Method for supervisor to share sensitive data in alliance chain scene based on group negotiation key
A technology for sensitive data and regulators, applied in digital data authentication, digital data protection, electronic digital data processing, etc., can solve the problem of session key efficiency and affect the efficient, orderly, credible and centralized organization of digital economic activities high cost etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
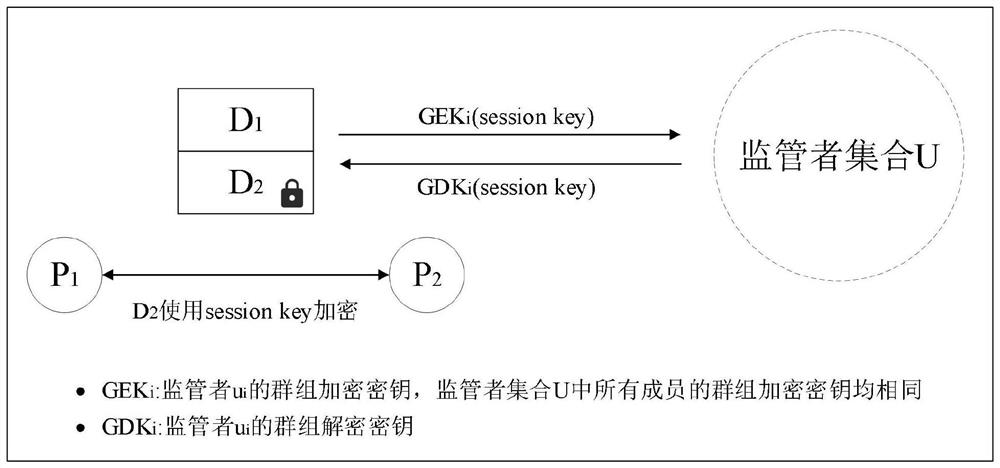
[0046] The present invention proposes a method for regulators to share sensitive data in a consortium chain scenario based on group negotiation keys. The flow chart is as follows: figure 1As shown, node P 1 with node P 2 For transactions, the specific transaction information is divided into plain text part D 1 and ciphertext part D 2 , where D 2 by P 1 with P 2 The agreed upon session key is encrypted.
[0047] The inventive method has the following steps:
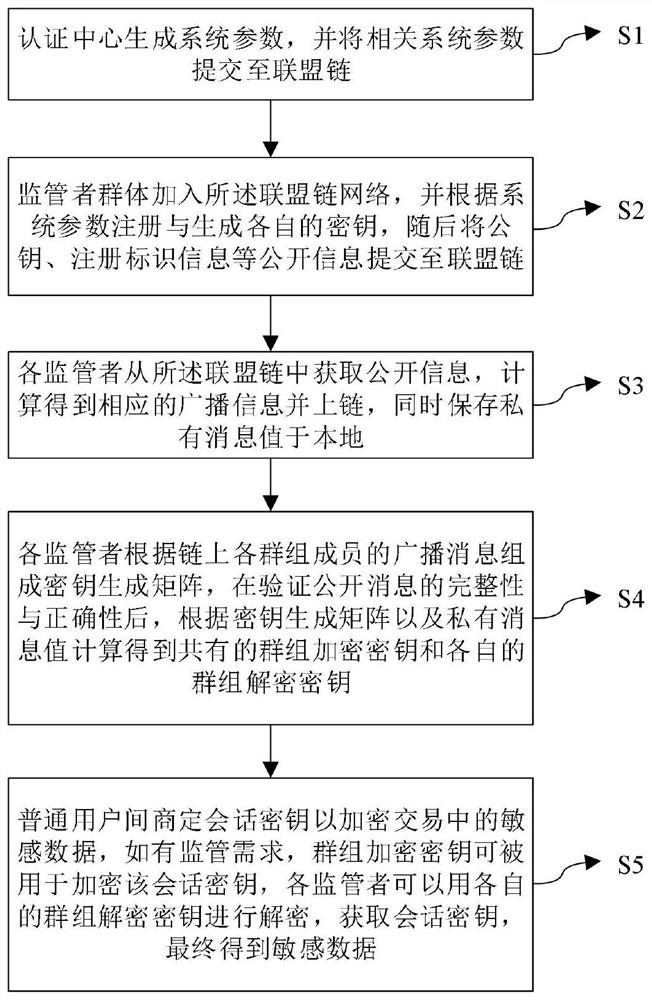
[0048] S1: The certification center generates system parameters and submits relevant system parameters to the alliance chain;
[0049] S2: The regulator group joins the alliance chain network, and completes their own key registration and generation according to the system parameters and other information on the chain, and then submits public information such as public key and registration identification information to the alliance chain;
[0050] S3: Each regulator obtains the public information from the alliance c...
Embodiment 2
[0055] The present invention is a method for regulators to share sensitive data in a consortium chain scenario based on group negotiation keys. The transaction sensitive data authorization scenario discussed is as follows: figure 2 As shown, there are n supervisors in the supervisor set U {u 1 ,u 2 ,...,u n}, each regulator needs to obtain the data used to encrypt sensitive data D 2 session key.
[0056] Specifically, the present invention has the following steps:
[0057] S1: The certification center generates system parameters and submits relevant system parameters to the alliance chain;
[0058] Its sub-steps are:
[0059] S1.1: Build a consortium chain network;
[0060] S1.2: The certification center generates relevant system parameters params based on the bilinear pairing of the elliptic curve group;
[0061] S1.3: The certification center submits relevant system parameters params to the alliance chain.
[0062] S2: The regulator group joins the alliance chain ne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com