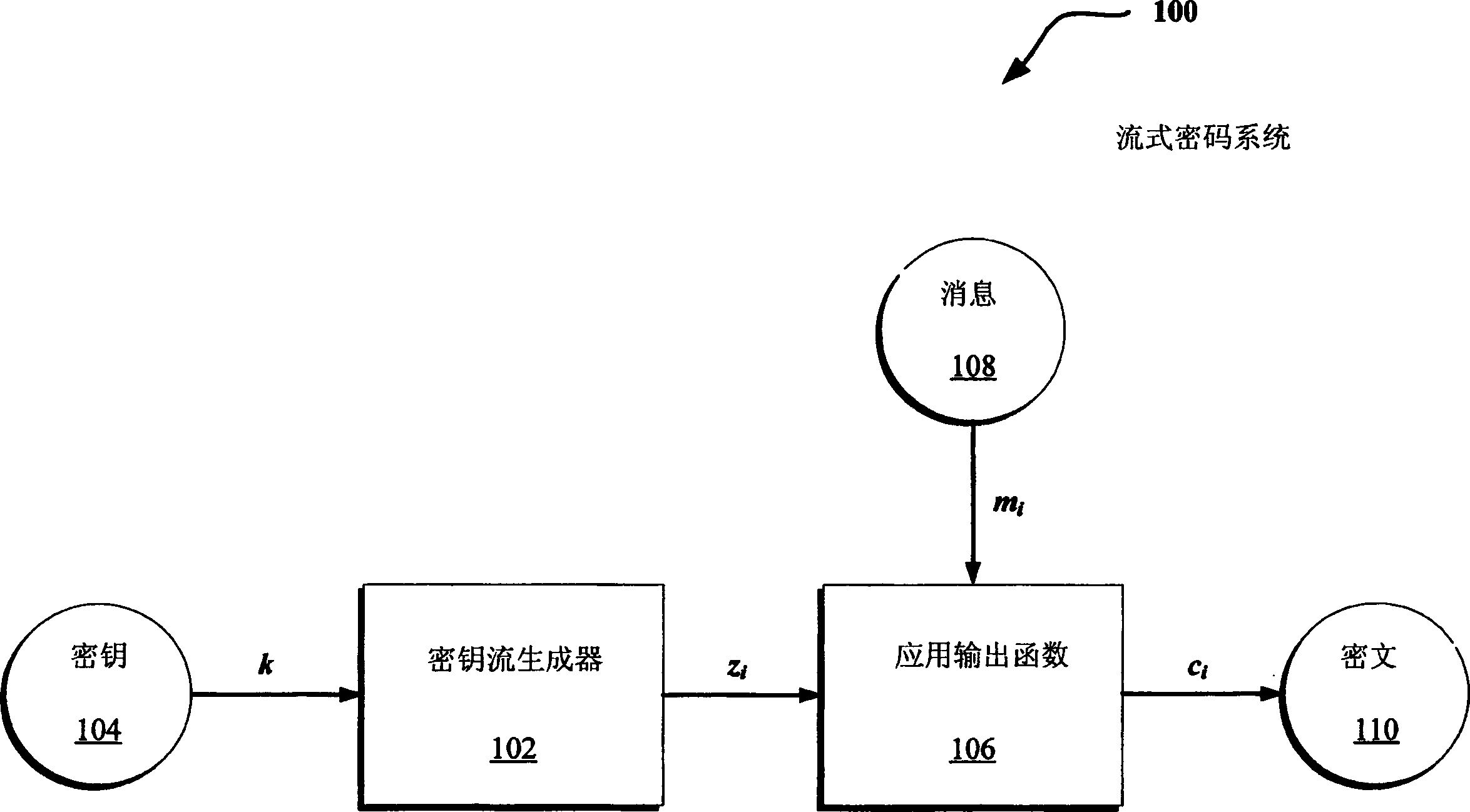
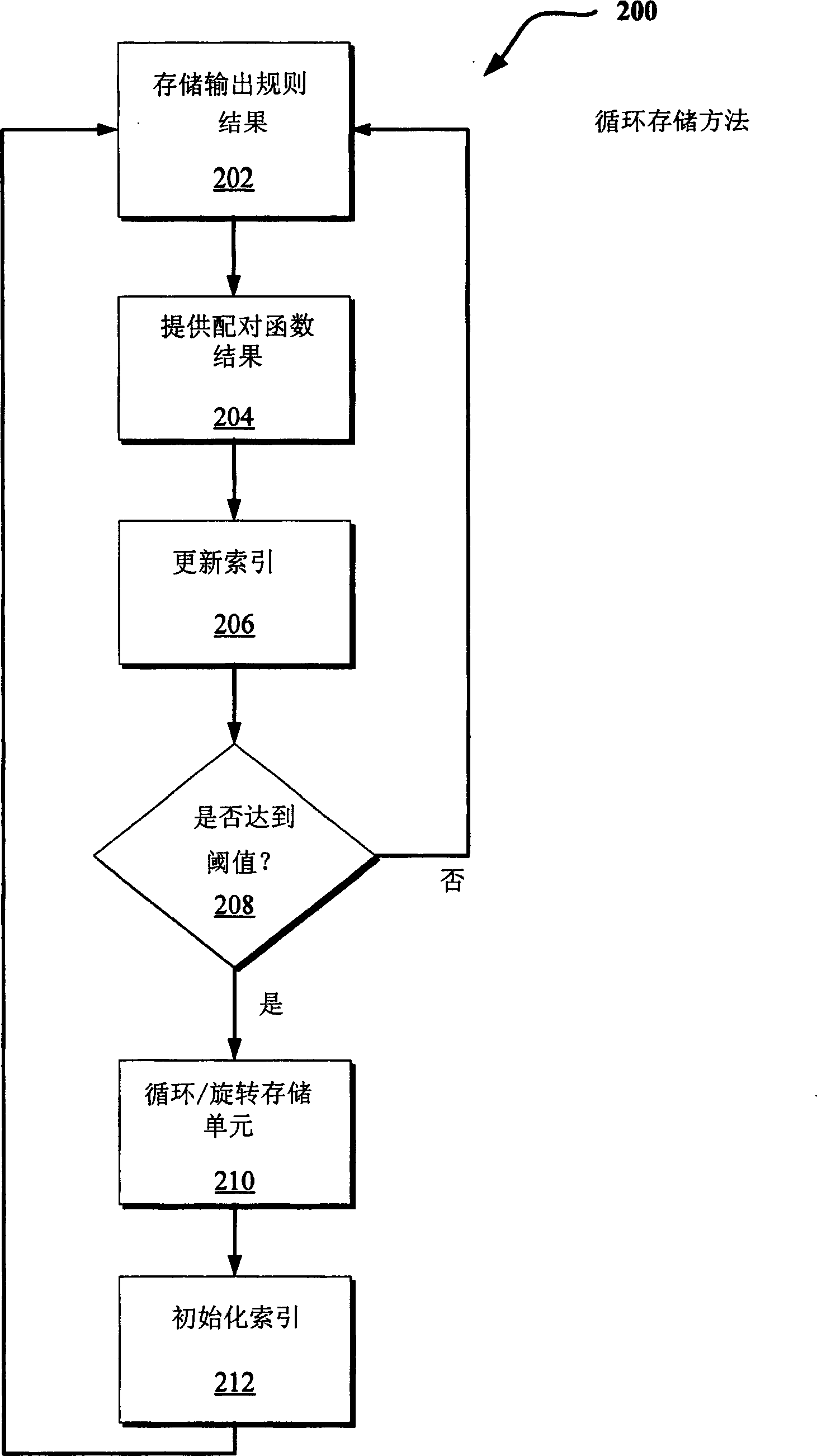
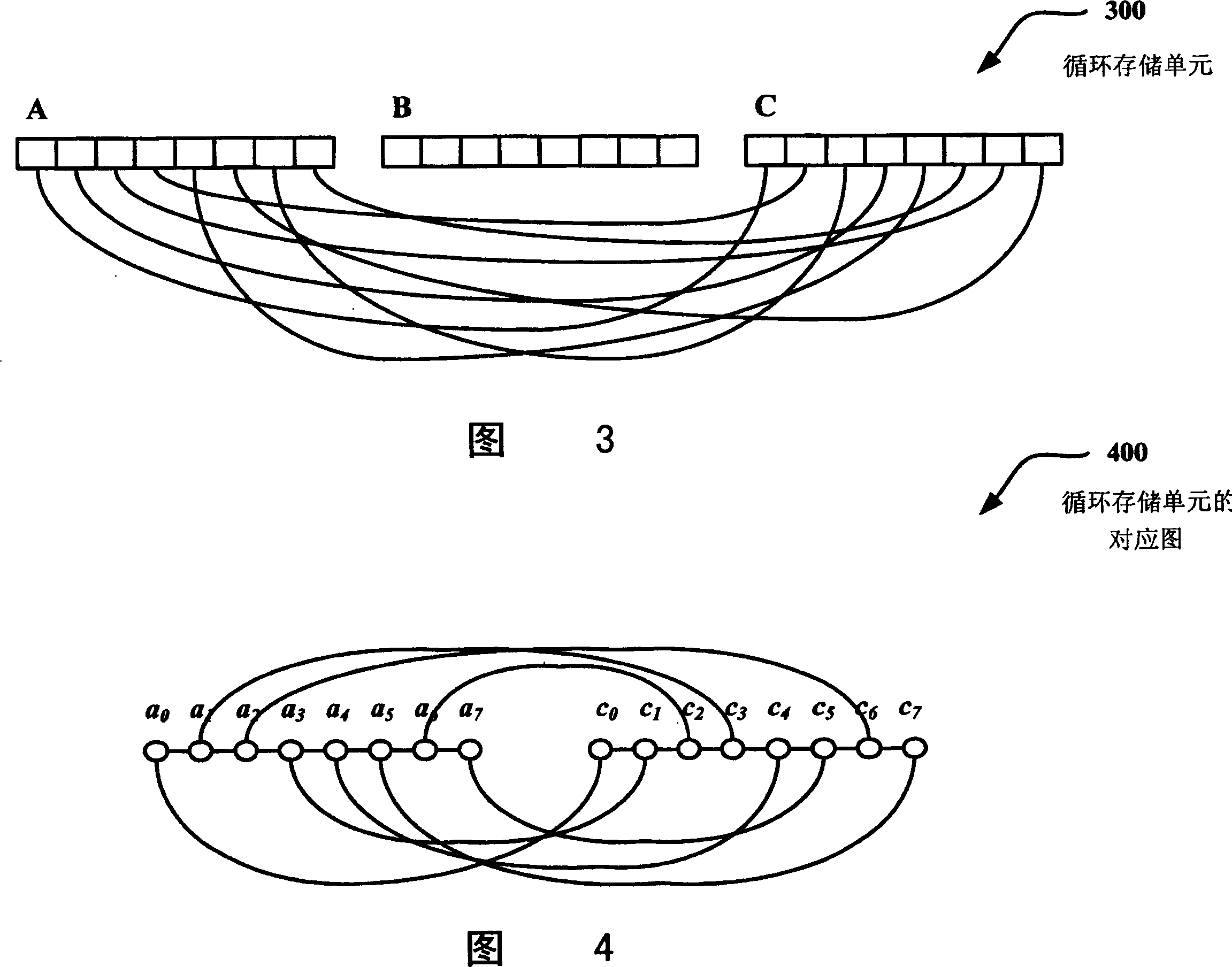
Stream cipher design with revolving buffers
A cryptographic and streaming technology, applied in the field of cryptography, which can solve the problem of encryption/decryption of secure data that cannot be streamed cryptographically
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The following discussion assumes the reader is familiar with cryptography. For a basic introduction to cryptography, the reader is referred to A. Menezes, P. van Oorschot and S. Vanstone, entitled Handbook of Applied Cryptography (Handbook of Applied Cryptography))) 5th Edition, published by CRC Issued by the company.
[0020] The following disclosure describes efficient techniques for limiting the local (or short-term) dependencies associated with stream cipher keystream generator outputs. These techniques are all based on pairing generator output values that are far enough apart that they can be considered uncorrelated. In one implementation, the absence of short periods in the pairing graph greatly limits linear and algebraic attacks, in part because an attacker cannot separate relatively short equations containing only a few variables.
[0021] In one implementation, relatively simple updates (discussed further below in the section entitled "Update Rules") are c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com