Computer data security protection method and device based on artificial intelligence and electronic equipment
A technology of data security and artificial intelligence, applied in the field of data security, can solve problems such as risks, data tampering, users can not find in time, etc., to achieve the effect of clear and easy-to-understand description
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
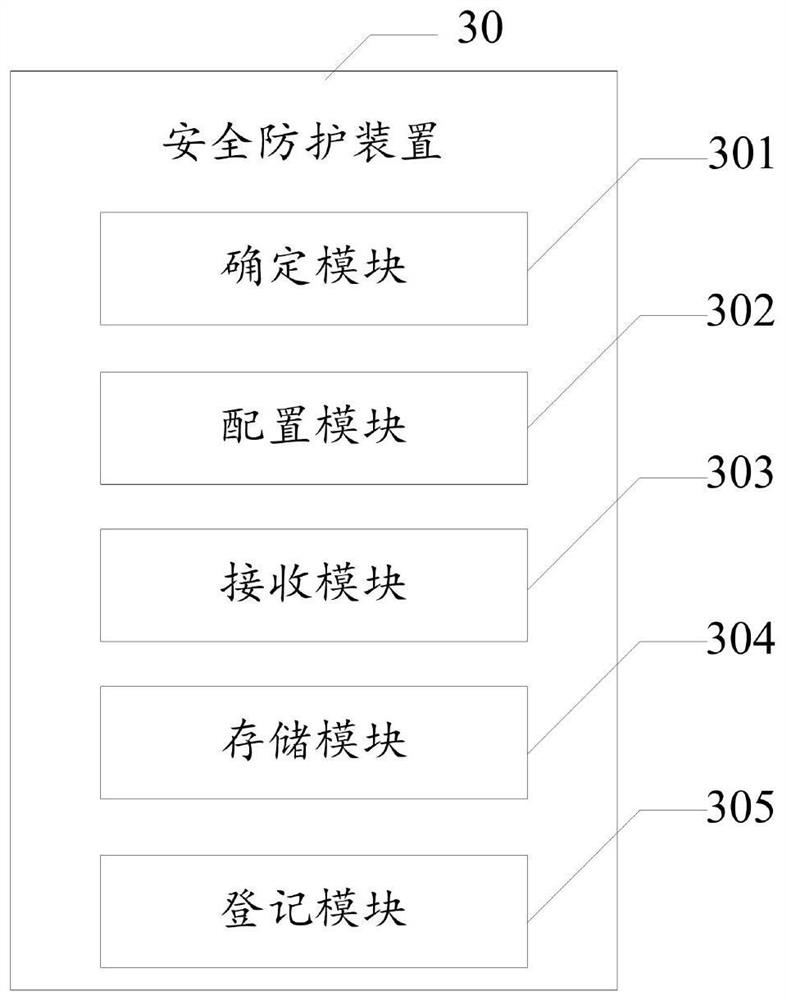
Embodiment approach
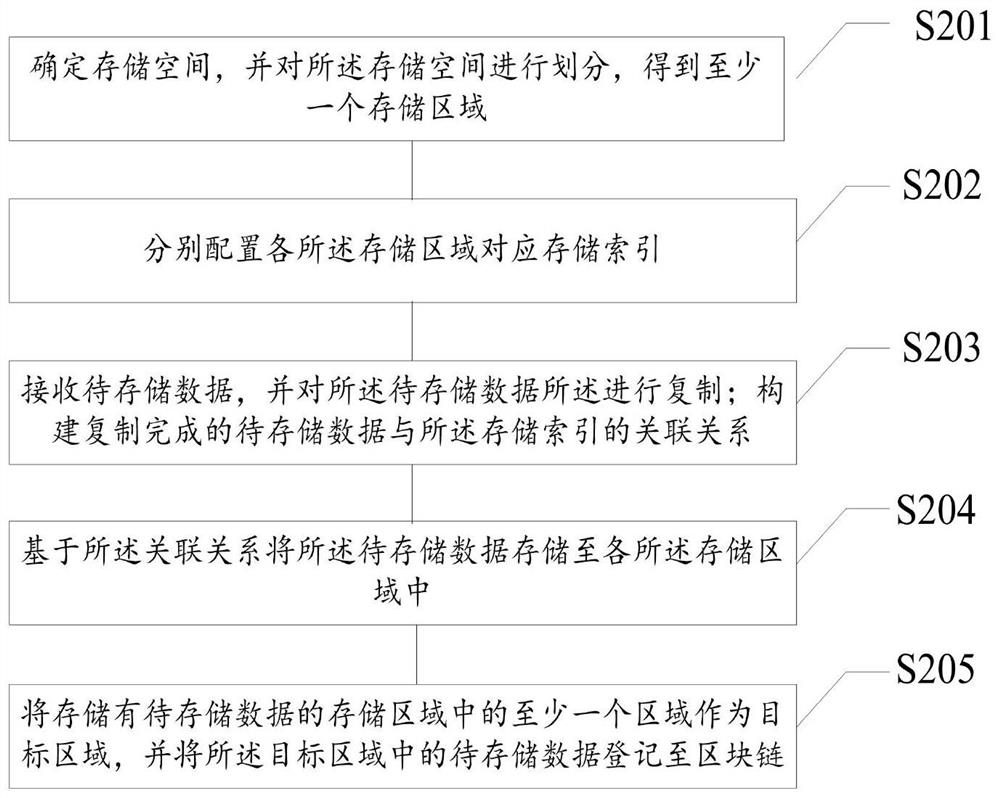
[0111] Further, in an exemplary embodiment, the method also includes:
[0112] Step S206, accessing and obtaining the first storage data stored in other storage areas except the target area.
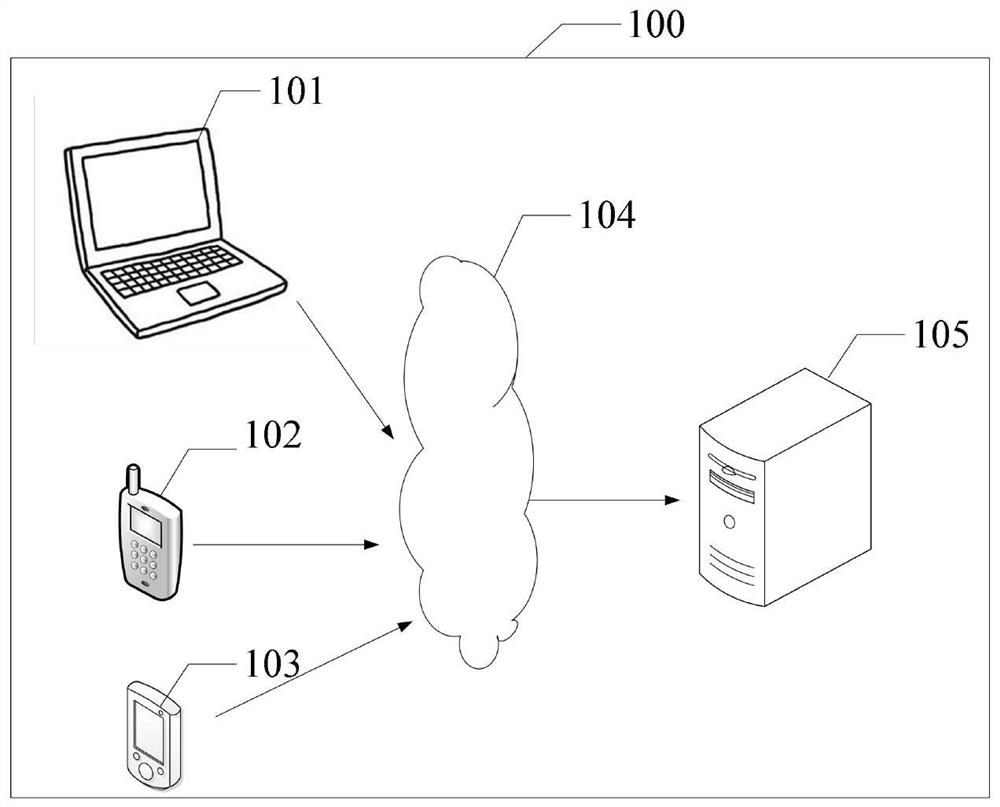
[0113] In this example embodiment, the access means may be that the user directly accesses in the server storage, for example, by clicking a storage location, such as a certain folder, or the user accesses the first stored data in the server storage through a client terminal. The above-mentioned first stored data may be data in any one or more areas except the target area.
[0114] Step S207, calculating a hash value corresponding to the stored data to obtain a first hash value.
[0115] In this exemplary embodiment, the above-mentioned algorithm for calculating the hash value may be an existing hash algorithm. This solution does not improve the above-mentioned hash algorithm, and calculates the hash value through the hash algorithm to obtain the hash value in this solution. The first ha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com