Use monitoring method and device of intelligent key
A smart key and intelligent technology, applied in the field of electric power, can solve the problems of low on-site operation efficiency, insufficient operation management and control ability of electric facilities, and inability to control electric facilities operation, etc., and achieve the effect of monitoring the scope of use.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
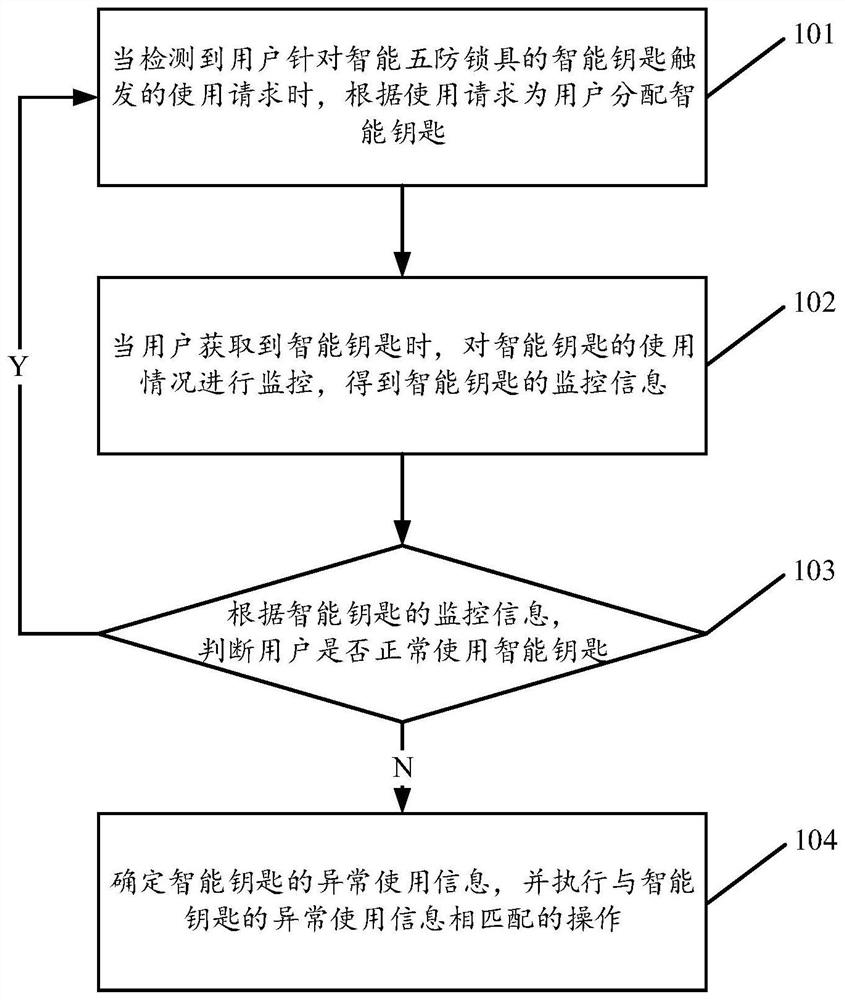
[0097] see figure 1 , figure 1 It is a schematic flowchart of a method for monitoring the use of a smart key disclosed in an embodiment of the present invention. in, figure 1 The described smart key use monitoring method can be applied to a smart key use monitoring device, wherein the device can include a smart key or a smart storage device (such as a smart key cabinet) or a power grid management system (grid management platform), the smart key The keys may be stored in a smart storage device. Wherein, the power grid management system may be a local power grid management system, or a power grid management cloud platform, which is not limited in this embodiment of the present invention. Such as figure 1 As shown, the usage monitoring method of the smart key may include the following operations:
[0098] 101. When detecting the user's use request triggered by the smart key of the smart five-proof lock, assign the user a smart key according to the use request.
[0099] In t...
Embodiment 2
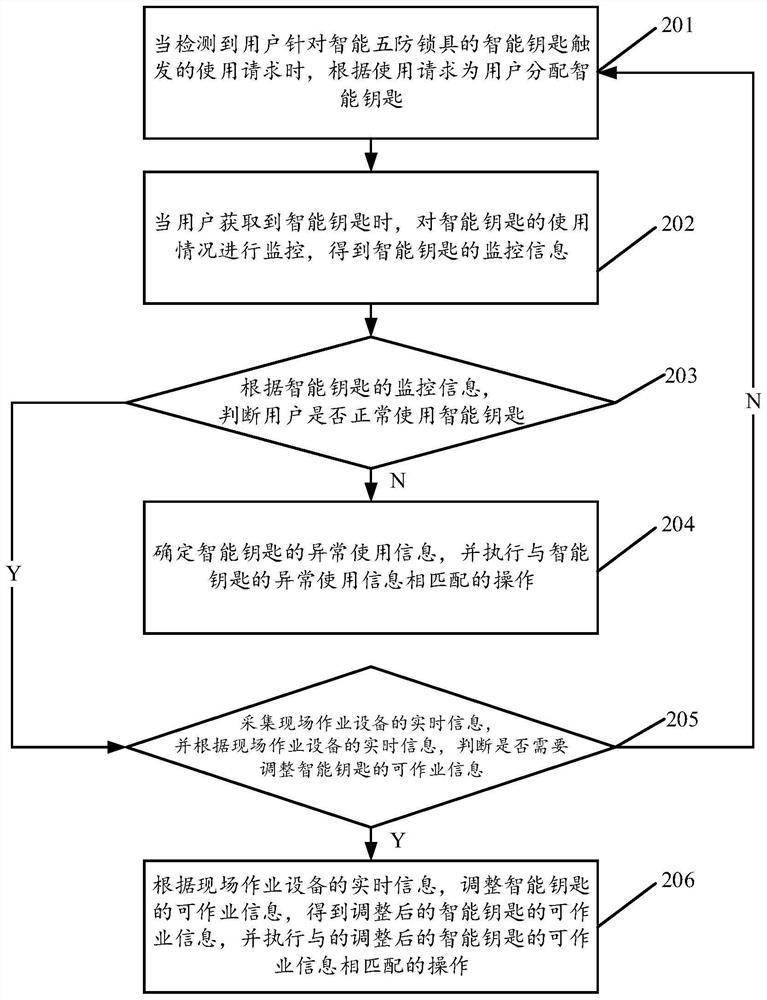
[0154] see figure 2 , figure 2 It is a schematic flowchart of another smart key usage monitoring method disclosed in the embodiment of the present invention. in, figure 2 The described smart key use monitoring method can be applied to a smart key use monitoring device, wherein the device can include a smart key or a smart storage device (such as a smart key cabinet) or a power grid management system (grid management platform), the smart key The keys may be stored in a smart storage device. Wherein, the power grid management system may be a local power grid management system, or a power grid management cloud platform, which is not limited in this embodiment of the present invention. Such as figure 2 As shown, the usage monitoring method of the smart key may include the following operations:
[0155] 201. When detecting the user's use request triggered by the smart key of the smart five-proof lock, assign the user a smart key according to the use request.
[0156] 202....
Embodiment 3
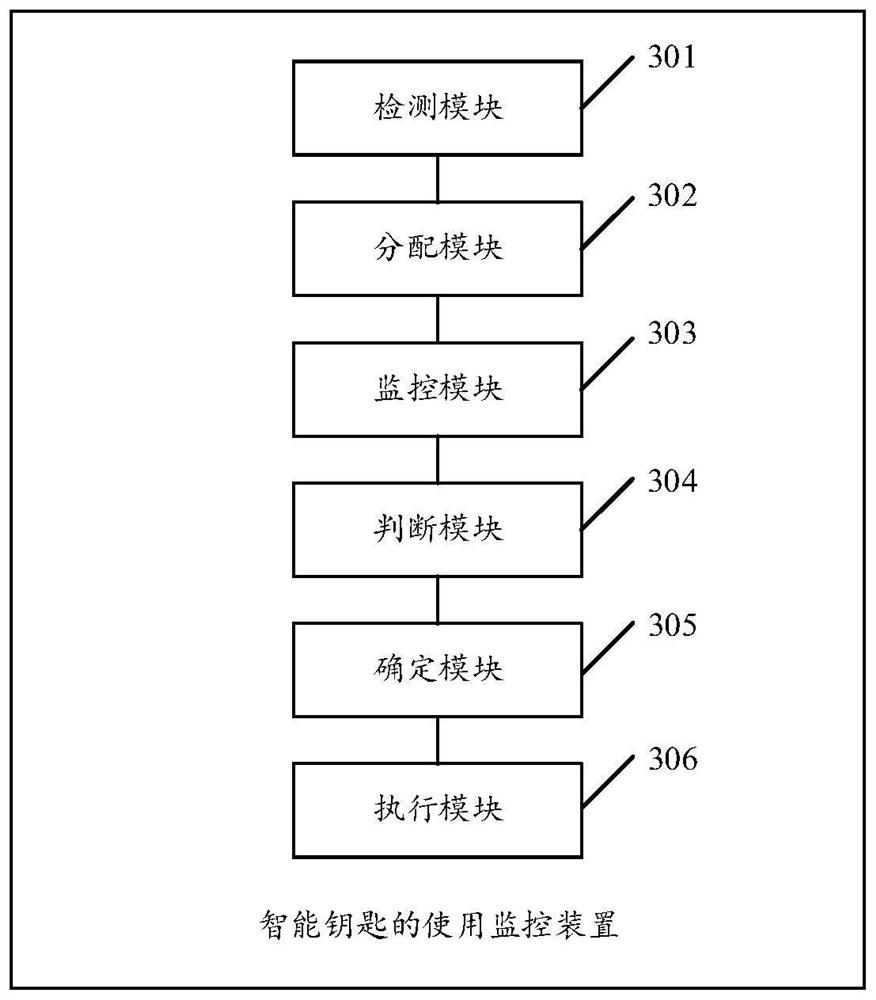
[0168] see image 3 , image 3 It is a structural schematic diagram of an intelligent key usage monitoring device disclosed in an embodiment of the present invention. Wherein, the device may include a smart key or a smart storage device (such as a smart key cabinet) or a grid management system (grid management platform), and the smart key may be stored in the smart storage device. Wherein, the power grid management system may be a local power grid management system, or a power grid management cloud platform, which is not limited in this embodiment of the present invention. Such as image 3 As shown, the smart key usage monitoring device may include: a detection module 301, an allocation module 302, a monitoring module 303, a judgment module 304, a determination module 305, and an execution module 306, wherein:
[0169] The detection module 301 is configured to detect the user's use request triggered by the smart key of the smart five-proof lock.
[0170] The allocation mod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com