spraying codes at low-lying parts of deeply recessed containers. The method is characterized in that: in order to prevent a two-dimensional code on a packaging container from being read through stealing before a consumer purchases a product, address the urgent needs of spraying codes at bottle caps or inner side bottom parts of the deeply recessed containers and take food safety into account, a protective thin film is sprayed on printed printing ink; and in order to improve identification sensitivity of the codes and be adapt to bottle caps or thedeeply recessed containers of different colors, background color spraying or printing is carried out at the inner side bottom parts of the bottle caps or the deeply recessed containers. The method can realize high-speed mass tagging on the bottle caps or deeply recessed containers which are generally impossible to be tagged.
Owner:天津市阿波罗信息技术有限公司
Card reader
InactiveUS20180196971A1Reduce the numberReduce sizeComplete banking machinesCoin countersEngineeringCapacitor
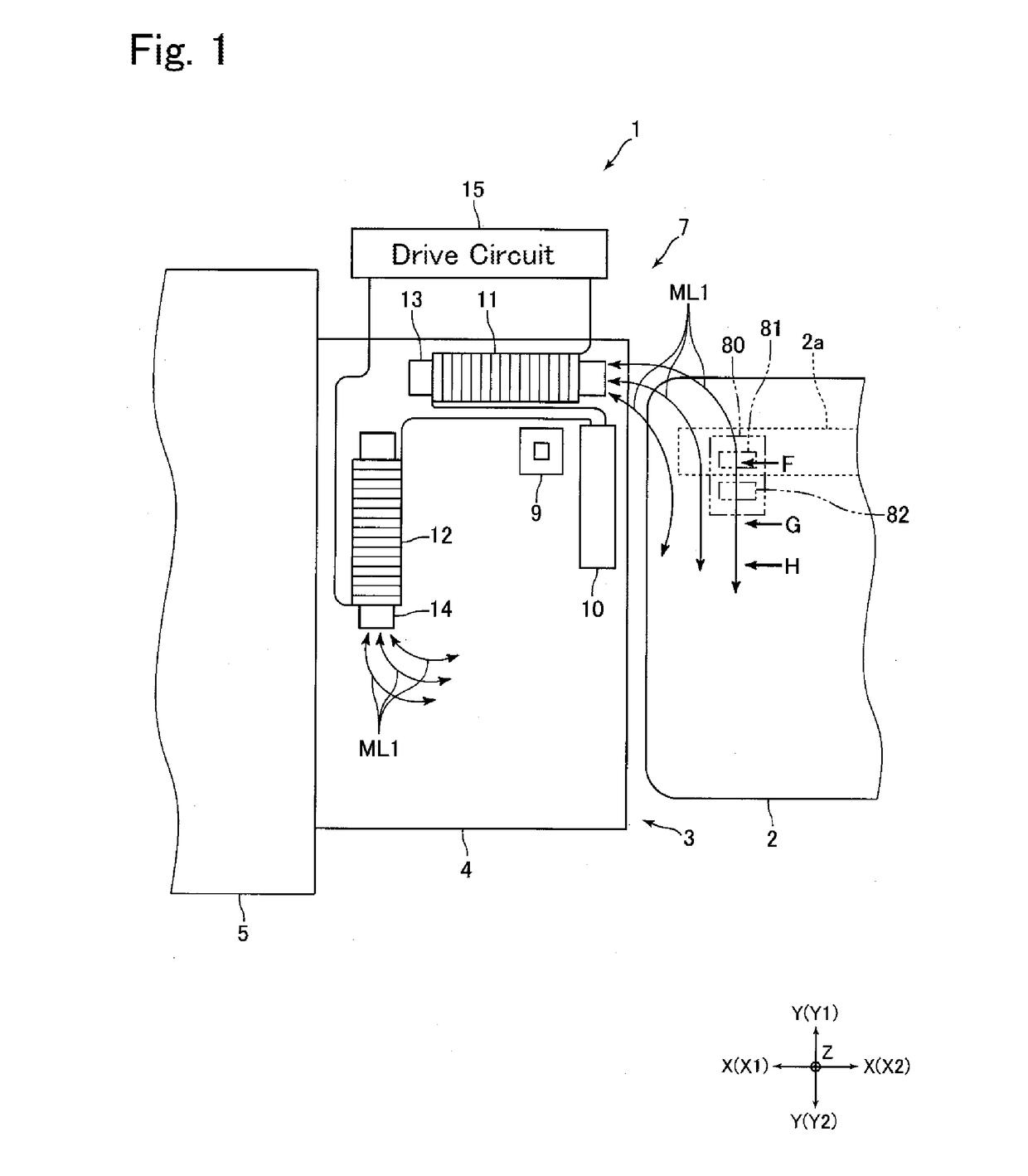
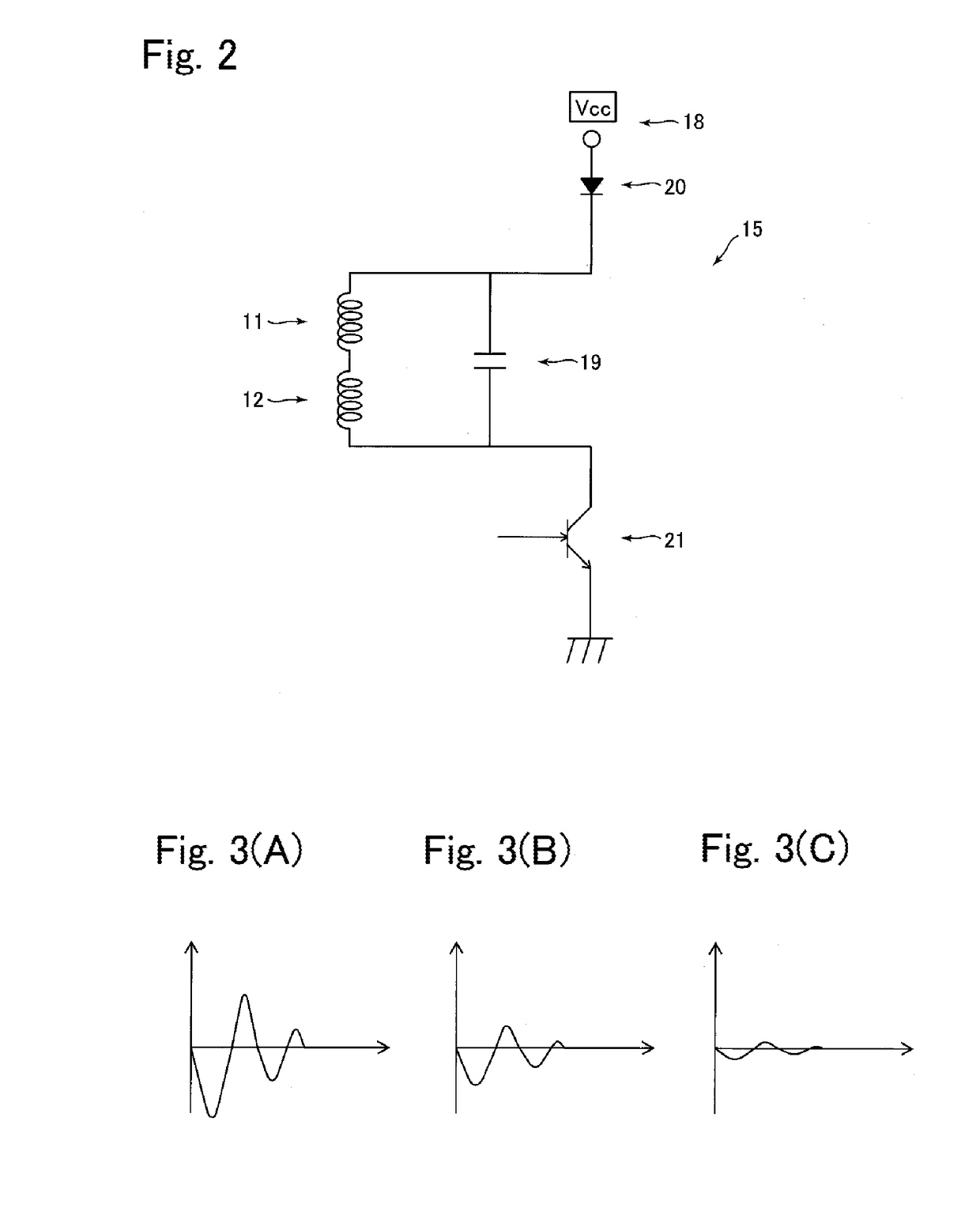
A card reader for use with a card having a magnetic stripe may include a card insertion port into which the card is inserted; a card passage along which the card is passed; and a disturbing magnetic field generation means structured to generate a magnetic field for disturbing illegal reading of magnetic data recorded in the magnetic stripe. The disturbing magnetic field generation means may include a plurality of coils which are serially-connected with each other; a capacitor connected in parallel with the plurality of the coils; and a drive circuit structured to supply an electric current to the plurality of the coils.
Owner:SANKYO SEIKI MFG CO LTD
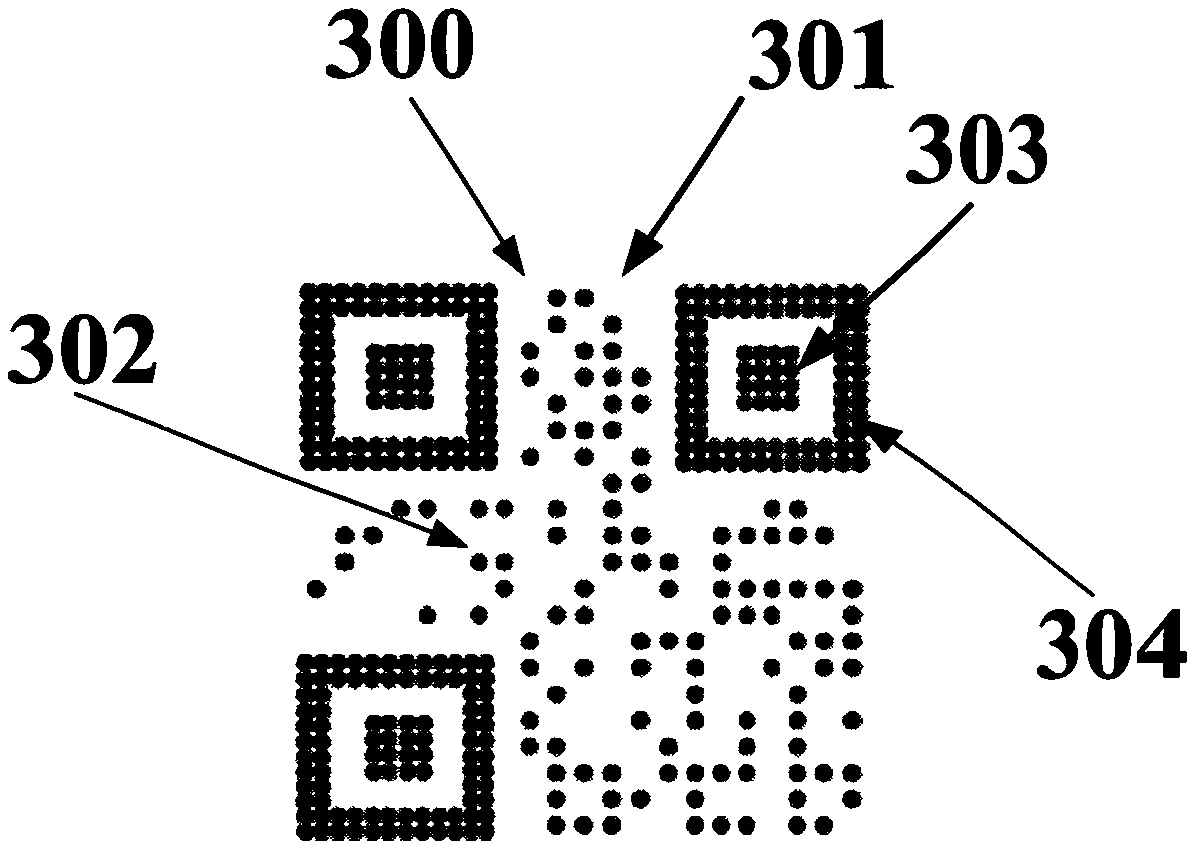
Implementation method and system for preventing illegal swiping of pseudo-dynamic two-dimensional code
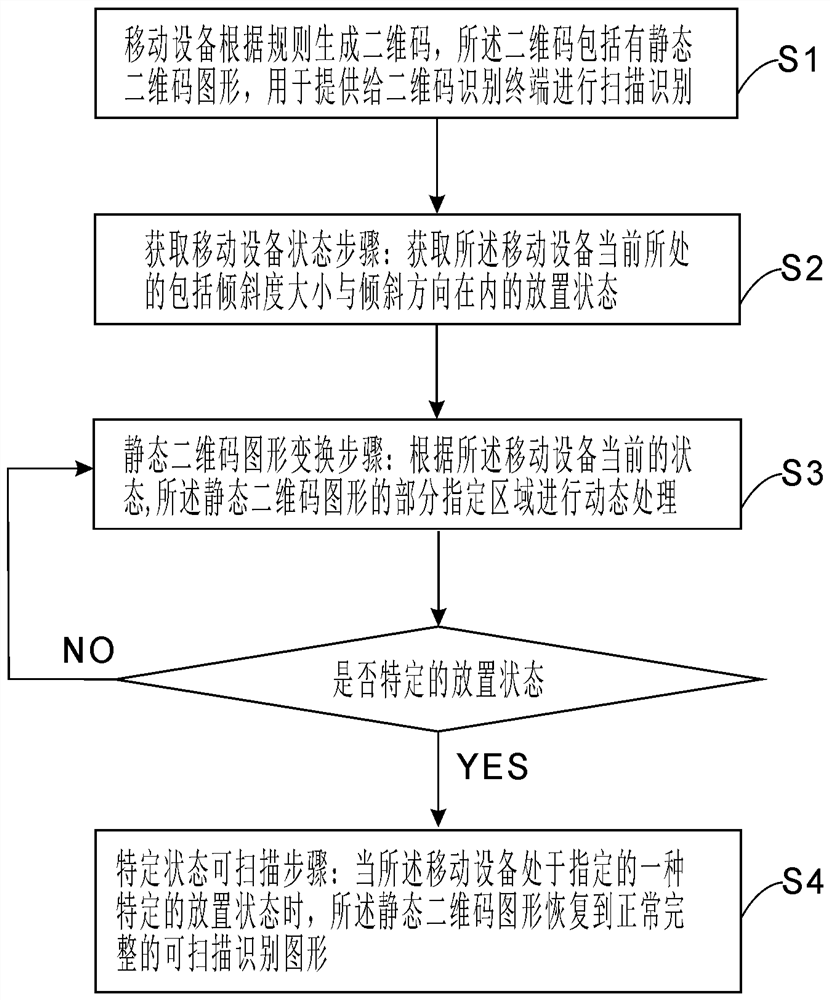
InactiveCN111931890AGuaranteed validityReduce processingRecord carriers used with machinesAlgorithmTheoretical computer science
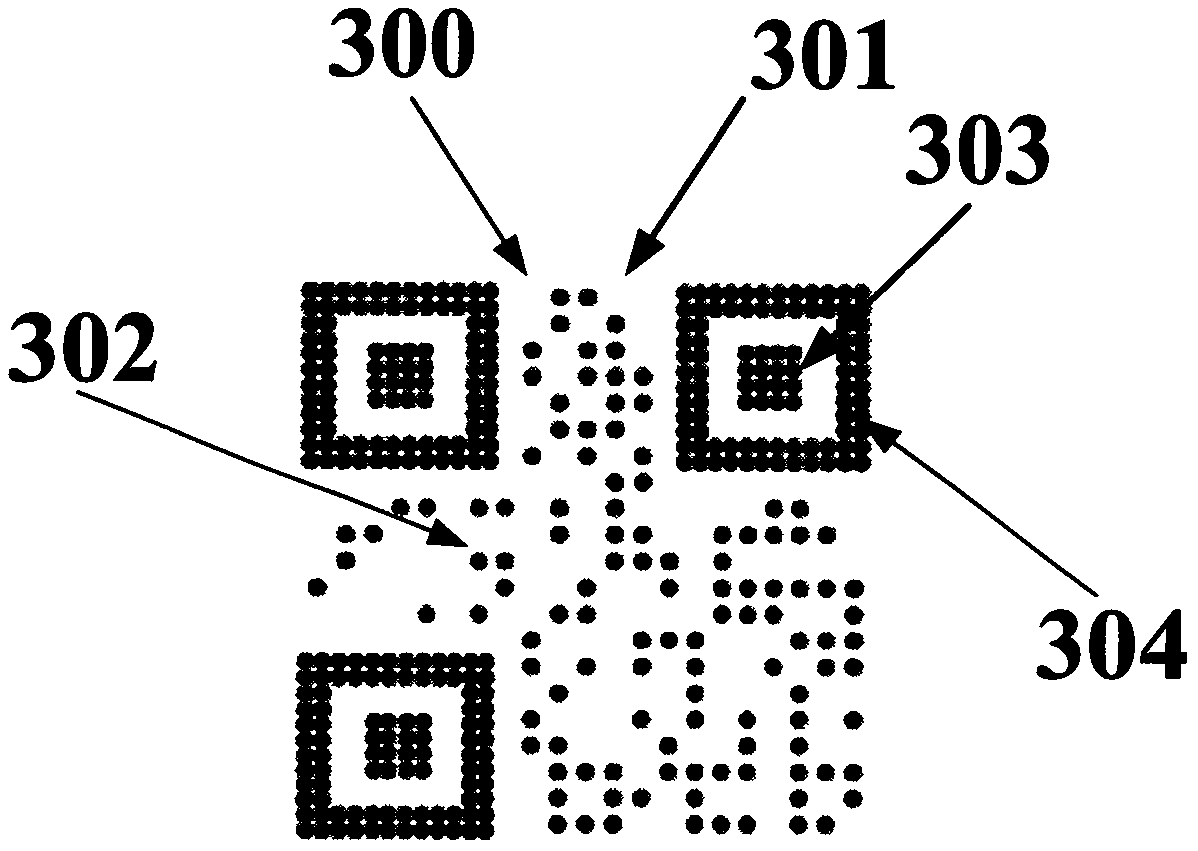
The invention provides an implementation method for preventing illegal swiping of a pseudo-dynamic two-dimensional code. On the premise that a two-dimensional code does not need to be dynamically generated again, the purpose of preventing illegal swiping is achieved through dynamic transformation of a local area of a static two-dimensional code graph, and the method comprises the following steps that S1, a mobile device generates the two-dimensional code according to a rule, and the two-dimensional code comprises the static two-dimensional code graph; s2, obtaining the current placement stateof the mobile equipment, including the inclination degree and the inclination direction; s3, performing dynamic transformation on a part of designated area of the static two-dimensional code graph according to the current state of the mobile equipment; and S4, when the mobile device is in a specified specific placement state, recovering the static two-dimensional code graph to a normal and complete scannable recognition graph.
Owner:福州智闽科技有限公司
Intelligent card and verification method thereof
PendingCN111695912AImplement password verificationEnsure safetyProtocol authorisationPasswordFinancial transaction
The invention provides an intelligent card and a verification method thereof. The intelligent card comprises a sensing module and an intelligent chip with card transaction information, the sensing module is composed of a plurality of sensing units which are distributed at intervals, when one group of sensing units in the sensing module is triggered, a verification password is generated, and afterthe verification password is verified, the card transaction information is interacted; according to the intelligent card, password verification is carried out on the non-contact intelligent card withthe quick pass function, and the safety of the intelligent card is ensured.
Owner:INVENTECSHANGHAI TECH +2
Encryption method based on USB interface
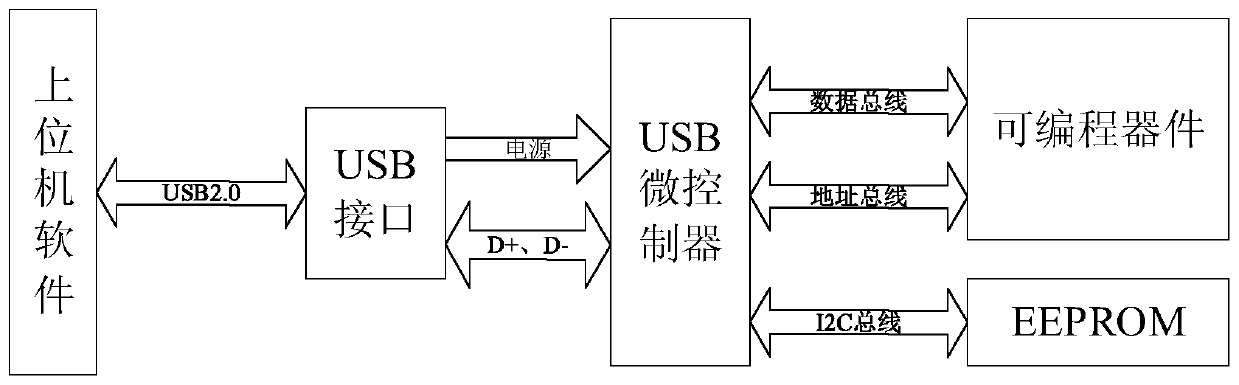
ActiveCN111222183APrevent skimmingPrevent copyingInternal/peripheral component protectionEnergy efficient computingMicrocontrollerProgrammer
The invention relates to an encryption method based on a USB interface, which comprises the following steps of: electrifying equipment, electrifying a USB encryption card, re-enumerating a USB and waiting for an instruction; judging whether timing time is up or not; sending, by an upper computer, an SETUP token to the USB encryption card; analyzing, by a USB microcontroller, the token, and selecting, by the upper computer, data and an algorithm for operation according to the wValue and wIndex which are randomly generated; judging whether the instruction code is a control code or not, and if yes, sending the wValue and wIndex to a programmable device; transmitting, by the programmable device, an operation result to the USB microcontroller; transmitting, by the programmable device, an operation result to the USB microcontroller; and comparing, by the upper computer, the operation results, and if the comparison is correct, executing other logic functions. According to the method, a randomnumber is used for generating an encryption effect, the design is simple, a complex encryption algorithm is not needed, but cracking is difficult, and the effect of software protection is effectivelyachieved.
Owner:TIANJIN JINHANG COMP TECH RES INST
manual card reader
ActiveCN103824042BPrevent skimmingCo-operative working arrangementsSensing by electromagnetic radiationEngineeringCard reader
A manually operated card reader can prevent skimming when a card is inserted and can move a magnetic head to read magnetic information of the card without using an actuator. The manually operated card reader (101) has an insertion opening (1a) allowing a card (C) to be inserted in a short edge direction (X), a magnetic head (2) reads magnetic information from a magnetic stripe (Cs) which is configured to extend in a long edge direction (Y) in the card (C), and a magnetic head moving mechanism (10). The magnetic head moving mechanism (10), through an inserting force when the card (C) is inserted in the short edge direction (X) from the insertion opening (1a), enables the magnetic head (2), in a state of being in contact with the magnetic stripe (Cs), to be moved from one end of the magnetic stripe (Cs) in the long edge direction (Y) in the card (C) to the other end.
Owner:HITACHI OMRON TERMINAL SOLUTIONS CORP
Method and device for processing web application programs
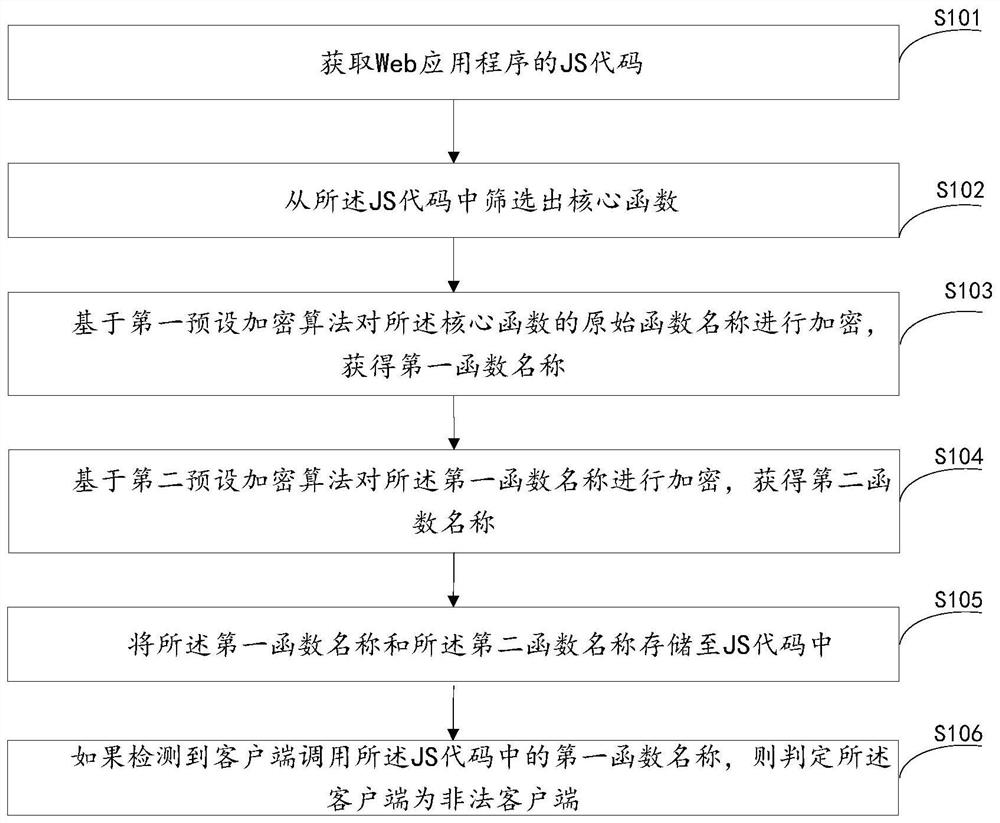
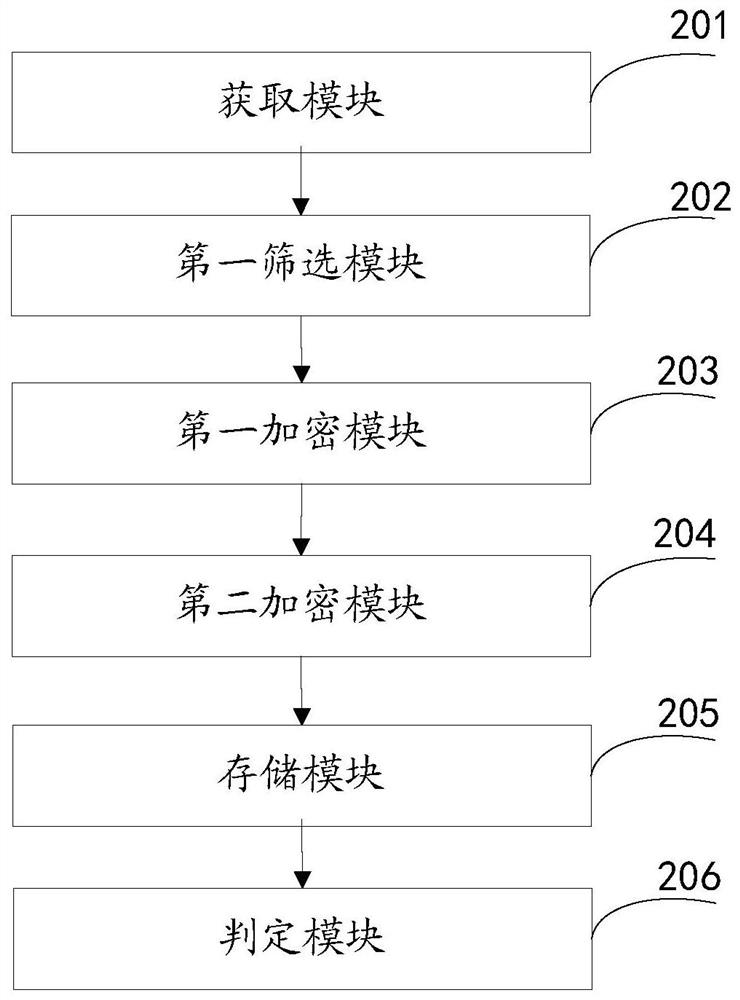
ActiveCN110032833BEnsure safetyAvoid gettingDigital data protectionProgram/content distribution protectionProgramming languageCore function
The embodiment of the present invention provides a method and device for processing a Web application, wherein the method includes: obtaining the JS code of the Web application; screening out the core function from the JS code; Encrypt the original function name of the core function to obtain a first function name; encrypt the first function name based on a second preset encryption algorithm to obtain a second function name; combine the first function name and the second function name The second function name is stored in the JS code; if it is detected that the client calls the first function name in the JS code, it is determined that the client is an illegal client. The method of the invention solves the technical problem that illegal clients cannot be detected in the prior art.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Card reader and control method therefor
ActiveUS9081993B2Prevent skimmingConveying record carriersSensing record carriersCard readerFrictional resistance
A card reader includes a taking-out detection mechanism for detecting taking-out of a card from a taking-out ready state, which is a state that a part of the card is protruded from the card insertion-and-ejection port to an outer side of the card reader so that the card is capable of being taken out from the card reader, and a resistance applying mechanism structured to abut with the card taken out from the card reader to apply a frictional resistance to the card so as to disturb taking-out of the card. The resistance applying mechanism may include a feed roller configured to feed the card in a direction ejecting the card from an inside of the card reader until the taking-out ready state and, when start of taking-out of the card from the taking-out ready state is detected by the taking-out detection mechanism, the feed roller may be temporarily rotated in a direction taking the card into the card reader.
Owner:SANKYO SEIKI MFG CO LTD
Packaging container constructive method for directly spraying codes to low-lying portions of concave deep containers
InactiveCN108357777AHigh recognition sensitivityPrevent skimmingClosure with auxillary devicesVisual representation by matrix printersEngineeringGraphics
The invention relates to a packaging container constructive method for directly spraying codes to the low-lying portions of concave deep containers. The method is characterized in that in order to prevent two-dimensional codes on packaging containers from being read wrongfully before consumers purchase commodities and prevent ink from contaminating the commodities in the containers, the adopted packaging container constructive method for spraying the codes to the low-lying portions of the concave deep containers comprises the steps that the spray-printed optical readable computer graphic codesare on the surfaces of the low-lying portions of the concave deep containers, each code is covered with a protection film in a spraying manner, and a large number of codes can be sprayed to common bottle caps or concave deep containers at a high speed, wherein codes are impossible to be sprayed to the common bottle caps or concave deep containers.
Owner:天津市阿波罗信息技术有限公司
Steam extractor device, kitchen appliance having a hob section and a steam extractor device, and method for operating a steam extractor device
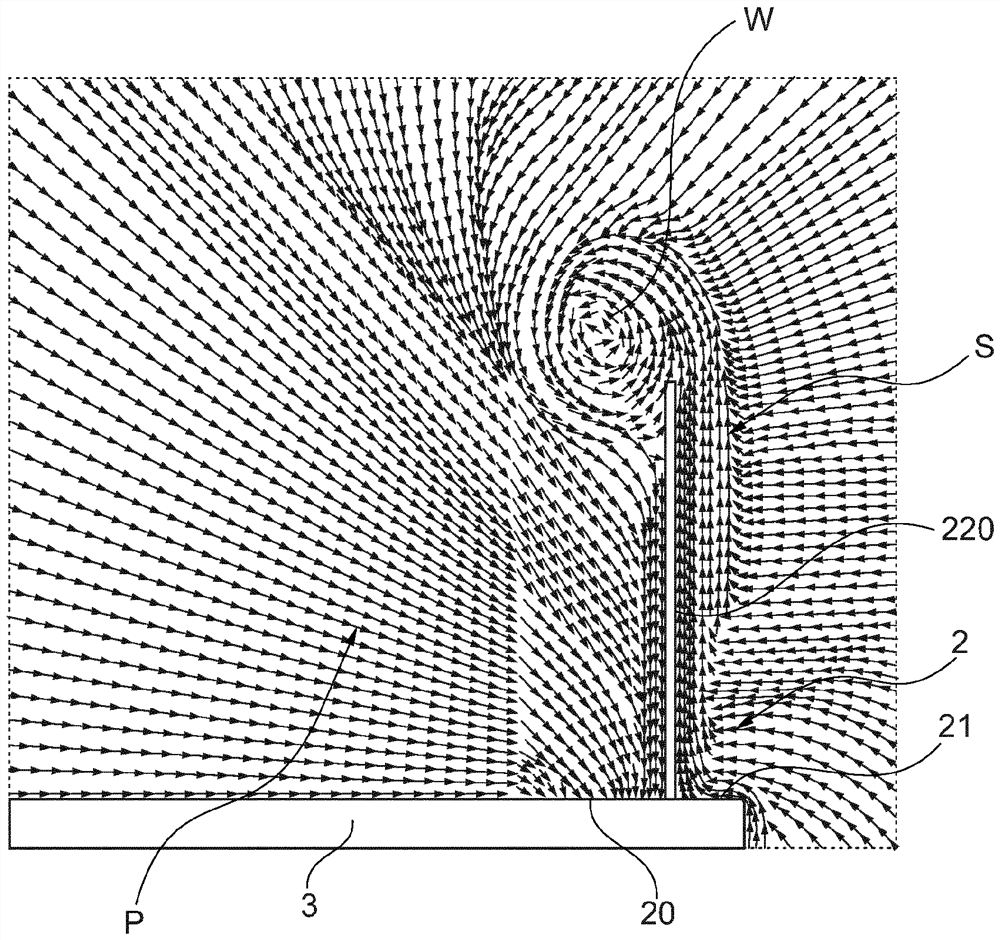
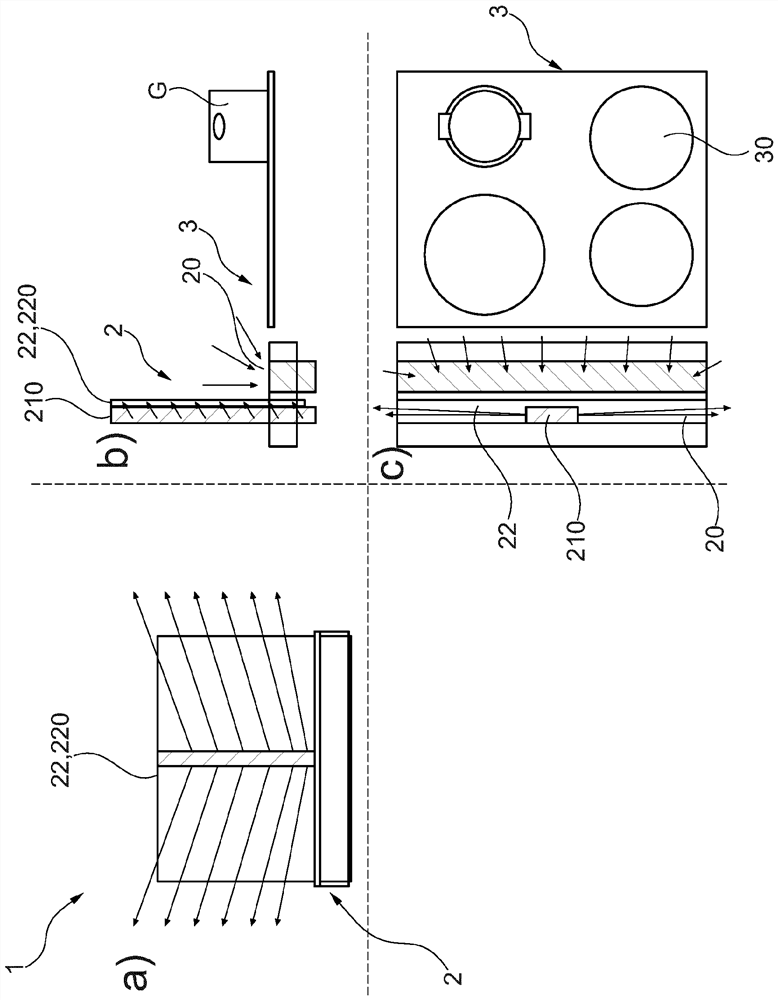
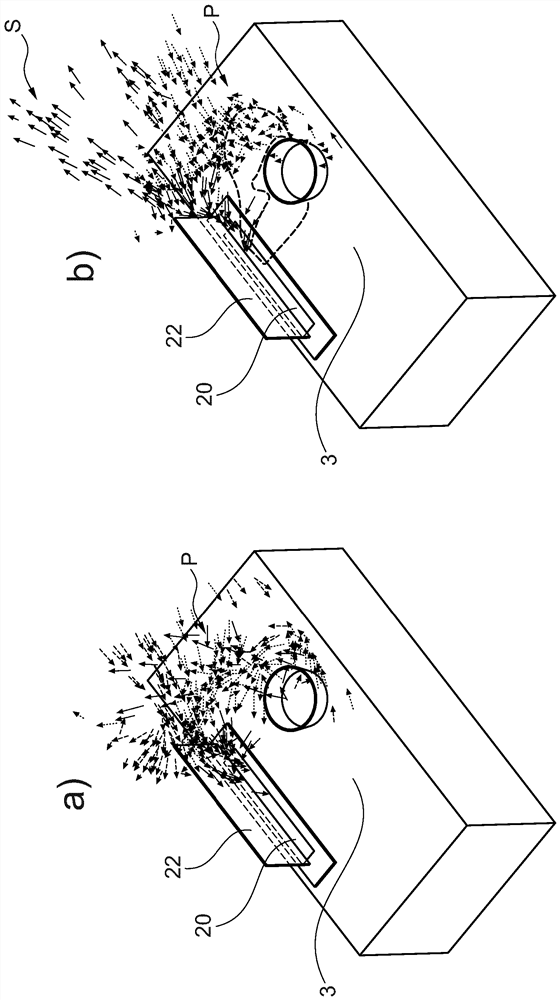
PendingCN113785161APrevent escapePrevent skimmingDomestic stoves or rangesLighting and heating apparatusThermodynamicsKitchen utensils
The present invention relates to a steam extractor device having a suction opening (20) and, arranged under the suction opening (20), a fan by means of which the primary air (P) is drawn downward via the suction opening (20), the steam extractor device being characterized in that the steam extractor device (2) has at least one expulsion opening (21) which is adjacent to the suction opening (20) and via which an oriented secondary air stream (S) is expelled. The invention furthermore relates to a kitchen appliance (1) having at least one such steam extractor device (2) and a method for operating such a steam extractor device (2).
Owner:BSH BOSCH & SIEMENS HAUSGERAETE GMBH
Fold-line-shaped and fan-shaped biaxial rotary sewage blocking and sewage cleaning system
InactiveCN102535407BStructural innovationEfficient cleaningArtificial water canalsTransmission beltMonitoring system
The invention relates to a fold-line-shaped and fan-shaped biaxial rotary sewage blocking and sewage cleaning system, which belongs to the field of water conservancy project facilities and comprises a vertical sewage blocking fence, a fold-line-shaped sewage blocking fence, a fan-shaped sewage blocking fence, a fence difference monitoring system a motive power device, a transmission belt, a work bridge, a sewage guide plate and bearings, wherein the fence difference monitoring system consists of an upstream water level sensor and a downstream water level sensor, and the bearings are used for respectively controlling the fold-line-shaped sewage blocking fence and the fan-shaped sewage blocking fence. The upstream water level sensor and the downstream water level sensor arranged in the fence difference monitoring system are respectively connected with a remote computer system through data wires, and the remote computer system is used for automatically or manually controlling the motive power device for monitoring the water level differences in front of the vertical sewage blocking fence and behind the vertical sewage blocking fence. The sewage blocking and sewage cleaning system provided by the invention has the advantages that the sewage collection, the sewage blocking and the sewage cleaning are integrated, the problem of sewage blocking fence blockage caused by sewage blockage at water taking openings in the water conservancy project operation process is solved, the manufacture is simple, the use is convenient and reliable, in addition, the cost is low, economy and applicability are realized, the sewage collection, sewage blocking and sewage cleaning effects are ideal, and the sewage blocking and sewage cleaning system is suitable for being popularized and applied.
Owner:SICHUAN UNIV
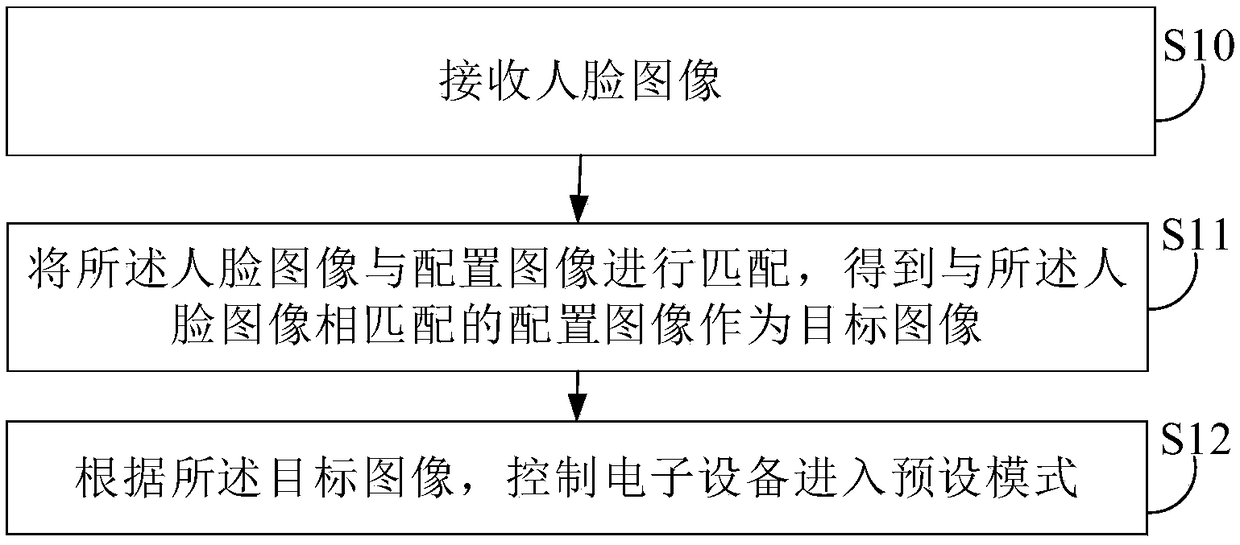
Anti-theft method and device, electronic device and compute readable storage medium
InactiveCN109086583AImprove user experiencePrevent skimmingDigital data authenticationPattern recognitionElectronic equipment
The invention provides an anti-theft method and device, an electronic device and a computer-readable storage medium. The anti-theft method comprises the following steps of: receiving a face image; matching the face image and the configuration image to obtain a configuration image matched with the face image as a target image; according to the target image, the electronic device being controlled toenter a preset mode. The invention can further restrict the access right based on face recognition, the electronic device can be controlled to enter corresponding preset mode according to different received face images, further effectively avoiding stealing behavior, and has stronger defensibility, so as to avoid unnecessary loss and bring better use experience to users.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Watermark display method and device, computer equipment and storage medium
PendingCN114004726AIncrease the difficulty of imitation and counterfeitingPrevent skimmingCharacter and pattern recognitionImage data processing detailsComputer visionComputer equipment
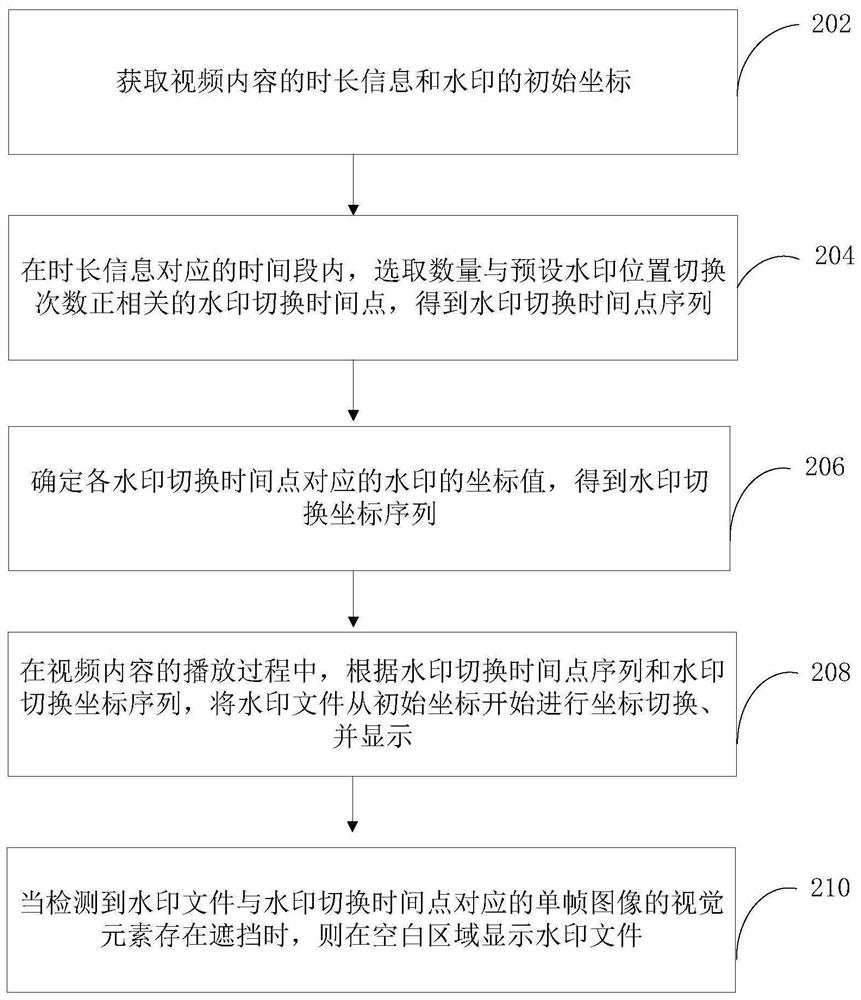
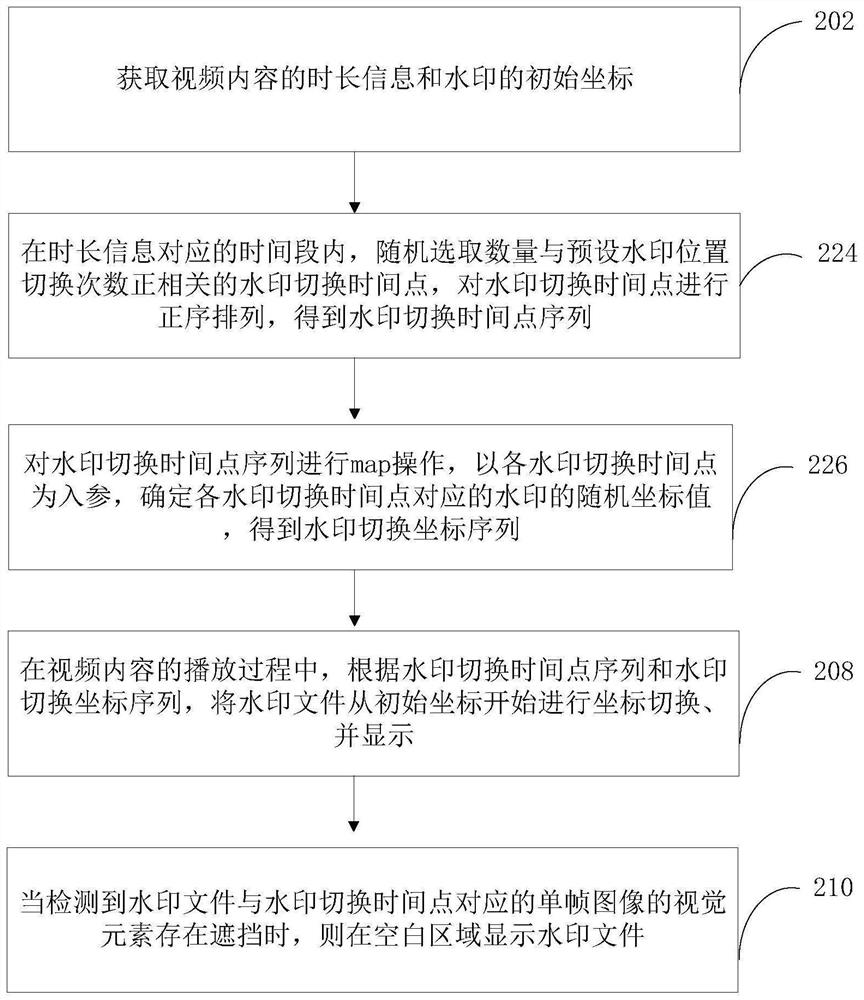
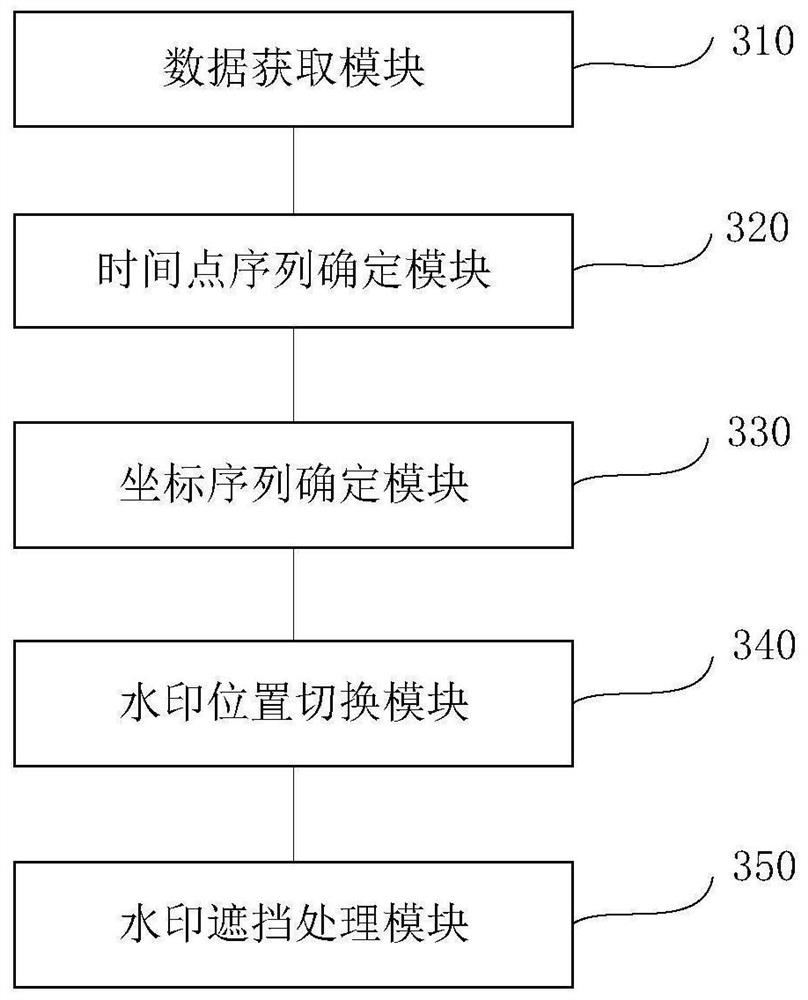
The invention relates to a watermark display method and device, computer equipment and a storage medium. The method comprises the following steps: acquiring duration information of video content and initial coordinates of watermarks, selecting watermark switching time points of which the number is positively correlated with a preset watermark position switching frequency in a time period corresponding to the duration information, obtaining a watermark switching time point sequence, determining coordinate values of watermarks corresponding to the watermark switching time points, obtaining a watermark switching coordinate sequence, performing coordinate switching on a watermark from an initial coordinate according to a watermark switching time point sequence and the watermark switching coordinate sequence in a video content playing process, displaying the watermark, and when the watermark and a visual element of a single-frame image corresponding to a watermark switching time point are detected to be shielded, displaying the watermark in a blank area. The dynamic watermark data generated by the method is high in security.
Owner:云南腾云信息产业有限公司
Card insertion and ejection mechanism and card processing device
InactiveUS10204242B2Prevent skimmingSkimming can be preventedConveying record carriersSensing record carriersTurn angleEngineering
Provided is a card insertion and ejection mechanism to be mounted forward of a card reader structured to convey a card so that a longitudinal direction of the card is coincided with a conveying direction of the card, the card insertion and ejection mechanism being capable of preventing skimming and capable of sending into the card reader the card in an orientation capable of being processed by the card reader even when the card is inserted into the card insertion and ejection mechanism in any orientation. A card insertion and ejection mechanism takes in a card to a turning position when the card is inserted into a card insertion port with front and rear sides of the card directed correctly so that a short widthwise direction of the card is coincided with an “X” direction, and controls a card turning and conveying mechanism in a turning direction and at a turning angle based on a result of determination as to an orientation of the inserted card, to turn the card. The card insertion and ejection mechanism does not take in the card when the card is inserted into the card insertion port so that a longitudinal direction of the card is coincided with the “X” direction or when the card is inserted into the card insertion port with the front and rear sides of the card directed oppositely.
Owner:SANKYO SEIKI MFG CO LTD
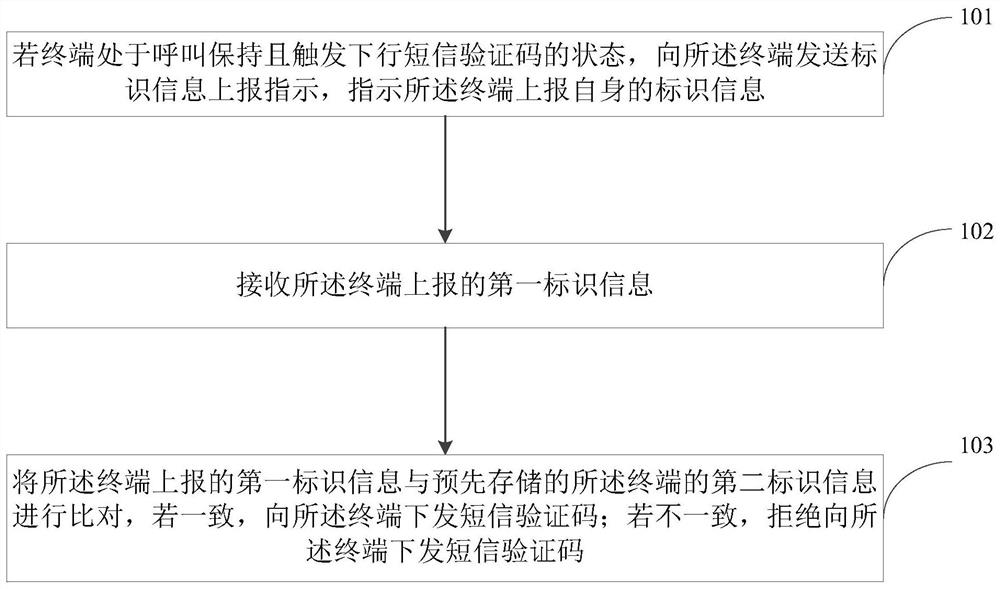
Security interception method and device
ActiveCN113556741APrevent skimmingAvoid economic lossSecurity arrangementHigh level techniquesComputer networkEngineering
The invention provides a security interception method and device, and belongs to the technical field of wireless communication. The security interception method is applied to network side equipment, and comprises the following steps: if a terminal is in a state of keeping a call and triggering a downlink short message verification code, sending an identification information reporting instruction to the terminal to indicate the terminal to report own identification information; receiving first identification information reported by the terminal; comparing the first identification information reported by the terminal with pre-stored second identification information of the terminal, and issuing a short message verification code to the terminal if the first identification information is consistent with the pre-stored second identification information of the terminal; and if not, refusing to issue the short message verification code to the terminal. The technical scheme of the invention can prevent the illegal swiping behavior after the user call is hijacked.
Owner:CHINA MOBILE COMM LTD RES INST +1
Printing method for labeling label at low-lying part of deeply recessed container
PendingCN108364041APrevent stolen readingImprove code recognition sensitivityVisual representatino by photographic printingPrinting inkAdhesive
The invention relates to a printing method for labeling labels at low-lying parts of deeply recessed containers. The printing method is characterized in that in order to prevent a two-dimensional codeon a packaging container from being read through stealing before a consumer purchases a product, improve code identification sensitivity and prevent the product in the container from being contaminated by printing ink, the printing method for labeling the labels at the low-lying parts of the deeply recessed containers is implemented by the steps of: printing an optically readable computer graph code on the back surface of a transparent thin film in a spraying mode, and arranging a non-setting adhesive layer larger than the code layer on the code layer; directly connecting the periphery of thenon-setting adhesive with the transparent thin film in a sealed manner, and at least adhering one protective layer on the non-setting adhesive; and finally performing die cutting to form a labeling label. The printing method can realize high-speed mass tagging at bottle caps or low-lying parts of deeply recessed containers which are generally impossible to be tagged, and can prevent the food andbeverage from being contaminated by the printing ink.
Owner:天津市阿波罗信息技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com