Network security data fusion method based on ontology and D-S evidence theory
A technology of network security and evidence theory, applied in reasoning methods, secure communication devices, digital transmission systems, etc., can solve problems such as semantic ambiguity, data structure differences, and unresolved problems, and achieve the effect of reducing conflicts
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
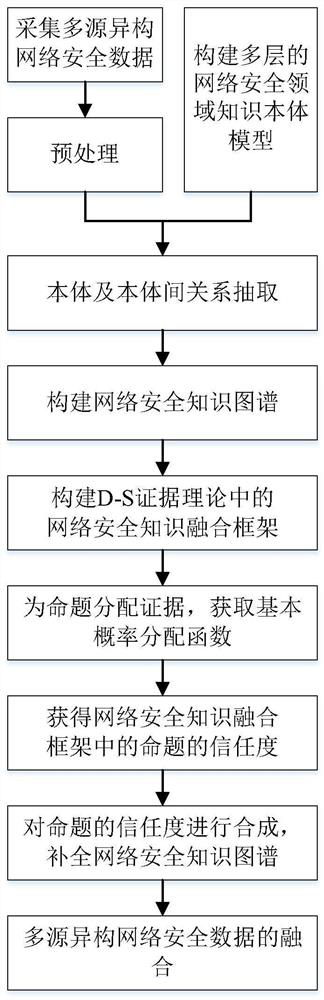
[0033] In order to make the technical solutions of the present invention more obvious and easy to understand, specific embodiments are given and described in detail below with reference to the accompanying drawings.
[0034] Step 1: Multi-source heterogeneous network security data collection
[0035] The method of the invention is based on the collected network security data, which mainly comes from equipment operation logs, security alarm logs, abnormal detection data, event data reported by manufacturers, etc.; the main contents include log data, detection data, reported event data, cyberspace asset data, etc. . In terms of data format, it also includes structured data, semi-structured data, and unstructured data. Therefore, network security data has the characteristics of multi-source heterogeneity and fragmentation.
[0036] Step 2: Multi-source heterogeneous network security data preprocessing
[0037] On the basis of analyzing the content of multi-source heterogeneous...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com