Sensitive information detection method and terminal
A technology of sensitive information and detection methods, applied in the field of network security, can solve the problems of unavailability of services, misjudgment of data, and high rate of misjudgment, saving storage space and cost, improving accuracy and efficiency, and improving accuracy. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
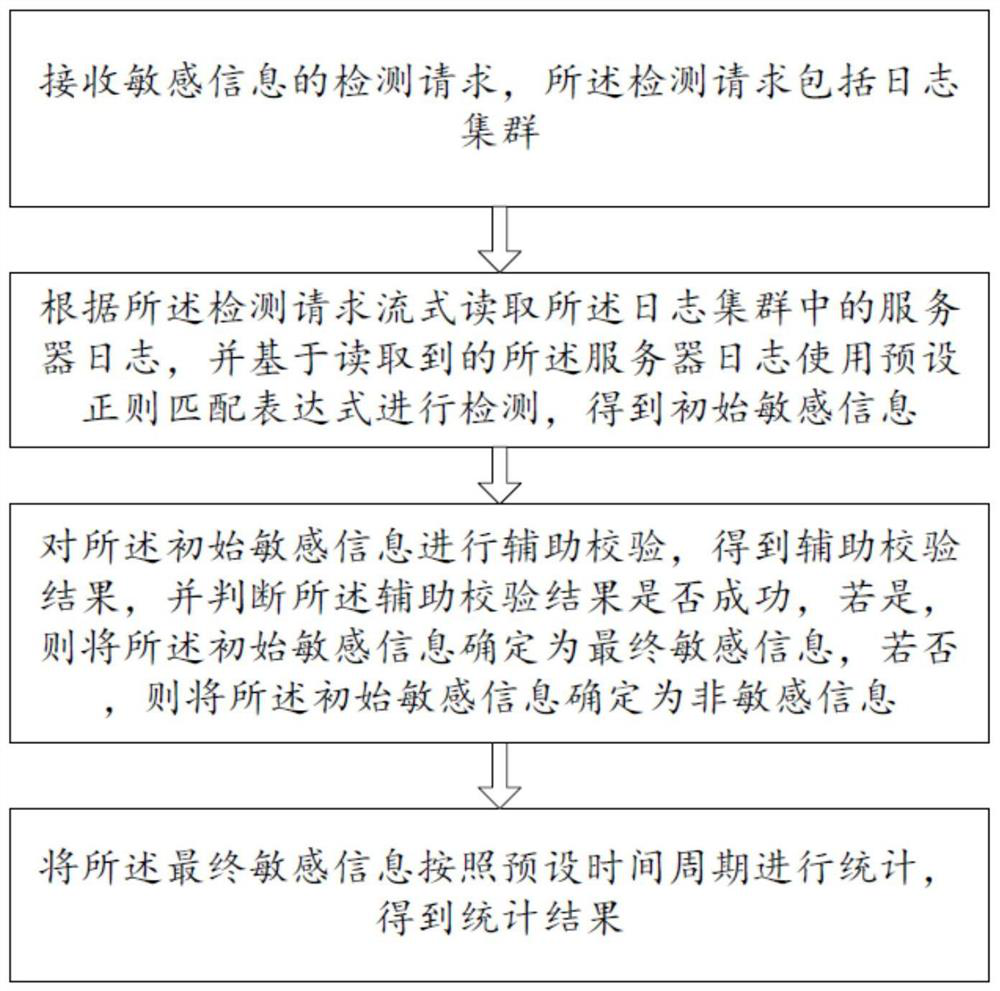
[0105] Please refer to figure 1 , 3 , a detection method for sensitive information in this embodiment, comprising:
[0106] S0. Receive a log collection instruction, where the log collection instruction includes a plurality of server information;
[0107] determining multiple servers according to the multiple server information;
[0108] Obtaining server logs from the plurality of servers in real time;
[0109] storing the server log in a log cluster according to a preset format;
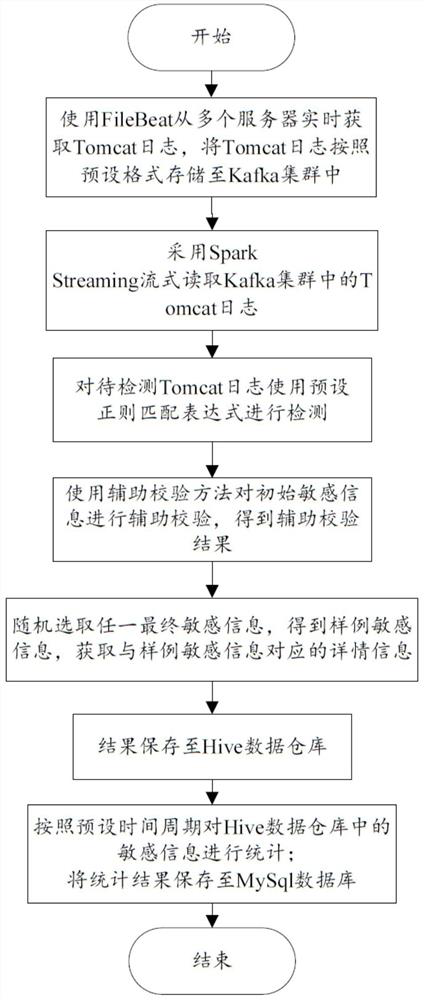
[0110] Specifically, such as image 3 As shown, use FileBeat (log collection tool) to obtain Tomcat logs from multiple servers in real time, and store Tomcat logs in the Kafka cluster (a log cluster) in a preset format, such as displaying the log level at the beginning of each Tomcat log , occurrence time, category name and other information;
[0111] S1. Receive a detection request for sensitive information, where the detection request includes a log cluster;
[0112] S2. Stream-read the serve...
Embodiment 2
[0117] Please refer to figure 1 , 3 , on the basis of Embodiment 1, this embodiment further defines how to perform detection based on the read server log, specifically:
[0118] The detection in S2 based on the read server log using a preset regular matching expression includes:
[0119] Obtaining a hash value corresponding to each server log according to the read server log;
[0120] Specifically, call the hashCode() method for each read Tomcat log to obtain the hash value corresponding to each Tomcat log;
[0121] performing a division operation on the hash value and the first preset value to obtain a division result;
[0122] Wherein, the first preset value can be flexibly set according to actual needs. In this embodiment, the first preset value is 5, that is, the Tomcat log is sampled by 1 / 5;
[0123] Specifically, divide the hash value by 5 to obtain a division result;
[0124] Judging whether the remainder in the result of the division operation is a second preset v...
Embodiment 3
[0138] Please refer to figure 1 , 3 , on the basis of Embodiment 1 or Embodiment 2, this embodiment further defines how to perform auxiliary verification of initial sensitive information, specifically:
[0139] Such as image 3 As shown, the S3 is specifically:
[0140] Obtain the information type corresponding to the initial sensitive information;
[0141] Wherein, the information type includes ID number information, mobile phone number information, email address information and bank card number information;
[0142] Acquiring an auxiliary verification method corresponding to the information type according to the information type corresponding to the initial sensitive information;
[0143] Among them, the auxiliary verification method corresponding to the information type includes an auxiliary verification method of an ID card number, an auxiliary verification method of a mobile phone number, an auxiliary verification method of an email address, and an auxiliary verificat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com