Active trapping security defense method and system, electronic equipment and storage medium
A security defense and entrapment technology, which is applied in transmission systems, digital transmission systems, security communication devices, etc., can solve problems such as inconvenience and inability to effectively trap attackers, and achieve the effect of security defense
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
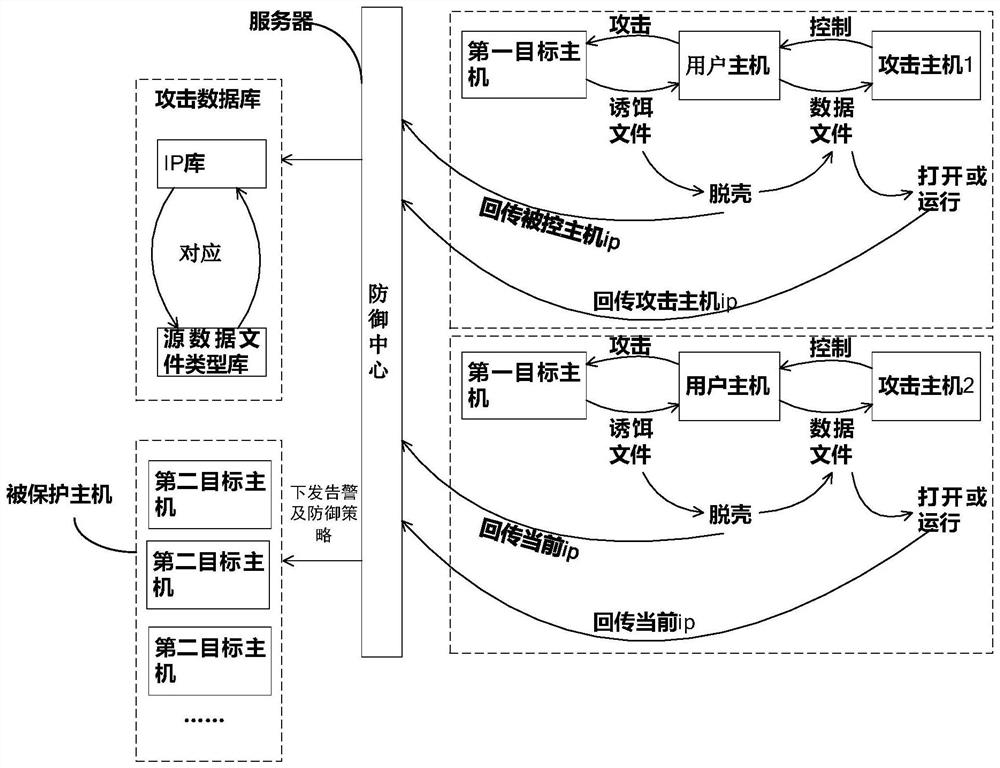
[0056] Figure 4 It is a schematic block diagram of an embodiment of the active decoy security defense system of the present invention. see Figure 4 As shown, the system of this embodiment includes:
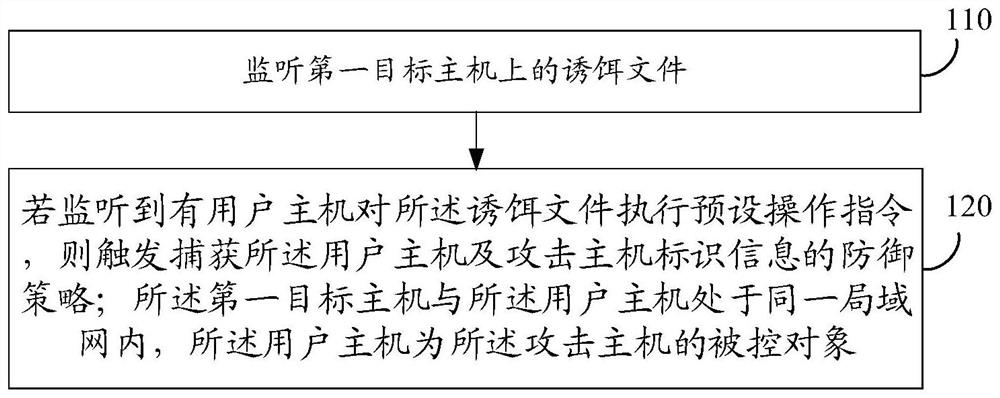
[0057] Listener module 210, used to monitor the decoy file on the first target host;
[0058] The triggering program module 220 is used to trigger the defense strategy of capturing the identification information of the user host and the identification information of the attacking host if it is detected that a user host executes a preset operation command on the decoy file; The user host is in the same local area network, and the user host is the controlled object of the attacking host.
[0059] The system of this embodiment can be used to execute figure 1 The implementation principles and technical effects of the technical solutions of the shown method embodiments are similar and will not be repeated here.
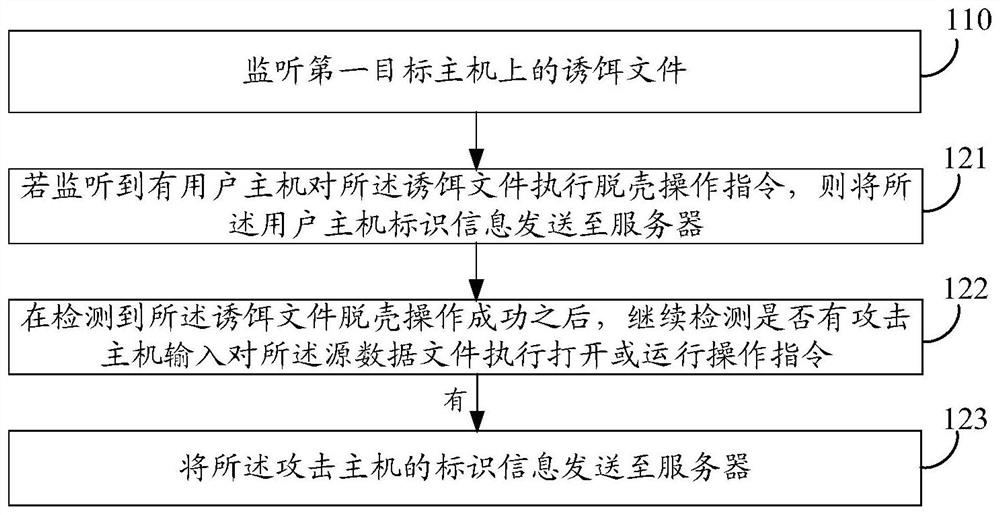
[0060] In some embodiments, the decoy file includes: a source data...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com