Open authorization method, device and equipment and storage medium
An open authorization, authentication and authorization technology, applied in the field of communication, can solve problems such as unsmooth migration, and achieve the effects of increasing reliability, optimizing user experience, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
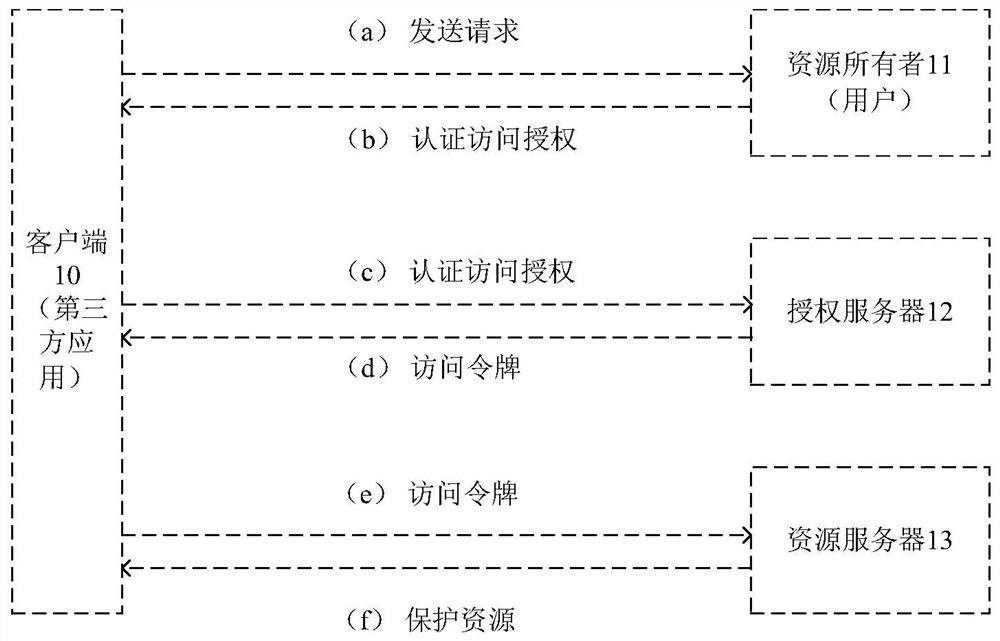
[0037] Figure 1A Schematic diagram of the process of providing API-level services to third parties for existing authentication methods, such as Figure 1A As shown, the interaction between the four roles of client 10, resource owner 11, authorization server 12 and resource server 13 is described, including the following steps:
[0038] Step (a) The third-party application requests user authorization; the client 10 sends an open authorization request (Authorization Request) to the resource owner 11, requesting the resource owner 11 to authorize. This open authorization request can be sent directly to the resource owner 11 (as shown in the figure), or preferably through the authorization server 12 as an intermediary between the client 10 and the resource owner 11 .
[0039] Step (b) After the user agrees to the authorization, the user will obtain a letter of authorization from the service provider and give it to the third-party application; the letter of authorization is the cre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com