Conditional access apparatus and method
A conditional access and equipment technology, applied in the field of equipment that replays recorded data and equipment that records distributed data, and can solve problems such as unusability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
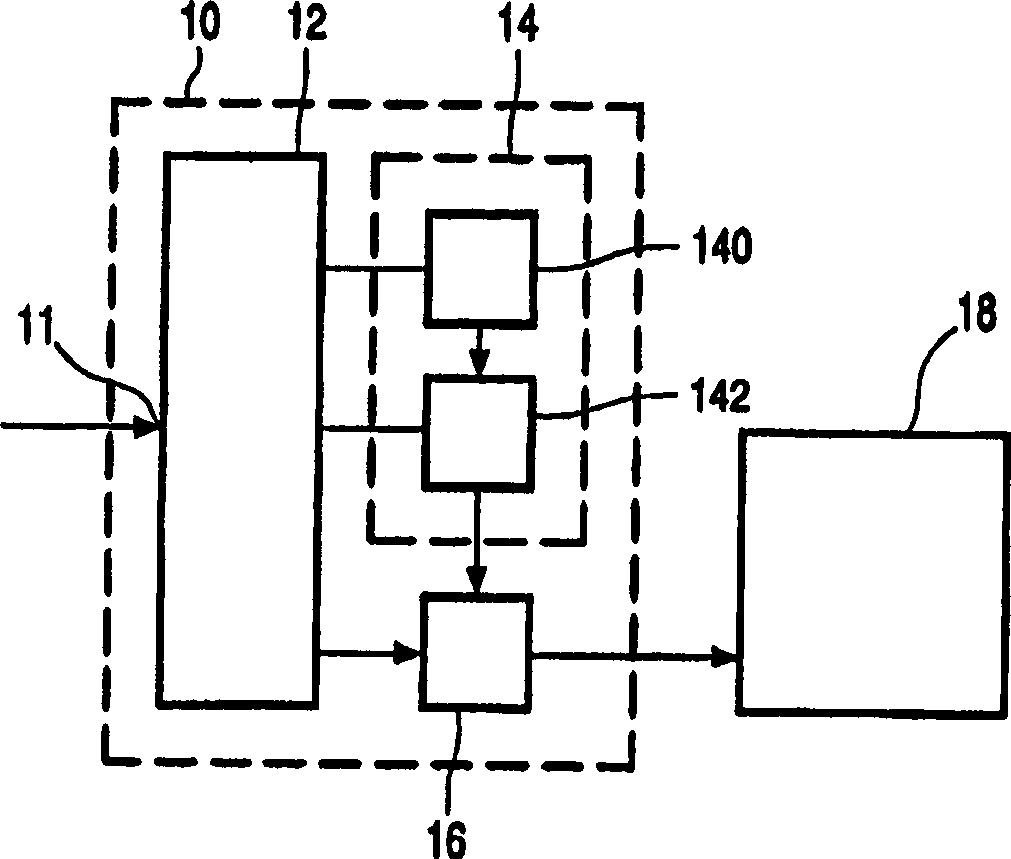
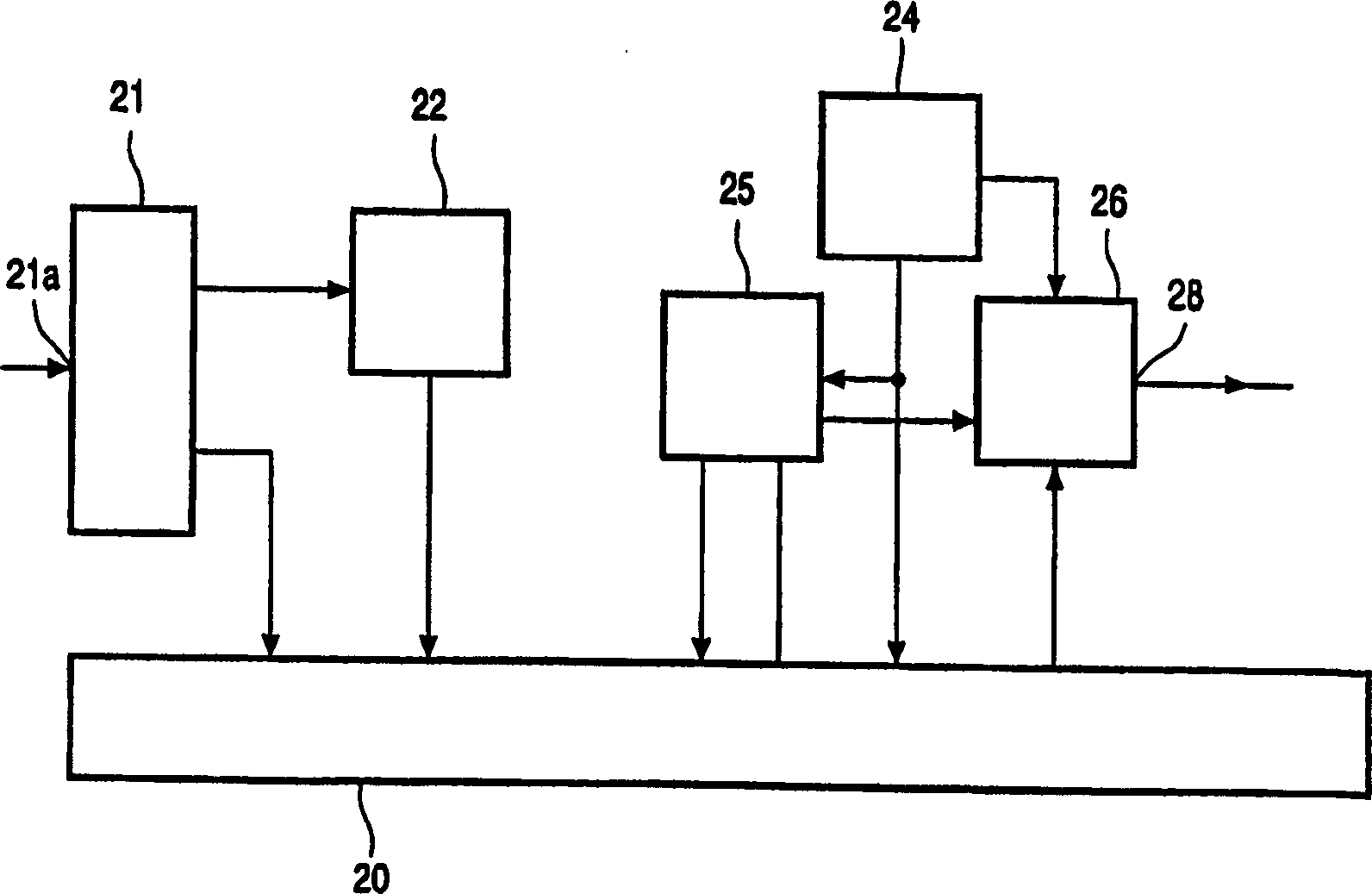
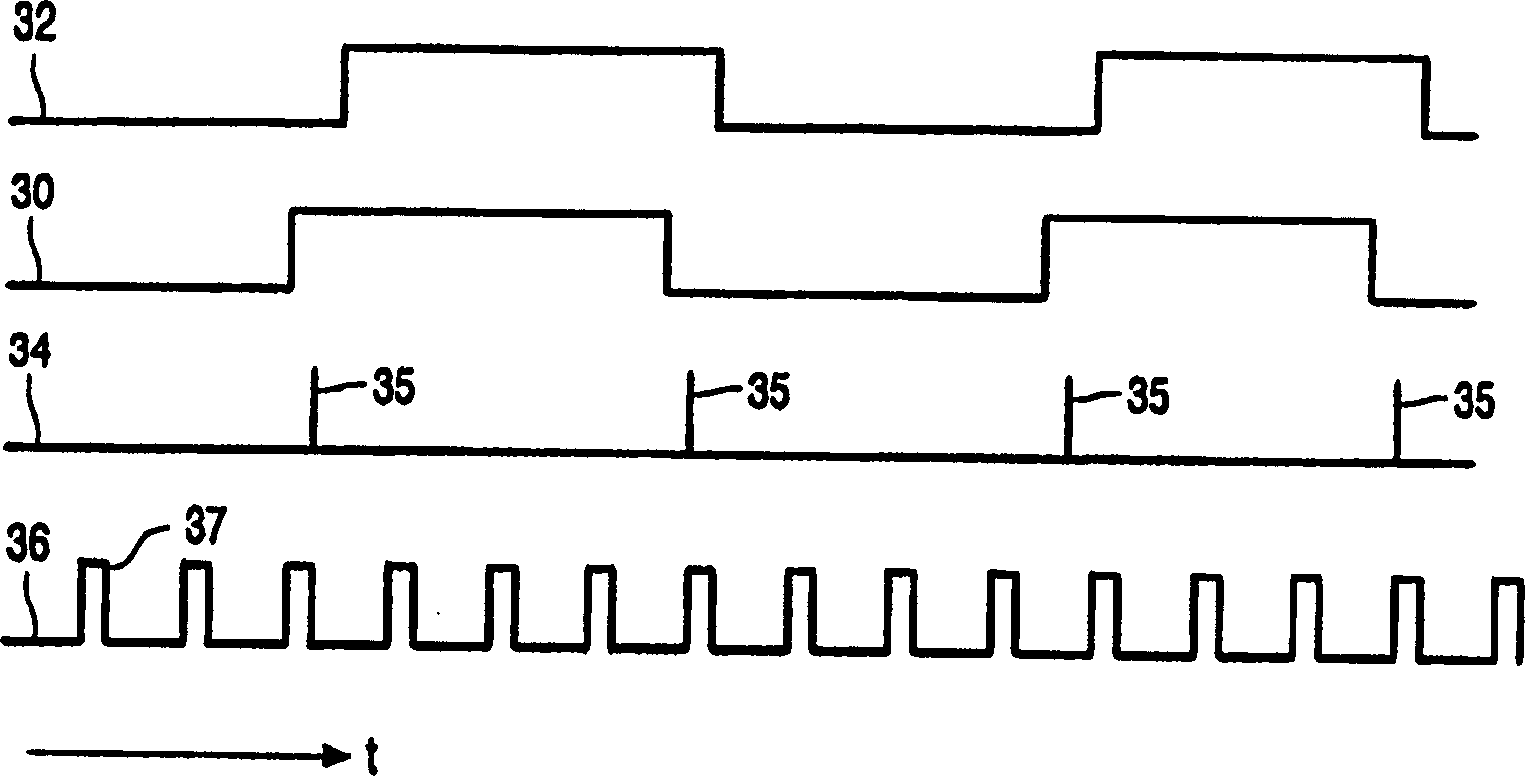
[0022] figure 1 A conditional access device is shown. The device comprises a receiving unit 10, such as a set-top box, and a presentation device 18, such as a television. The receiving unit 10 has an input 11 for receiving input signals from eg a cable TV system or a satellite broadcast receiving unit, a demultiplexer 12 , a security device 14 such as a smart card and a data decryption unit 16 . A first output of the demultiplexer 12 is coupled via a decryption unit 16 to a presentation device 18 . The security device 14 includes an EMM processing unit 140 and an ECM processing unit 142 . The second and third outputs of the demultiplexer 12 are coupled to the EMM processing unit 140 and the ECM processing unit 142, respectively. EMM processing unit 140 has an output coupled to ECM processing unit 142 . ECM processing unit 142 has an output coupled to decryption unit 16 . (Although EMM processing unit 140 and ECM processing unit 142 are shown separately, their functions ma...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com