Method for avoiding malicious calling
A technology of malicious calls and normal calls, applied in the direction of unauthorized/fraudulent telephone prevention, selection devices, electrical components, etc., can solve the problem that the calling number cannot shield malicious calls, etc., to prevent continued harassment, and the operation method is simple , to achieve the effect of a simple way
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
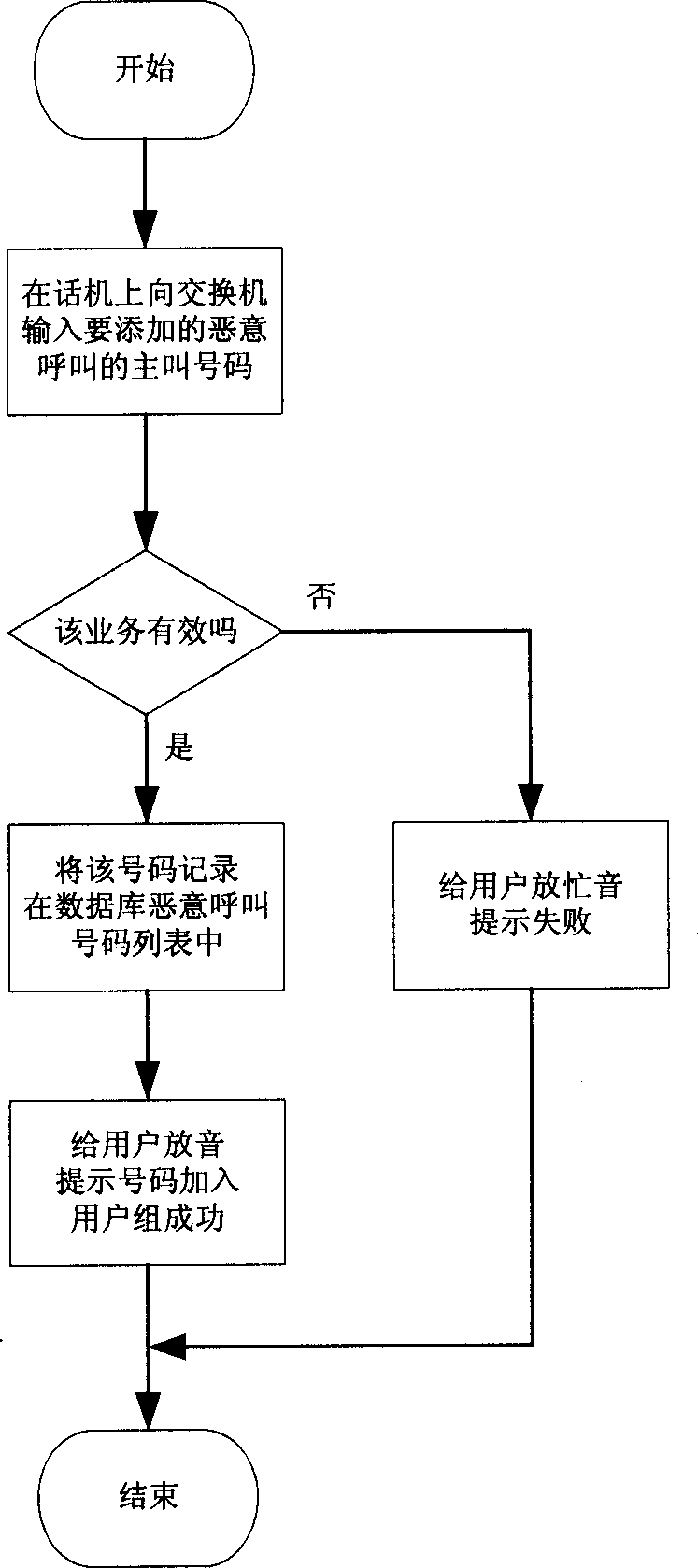
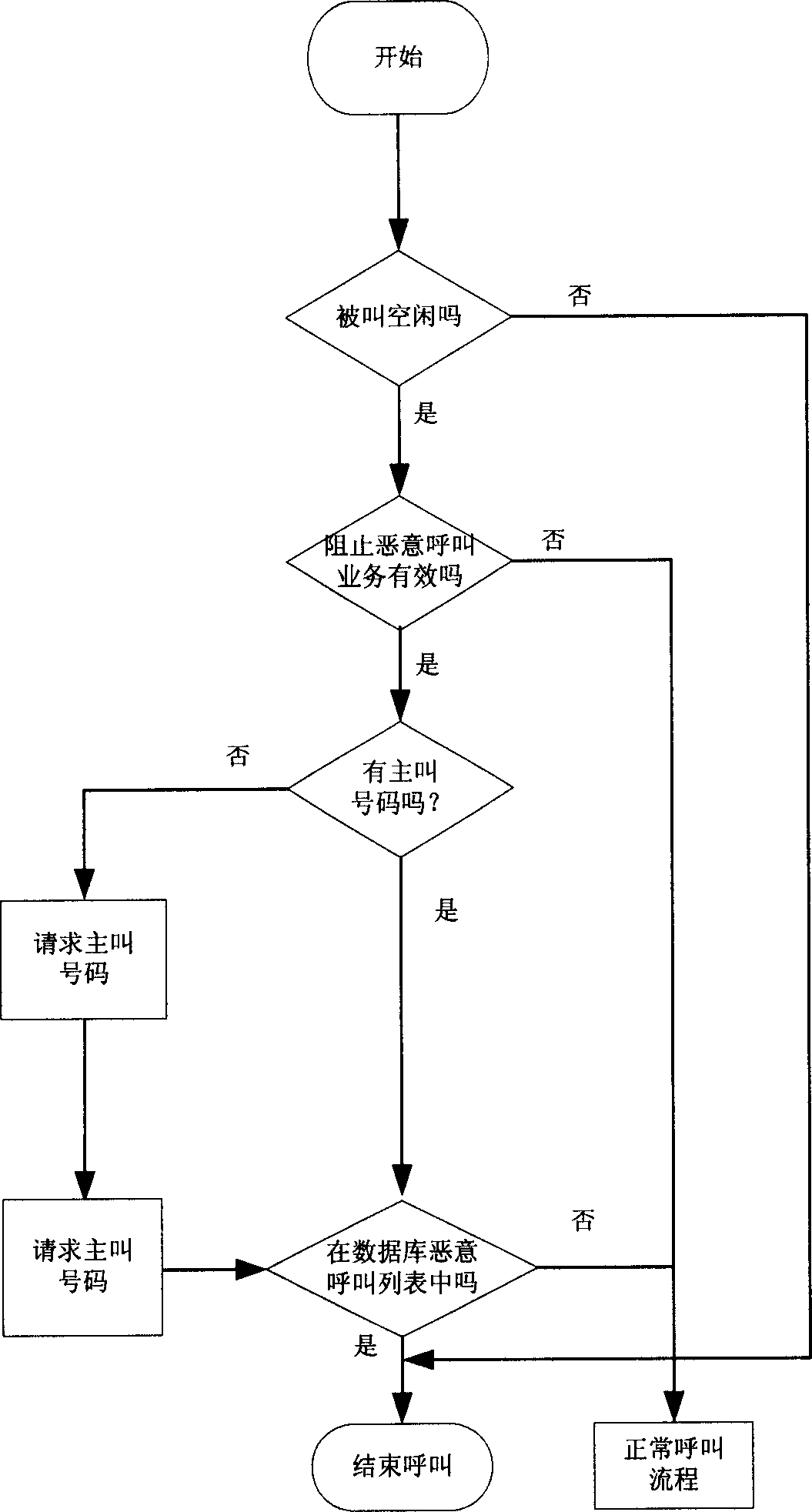
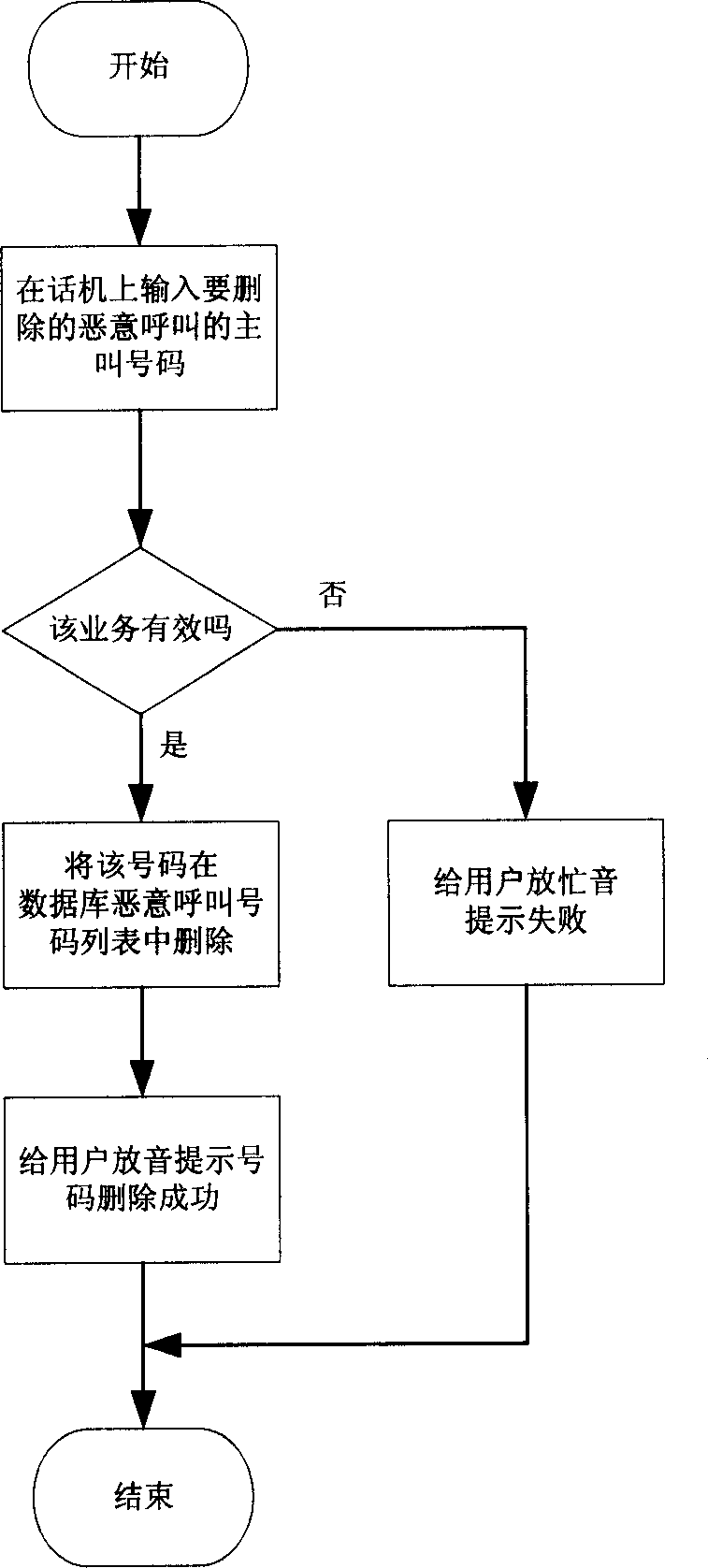
[0025] figure 1 It is a flow chart for users to add a list of malicious calling numbers. According to the method proposed by the invention, the user must first activate the service of "blocking malicious calls" before adding the list of malicious calling numbers. The user can actively apply to the telecommunications department to register the service or input a specific instruction code to the switch on the telephone to activate the service. For example, the user can enter the command code "*#23856#*" into the digital program-controlled switchboard on the phone (the command code is preset for the switchboard and notified to the user), and the switchboard will automatically activate "prevent malicious calls" after receiving the command code business. Such as figure 1 As shown, the process for the user to add the malicious calling number lis...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com