Method and device for processing web application programs
A processing method and web application technology, applied in the computer field, can solve the problem of inability to detect illegal clients, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
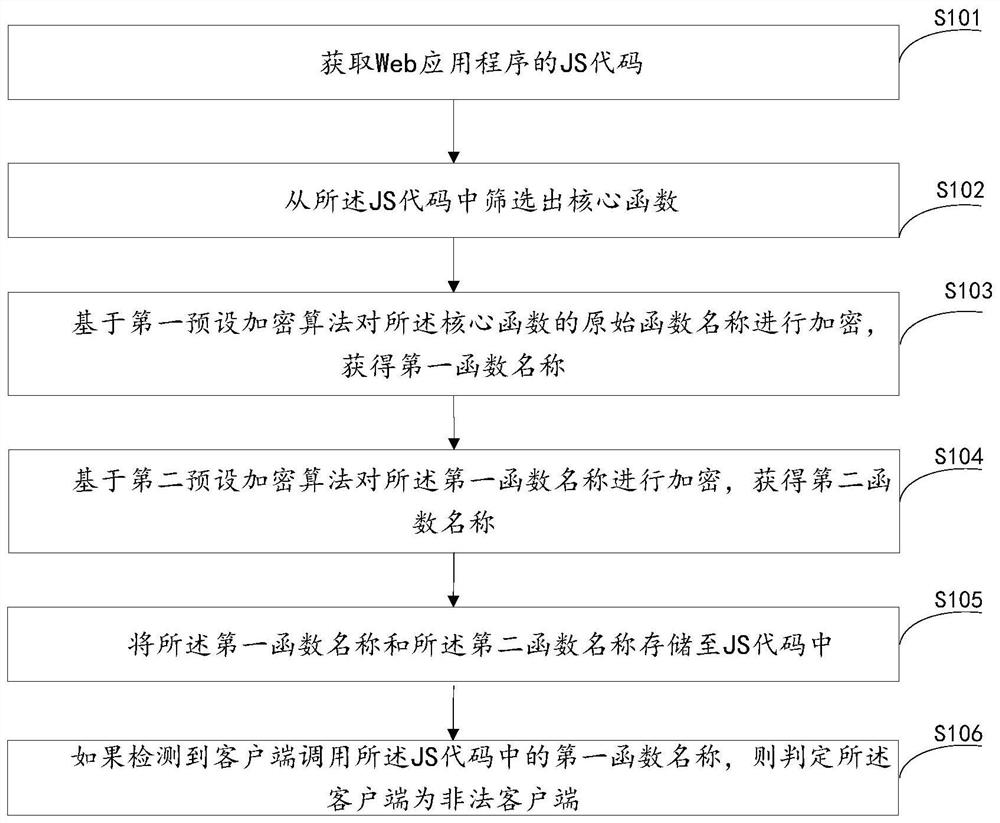
[0049] This embodiment provides a processing method for a Web application, such as figure 1 As shown, the method includes:
[0050] Step S101: Obtain the JS code of the web application.
[0051]Specifically, JS code is JavaScript code, which is a literal scripting language, and also a dynamic type, weak type, and prototype-based language with built-in support types. Usually used to write web applications.
[0052] Step S102: Filter out core functions from the JS code.
[0053] Specifically, the JS code includes implementation codes for the core functions and security functions of the web application, and these codes are implemented by using functions, that is, core functions.
[0054] In an optional implementation, in order to better conceal the core functions, this implementation will also filter out some non-core functions, and the number of non-core functions can be selected according to needs, for example, the number of core functions is 50, the number of non-core func...
Embodiment 3
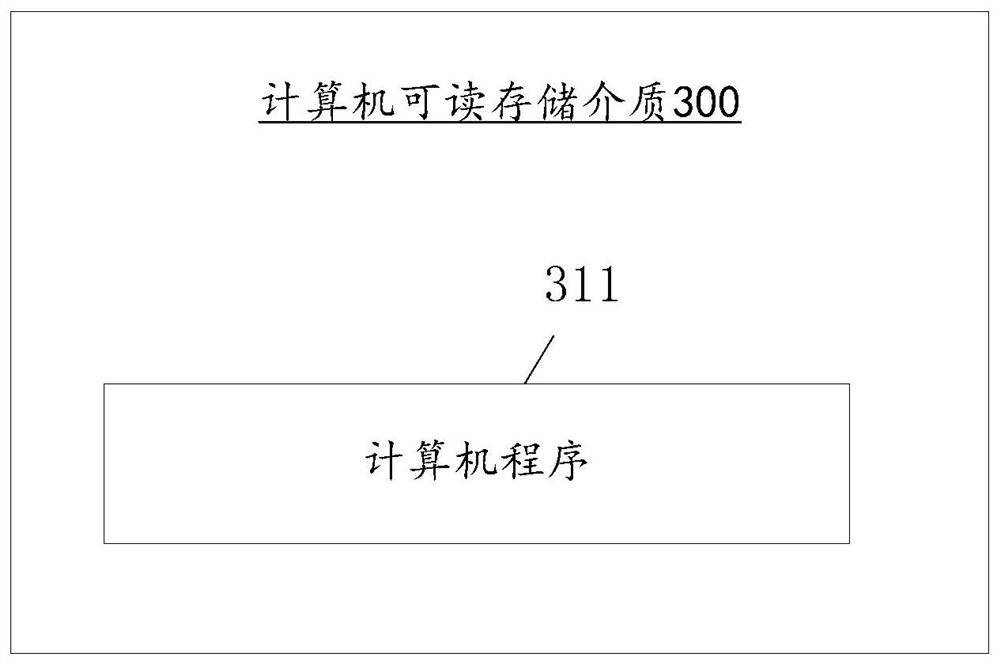
[0153] Based on the same inventive concept, the present application also provides a computer-readable storage medium 300, on which a computer program 311 is stored, and when the program is executed by a processor, the method in Embodiment 1 is realized.
[0154] Specifically, the above program is configured to perform the following steps:
[0155] Get the JS code of the web application;
[0156] Filter out core functions from the JS code;
[0157] Encrypting the original function name of the core function based on a first preset encryption algorithm to obtain a first function name;
[0158] Encrypting the first function name based on a second preset encryption algorithm to obtain a second function name;
[0159] storing the first function name and the second function name in the JS code;
[0160] If it is detected that the client calls the first function name in the JS code, it is determined that the client is an illegal client.
Embodiment 4
[0162] Based on the same inventive concept, this application also provides a kind of computer equipment, please refer to Figure 4 , including a storage 401, a processor 402, and a computer program 403 stored in the storage and operable on the processor, and the processor 402 implements the method in Embodiment 1 when executing the program.
[0163] Specifically, the above processor is configured to perform the following steps:
[0164] Get the JS code of the web application;
[0165] Filter out core functions from the JS code;
[0166] Encrypting the original function name of the core function based on a first preset encryption algorithm to obtain a first function name;
[0167] Encrypting the first function name based on a second preset encryption algorithm to obtain a second function name;
[0168] storing the first function name and the second function name in the JS code;
[0169] If it is detected that the client calls the first function name in the JS code, it is de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com