Adversarial sample generation method
A technology against samples and images, applied in the field of pattern recognition, can solve problems such as limiting network knowledge, not knowing parameters or training data, and achieving high usability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
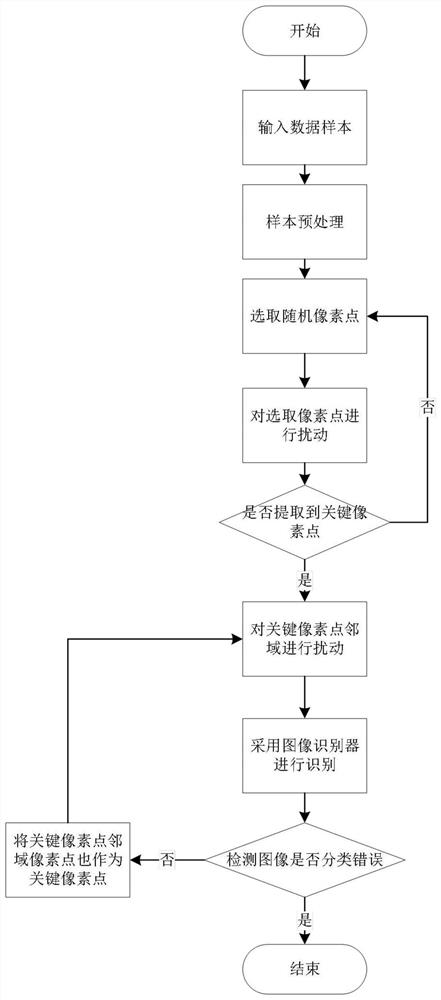
[0023] see figure 1 , this embodiment provides a method for generating an adversarial sample according to the present invention, including the following steps,
[0024] Step S1, input image I, normalize the image, the size of the normalized image is the same as the original image, all the coordinates of the normalized image are in the range of [LB, UB], LB and UB are two constants, and LB0; with T ∈ R l×w×h Represents the space of all valid images satisfying the above properties; for each I∈T, all coordinates in the image satisfy: (b,x,y)∈[l]×[w]×[h],I(b,x ,y)∈[LB,UB];
[0025] Step S2, the classification label is C(I)∈{1,...,C}, p and r are the perturbation coefficients, the side length of the image neighborhood search radius is 2d, the maximum number of iterations is R, and the selected The number of pixels is t;
[0026] Step S3, randomly select 10% of the pixels, and initialize the set (P x ,P y ), (P x ,P y ) i is a group of pixel positions; the first round (P x ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com