Security defense method and device
A technology for security defense and Internet of Things equipment, applied in the field of security defense methods and devices, can solve the problem that the security of Internet of Things equipment cannot be effectively guaranteed, and achieve the effect of realizing security defense, ensuring security, and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
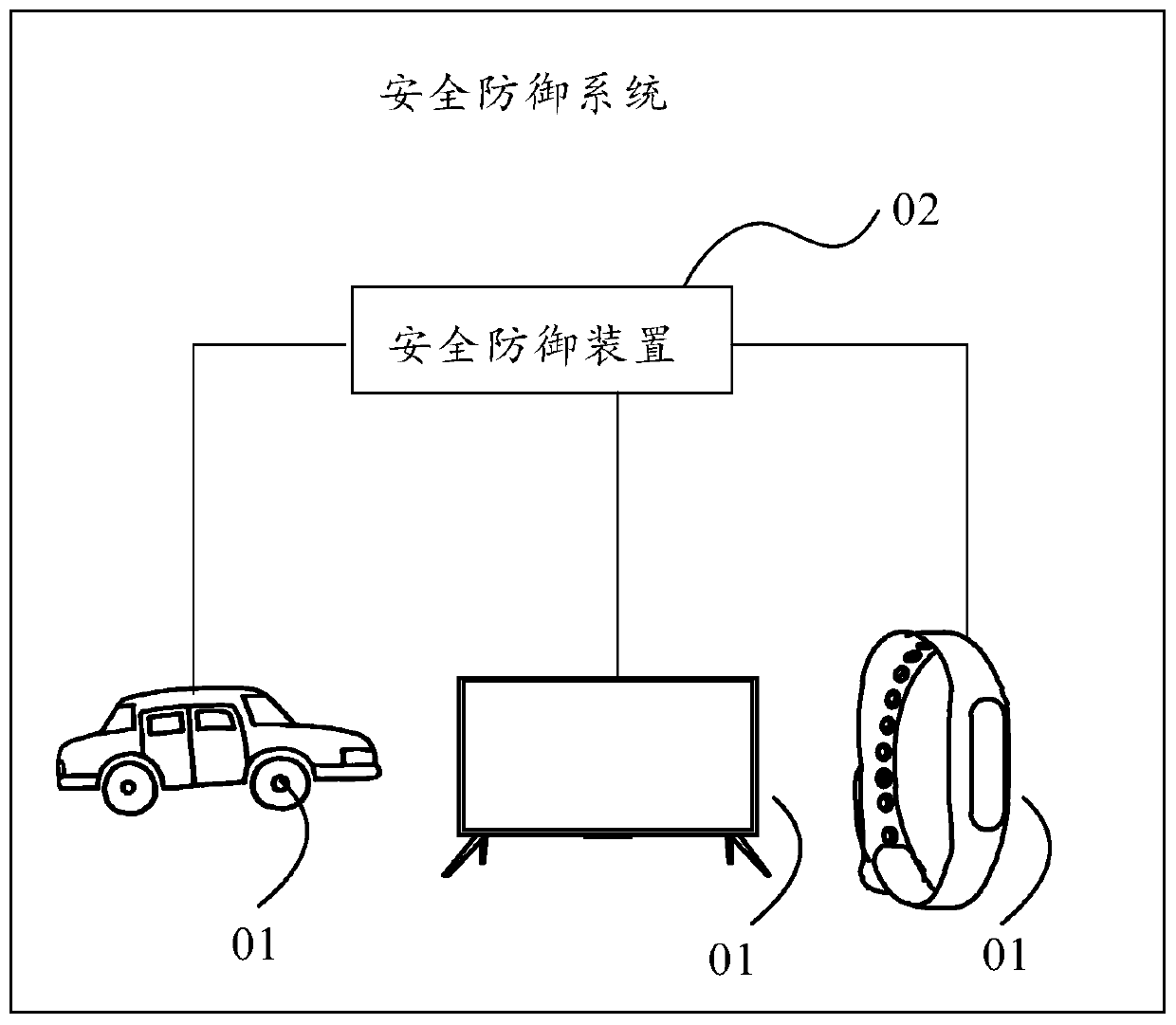
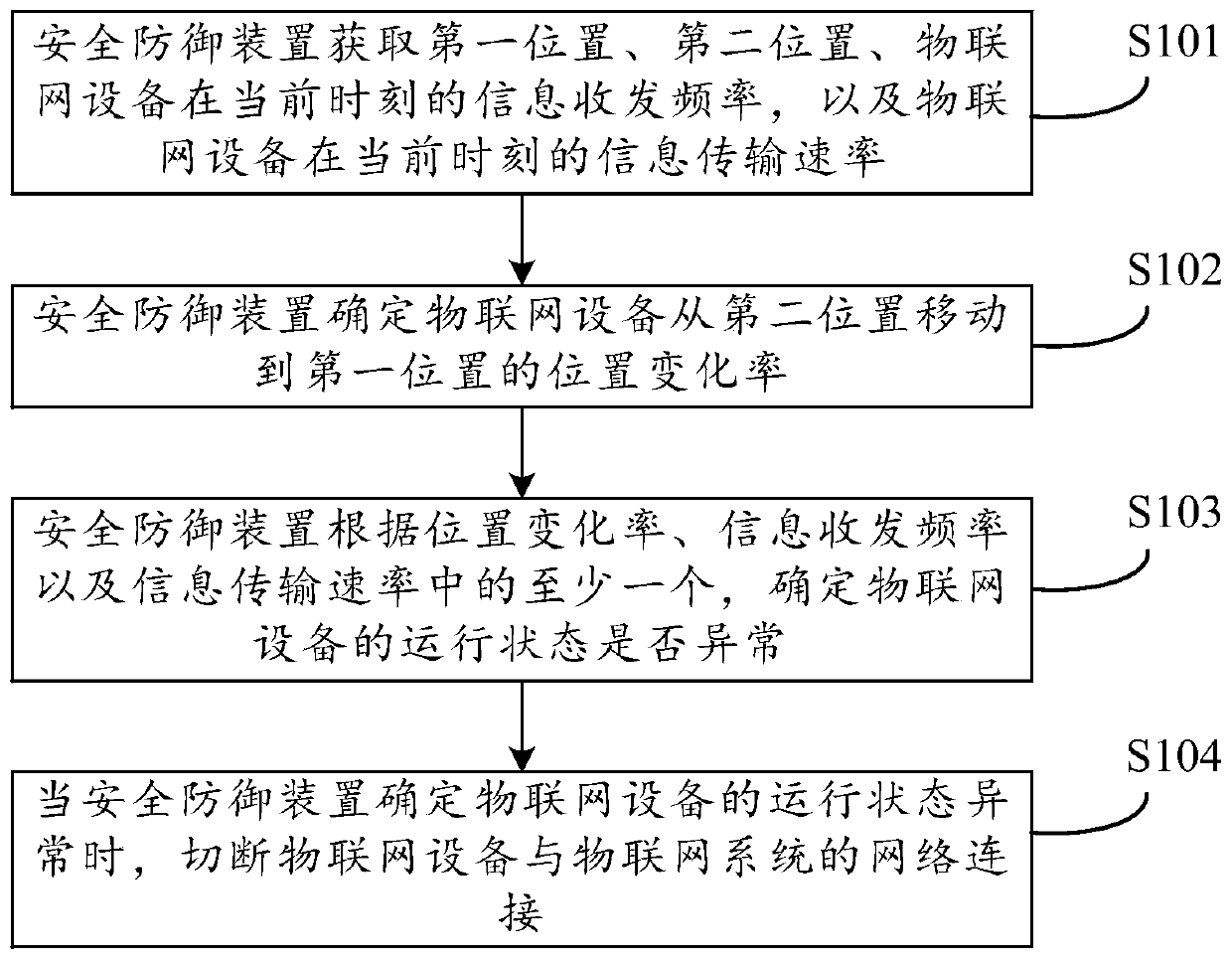
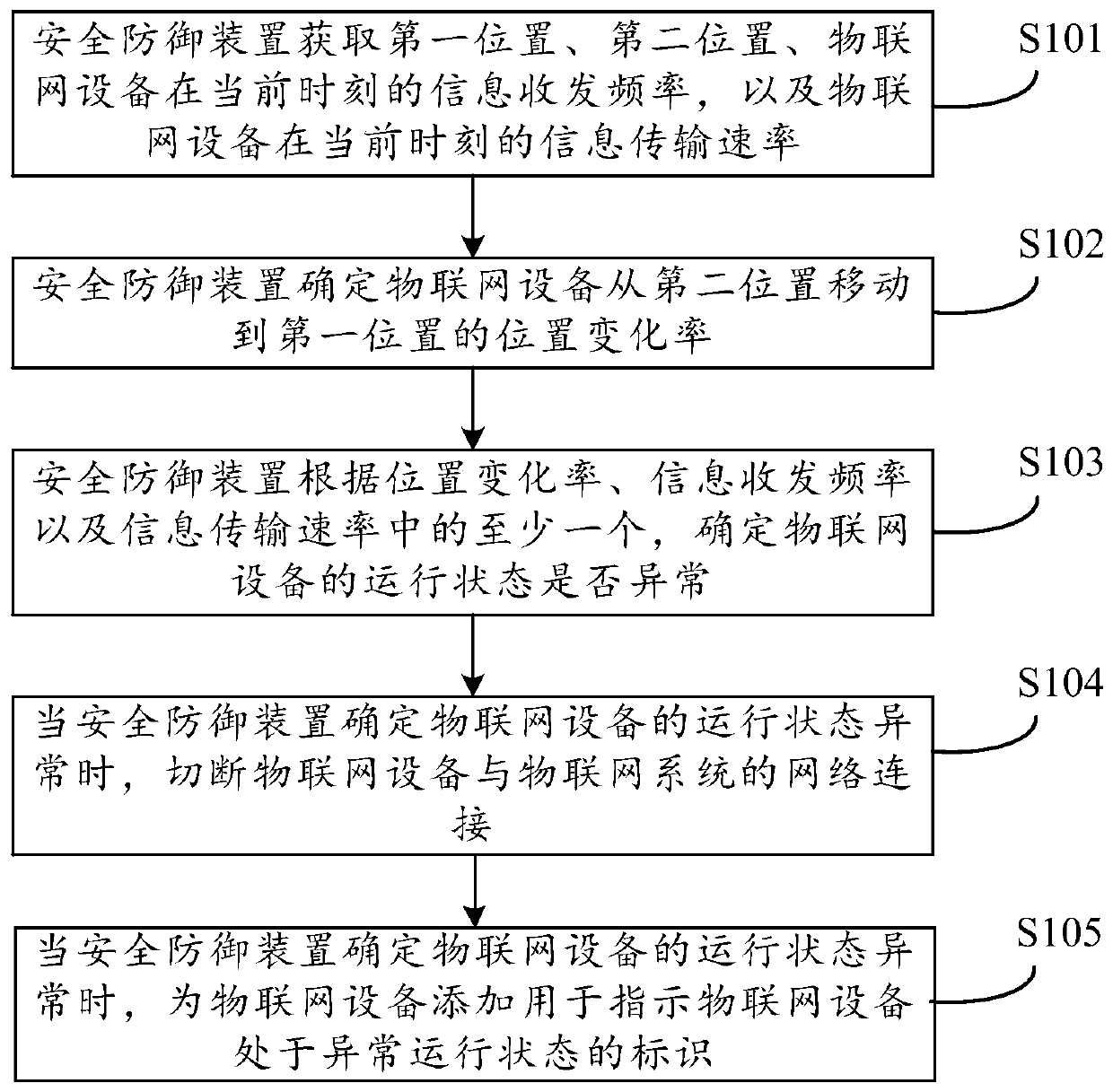
[0022] The security defense method and device provided by the embodiments of the present application will be described in detail below with reference to the accompanying drawings.
[0023] The term "and / or" in this article is just an association relationship describing associated objects, which means that there can be three relationships, for example, A and / or B can mean: A exists alone, A and B exist simultaneously, and there exists alone B these three situations.
[0024] The terms "first" and "second" in the specification and drawings of the present application are used to distinguish different objects, or to distinguish different processes for the same object, rather than to describe a specific sequence of objects.
[0025] In addition, the terms "including" and "having" mentioned in the description of the present application and any variations thereof are intended to cover non-exclusive inclusion. For example, a process, method, system, product or device comprising a ser...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com