Internet-of-things data security access method, system and device based on blockchain and edge computing, and storage medium
An edge computing and data security technology, applied in the field of the Internet of Things, can solve problems such as the server's inability to respond to device update requests, data call failures, etc., and achieve the effect of avoiding excessive growth and solving high costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
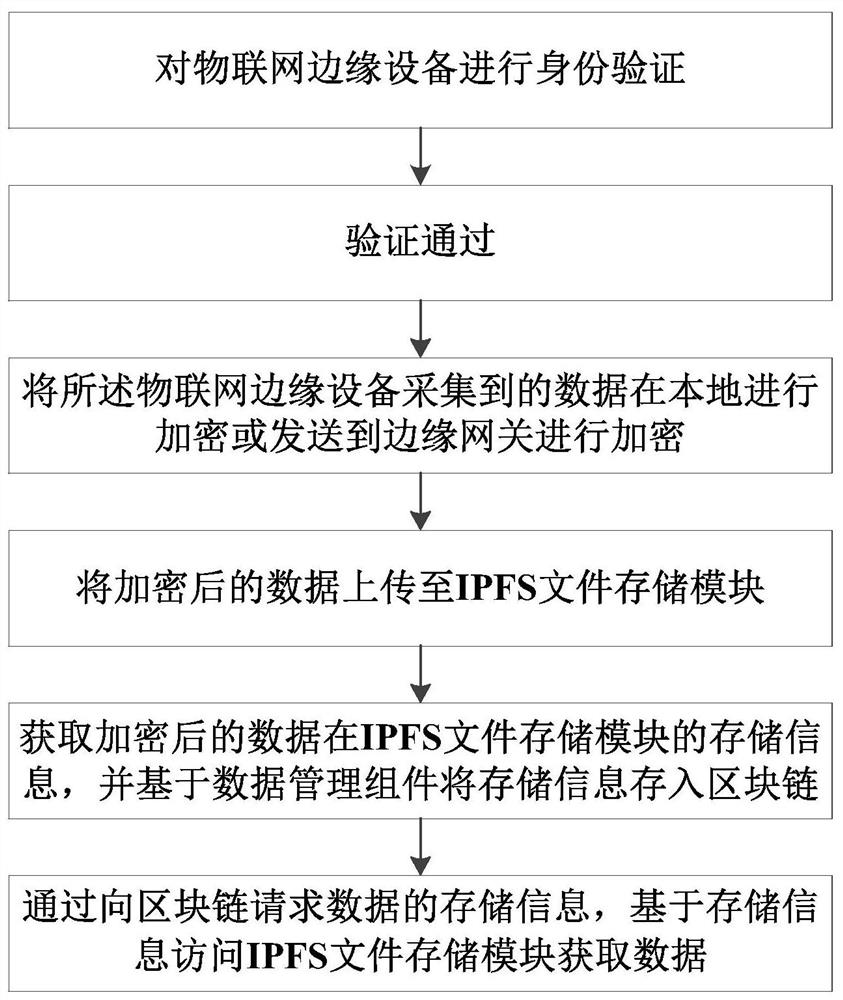
[0028] Such as figure 1 As shown, the embodiment of the present invention provides a secure access method for IoT data based on blockchain and edge computing, including the following steps:
[0029] (1) Perform identity verification on the edge device of the Internet of Things. If the verification is passed, the data collected by the edge device of the Internet of Things is encrypted locally or sent to the edge gateway for encryption;
[0030] The authentication of the edge device of the Internet of Things includes: verifying the identity of the edge device of the Internet of Things and obtaining the corresponding data writing permission.
[0031] Through the blockchain-based distributed identity authentication technology, the basic information of IoT edge devices is stored in the block, forming an independent identity sub-chain dedicated to storing identity information, and storing device permission information in a separate permission sub-chain Chain to realize the separati...
Embodiment 2
[0039] An embodiment of the present invention provides a secure access device for IoT data based on blockchain and edge computing, the device includes:
[0040] The acquisition and encryption module is used to authenticate the edge device of the Internet of Things. If the verification is passed, the data collected by the edge device of the Internet of Things is encrypted locally or sent to the edge gateway for encryption;
[0041] Distributed storage module, used to upload encrypted data to IPFS file storage module;
[0042] The blockchain storage module is used to obtain the storage information of the encrypted data in the IPFS file storage module, and store the storage information into the blockchain based on the data management component;
[0043] The data acquisition module is used to request the storage information of the data from the block chain, and access the IPFS file storage module to acquire data based on the storage information.
Embodiment 3
[0045] The embodiment of the present invention provides a secure access device for Internet of Things data based on blockchain and edge computing, which is characterized in that it includes a processor and a storage medium;
[0046] The storage medium is used to store instructions;
[0047] The processor is configured to operate in accordance with the instructions to perform the steps according to any one of the methods described above.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com