User behavior pattern recognition method and device
A behavior and user technology, applied in character and pattern recognition, calculation models, data processing applications, etc., can solve problems such as low risk judgment efficiency, and achieve the effect of improving accuracy and reducing workload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0068] The solution provided by the present invention will be described below with reference to the accompanying drawings.
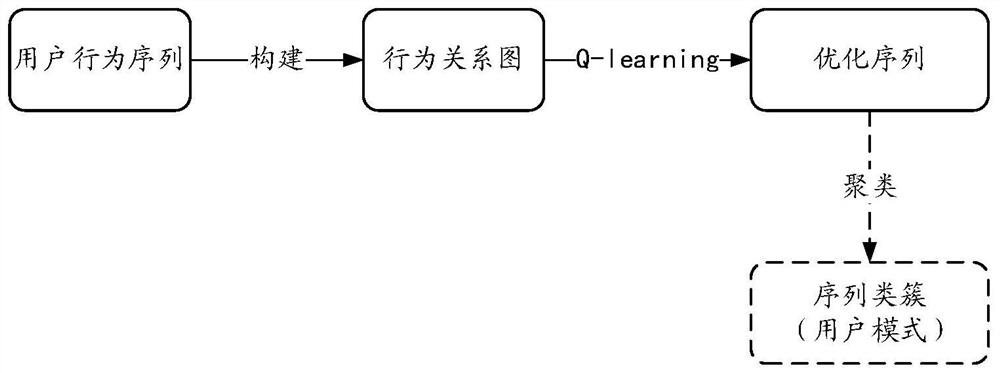
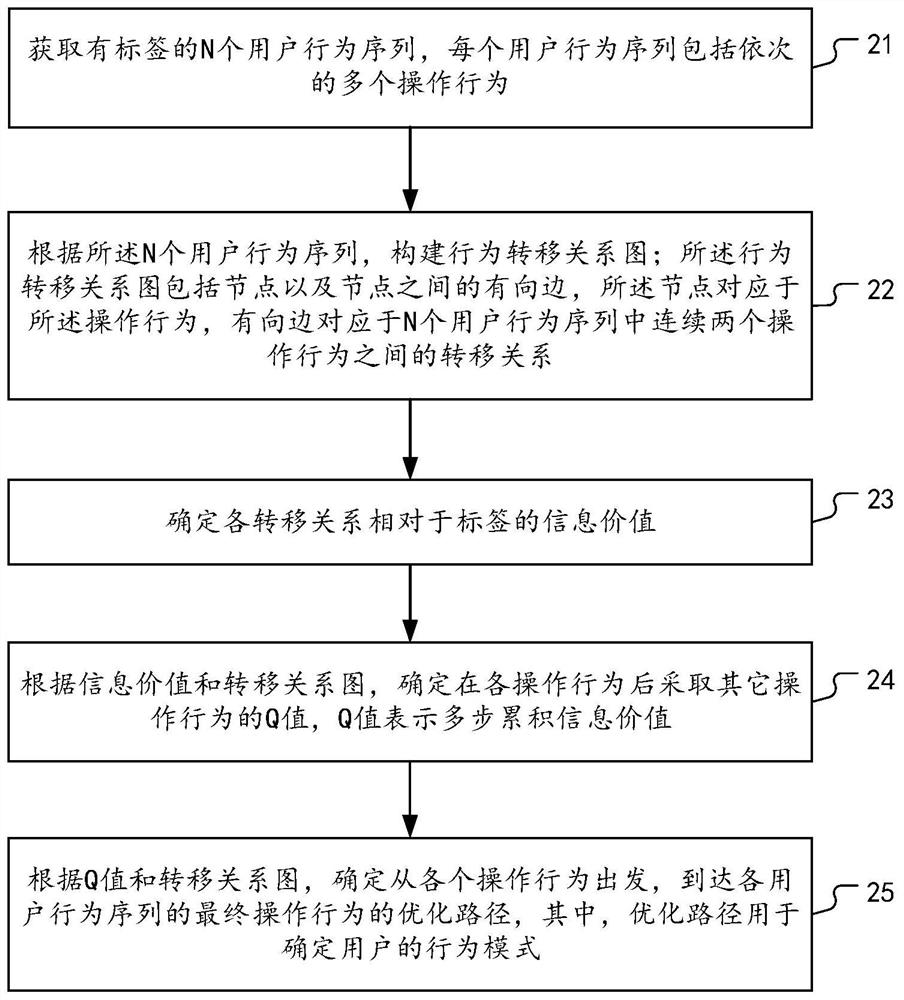
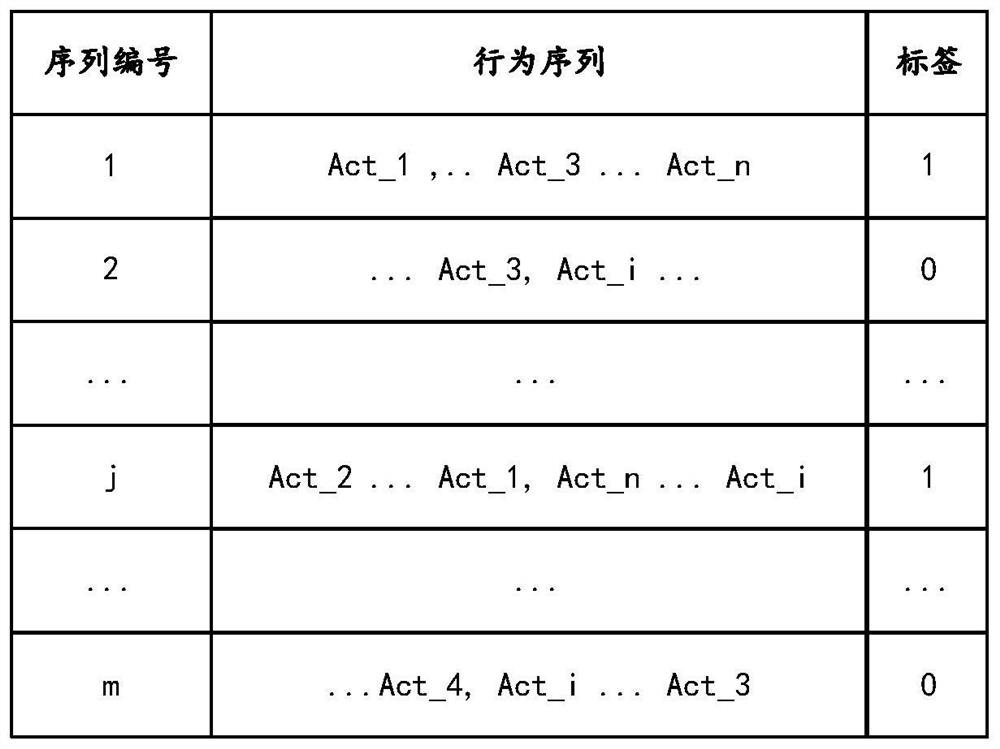
[0069] As mentioned earlier, operational risk control is required in many industries. For example, in electronic payment and transaction platforms, risk operators often need to analyze the illegal operation links of some risk cases, and analyze some common illegal operation patterns from them. Usually, the behavior link of a user in the client application may be very complex, for example, it may include various complex behaviors such as registration, login, click, visit, request submission, and purchase.
[0070] However, for the illegal operation of a specific scenario, the user's behavior link may be very similar. For example, in the scenario of account theft, the typical illegal operation sequence often includes, for example, changing passwords, changing bindings, verifying identity, paying In a fraud scenario, the typical action sequence of the defr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com