Password and policy based device independent authentication
A password and policy technology, applied in encryption devices with shift registers/memory, instruments, televisions, etc., can solve the problems of cumbersome loading of electronic devices, complicated registration process, time-consuming and other problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
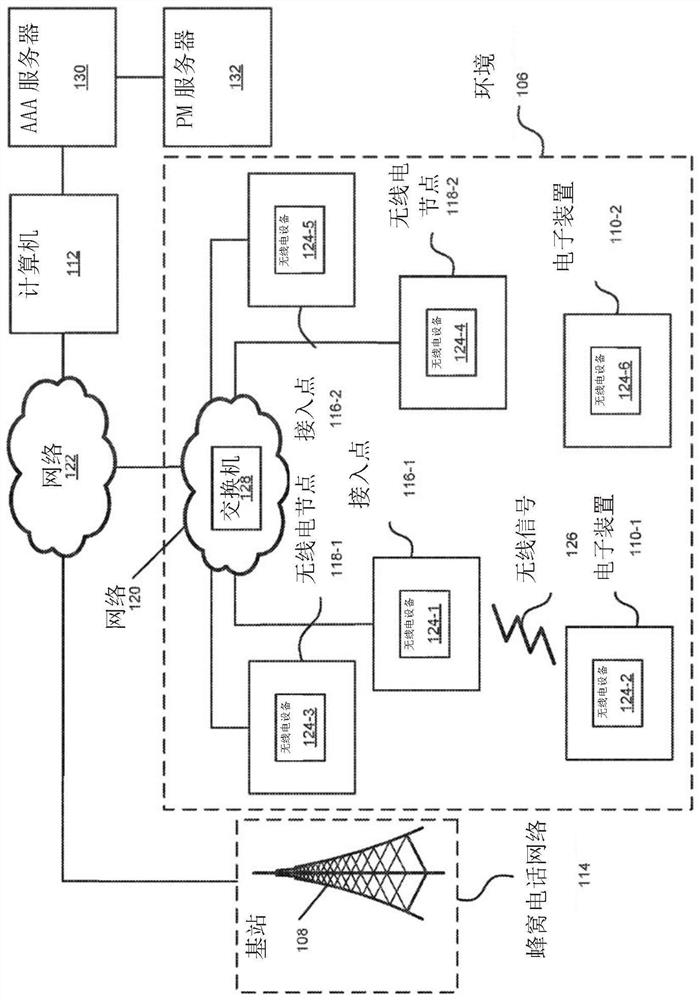
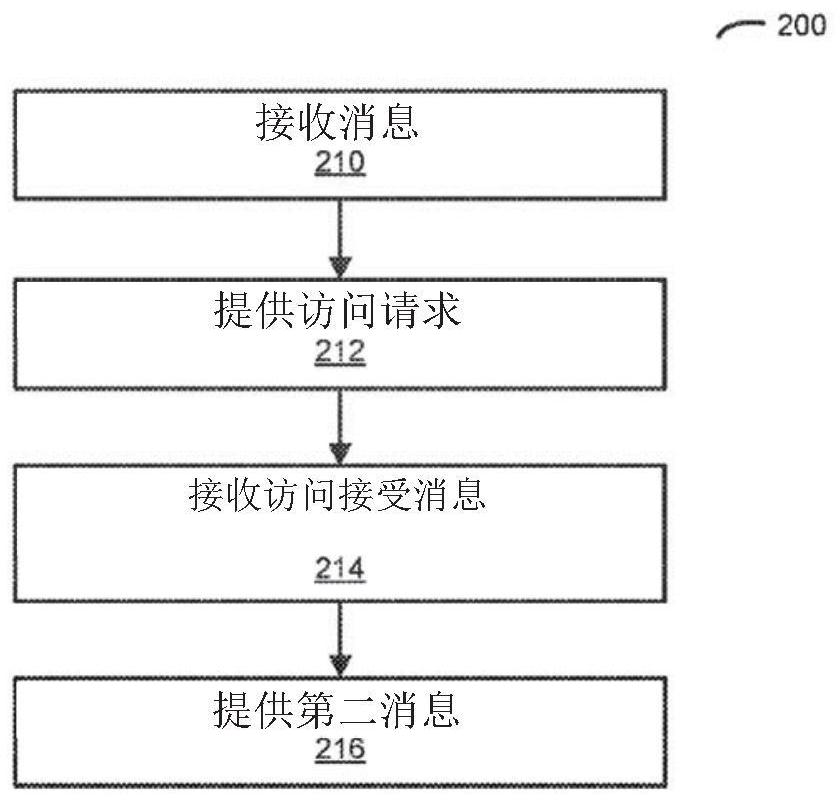
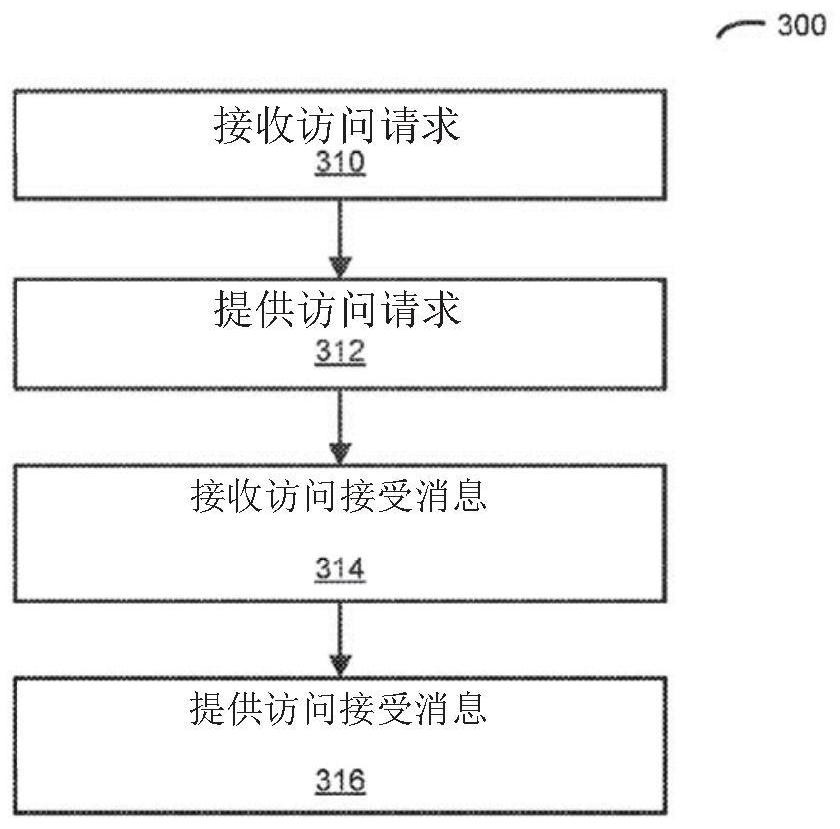
[0052] An electronic device (eg, an AAA server) that selectively authorizes secure access to a network by a second electronic device is described. Such an electronic device may receive an access request associated with a computer, wherein the access request includes a password parameter associated with the user, and the password parameter includes the input and output of the encryption computation. In response, the electronic device may compute one or more second outputs of the encrypted computation based at least in part on the input and the one or more stored passwords. Furthermore, when there is a match between one of the one or more second outputs and the output, the electronic device can access the policy associated with the user. Then, when one or more criteria associated with the policy are satisfied, the electronic device may optionally provide an access accept message to the computer, the access accept message including information for establishing secure access for t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com