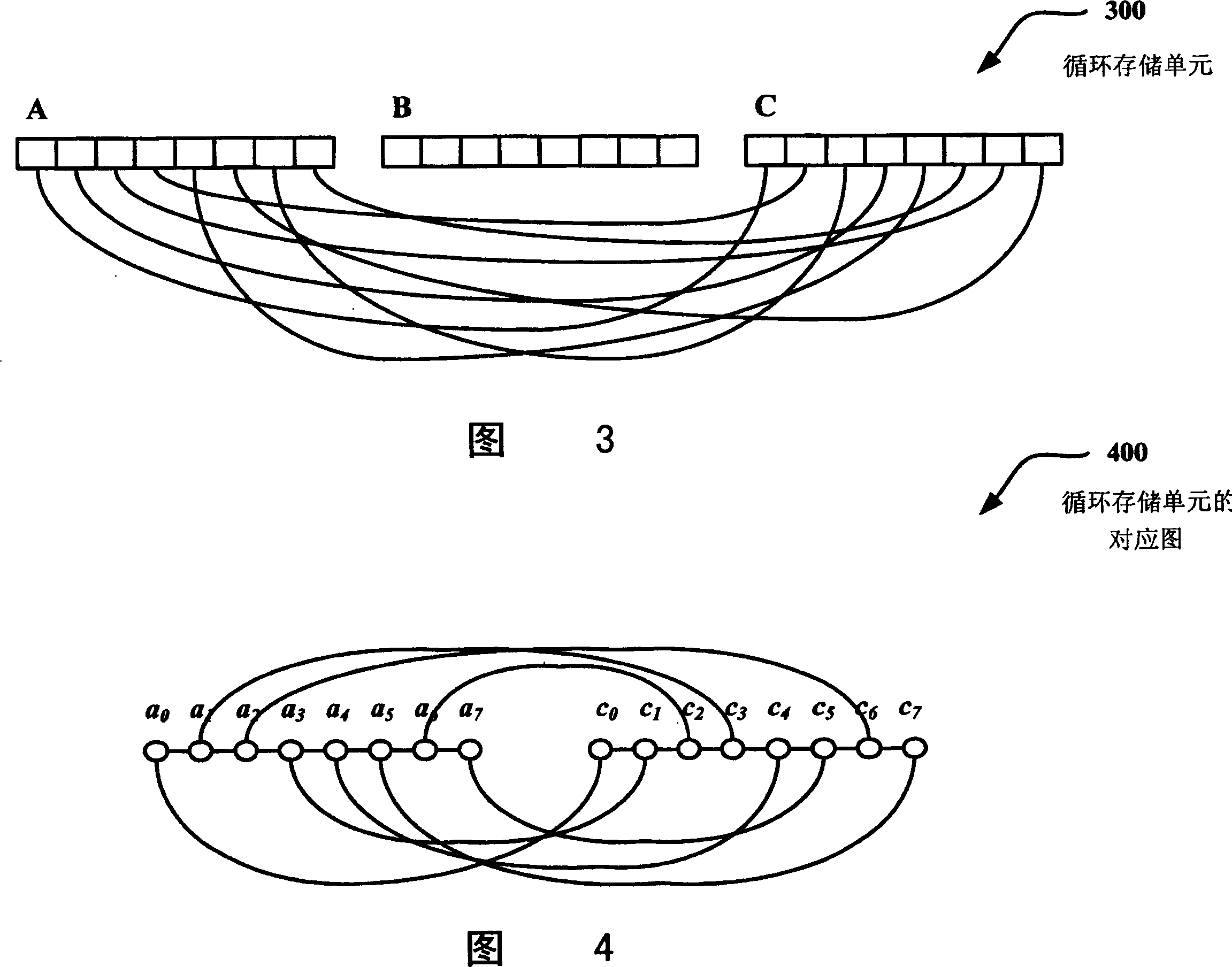
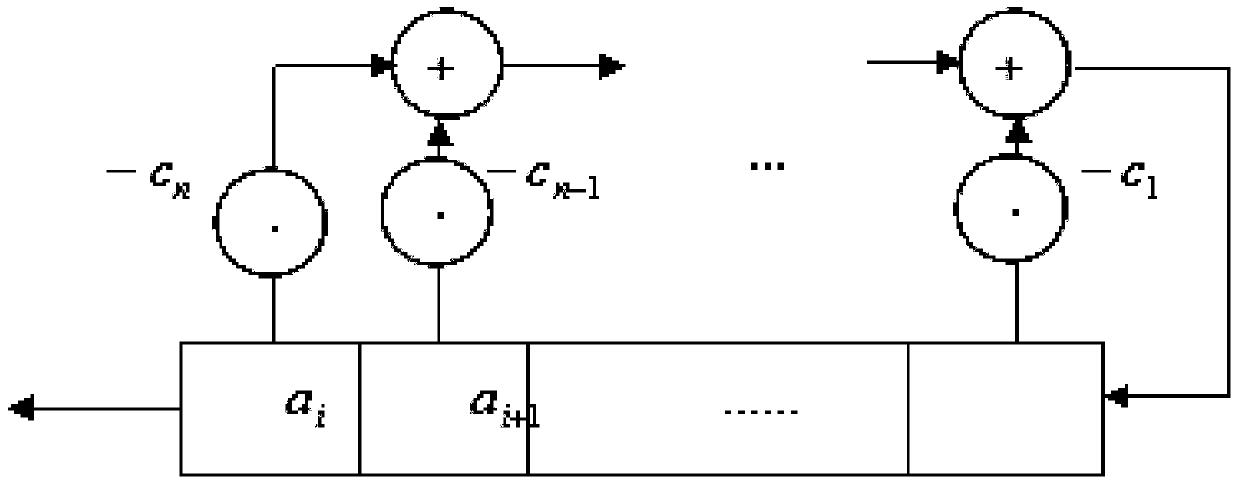
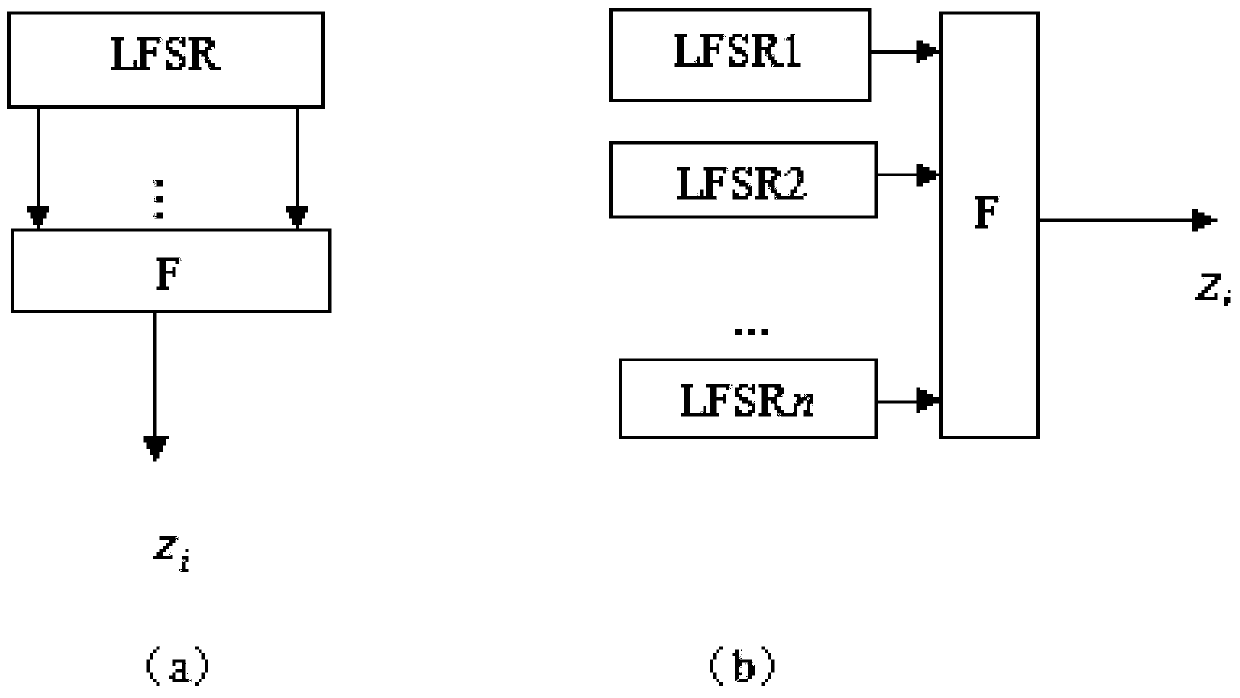
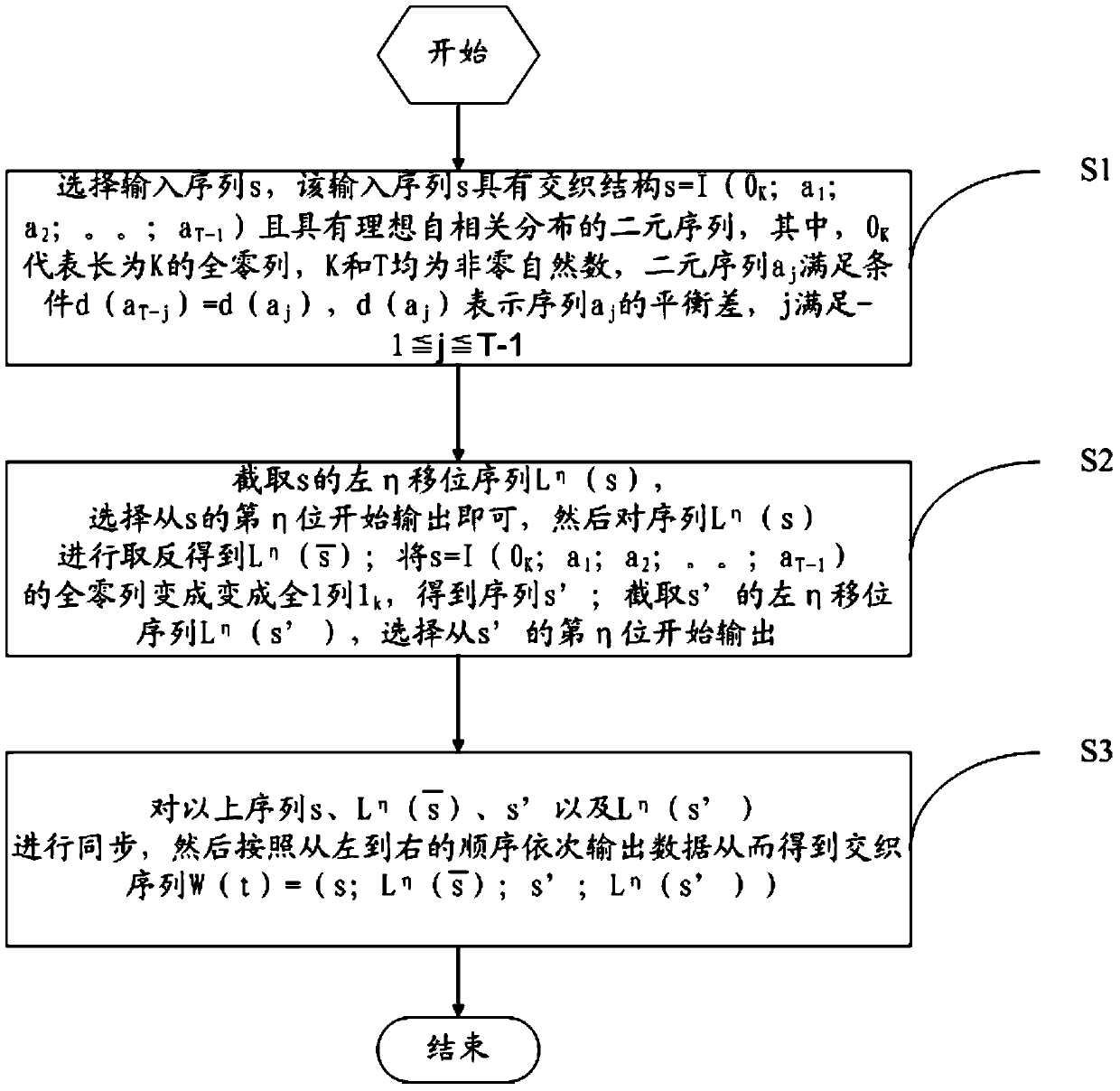
Patents
Literature
41 results about "Keystream generator" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
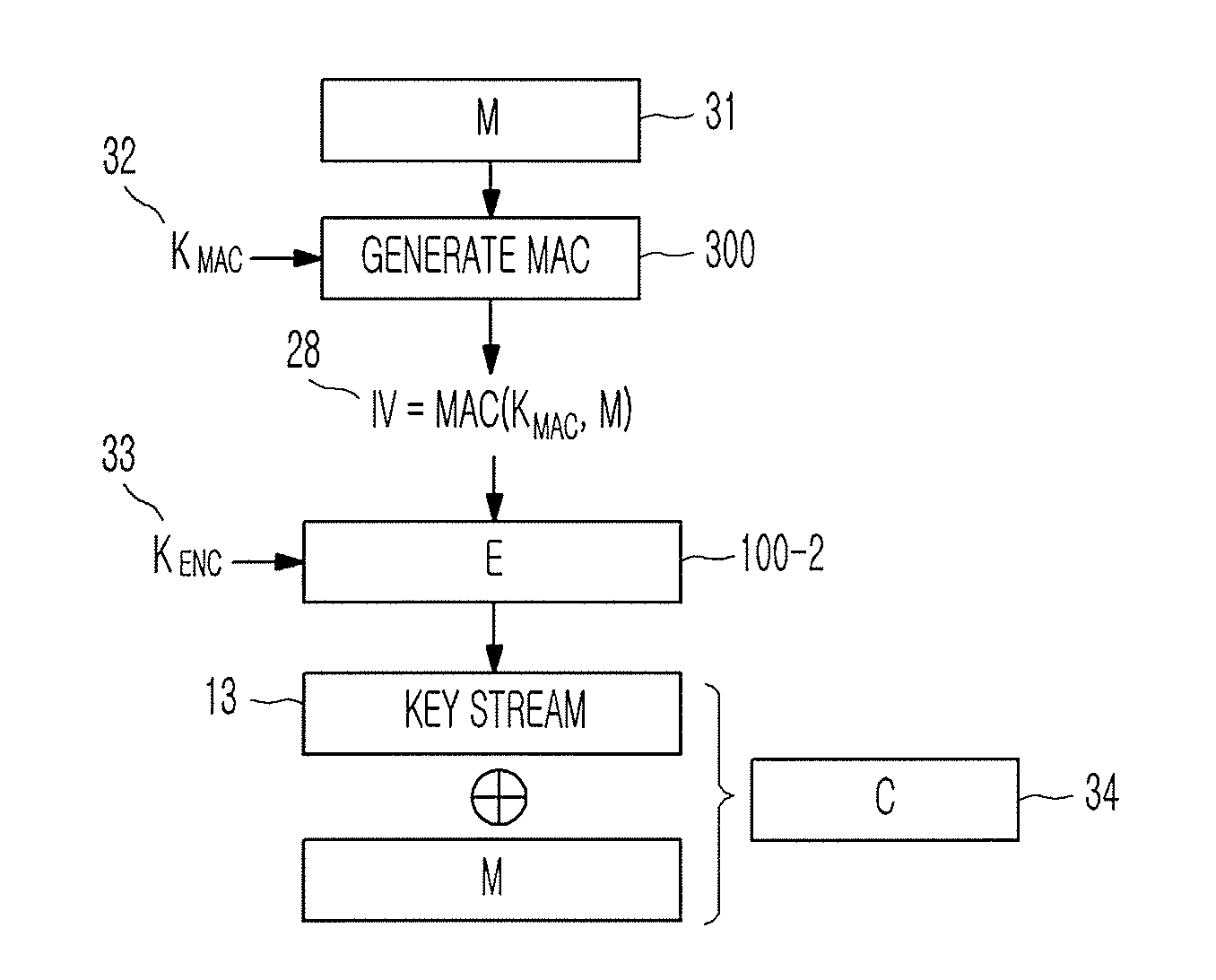
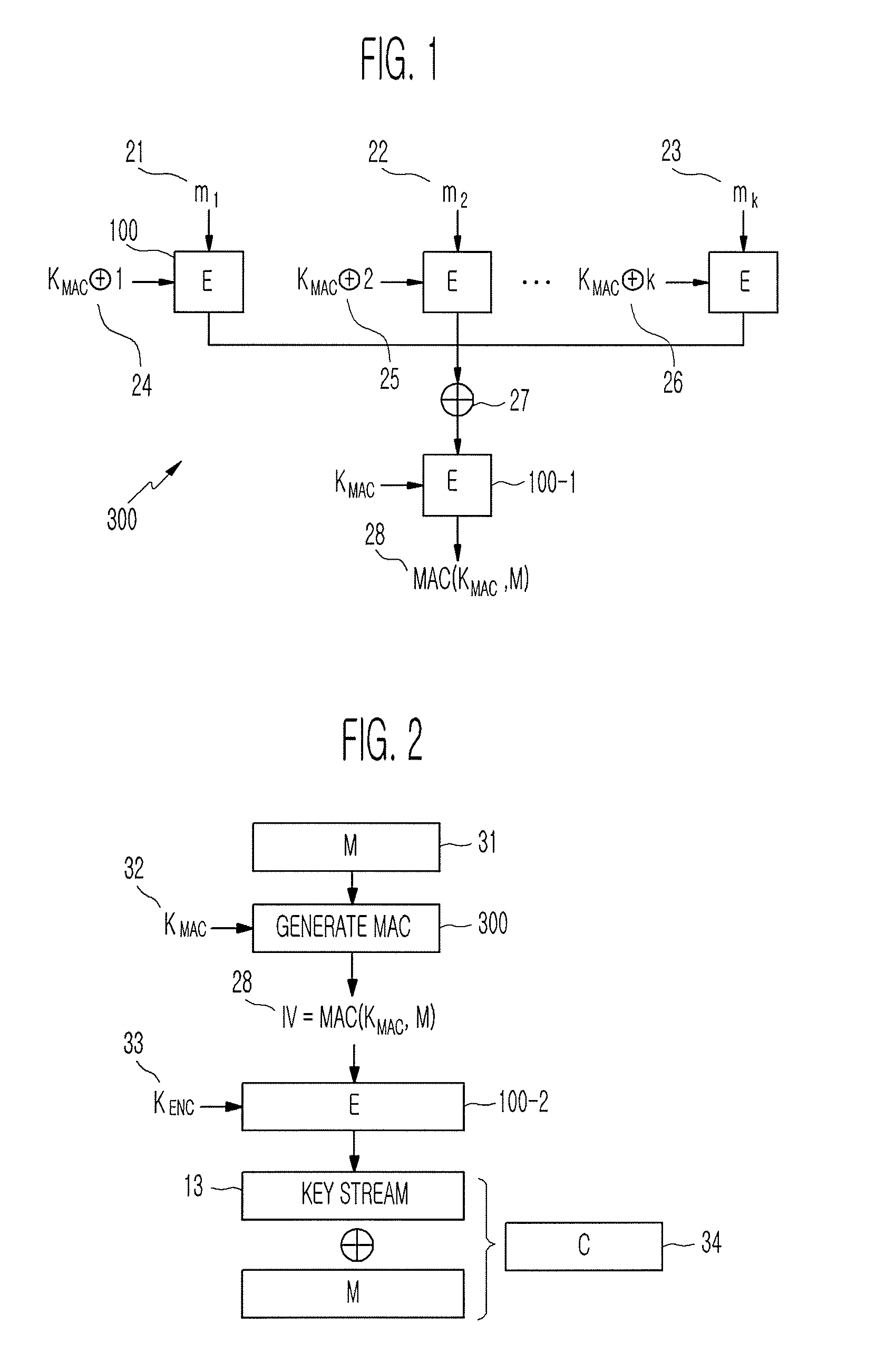
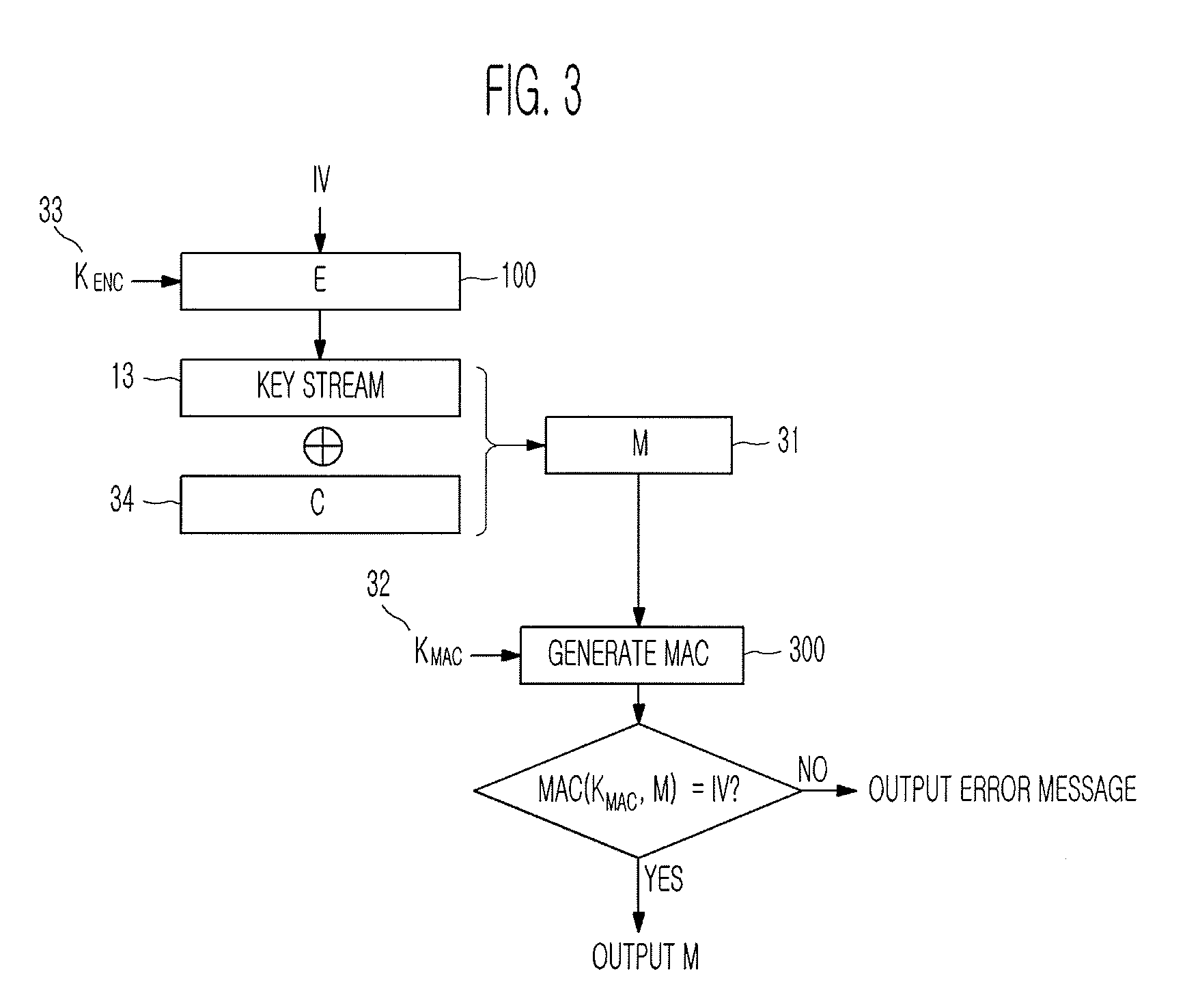
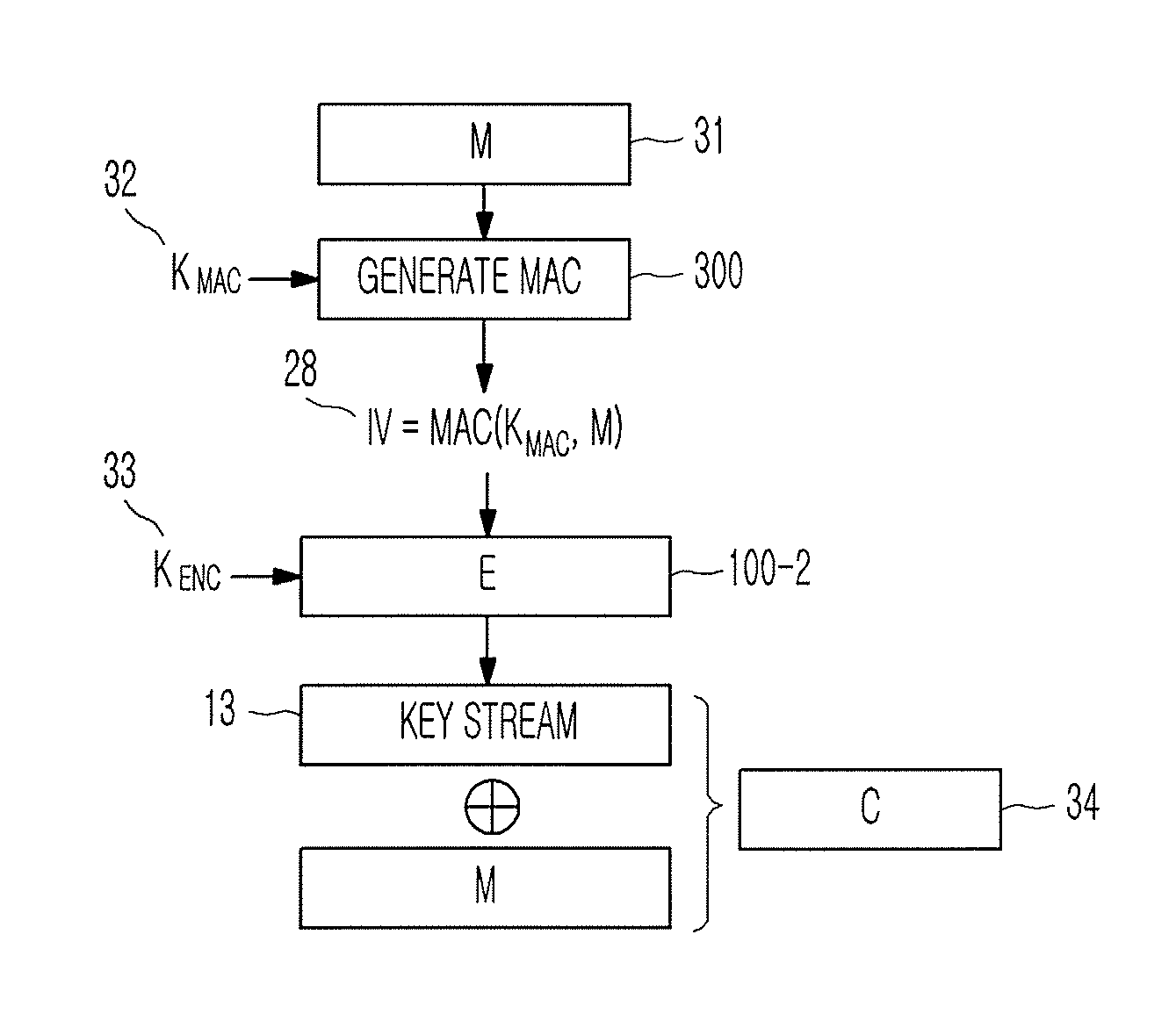
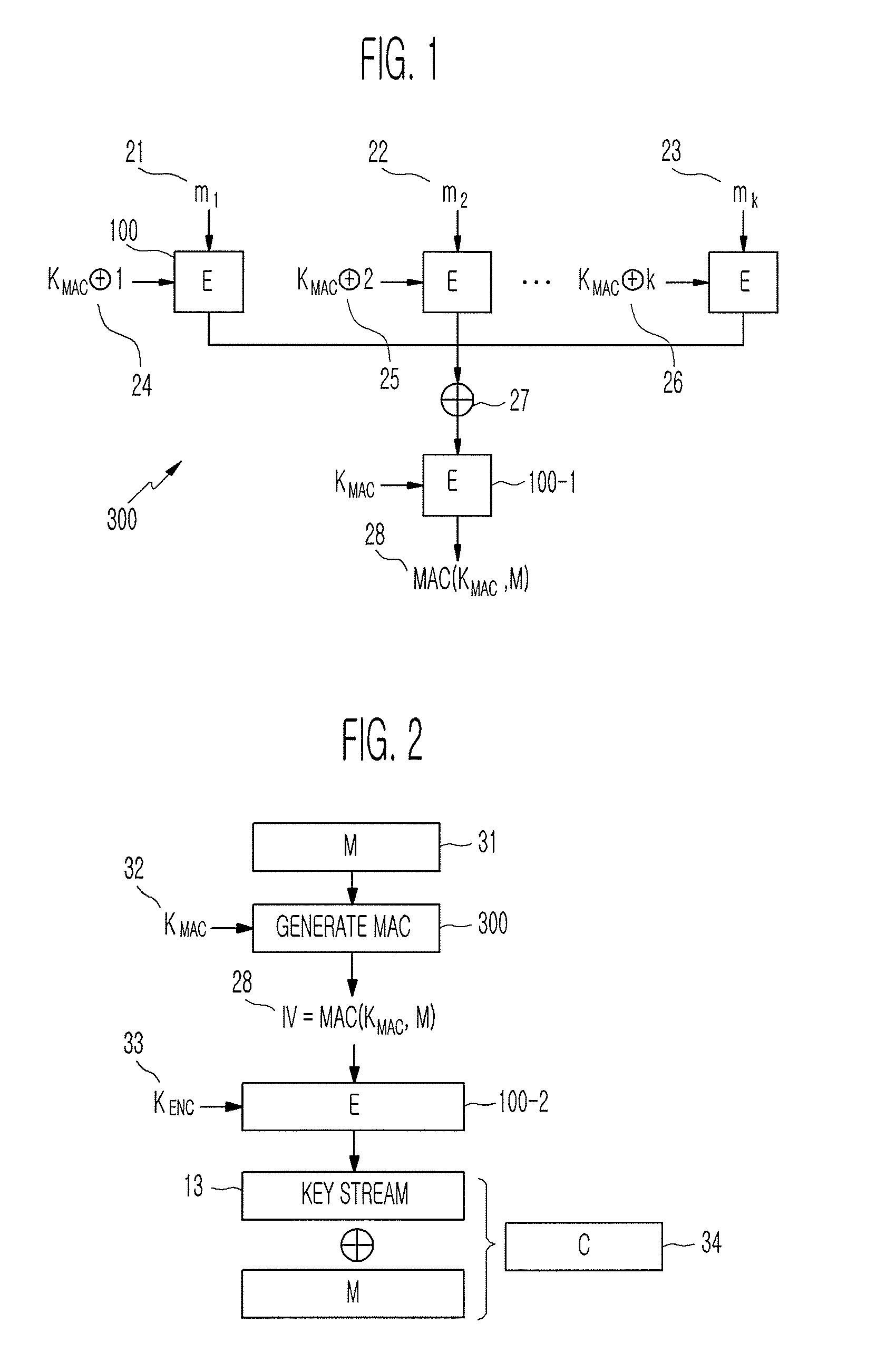
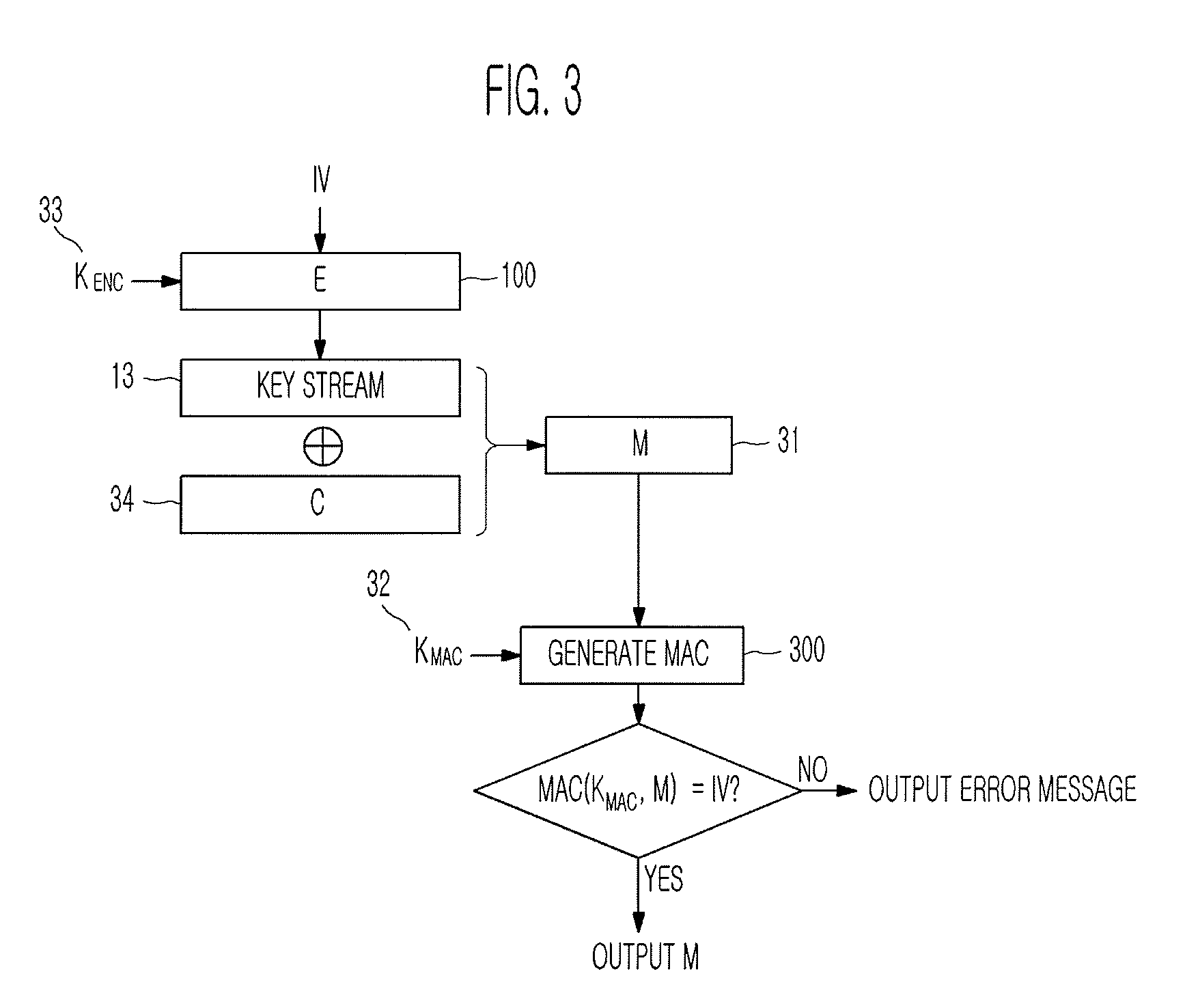
Method of generating message authentication code using stream cipher and authentication/encryption and authentication/decryption methods using stream cipher
InactiveUS20080112561A1Secret communicationSecuring communicationComputer hardwareHash-based message authentication code
Provided are a method of generating a Message Authentication Code (MAC) using a stream cipher, and authentication / encryption and authentication / decryption methods using a stream cipher.According to the methods, authentication / encryption is performed using a MAC generated using a stream cipher as an initialization vector of the stream cipher. Therefore, it is unnecessary to use a random number generation algorithm to generate the initialization vector, and thus implementation efficiency can be improved.In addition, upon generation of a MAC, a plurality of key stream generators perform computation for a plurality of message blocks, respectively. Therefore, the message blocks are computed in parallel at a time, and thus computation efficiency is excellent.
Owner:NAINFOX CO LTD
Dual-mode variable key length cryptography system
InactiveUS20090103726A1More robustMore secureSynchronising transmission/receiving encryption devicesKey sizeTime transfer
Owner:LUCENT TECH INC
Cryptographic combiner using two sequential non-associative operations
InactiveUS7277543B1Minimal increase of resourceDigital computer detailsUnauthorized memory use protectionPlaintextComputer hardware
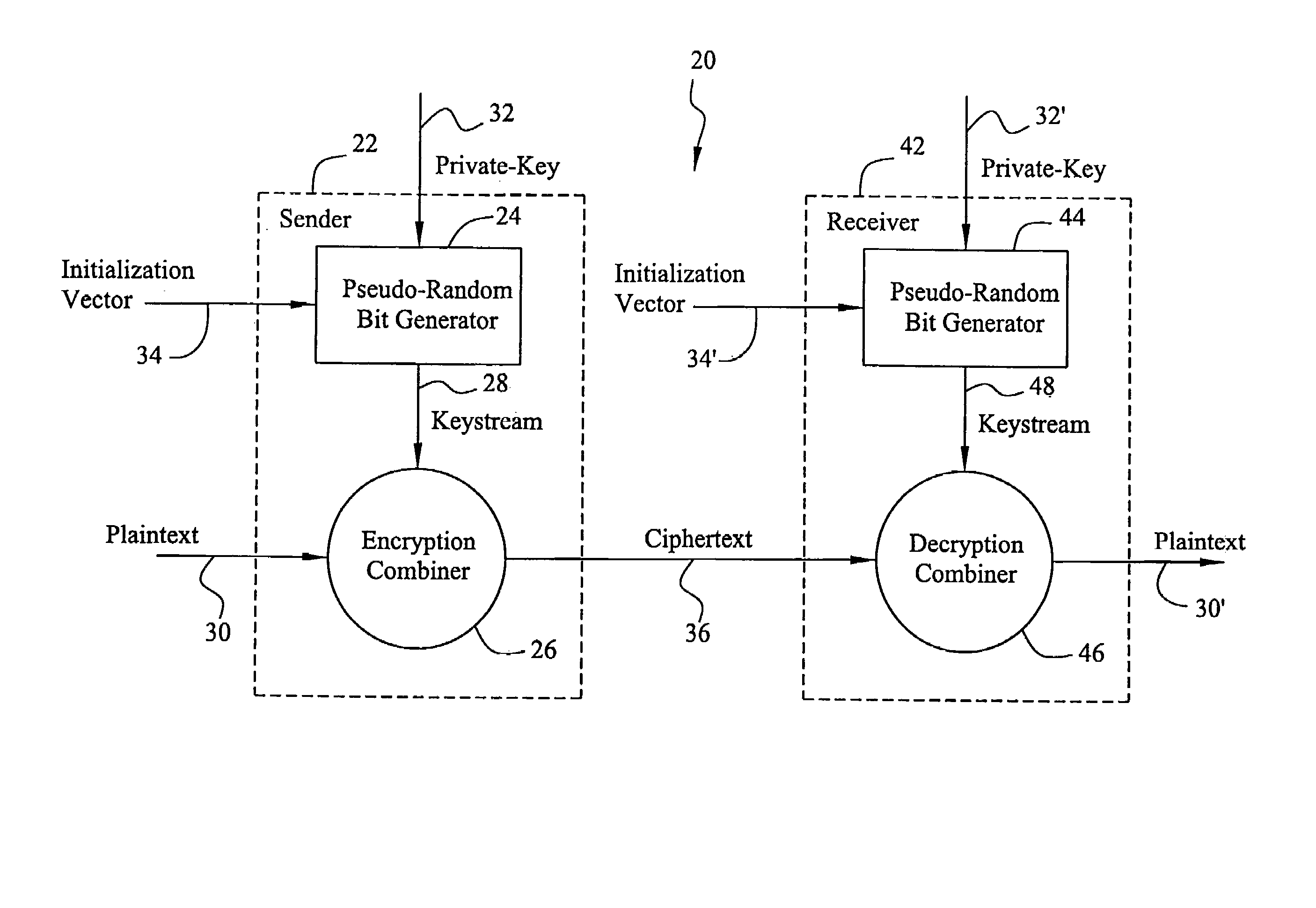
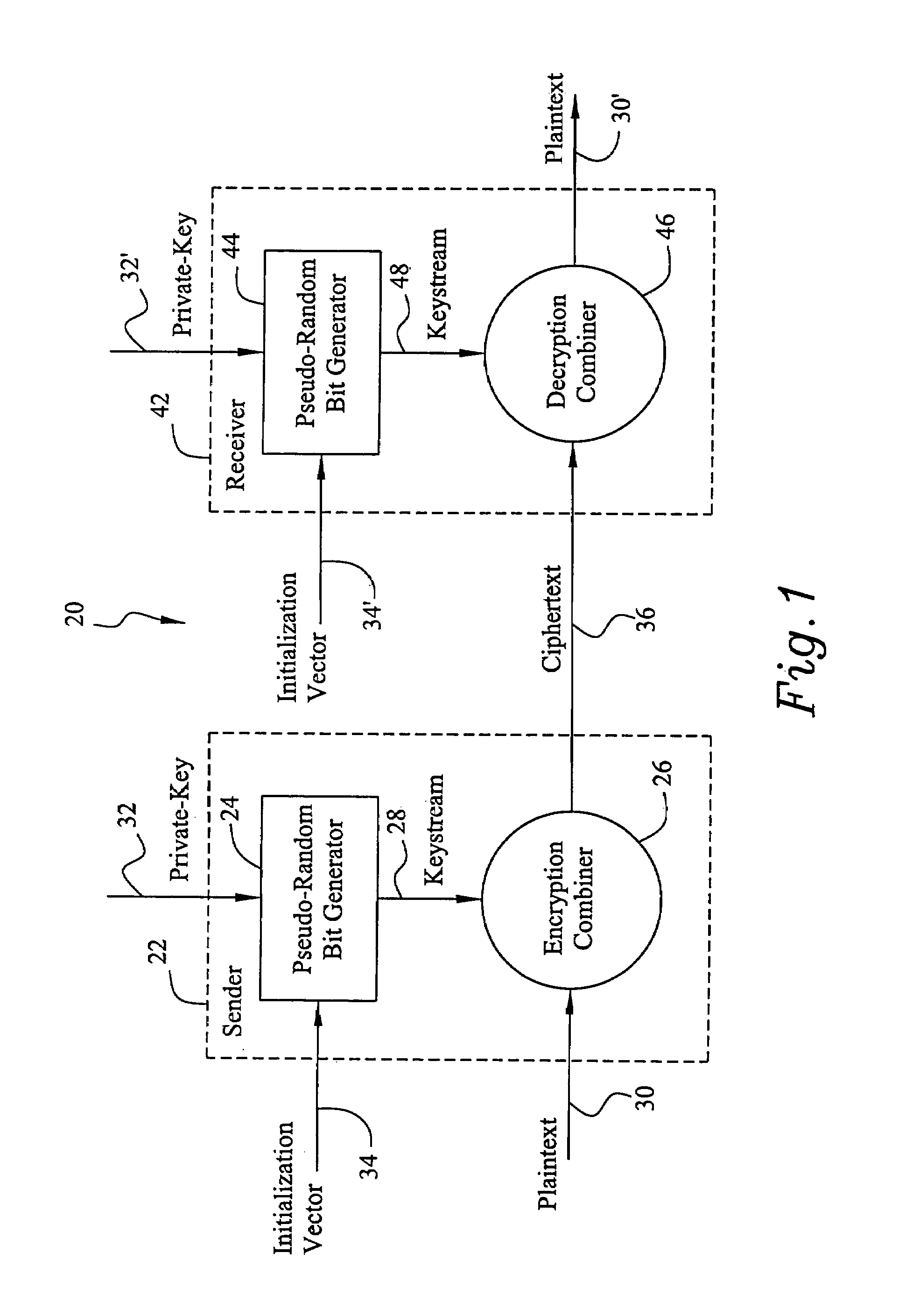
A stream cipher cryptosystem includes a keystream generator receiving a key and providing a keystream. A cryptographic combiner combines a first binary data sequence and the keystream with two non-associative operations to provide a second binary data sequence. In encryption operations, the cryptographic combiner is an encryption combiner and the first binary data sequence is a plaintext binary data sequence and the second binary data sequence is a ciphertext binary data sequence. In decryption operations, the cryptographic combiner is a decryption combiner and the first binary data sequence is a ciphertext binary data sequence and the second binary data sequence is a plaintext binary data sequence.
Owner:HONEYWELL INT INC
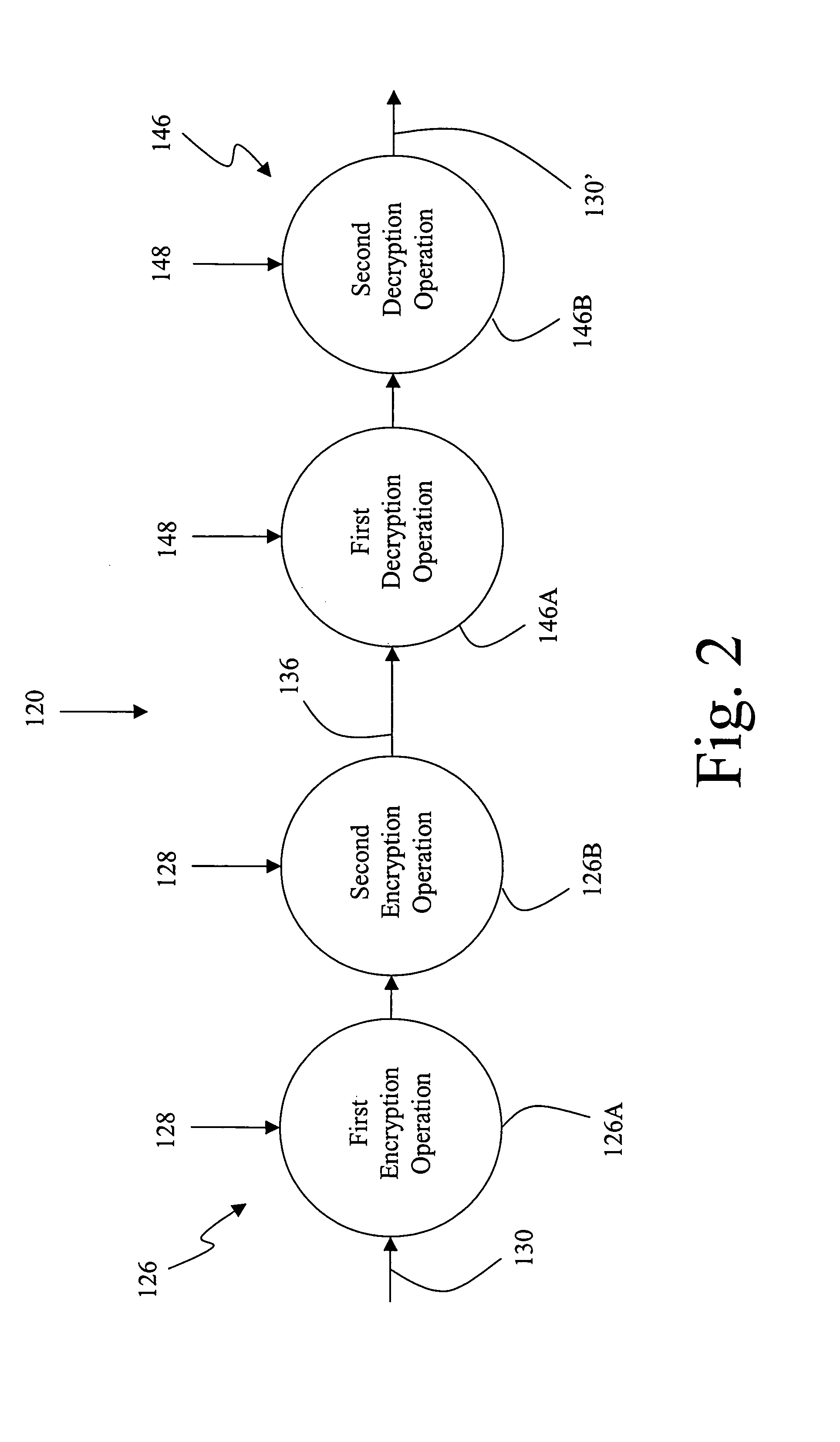
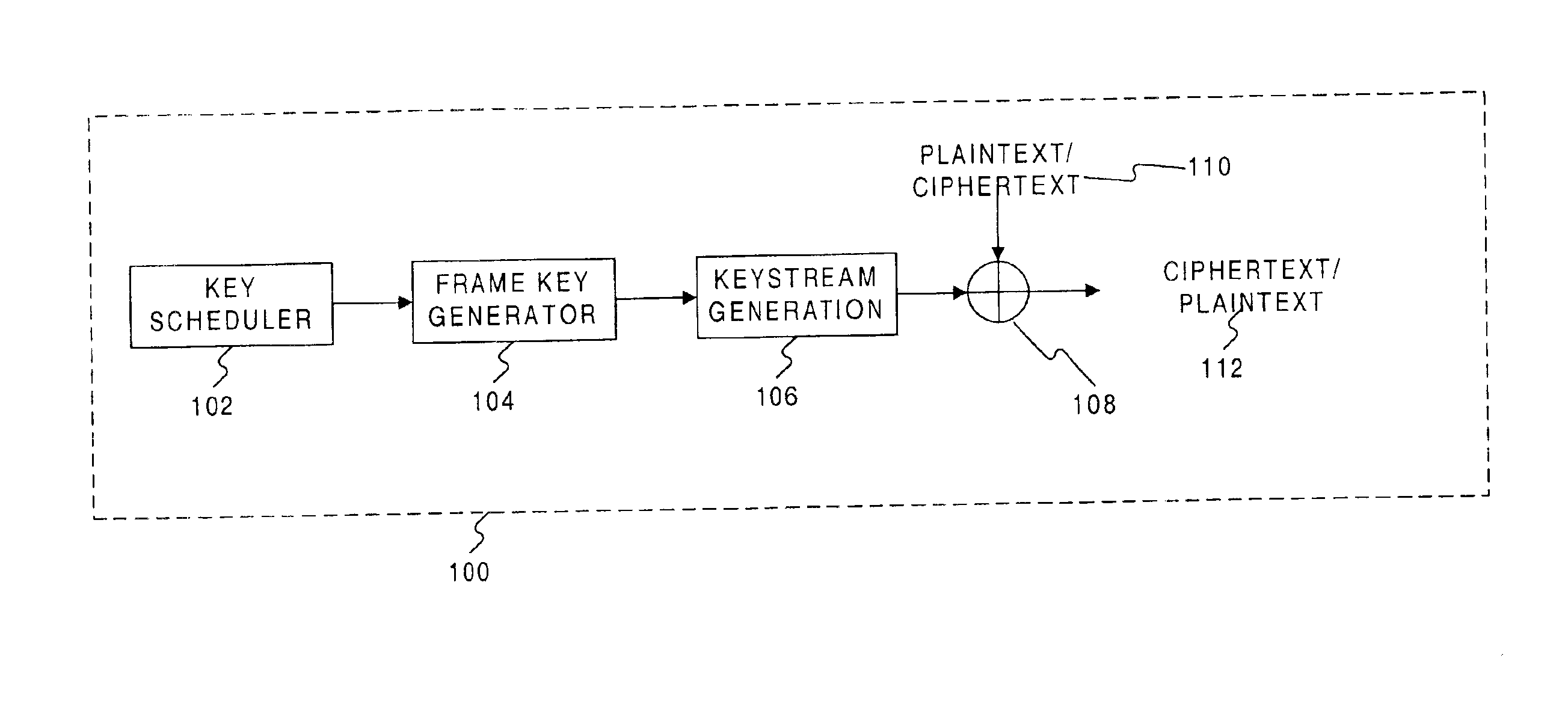
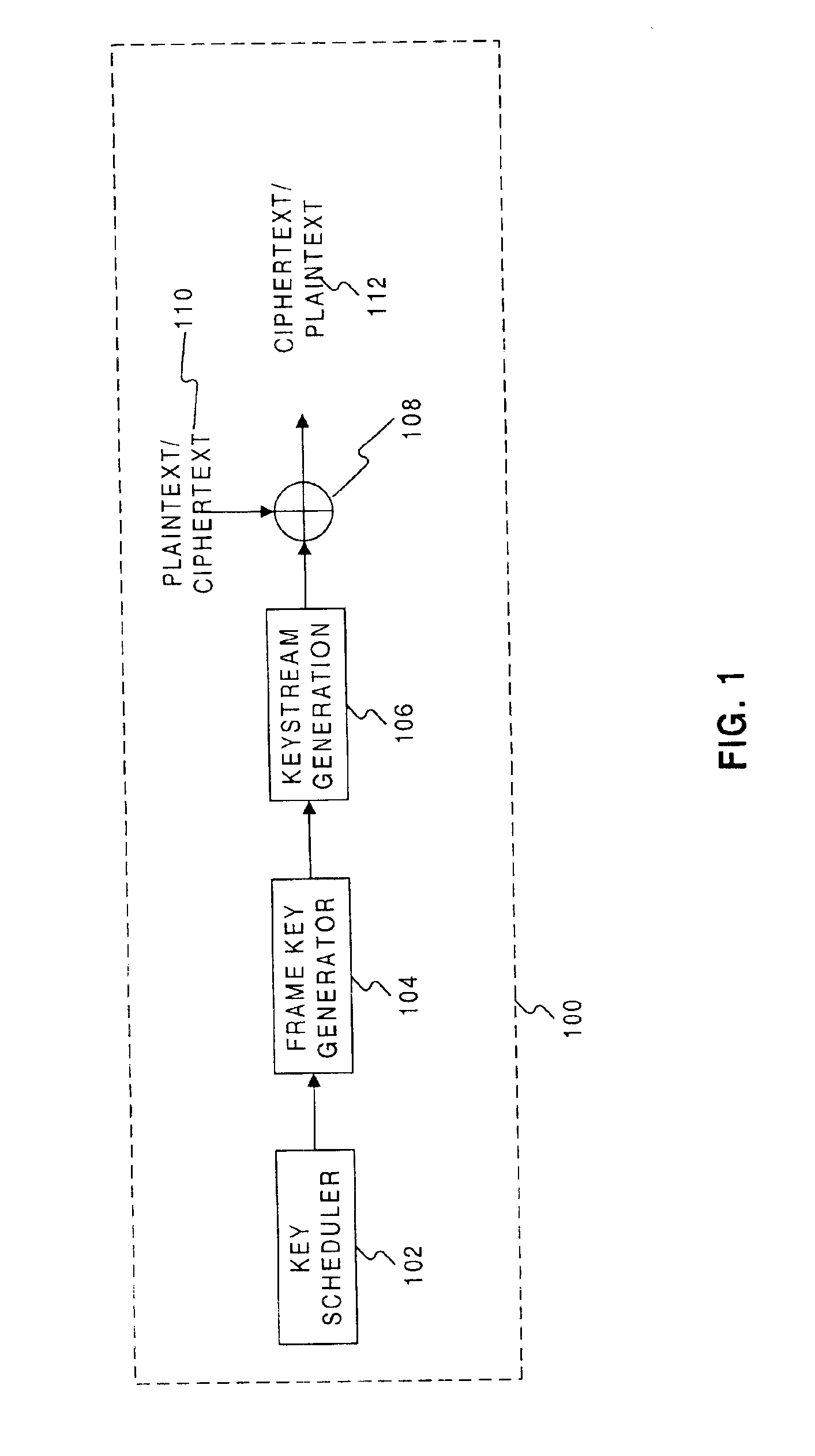
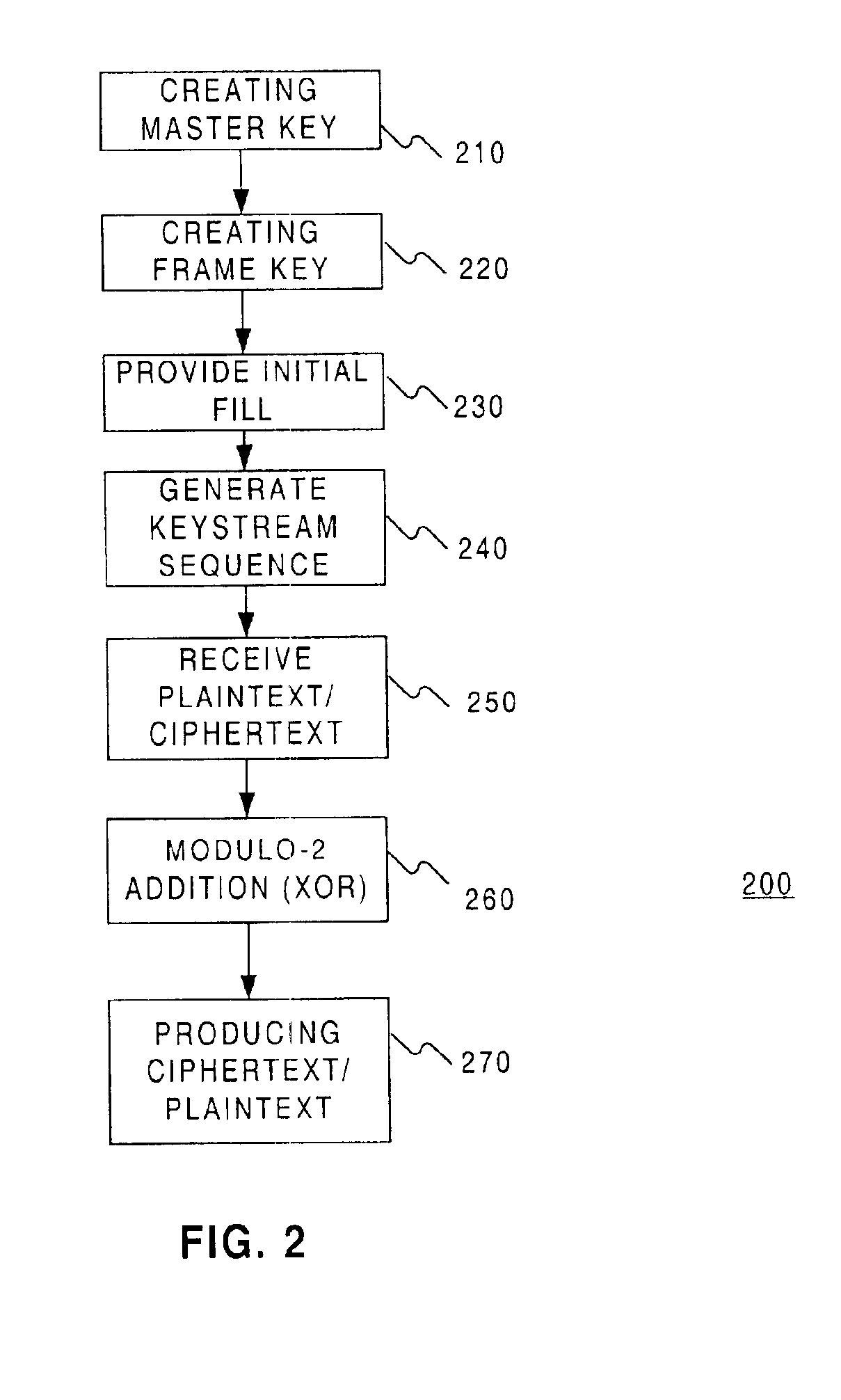
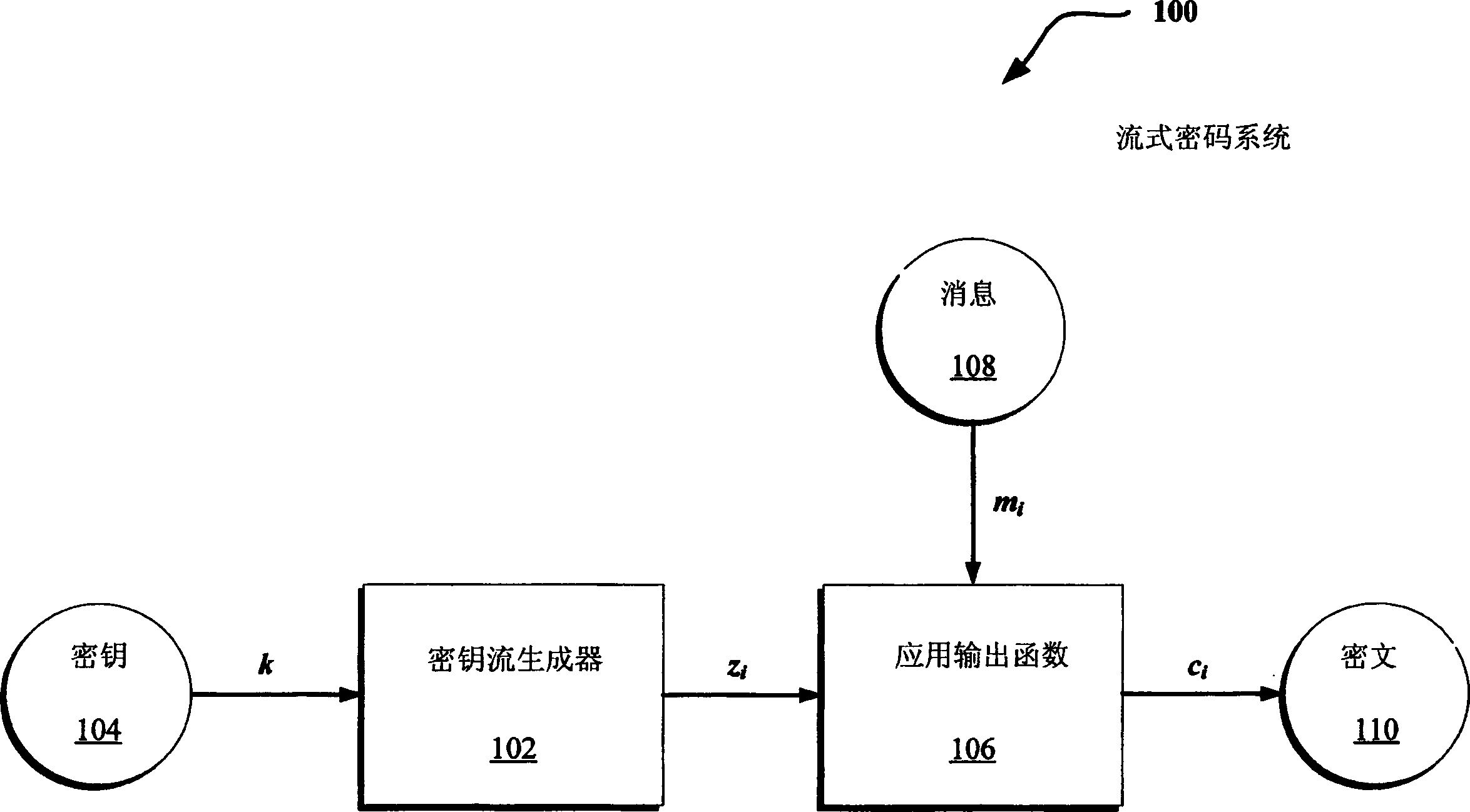
Stream-cipher method and apparatus
Methods and systems are provided for processing information. In one embodiment, there is provided a method, providing a frame key based on a master key and a frame number of a frame of information to a keystream generator as an initial fill for one or more registers of the keystream generator such that the initial fill establishes a state for the one or more registers of the keystream generator; and generating, at the keystream generator, a keystream sequence based on the state established by the initial fill, wherein the keystream sequence includes a modulo-2 sum of a lagged-Fibonacci sequence and a pseudo-random sequence produced by a filter generator.
Owner:VERIZON LAB +1
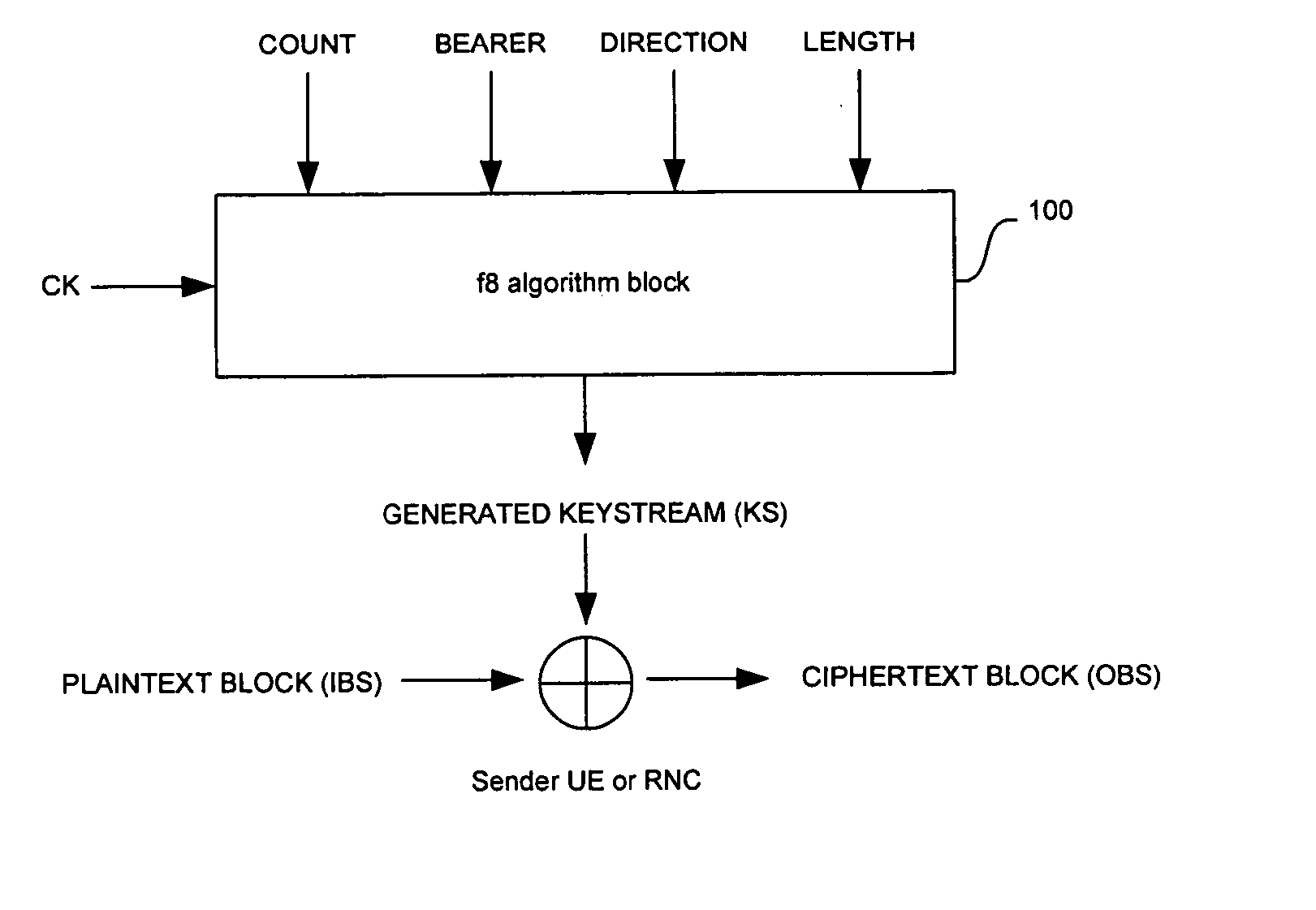
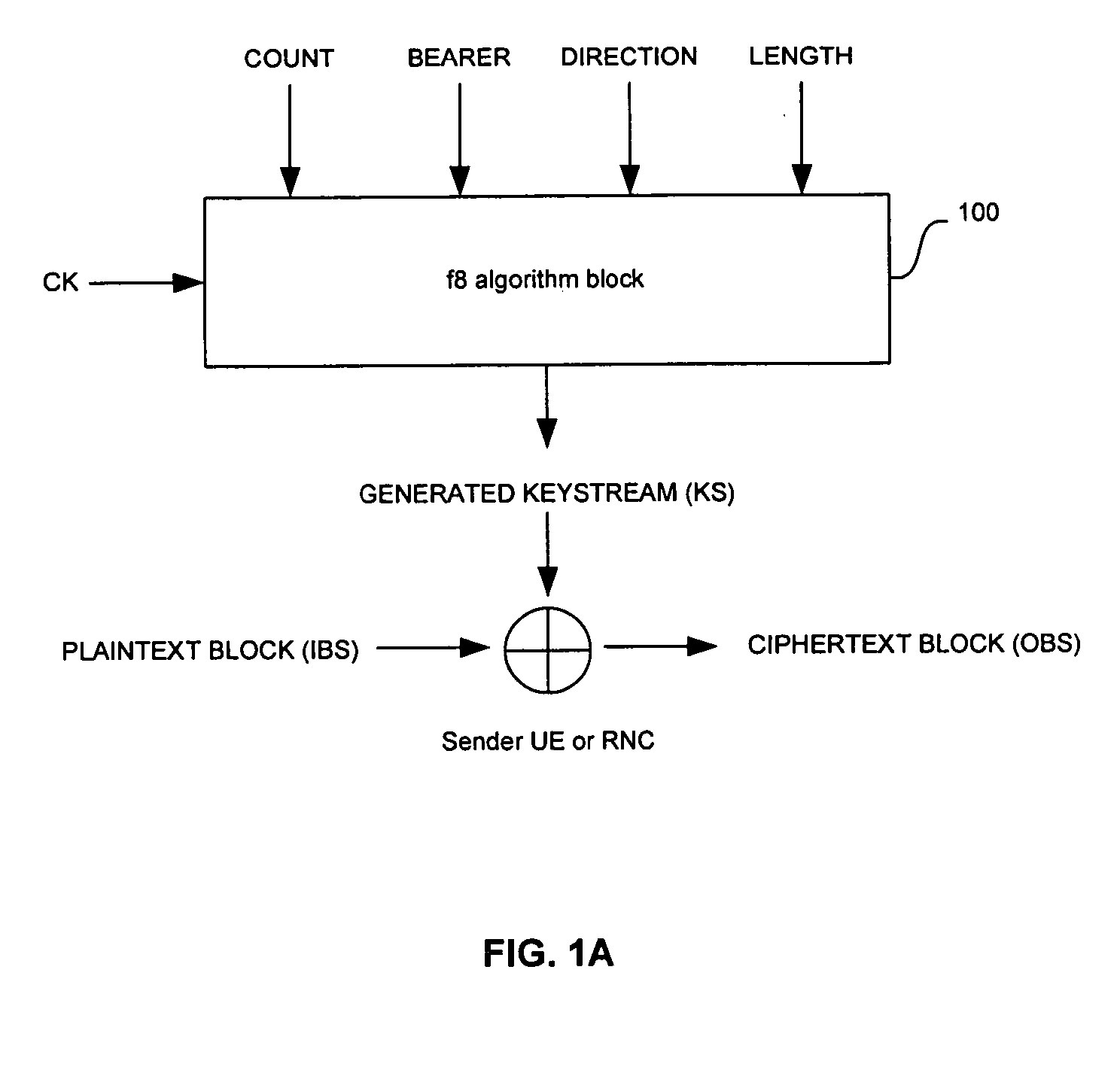
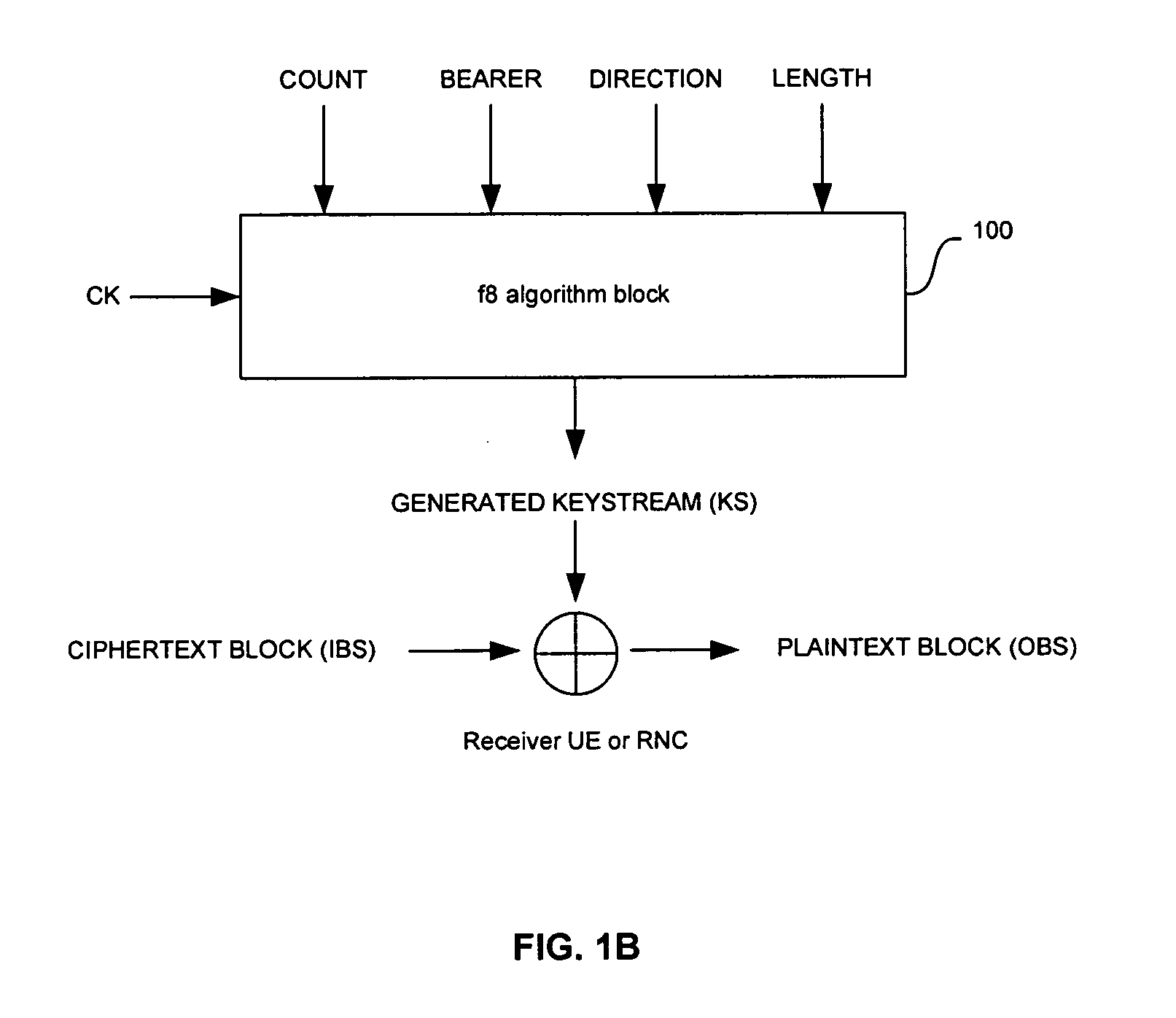
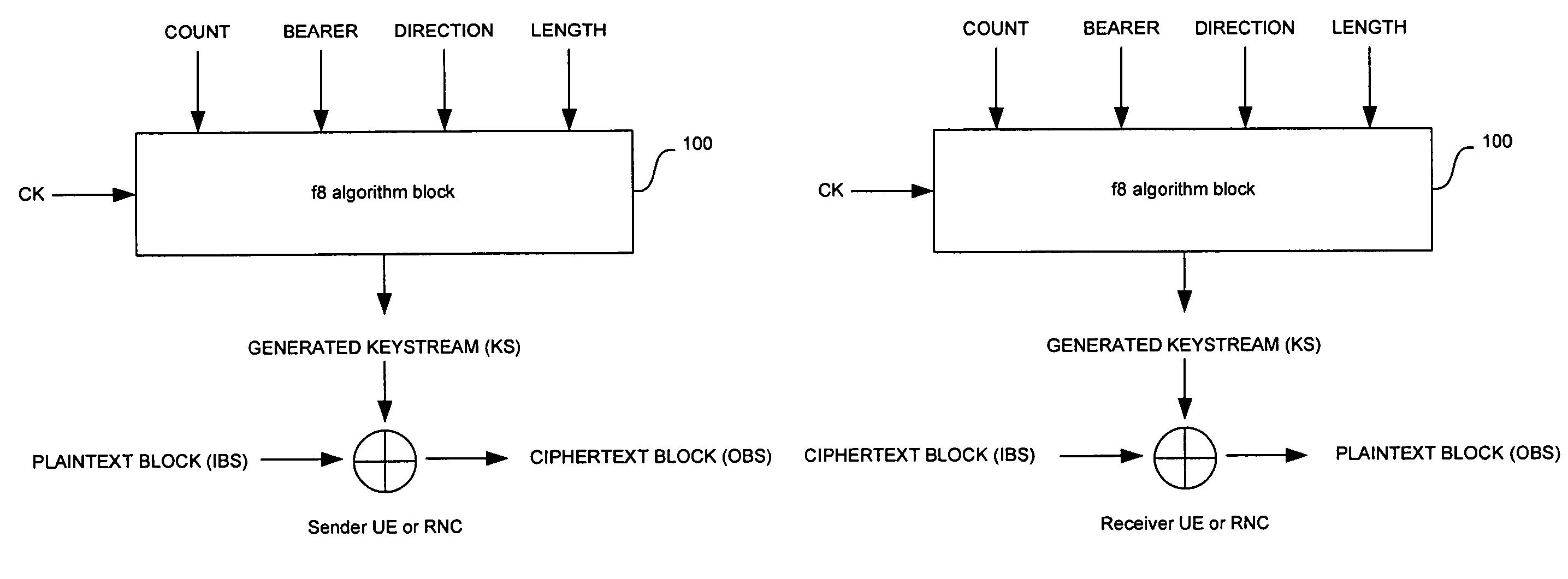
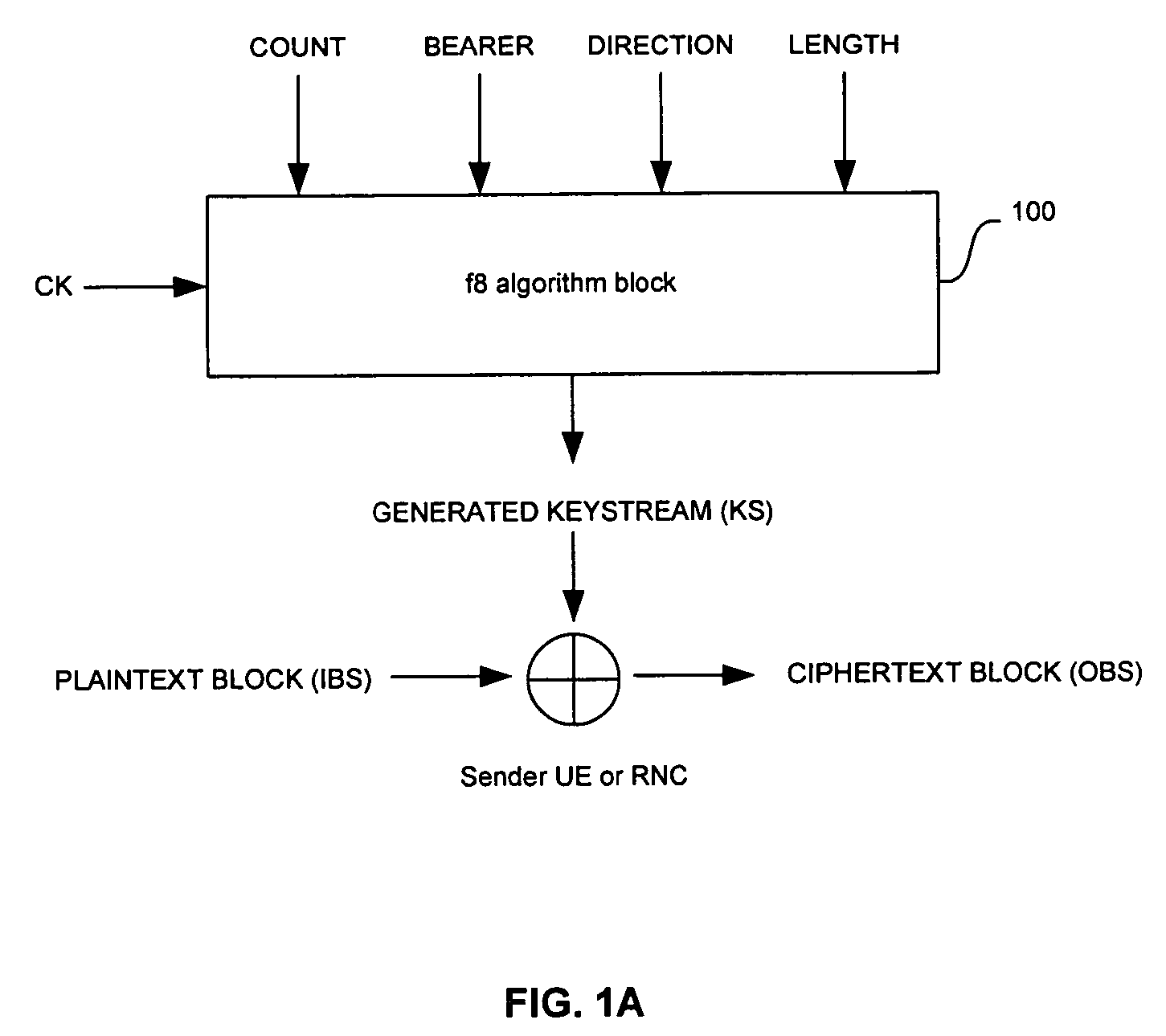
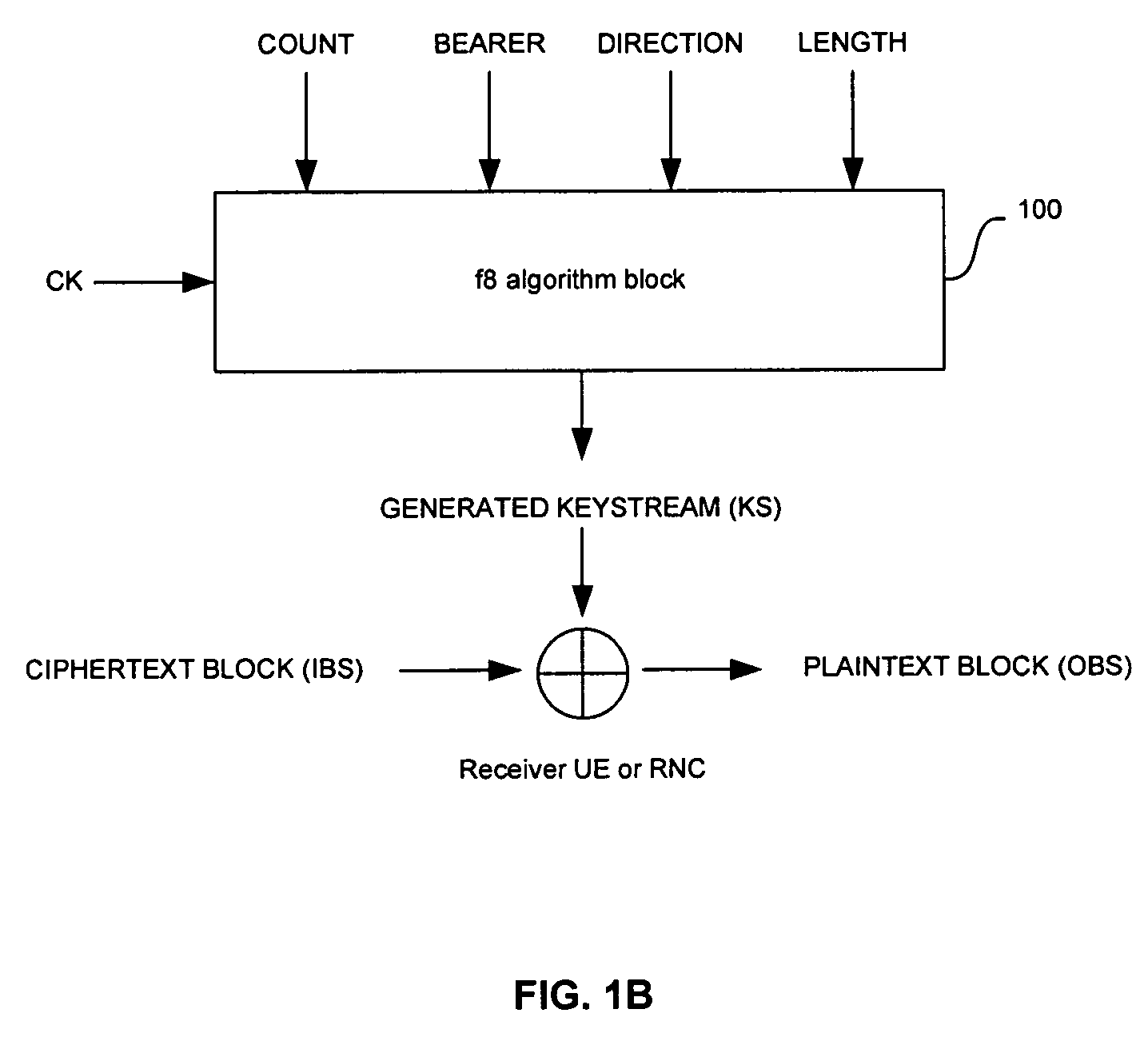
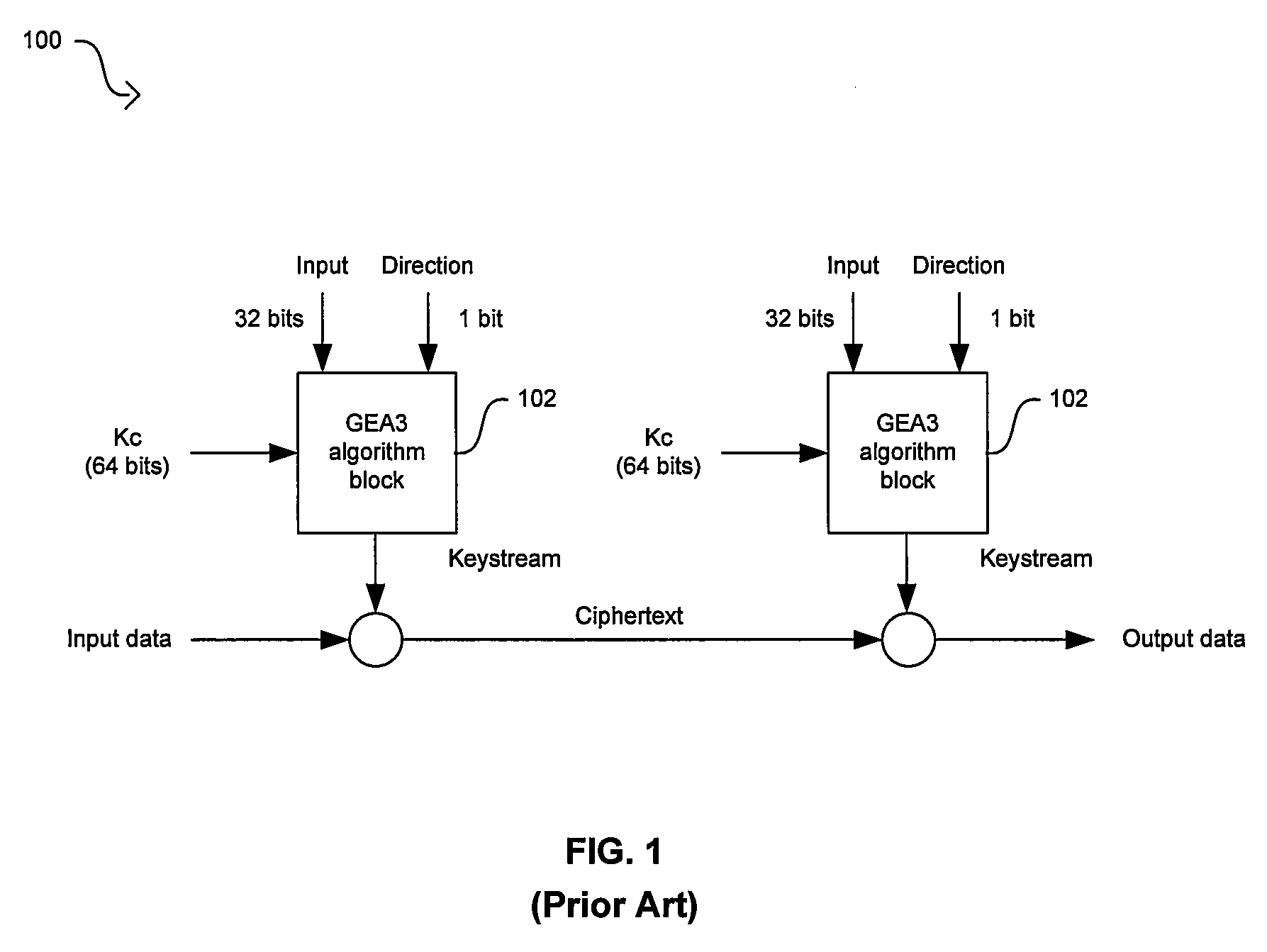
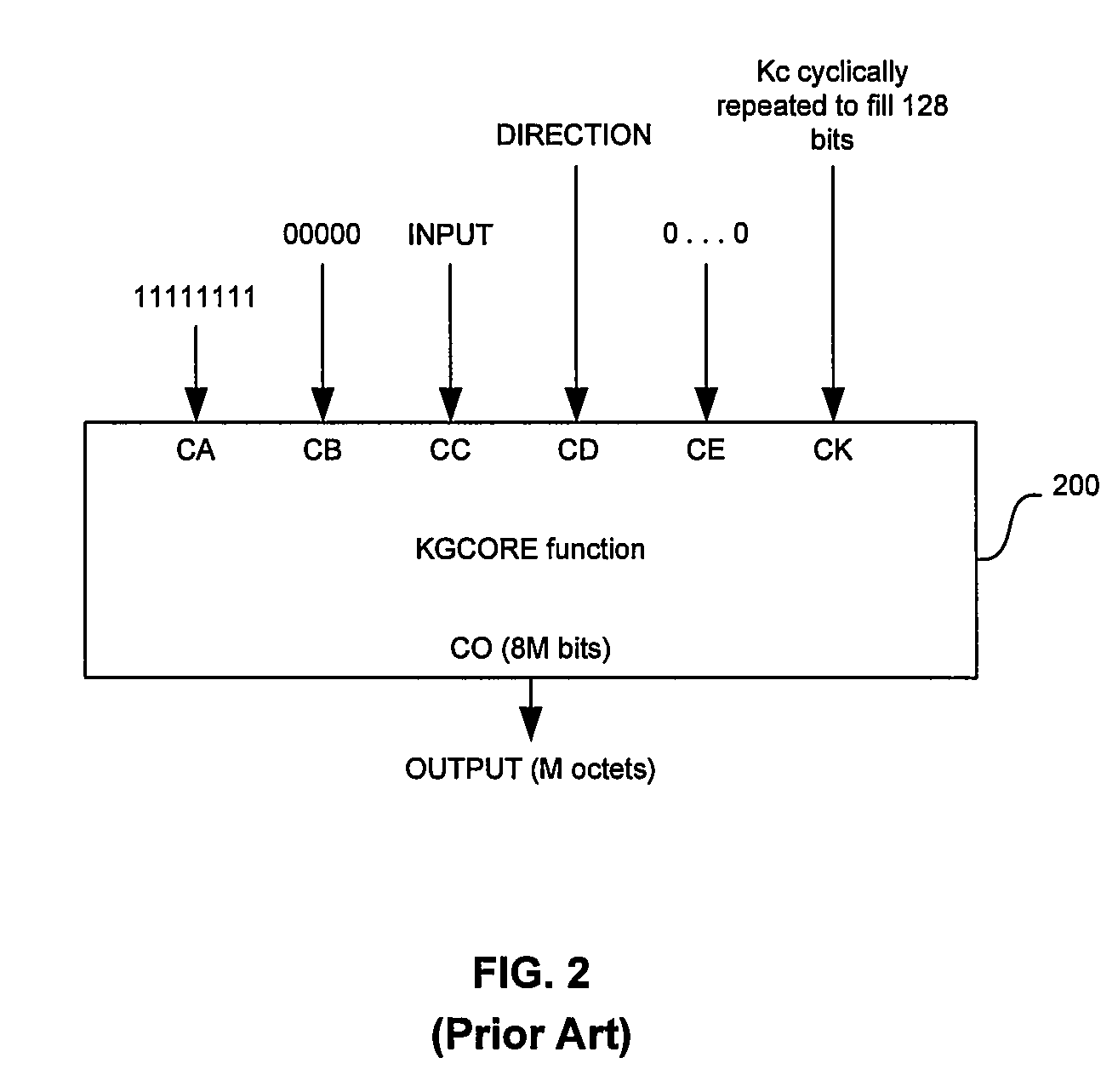
Method and system for hardware accelerator for implementing f8 confidentiality algorithm in WCDMA compliant handsets
InactiveUS20060177050A1Secret communicationSecuring communicationComputer hardwareCommunications system
In a wireless communication system, a method and system for hardware accelerator for implementing the f8 confidentiality algorithm in WCDMA compliant handsets are provided. Input variables may be initialized in a keystream generator and an intermediate value may be generated with a confidentiality key parameter and a key modifier. The number of processing blocks of output bits may be based on the length of the input bitstream. The processing blocks of output bits may be generated utilizing a KASUMI operation and may be based on an immediately previous processing block of output bits, the intermediate value, and an indication of the current processing block of output bits. The processing blocks of output bits may be generated after an indication that an immediately previous processing block of output bits is available. The keystream generator may indicate when a first and any additional processing blocks of output bits have been determined.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
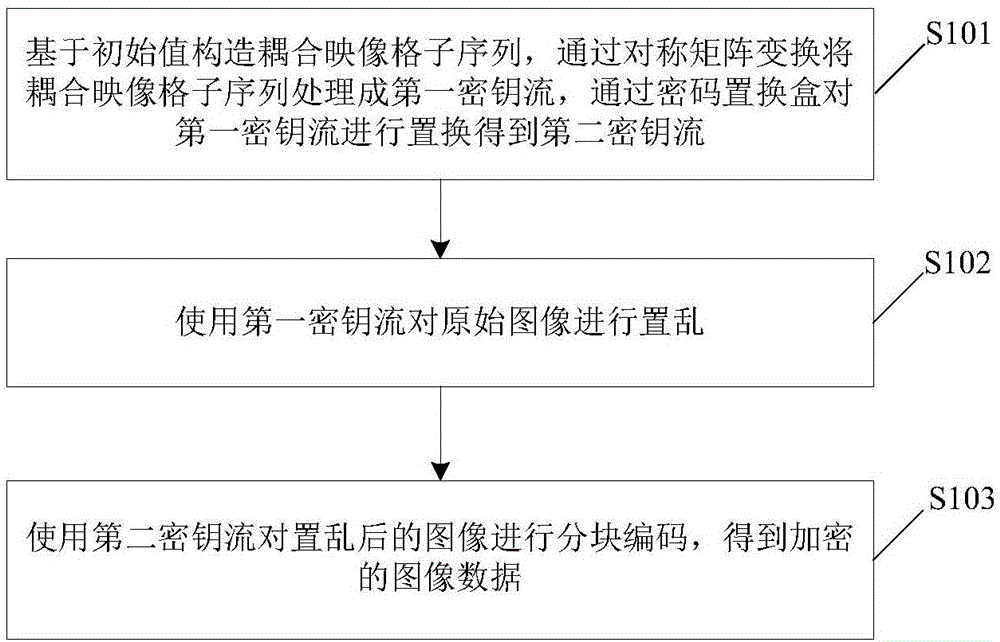
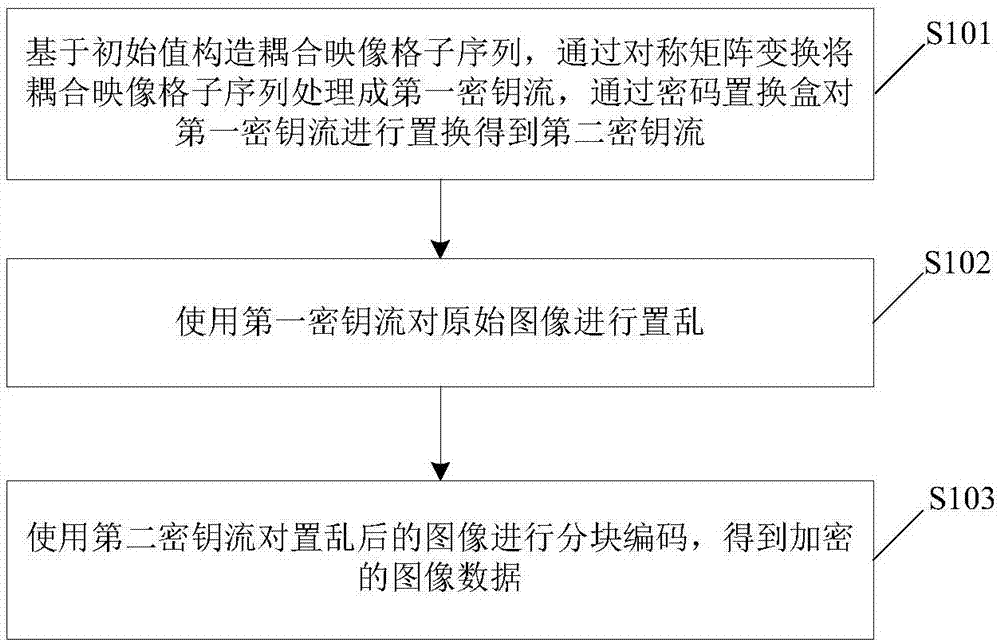
Image encryption method and device
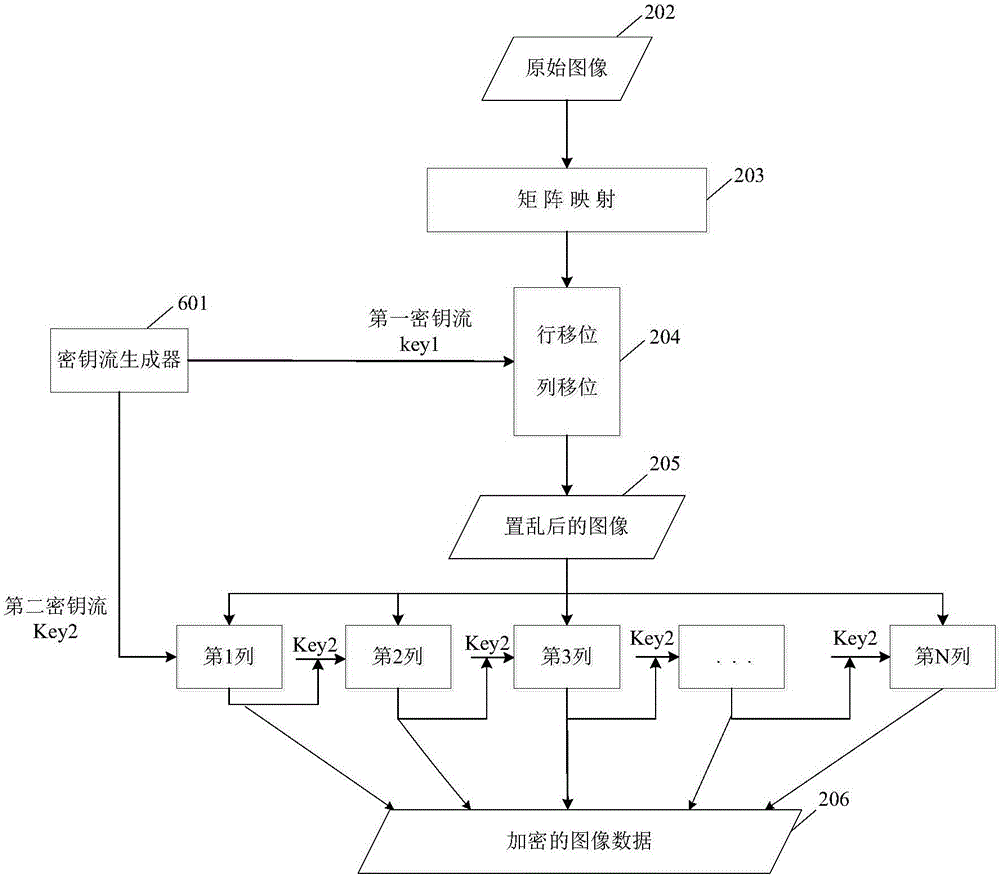
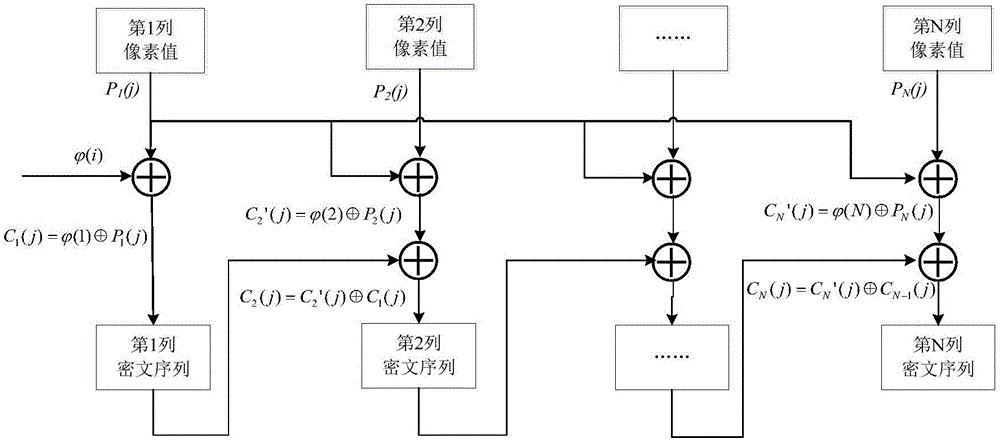
ActiveCN106407824AReduce computational complexityImprove encryption securityEncryption apparatus with shift registers/memoriesDigital data protectionComputer hardwareComputation complexity
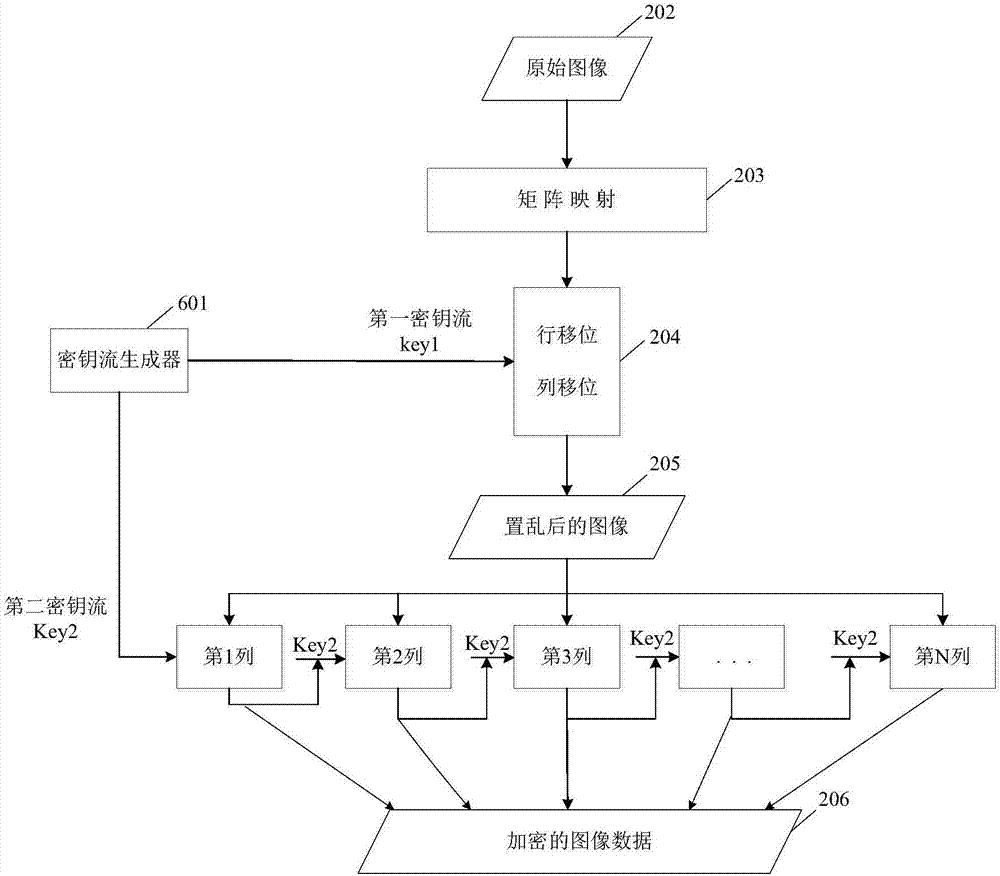
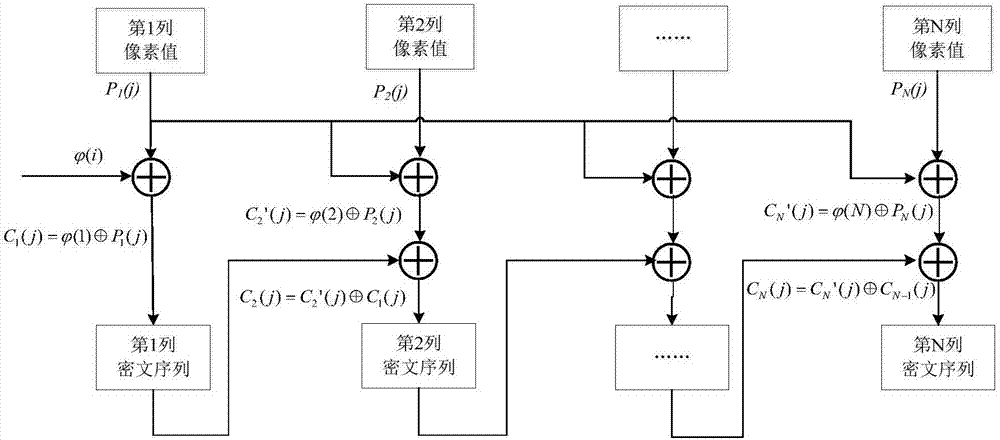
The invention relates to an image encryption method, an image encryption device, a key stream generation method and a key stream generator. The image encryption method comprises following steps of constructing a coupling image grid sequence based on the initial value, processing the coupling image grid sequence to be a first key stream by means of symmetric matrix transformation, replacing the first key stream through a password displacement box to obtain a second key stream, scrambling the original image by means of the first key stream, carrying out block encoding to the scrambled image by means of the second key stream, and obtaining the encrypted image data. According to the invention, the scrambling operation encryption method and the block encoding encryption method are combined, the encryption safety is improved, and the computation complexity of the encryption operation is well reduced; different key streams are used in the scrambling operation and the block encoding; compared with a method that a single key stream is used, the image encryption method is advantaged in that the encryption safety is higher.
Owner:CHONGQING UNIV OF EDUCATION
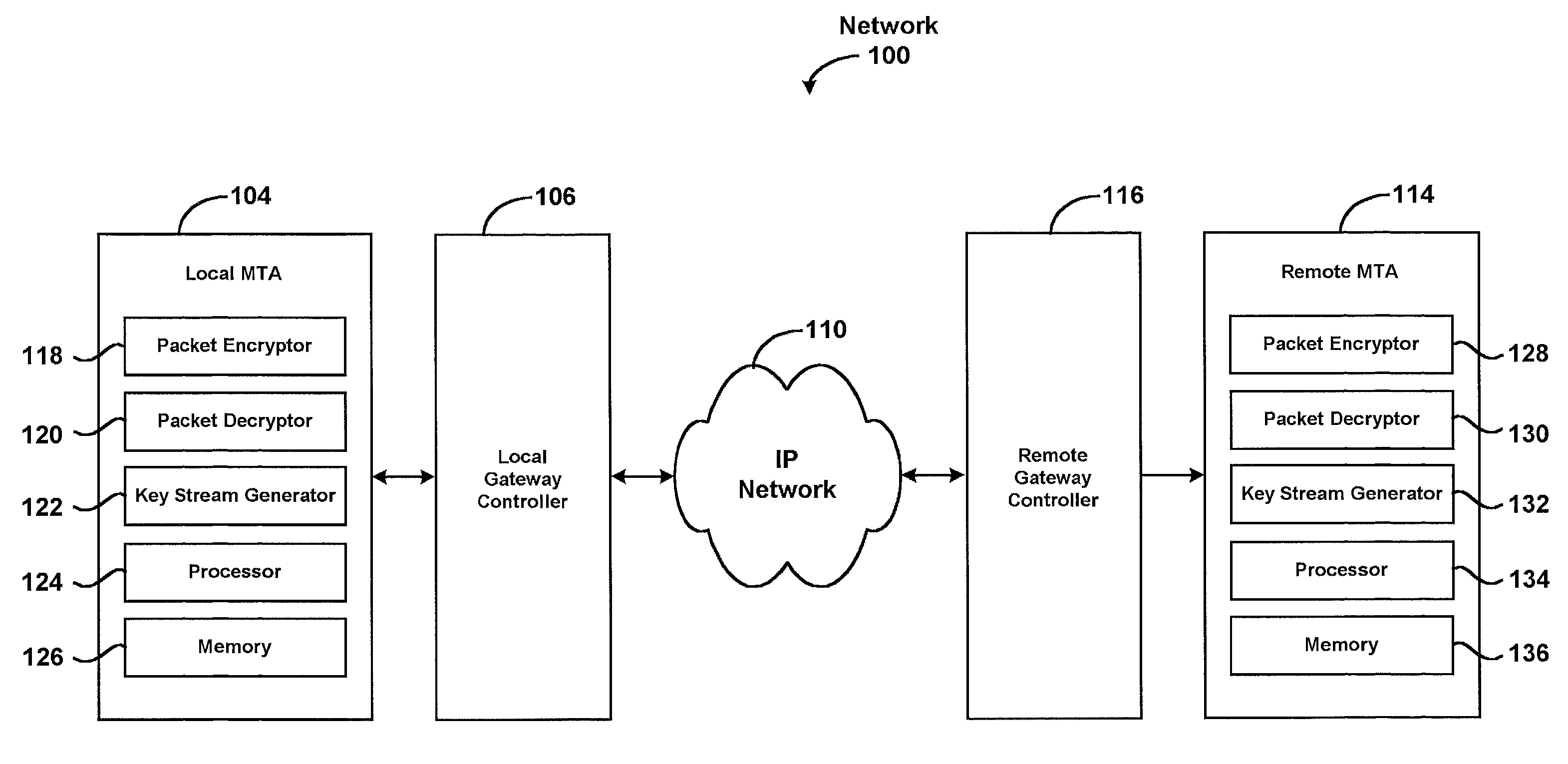
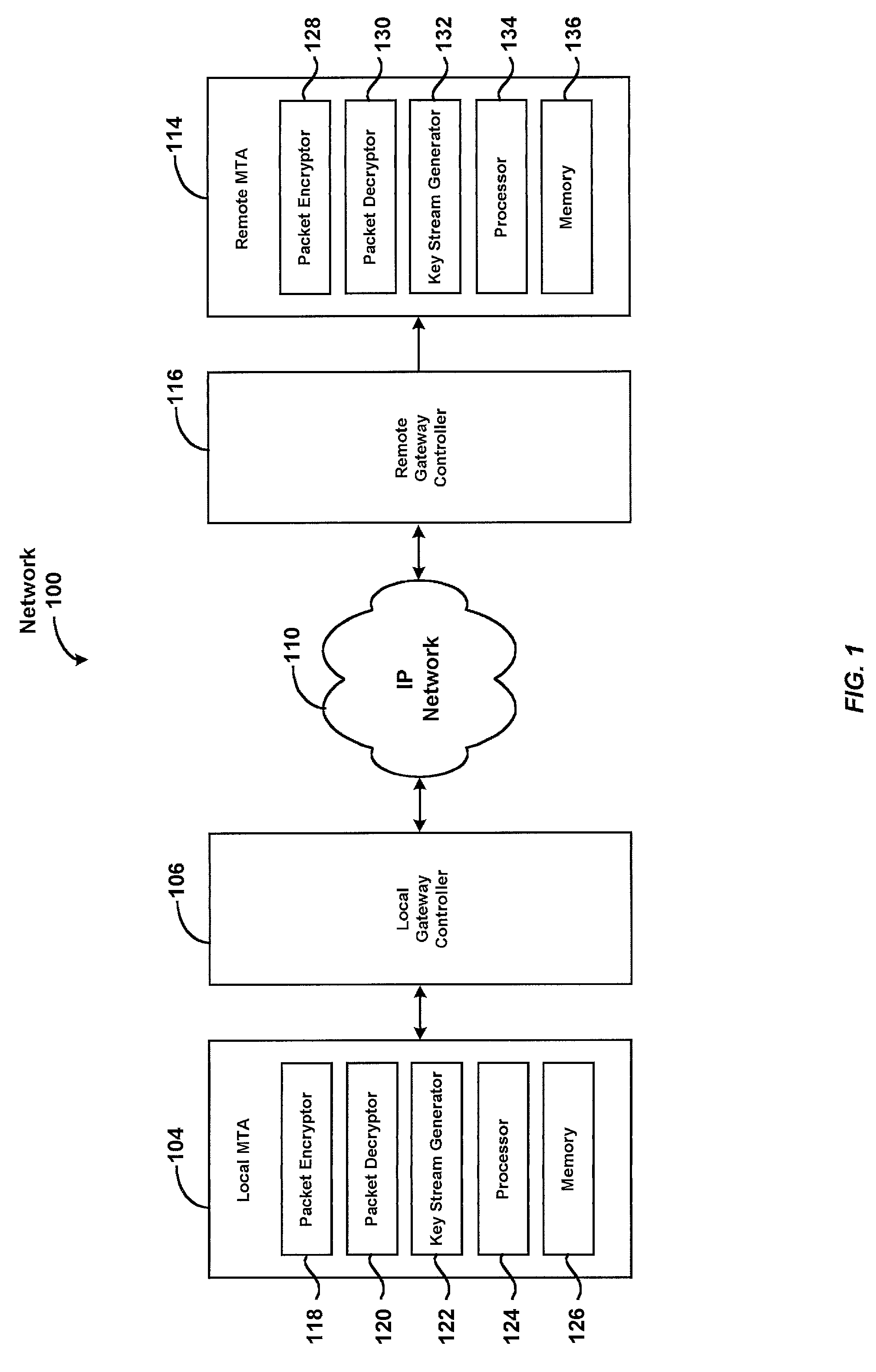
System for securely communicating information packets
InactiveUS7684565B2Secure transmissionEasy to decryptSynchronising transmission/receiving encryption devicesData stream serial/continuous modificationComputer networkTime Protocol
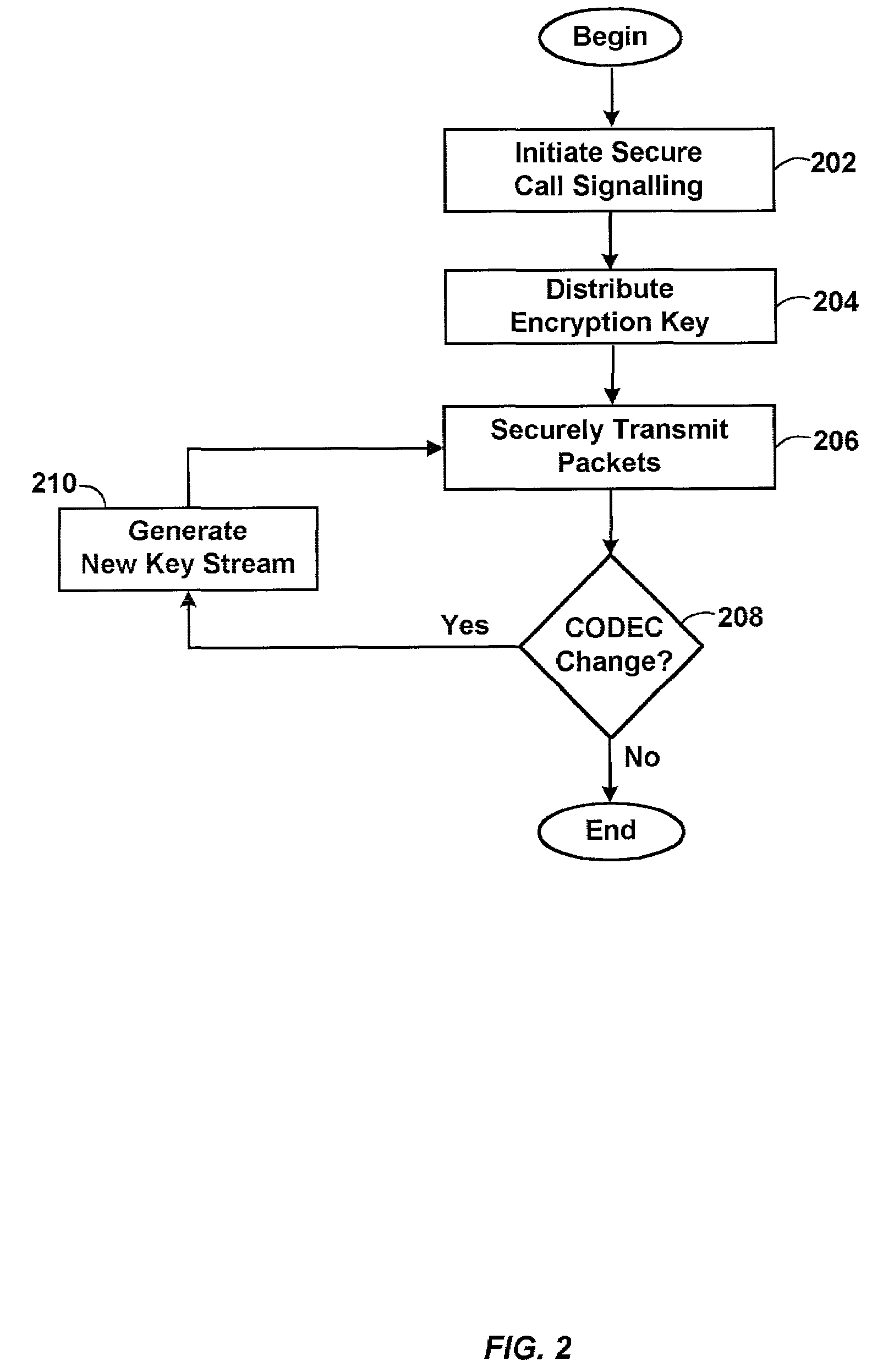
A system for securely transmitting Real Time Protocol voice packets to a remote multimedia terminal adapter over an Internet protocol network. The system features an MTA (a local multimedia terminal adapter) having a key stream generator for generating a first key stream used for encrypting the voice packets. The remote multimedia terminal adapter receives and decrypts the voice packets. Also, the system includes a remote key stream generator for generating the first key stream in order to decrypt the encrypted voice packets and a packet decryptor decrypting the encrypted voice packets using the first key stream, wherein both key stream generators are capable of generating a second key stream to prevent reuse of any portion of the first key stream during the communication session.
Owner:GOOGLE TECH HLDG LLC
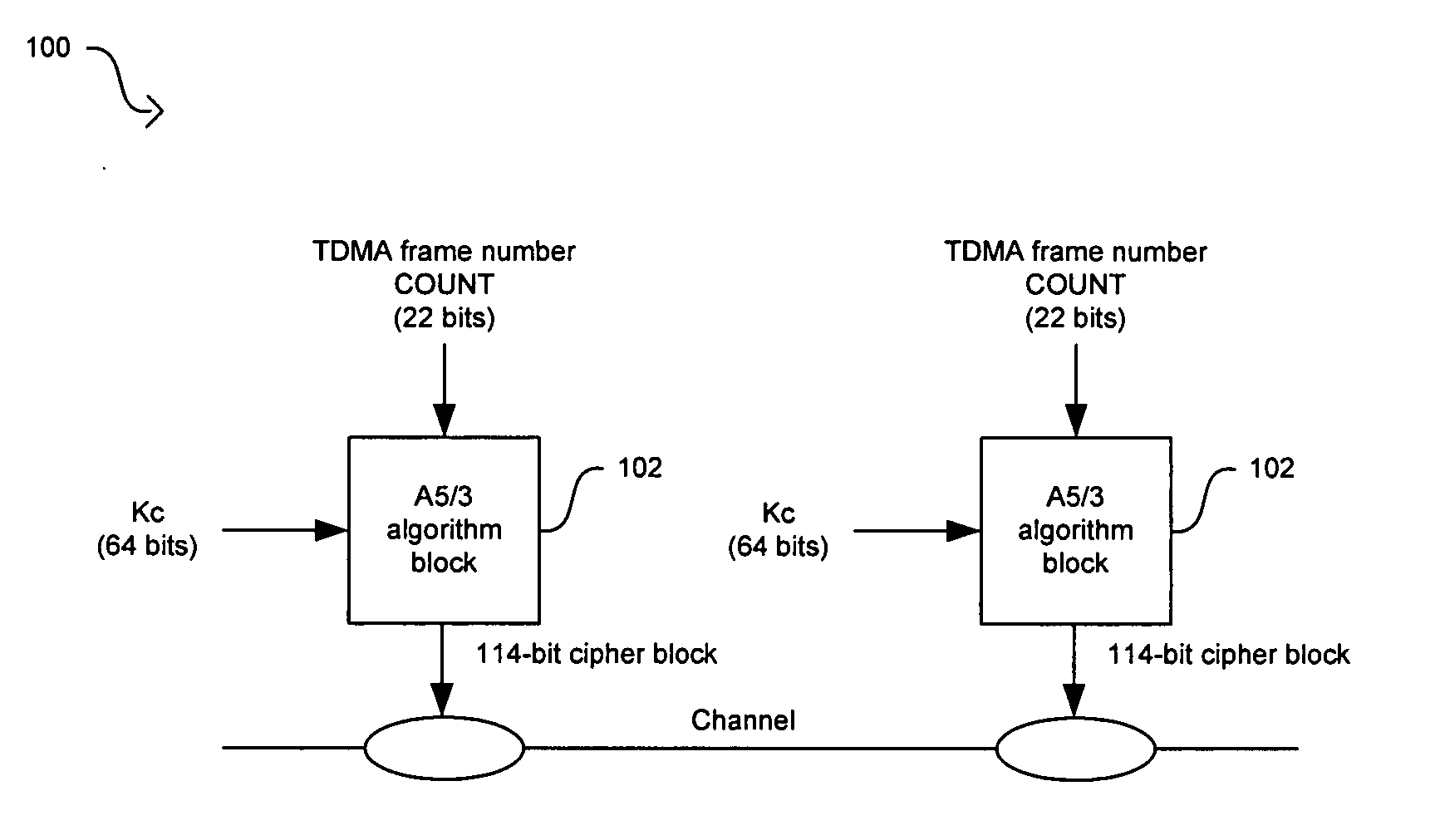
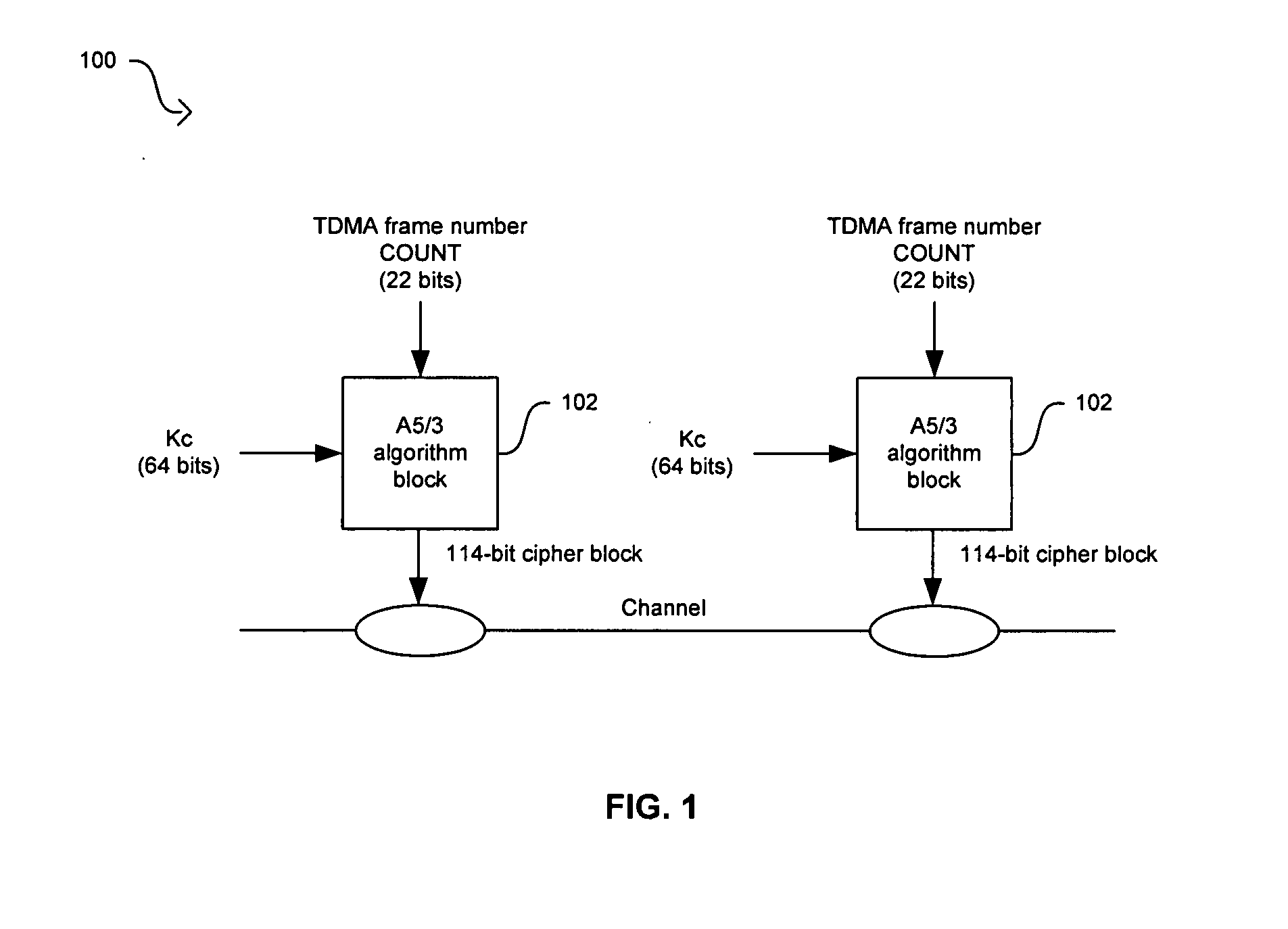
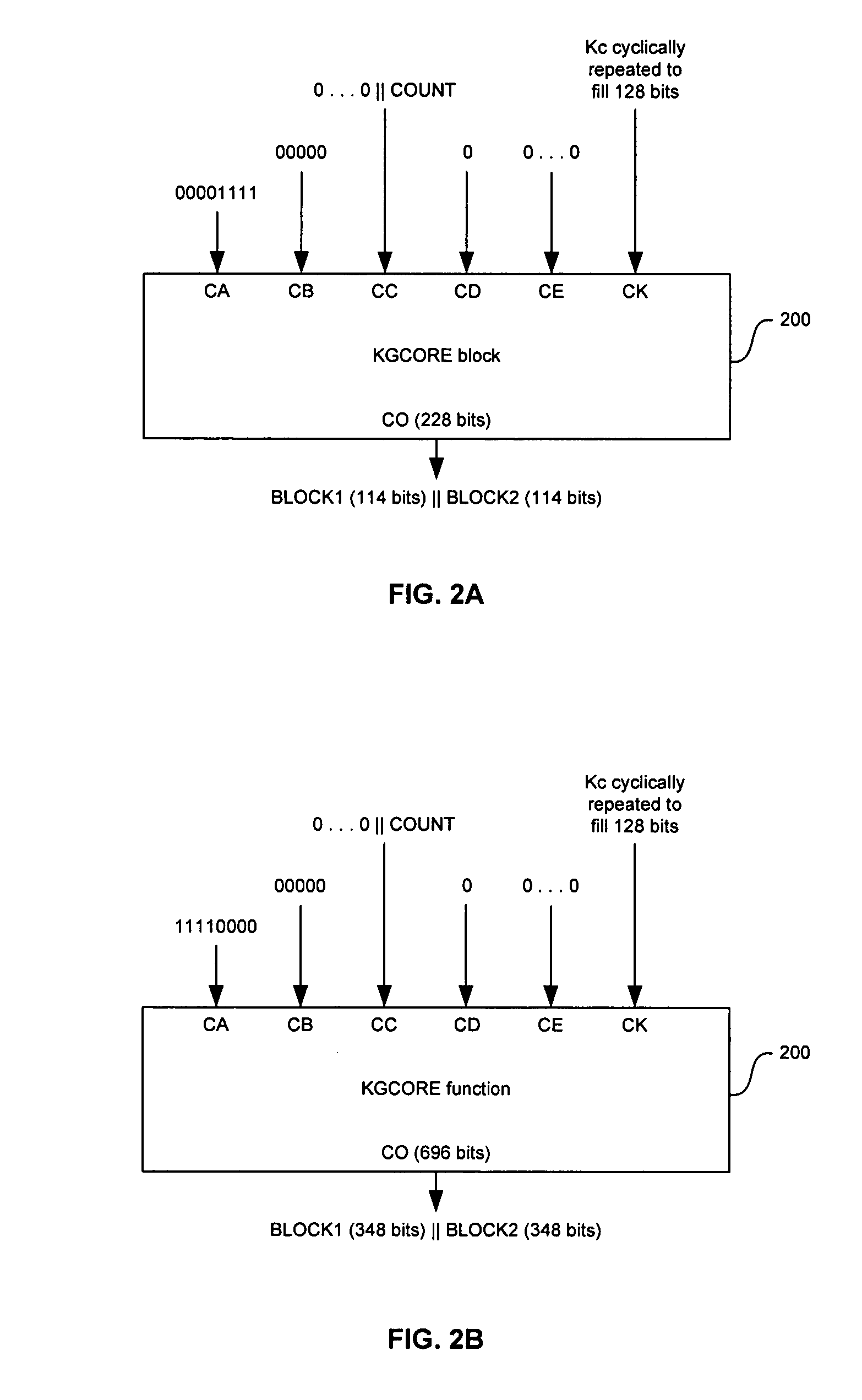
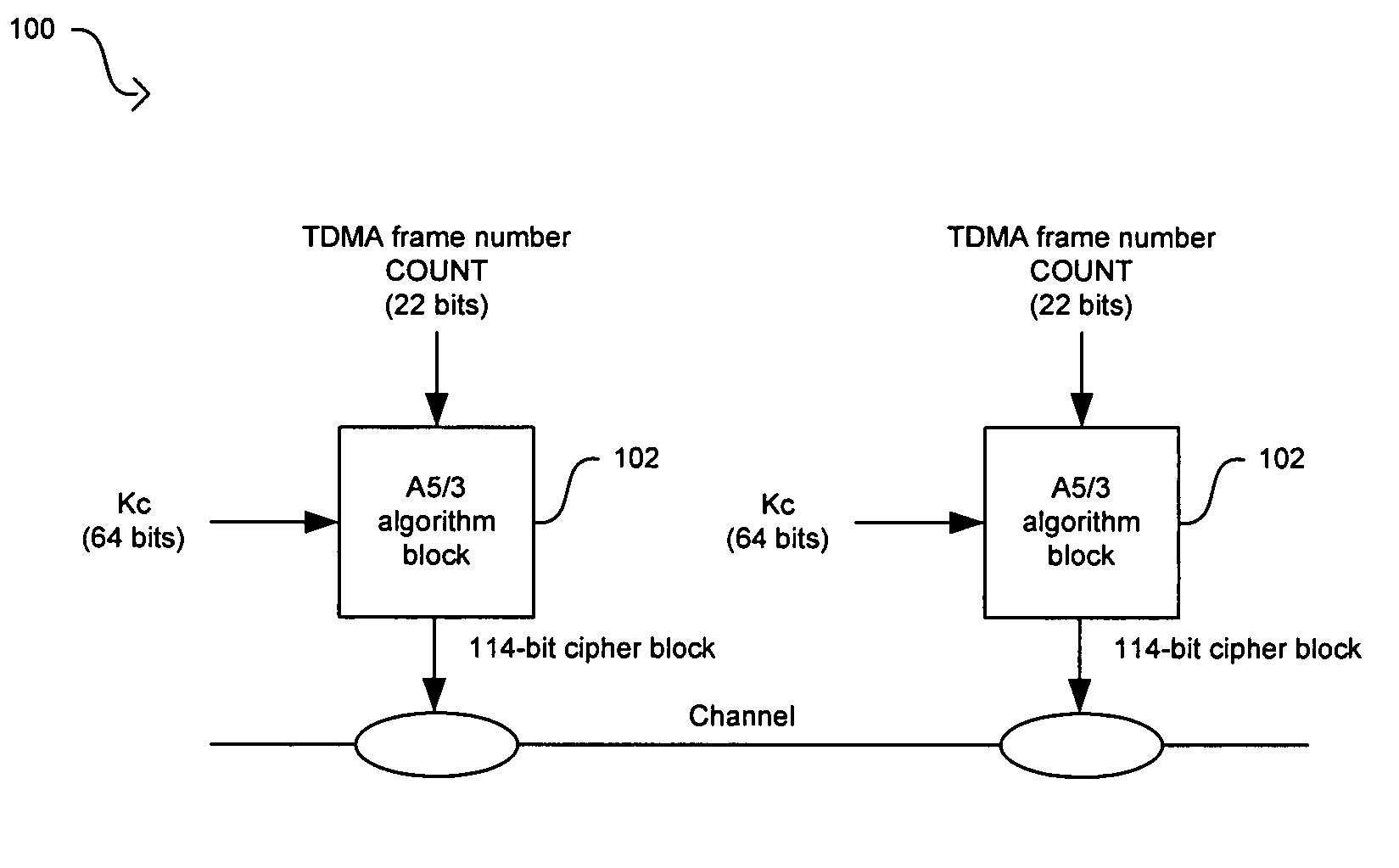
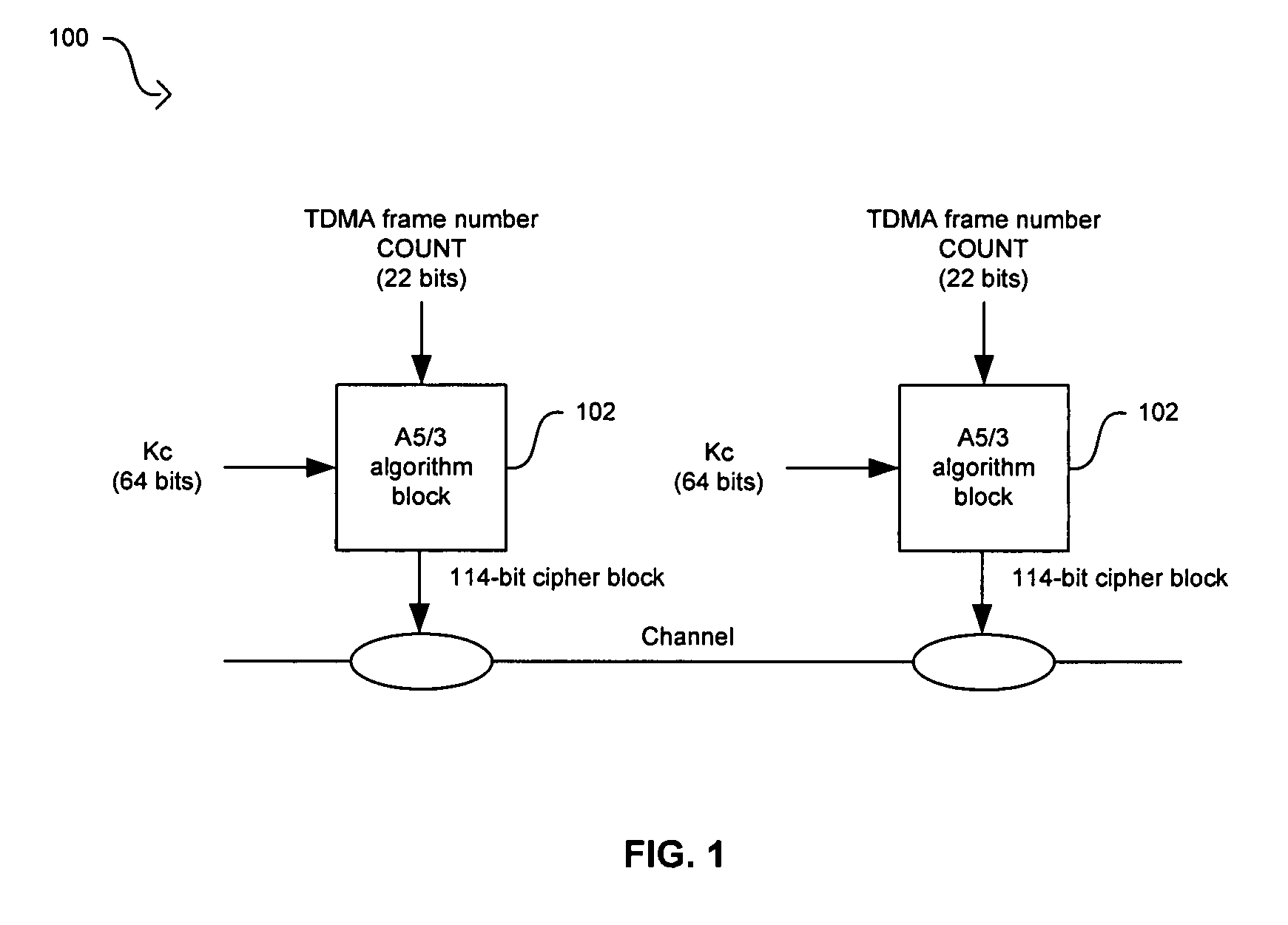
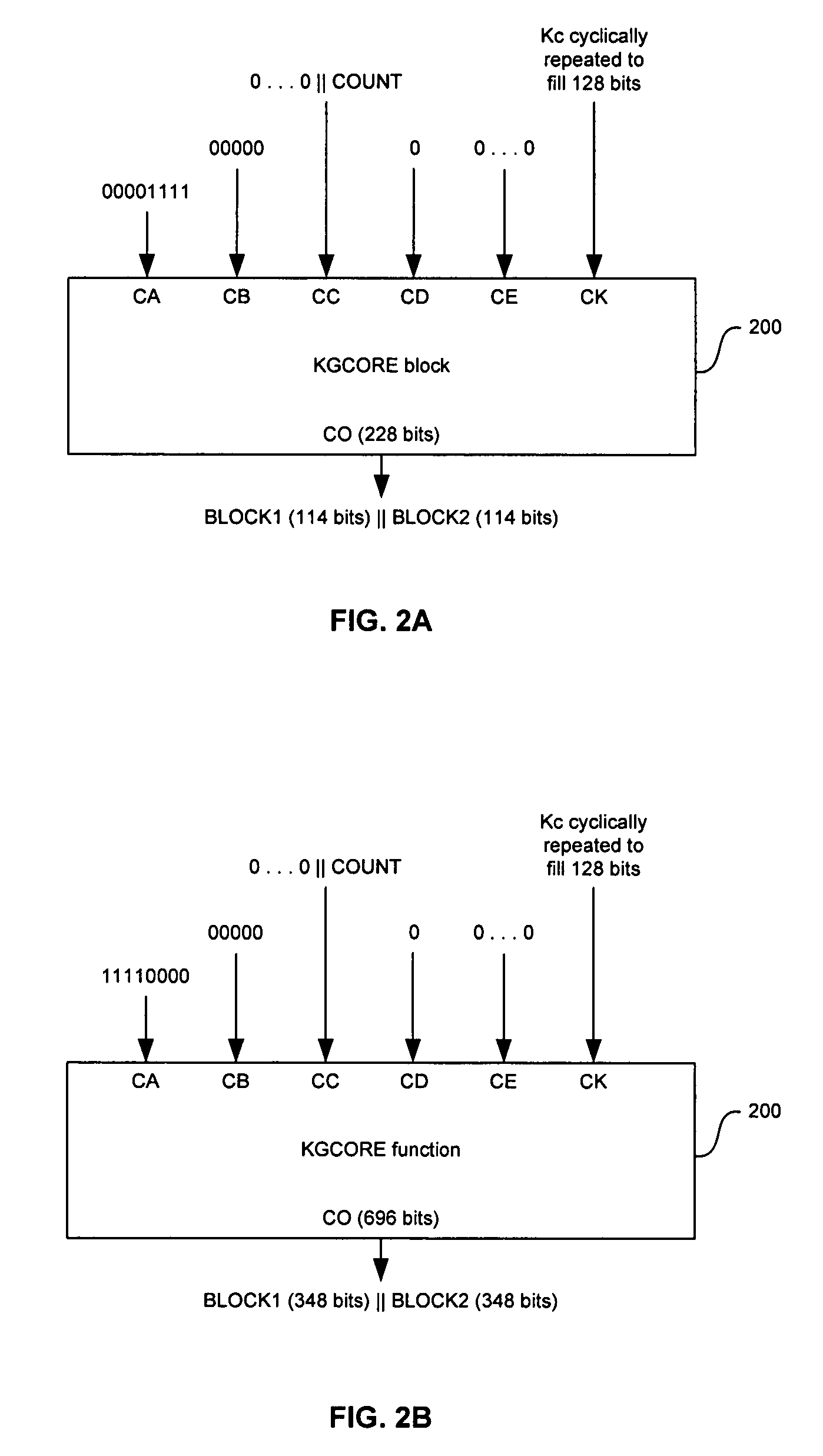
Method and system for implementing the A5/3 encryption algorithm for GSM and EDGE compliant handsets
InactiveUS20060039553A1Data stream serial/continuous modificationSecret communicationComputer hardwareCommunications system
In a wireless communication system, a method and system for implementing the A5 / 3 encryption algorithm for GSM and EDGE compliant handsets are provided. Input variables may be initialized in a keystream generator and an intermediate value may be generated with a cipher key parameter and a key modifier. A number of processing blocks of output bits may be determined based on a number of bits in an output keystream. The processing blocks of output bits may be generated utilizing a KASUMI operation and may be based on an immediately previous processing block of output bits, the intermediate value, and an indication of the processing block of output bits being processed. The processing blocks of output bits may be generated after an indication that an immediately previous processing block of output bits is available and may be grouped into two final blocks of output bits in the output keystream.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Data-processing apparatus and method for processing data
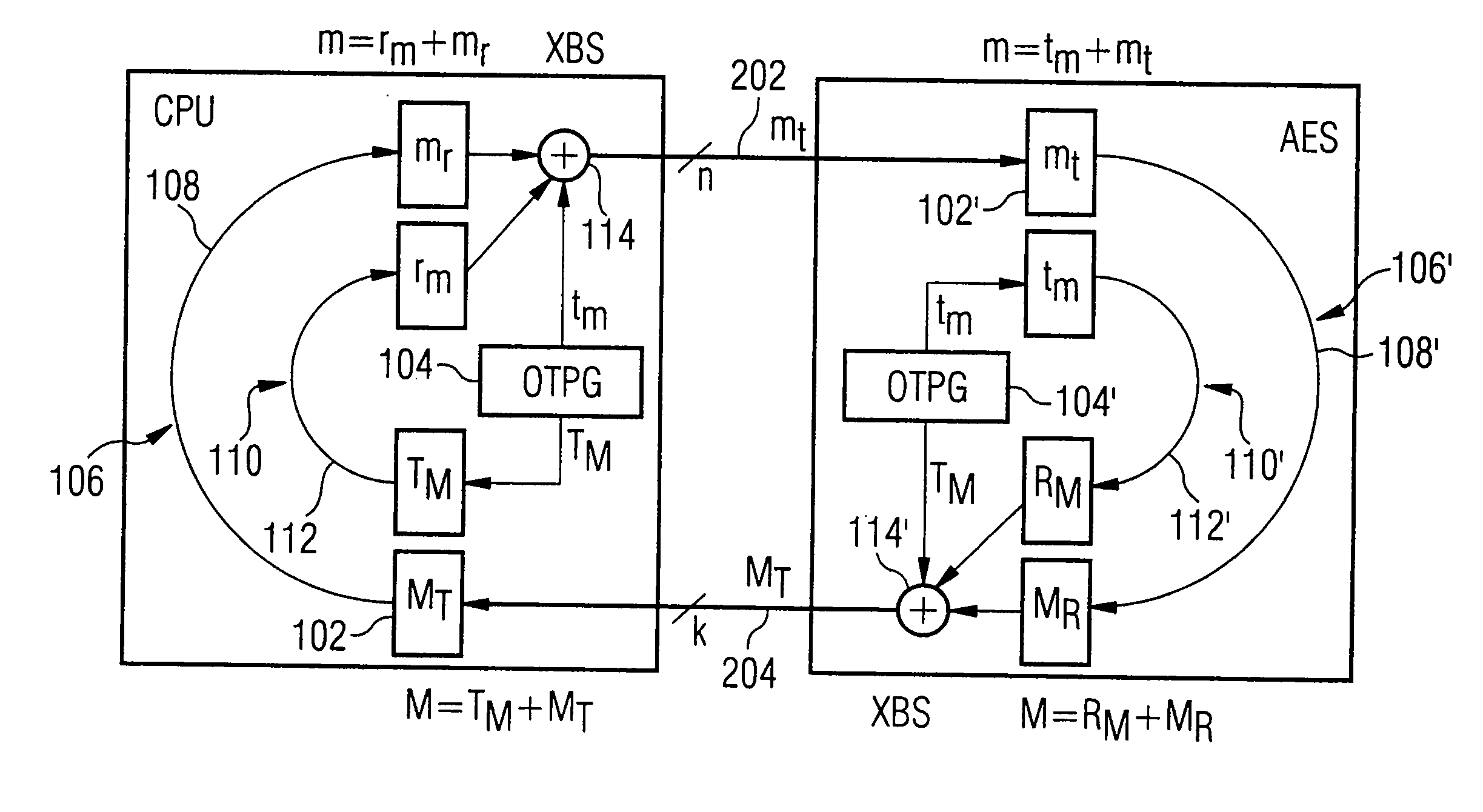
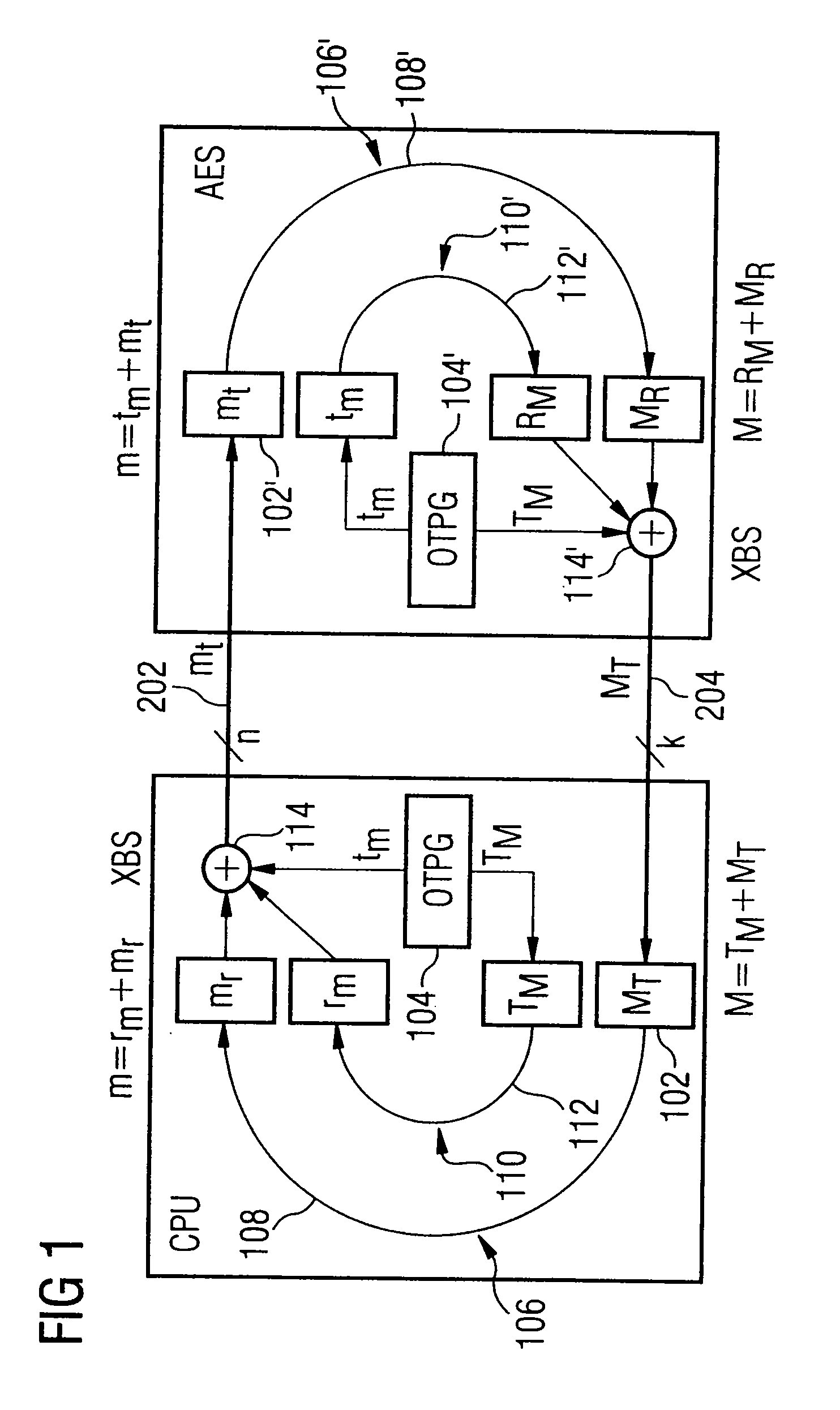
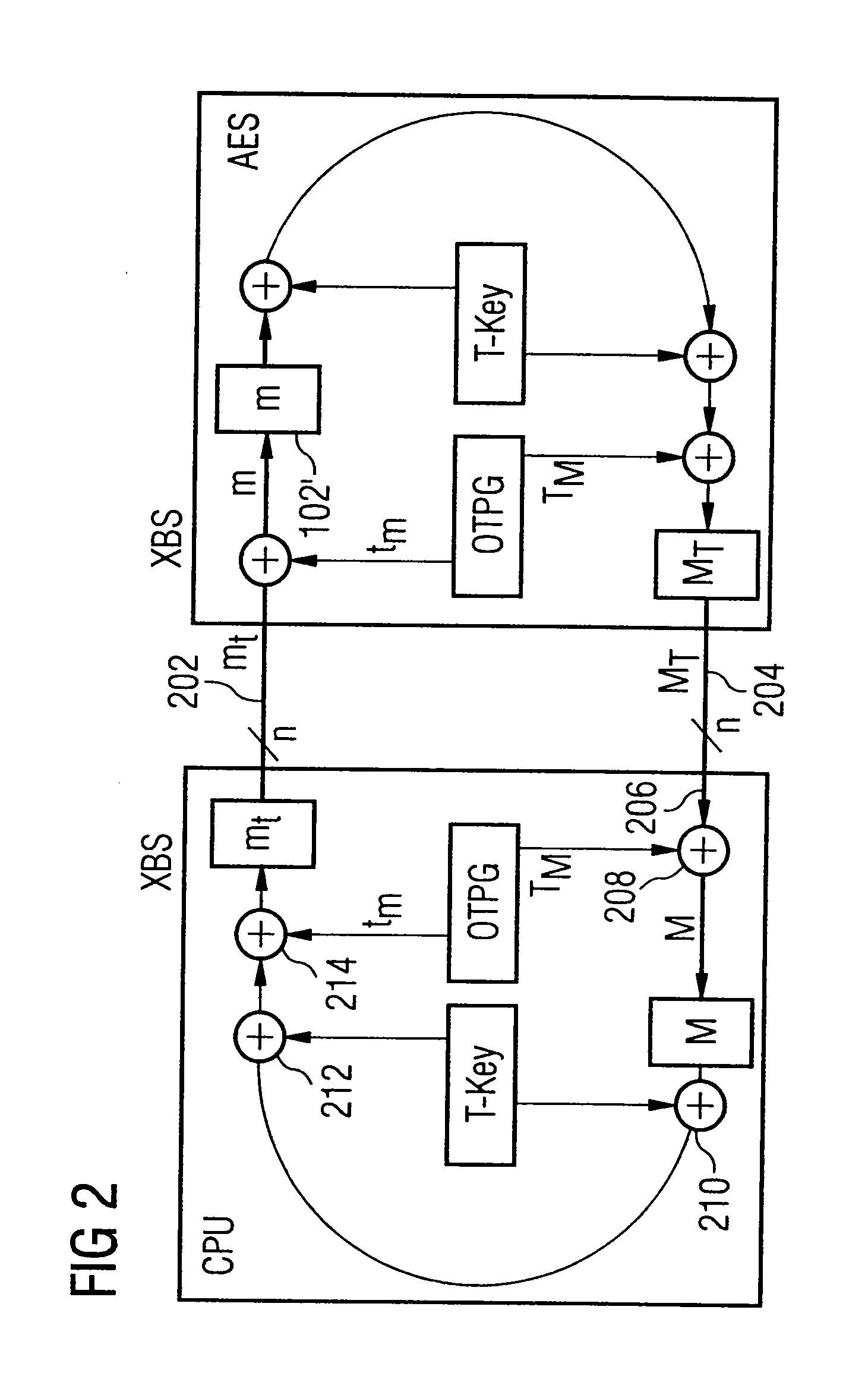
ActiveUS20070189543A1Key distribution for secure communicationSynchronising transmission/receiving encryption devicesComputer hardwareData provider
A data-processing apparatus has a data provider for providing an input datum encrypted by an encryption key. In addition, the data-processing apparatus has a key stream generator for generating a key stream in a predetermined deterministic manner such that the key stream has a decryption key corresponding to the encryption key. Furthermore, the data-processing apparatus has a data processor for processing the encrypted input datum in a masked manner using the decryption key as a temporary key to obtain an output datum encrypted by an output key such that the encrypted output datum corresponds to a result, encrypted by the output key, of a predetermined operation on the encrypted input datum having been decrypted by the decryption key.
Owner:INFINEON TECH AG
Method and apparatus for decrypting a communication
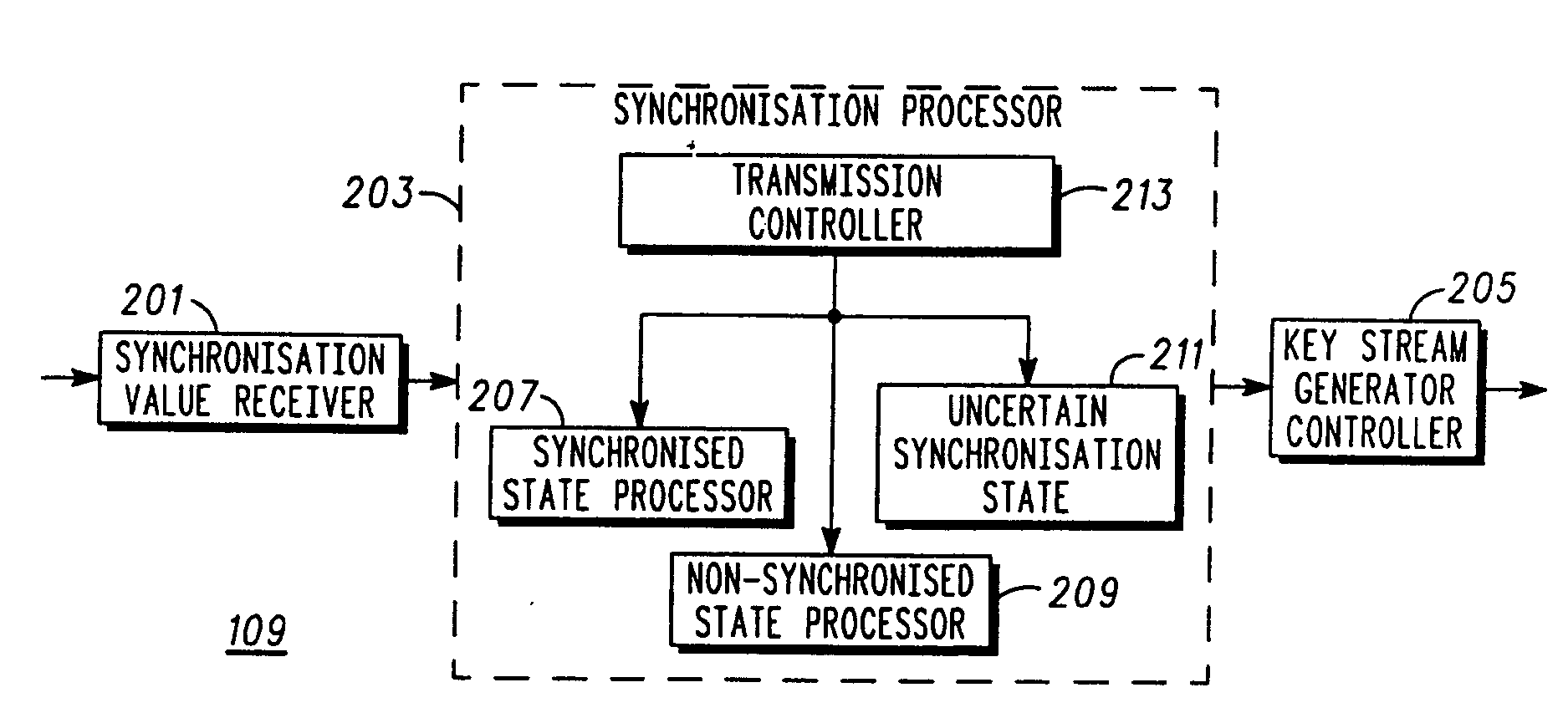
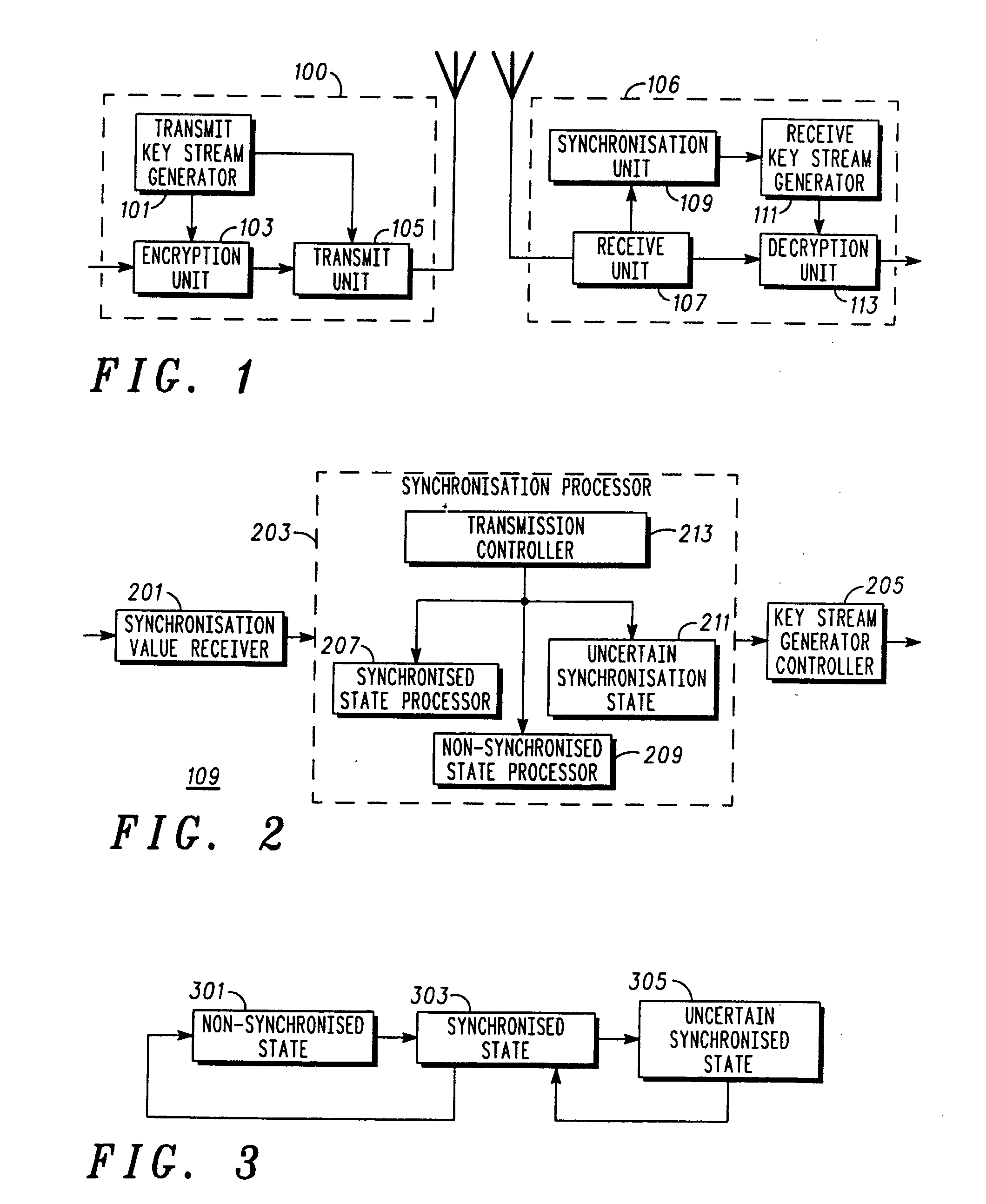
ActiveUS20080031453A1Easy to detectAddressing slow performanceSynchronising transmission/receiving encryption devicesSecret communicationComputer hardwareKeystream generator
A decryption apparatus (109) comprises a key stream generator (111) generating a local decryption key stream. It furthermore comprises a synchronisation value receiver (201) receiving key stream synchronisation values. A synchronisation processor (203) implements a state machine which may operate in a synchronised state (303) wherein the communication is decrypted using the local key stream, a non-synchronised state (301) wherein the local key stream is not synchronised, or in an uncertain synchronisation state (305) wherein the communication is decrypted using the local key stream and wherein the local key stream is synchronised to each new received synchronisation value. The synchronisation processor (203) furthermore comprises a transition controller (213) operable to transition from the synchronised state to the non-synchronised state in response to a first criterion and to the uncertain synchronisation state in response to a second criterion.
Owner:MOTOROLA SOLUTIONS INC
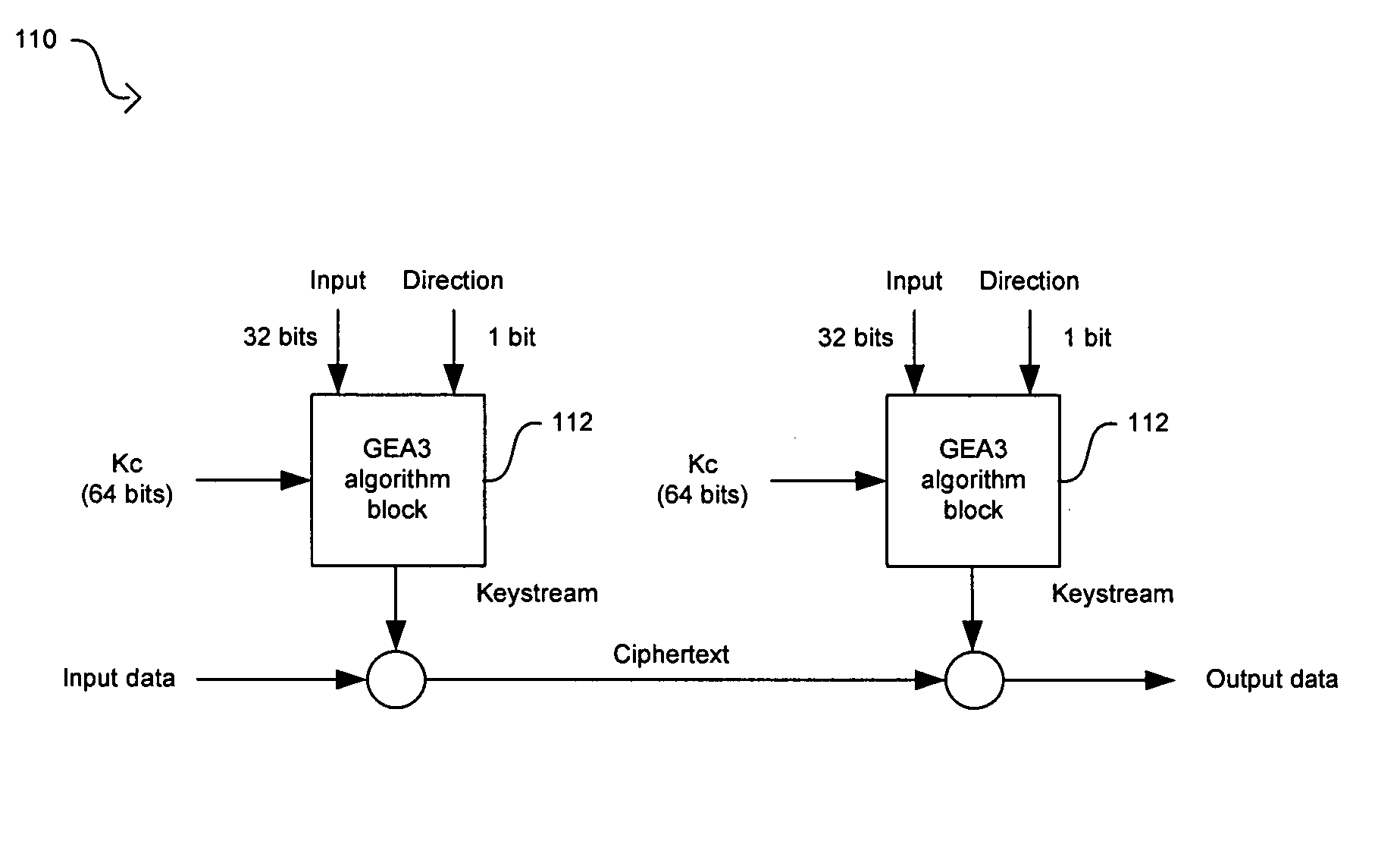
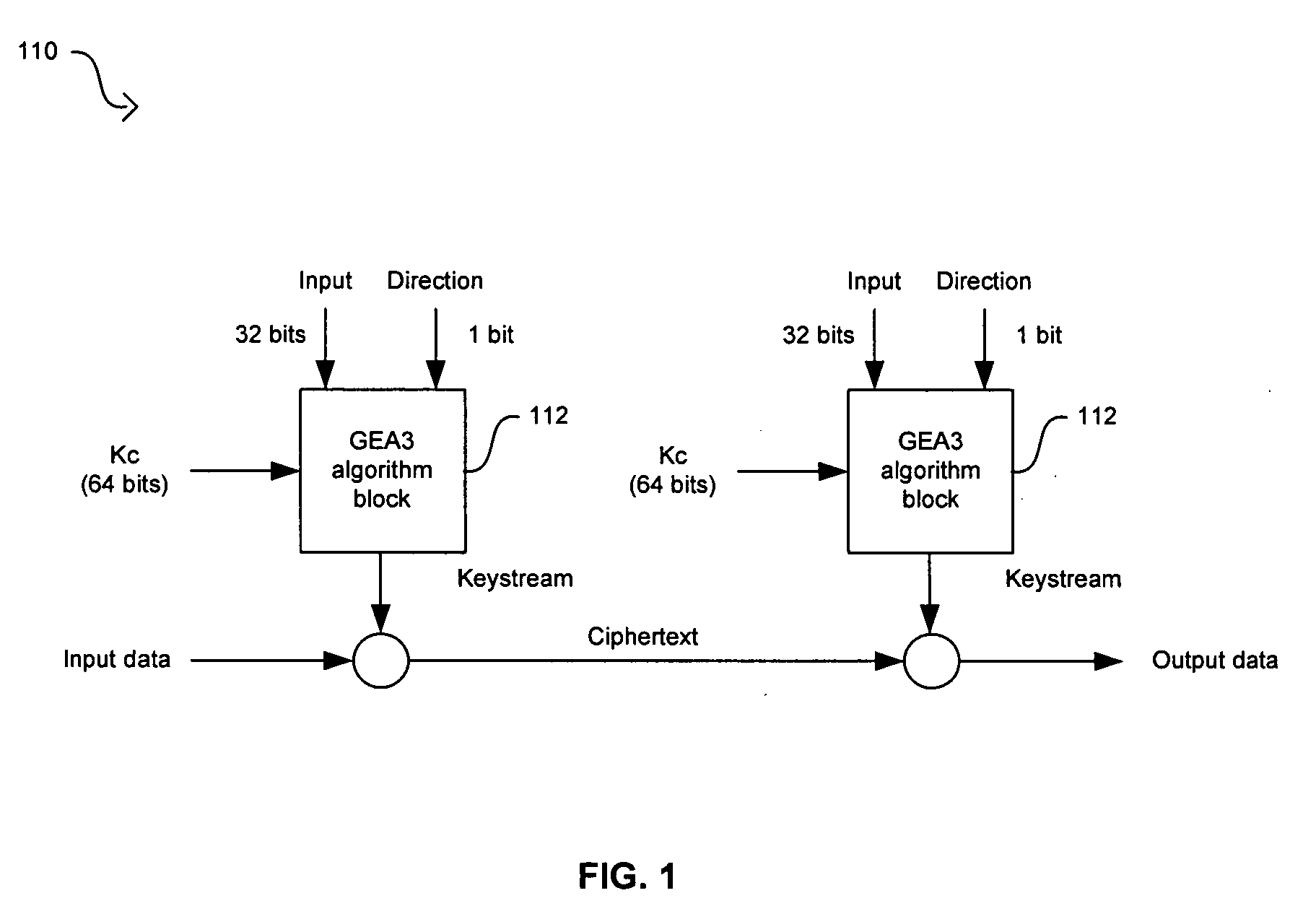
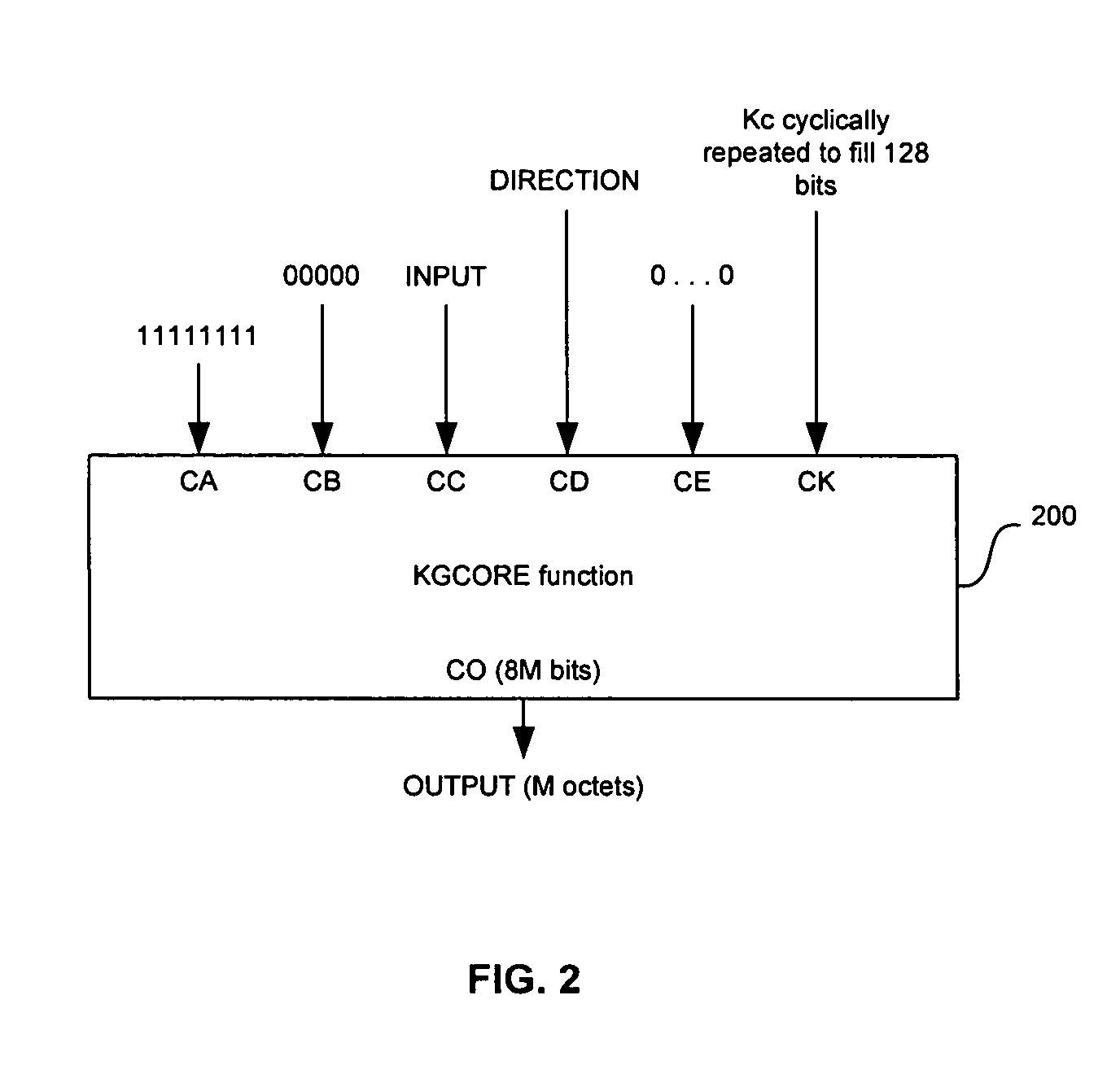
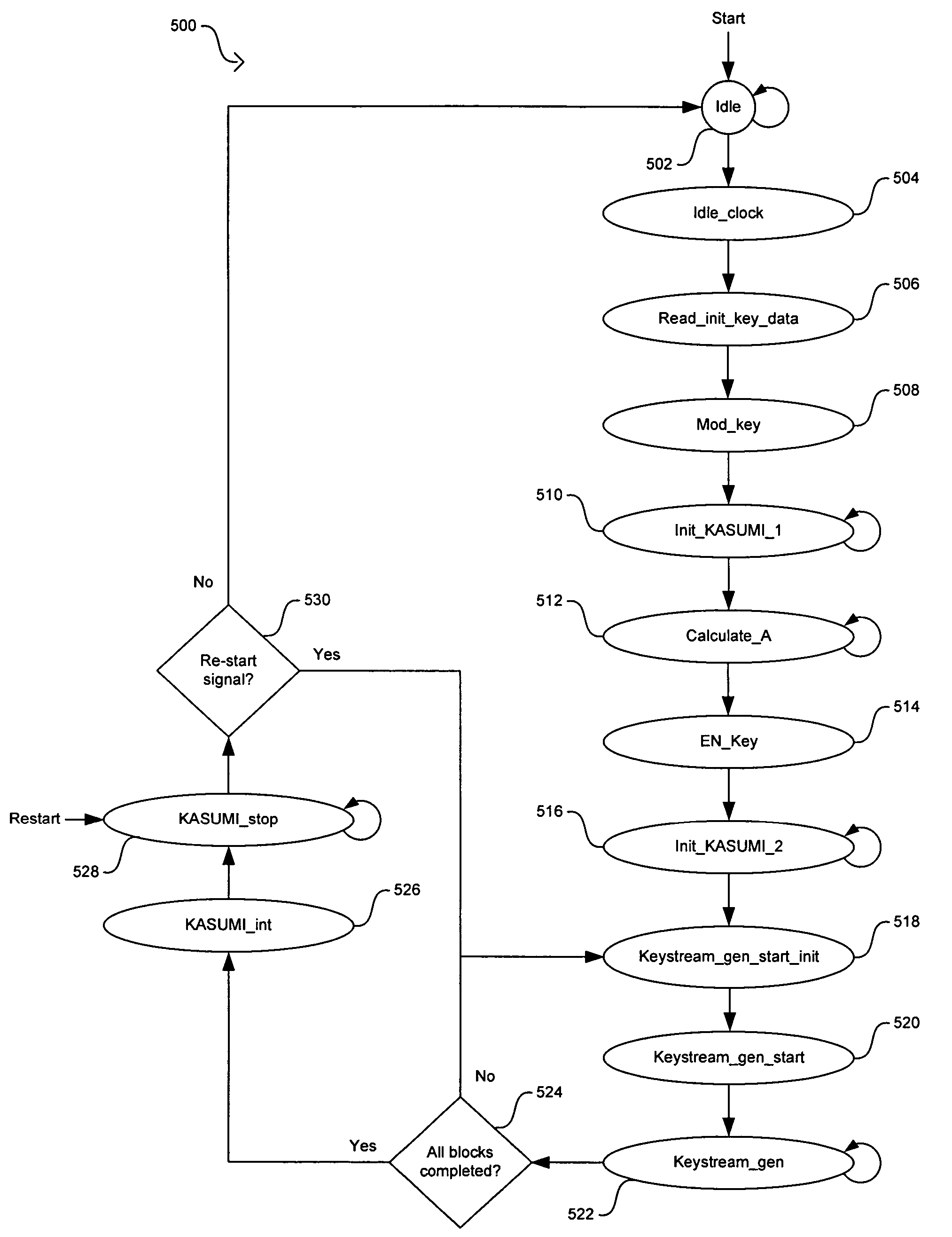
Method and system for implementing the GEA3 encryption algorithm for GPRS compliant handsets
InactiveUS20060039556A1Data stream serial/continuous modificationSecret communicationComputer hardwareCommunications system
In a wireless communication system, a method and system for implementing the GEA3 encryption algorithm for GPRS compliant handsets are provided. An intermediate value may be generated based on initialized input variables, a cipher key and a key modifier. A first processing block of output bits may be generated by a keystream generator from the intermediate value, the cipher key, and an indication of the processing block of output bits being processed. Additional processing blocks of output bits may also be generated by the keystream generator based on an immediately previous processing block of output bits, the intermediate value, the cipher key, and an indication of the processing block of output bits being processed. A restart signal may indicate that subsequent processing blocks of output bits may be generated by the keystream generator by utilizing the same cipher key and the generated intermediate value.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Encryption and decryption method and device based on zipper type dynamic hash and NLFSR
ActiveCN109981249AImprove uniformityLong cycleEncryption apparatus with shift registers/memoriesPlaintextShift register
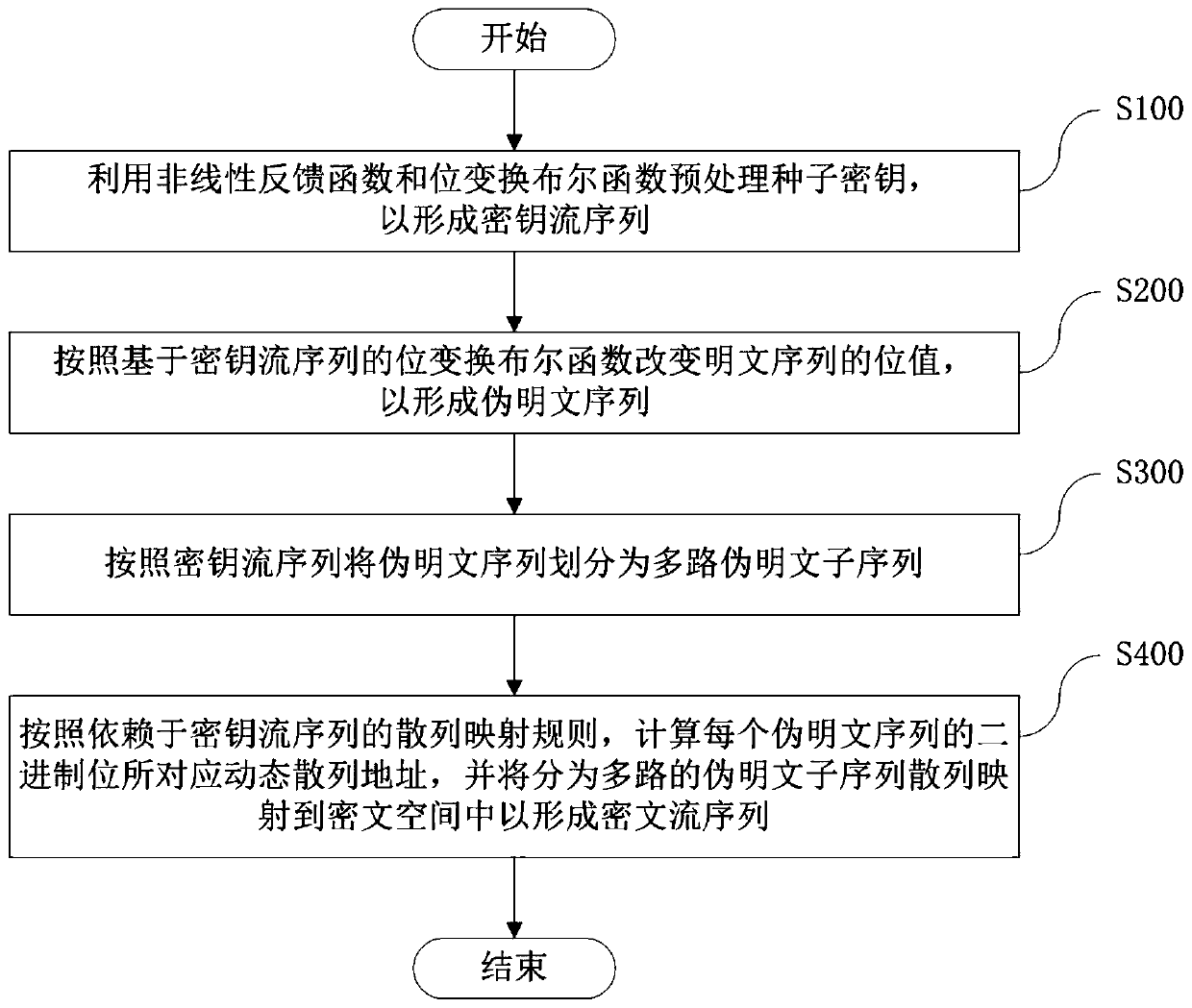
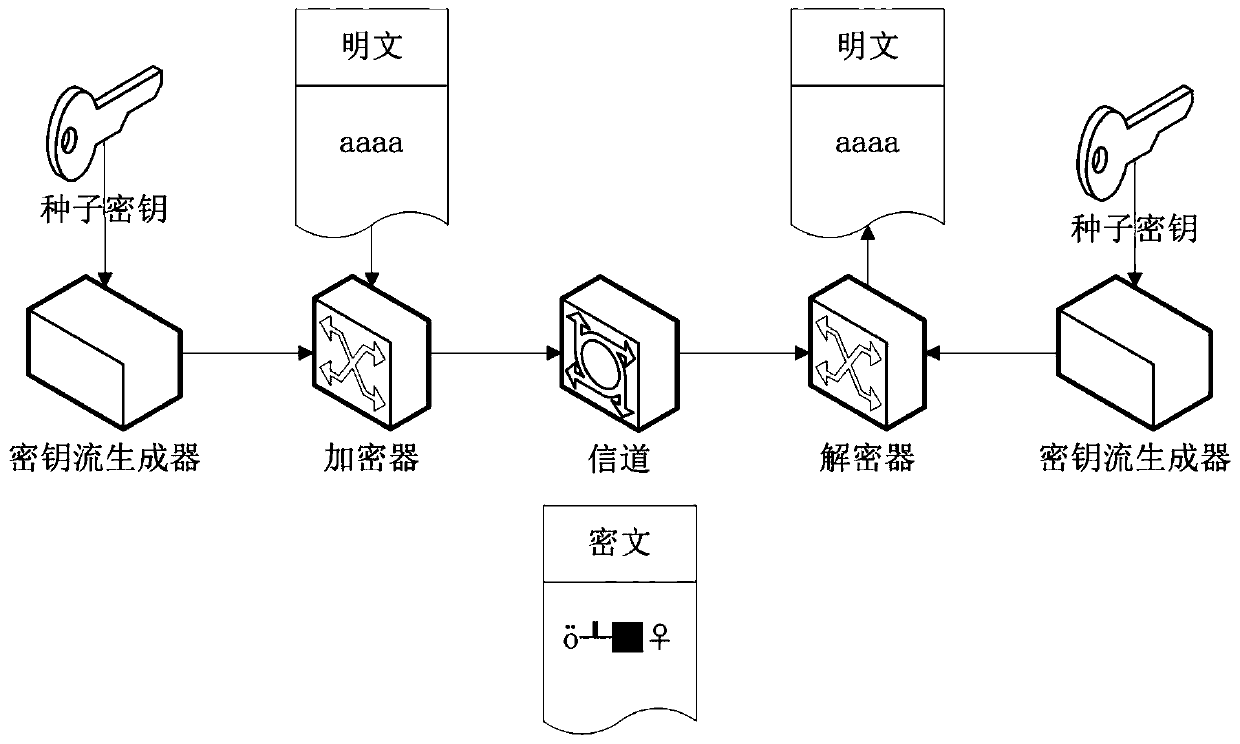
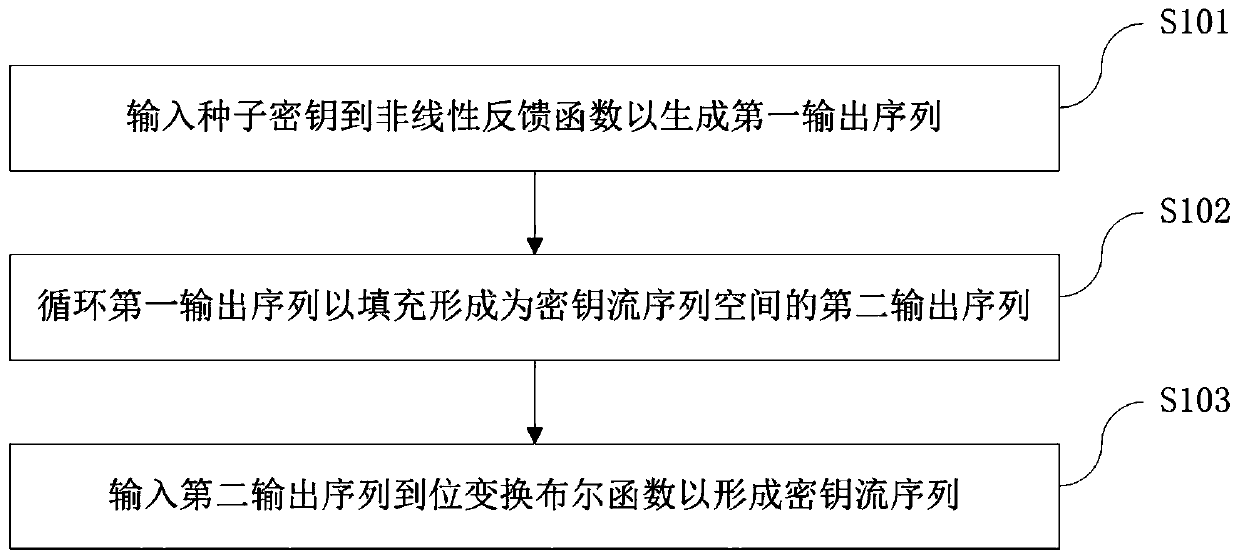
An encryption and decryption method based on zipper type dynamic hashes and NLFSRs comprises the following steps that a nonlinear feedback function and a bit transformation Boolean function are used for preprocessing a seed secret key to form a secret key stream sequence; changing the bit value of the plaintext sequence according to the bit transformation Boolean function based on the key stream sequence to form a pseudo plaintext sequence; dividing the pseudo-plaintext sequence into a plurality of paths of pseudo-plaintext subsequences according to the key stream sequence; and calculating a dynamic hash address corresponding to the binary bit of each pseudo plaintext sequence according to a hash mapping rule depending on the key stream sequence, and mapping the pseudo plaintext subsequence hashes which are divided into multiple paths into a ciphertext space to form the ciphertext stream sequence. The method has the beneficial effects that the key stream generator not only uses a nonlinear feedback shift register, but also introduces a bit transformation Boolean function, so that the key stream with longer period and better randomness is obtained; and through a plaintext bit transformation rule and a zipper type dynamic hash mapping rule, the decoding difficulty of the ciphertext stream sequence is improved.
Owner:ZHUHAI COLLEGE OF JILIN UNIV +1
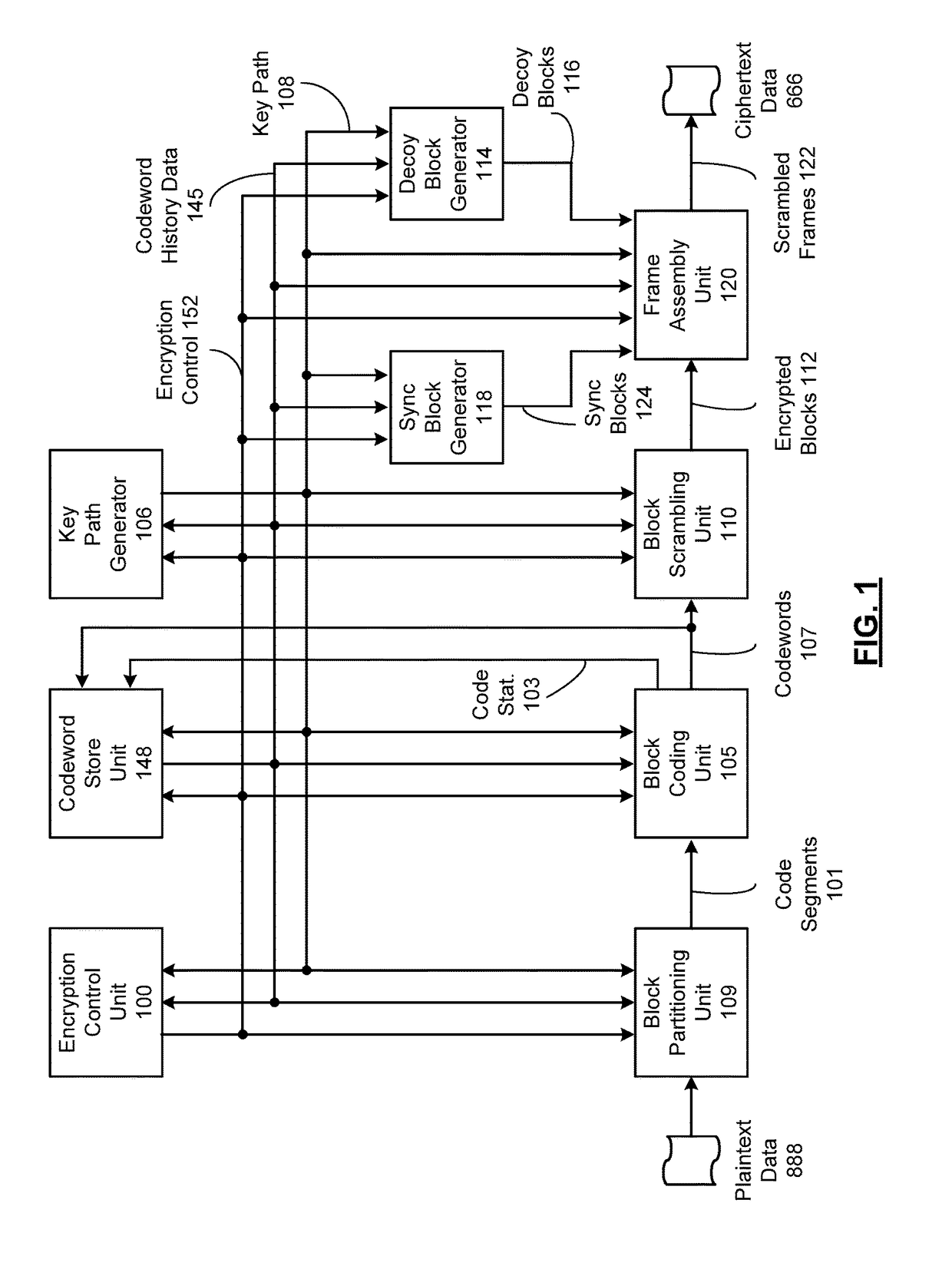
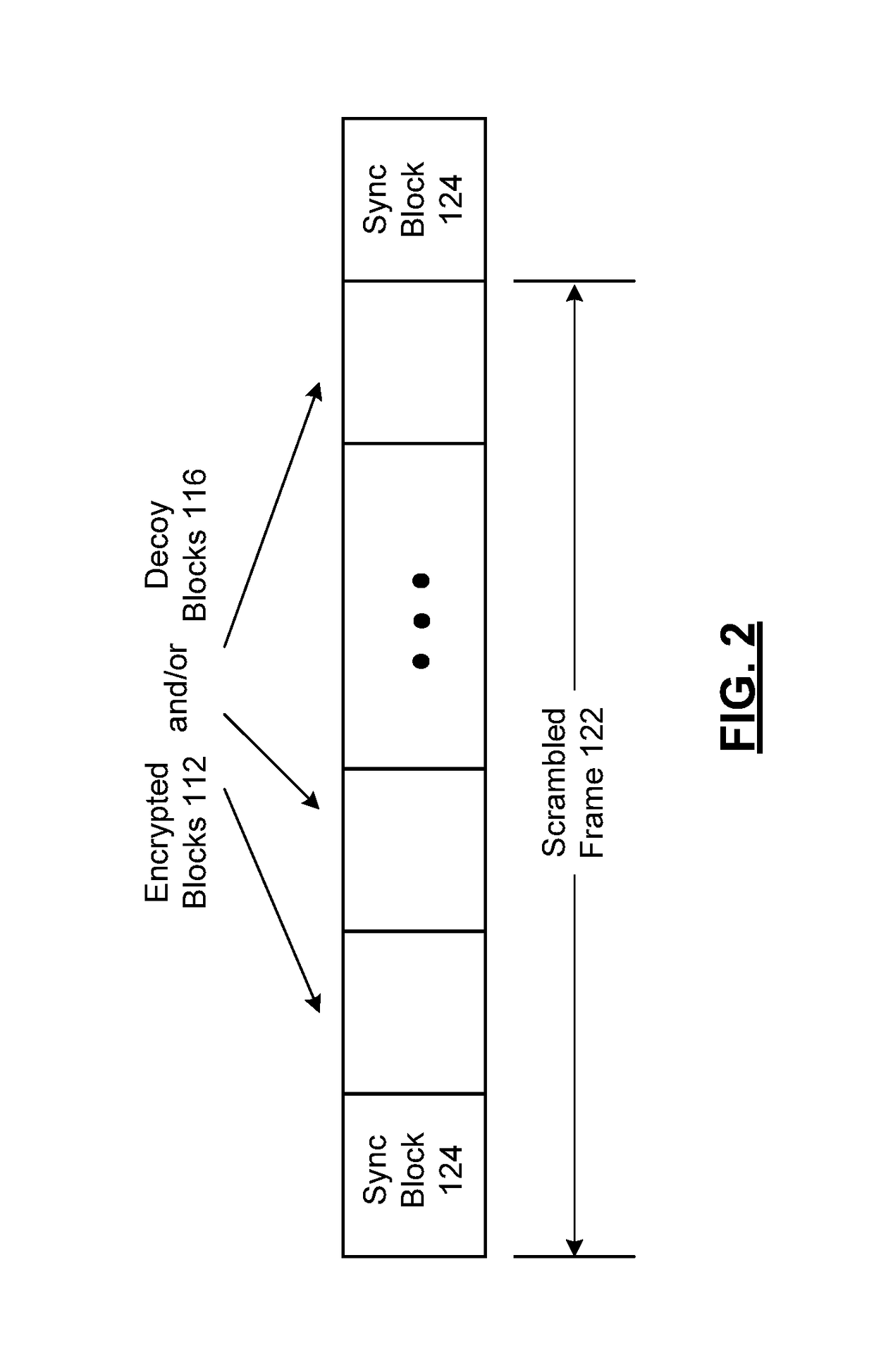
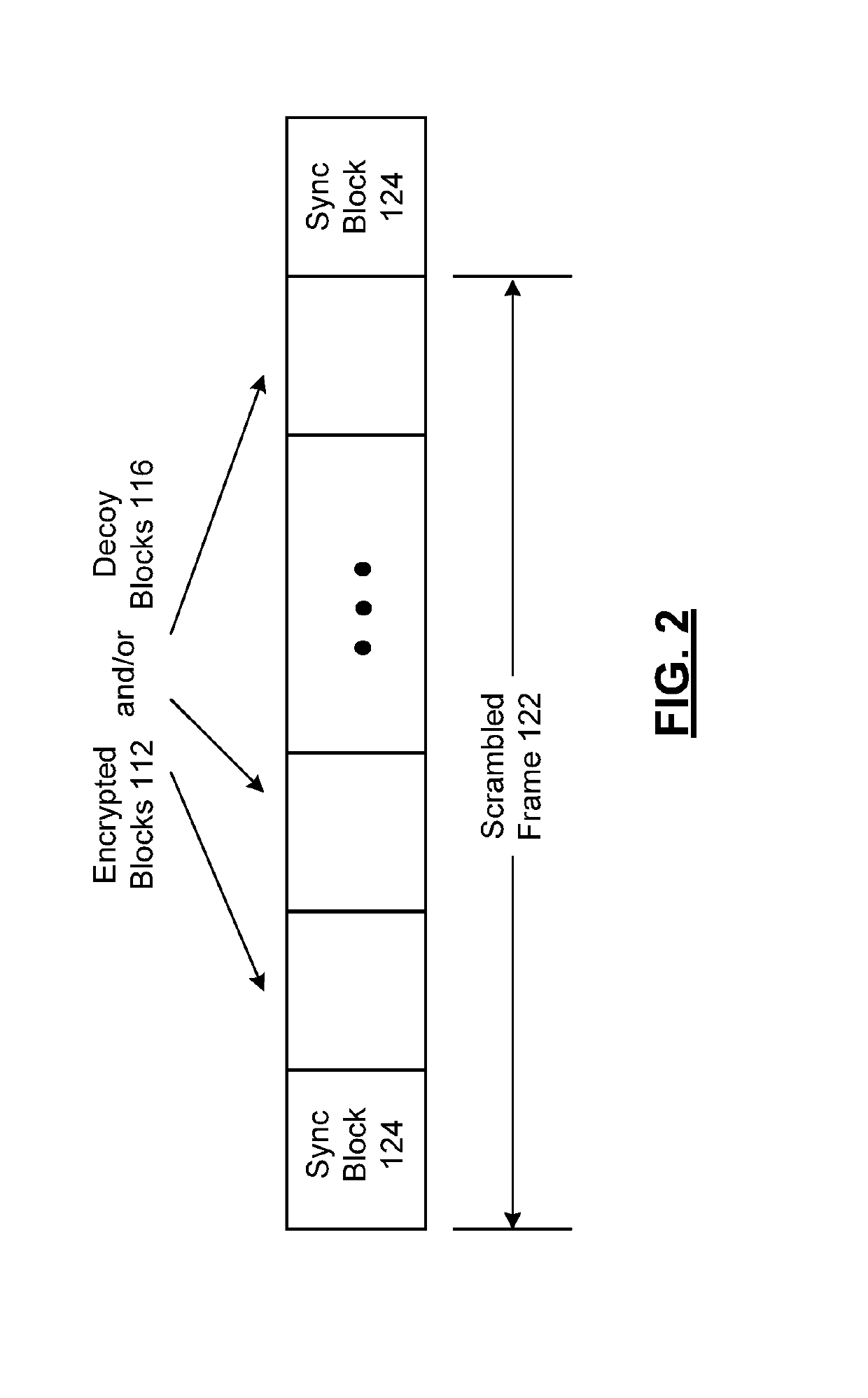
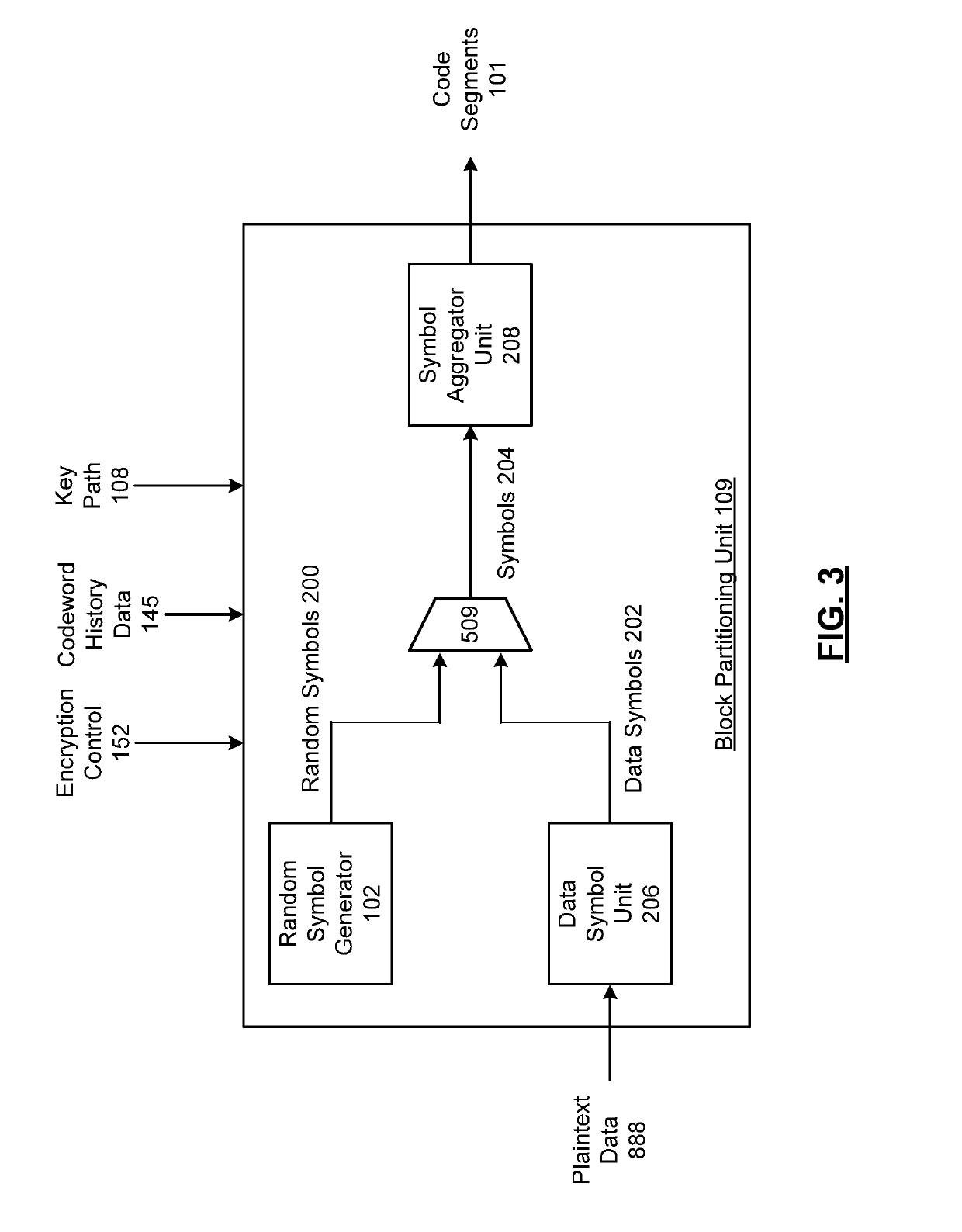
System for scrambling and methods for use therewith
ActiveUS20180083775A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesCryptographic key generationComputer hardware
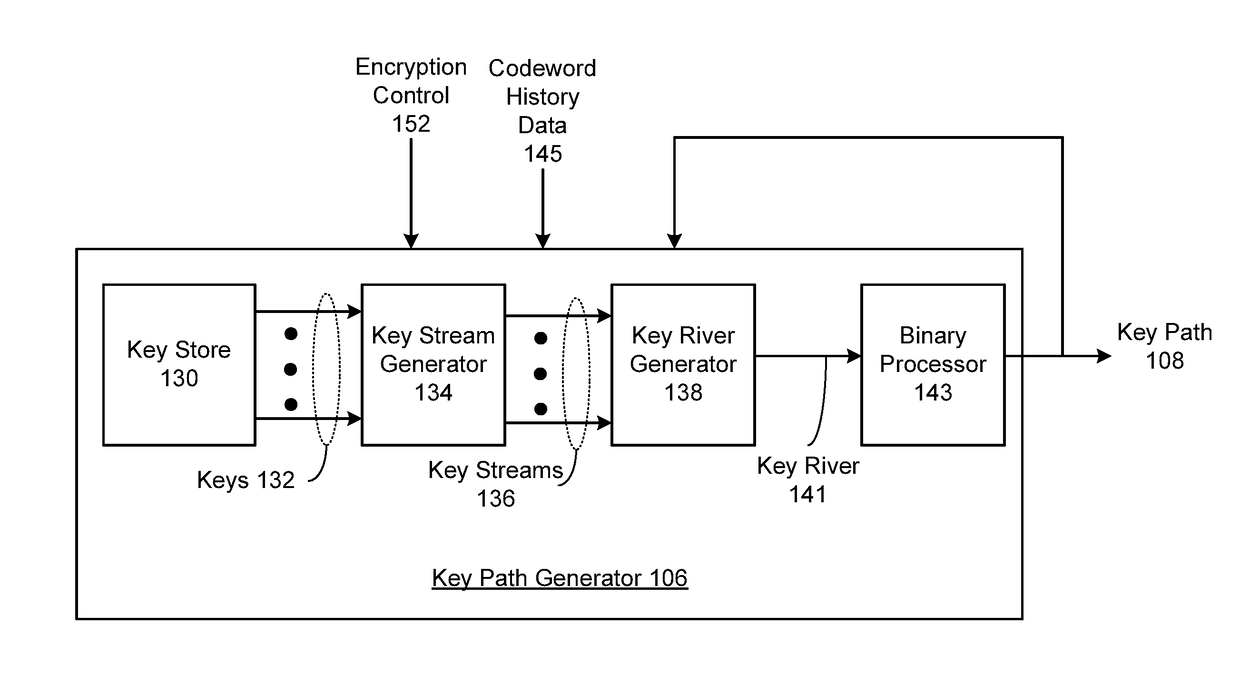
Processing circuitry includes key store hardware that stores a plurality of encryption keys. Key stream generator hardware generates a plurality of key streams from the plurality of encryption keys, wherein each key stream comprises a repeating stream of key data. Key river generator hardware generates a key river by parallelizing the plurality of key streams as key river symbols, wherein bits from each key river symbol are selected from each key stream as individual bits from differing ones of the plurality of encryption keys. Binary processor hardware generates a key path as a sequence of binary digits generated from at least one binary function of the key river.
Owner:HUANG LAWRENCE P
Method of generating message authentication code using stream cipher and authentication/encryption and authentication/decryption methods using stream cipher
InactiveUS8090098B2Secret communicationSecuring communicationComputer hardwareHash-based message authentication code
Provided are a method of generating a Message Authentication Code (MAC) using a stream cipher, and authentication / encryption and authentication / decryption methods using a stream cipher.According to the methods, authentication / encryption is performed using a MAC generated using a stream cipher as an initialization vector of the stream cipher. Therefore, it is unnecessary to use a random number generation algorithm to generate the initialization vector, and thus implementation efficiency can be improved.In addition, upon generation of a MAC, a plurality of key stream generators perform computation for a plurality of message blocks, respectively. Therefore, the message blocks are computed in parallel at a time, and thus computation efficiency is excellent.
Owner:NAINFOX CO LTD
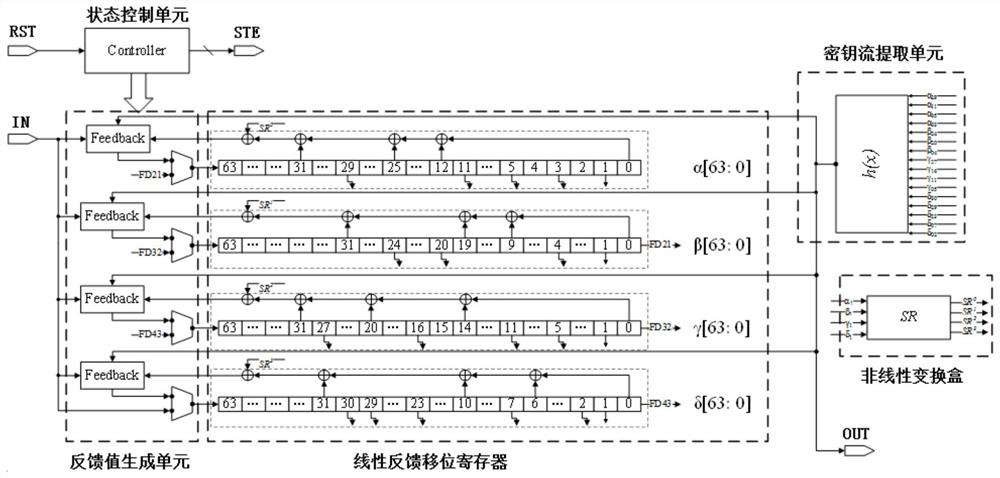
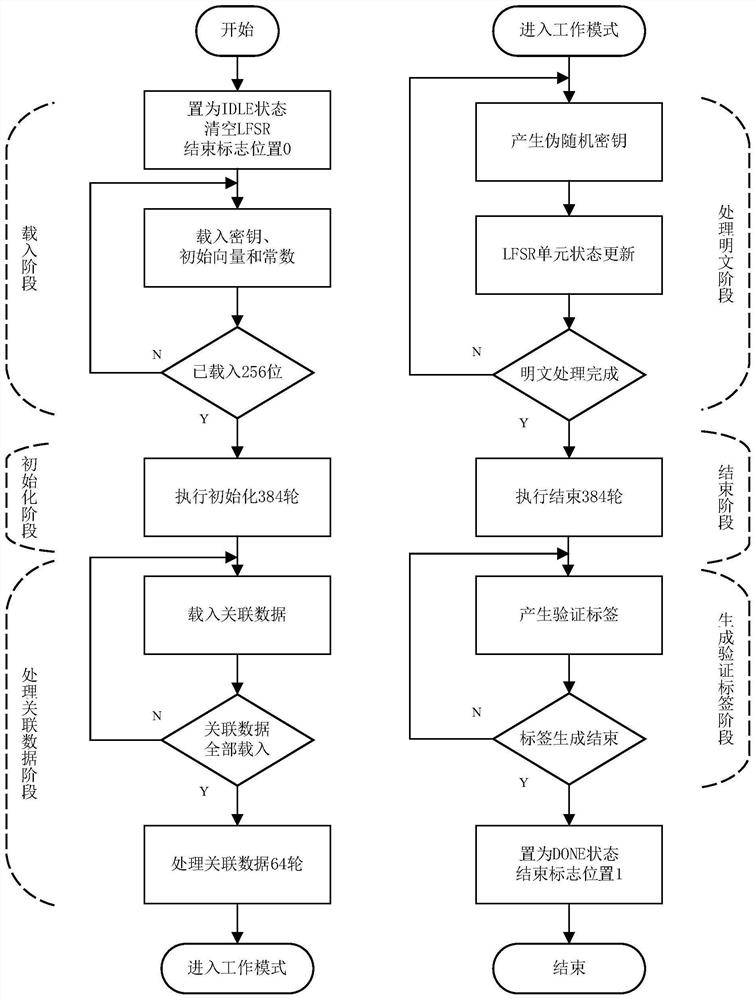
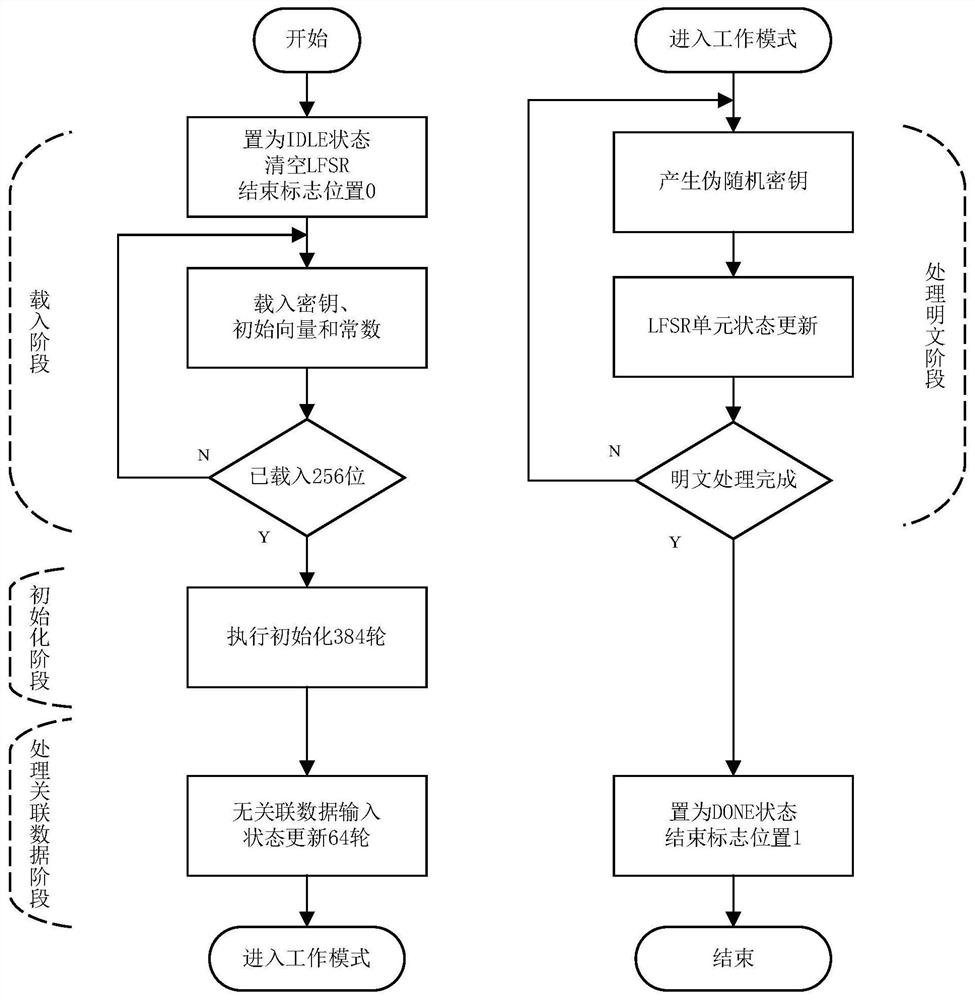
Implementation device, method and application of Fountain lightweight encryption algorithm
ActiveCN112398639AImprove data throughputCompact designData stream serial/continuous modificationParallel computingThe Internet
The invention discloses an implementation device, method and application of a Fountain lightweight encryption algorithm. The device comprises a state control unit, a linear feedback shift register, anonlinear transformation box, a key stream extraction unit and a feedback value generation unit. The implementation method comprises an area optimization scheme and a parallel scheme, and the application comprises the steps of generating a Fountain stream password, generating a Fountain type key stream generator and generating a Fountain type MAC function. The Fountain lightweight encryption algorithm disclosed by the invention is compact in design, resource-saving, low in time delay and high in security, improves the data throughput rate, and can meet the data encryption requirement of the Internet-of-Things terminal equipment with resource shortage.
Owner:SHANDONG UNIV
E-mail data security protection method based on hybrid encryption
ActiveCN111049738AWith integrity authentication functionImprove securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesConfidentialityKeystream generator
The invention relates to an e-mail data security protection method based on hybrid encryption. An existing data encryption method is relatively low in confidentiality or more in memory resources. Thepresent invention includes a data encryption method for e-mail communication between terminals and a data encryption method for communication between terminals and a server. The server generates a pair of public key and private key for asymmetric encryption, and issues the server public key to the client for storage. A client generates a pair of public and private keys for asymmetric encryption, and uploads the public key of the client to the server; the server sets a client public key library, and stores each client public key and the registration ID serving as the identifier in the client public key library; the client is provided with a key stream generator, and generates a symmetric key by setting the number of registers. A symmetric encryption method and an asymmetric encryption method are combined so thatthe advantages of high speed of a symmetric encryption mechanism and higher security of asymmetric encryption are integrated, the occupied resources are few, and the confidentiality is high.
Owner:杭州安司源科技有限公司
Cryptographic checksum apparatus
InactiveUS6477652B1Reduce the chance of counterfeitingReduce probabilityUser identity/authority verificationUnauthorized memory use protectionComputer hardwareTransmission gate
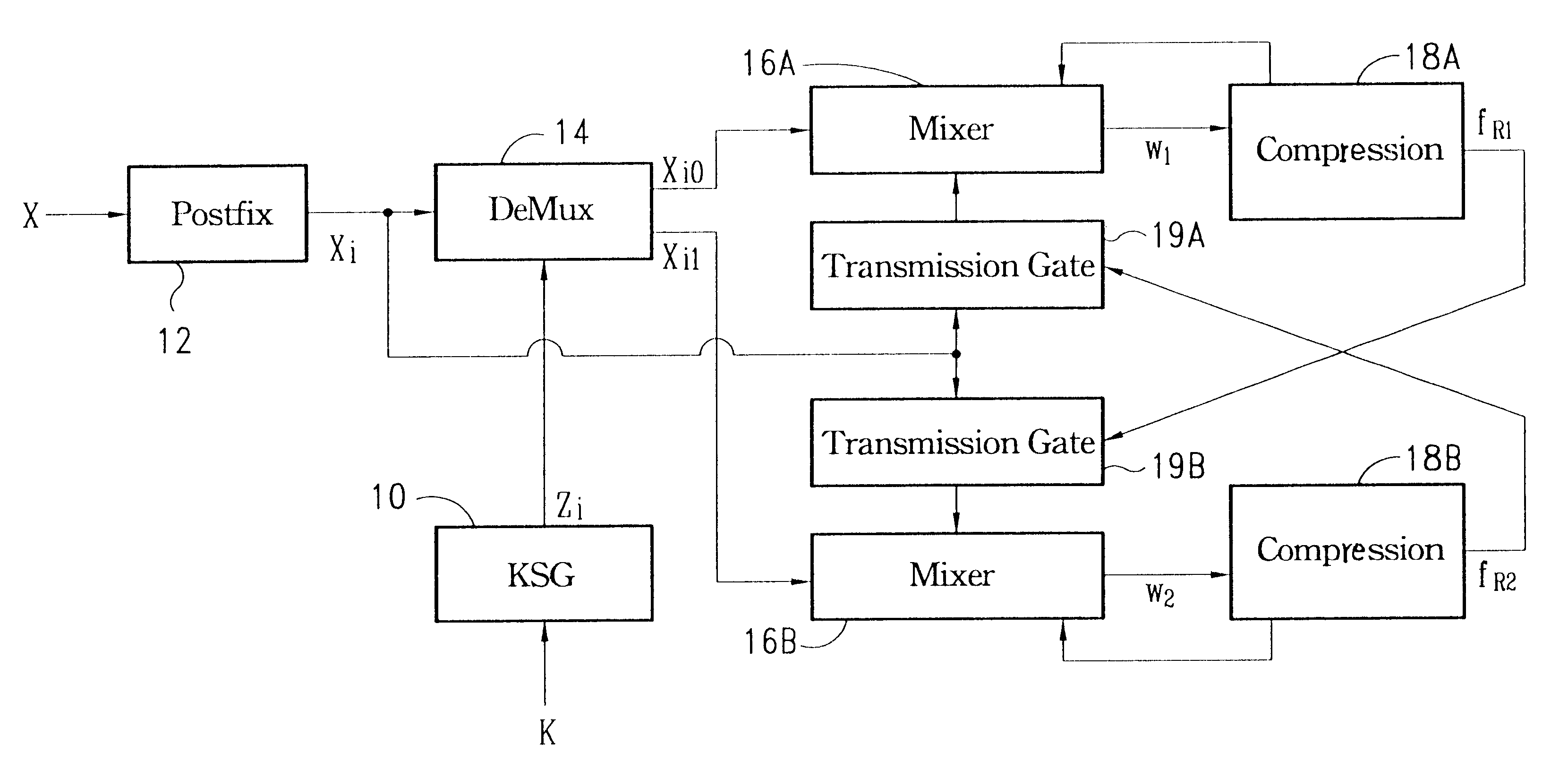
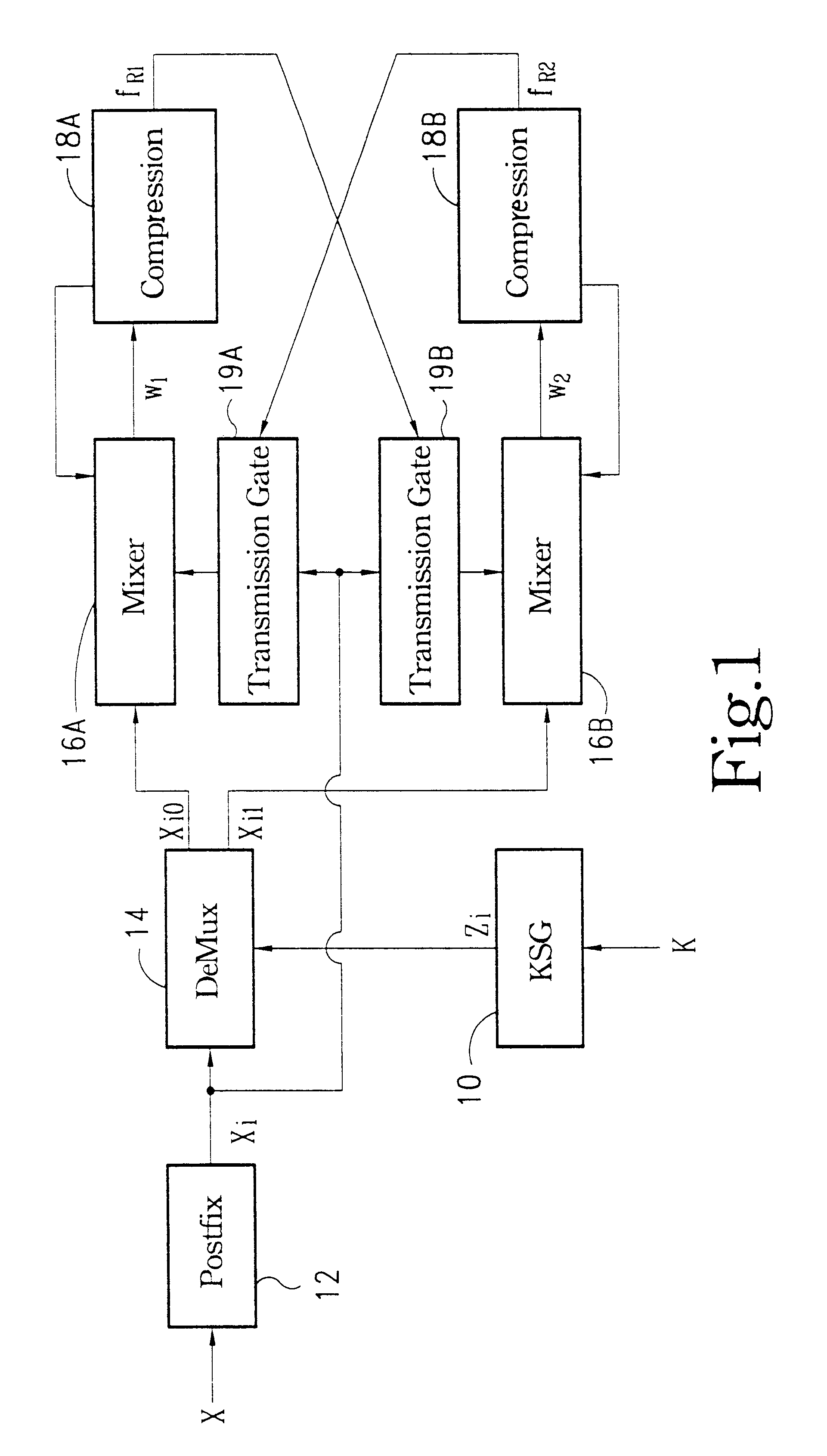
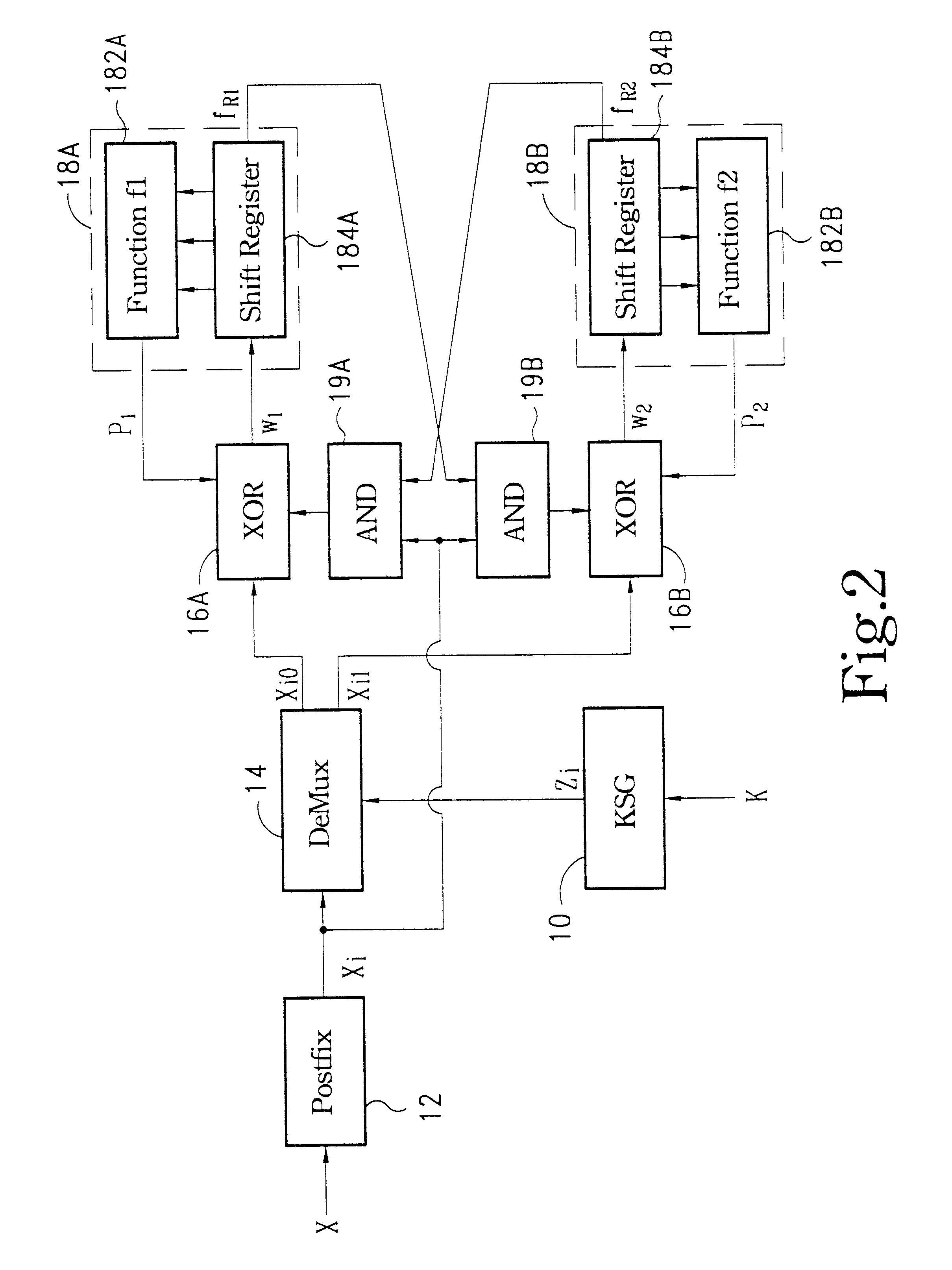
A cryptographic checksum apparatus is disclosed. This apparatus includes a keystream generator configured to generate a secret keystream according to a common secret key. The apparatus also includes a postfix circuit configured to augment postfix bits after an original message. Further, a demultiplexer is used to direct the postfixed message to one of the output terminals under the control of the secret keystream. A first mixer is connected to one output terminal of the demultiplexer, and a second mixer is connected to the other output terminal of the demultiplexer. Moreover, a first compression circuit is used to receive an output of the first mixer, wherein content of the first compression circuit is used as the first part of the checksum output. Similarly, a second compression circuit is used to receive an output of the second mixer, wherein content of the second compression circuit is used as the second part of the checksum output. Finally, a first transmission gate is connected to the second compression circuit, whose output bit is then transferred to the first mixer through the first transmission gate under control of the postfixed message bit. A second transmission gate is connected to the first compression circuit, whose output bit is then transferred to the second mixer through the second transmission gate under control of the postfixed message bit.
Owner:INSTITUTE FOR INFORMATION INDUSTRY
Method and system for hardware accelerator for implementing f8 confidentiality algorithm in WCDMA compliant handsets
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
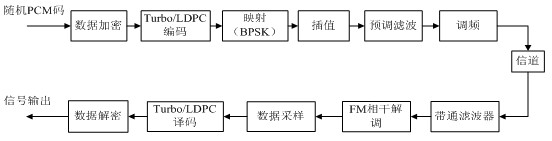
PCM/FM telemetering system-based data security communication method
InactiveCN102082661AImprove securityGood linear complexityKey distribution for secure communicationComputer hardwareLinear complexity
The invention relates to a pulse code modulation (PCM) / frequency modulation (FM) telemetering system-based data security communication method. The method comprises the following steps of: assigning a cipher key until an initial key generator generates an initial key; generating a key stream through a clock-controlled key stream generator, and generating a next group of data cipher keys; generating ciphertext from data to be transmitted and key stream exclusive OR, packaging into a frame, and performing Turbo encoding on the packaged data frame; and finally, performing signal sampling on the data subjected to the Turbo encoding, performing preset filtering on the sampled data, feeding the data into a channel through FM modulation, wherein a receiving end receives and synchronizes the signal, and at the receiving end, the signal is processed in an inverted sequence in turn and is successively subjected to coherent demodulation, data sampling, Turbo code decoding and decryption through the FM so as to obtain the needed data finally. The method has high linear complexity, can effectively protect the data, and improves security of the PCM / FM telemetering system.
Owner:HANGZHOU DIANZI UNIV
Method and apparatus for synchronous stream cipher encryption with reserved codes
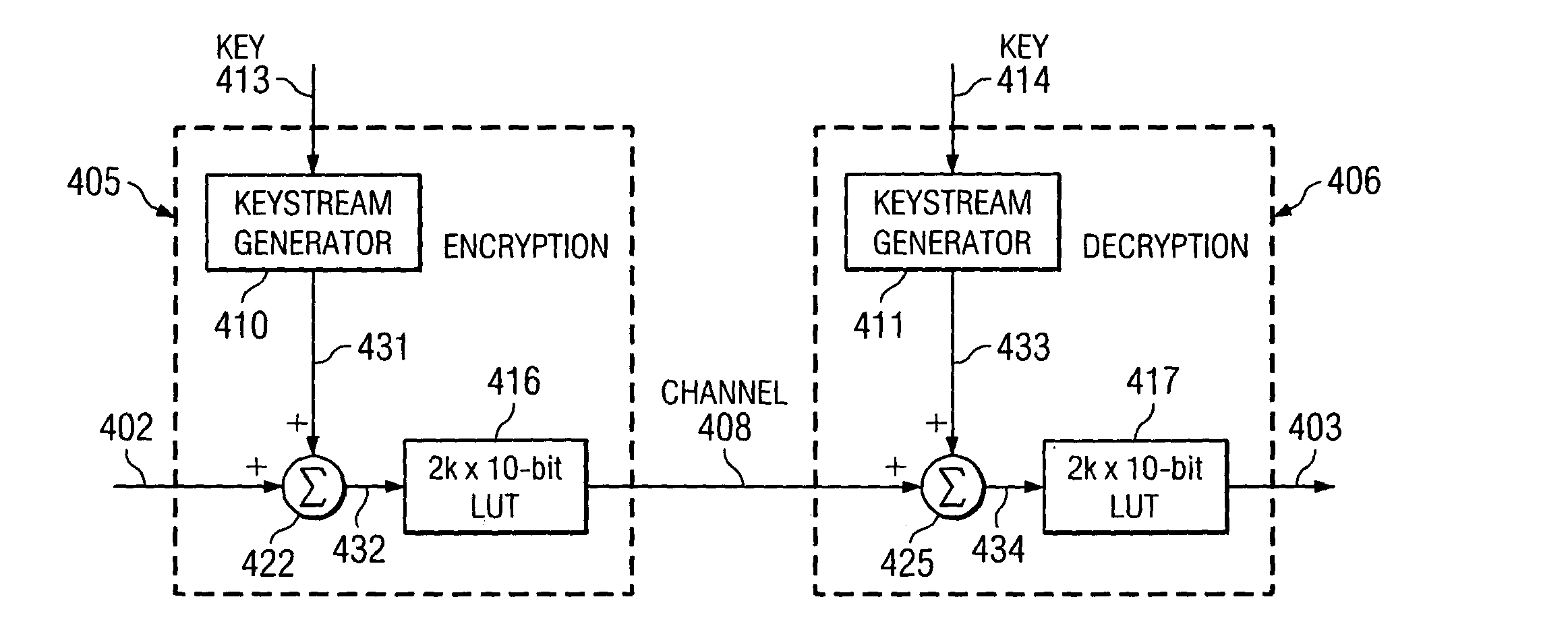
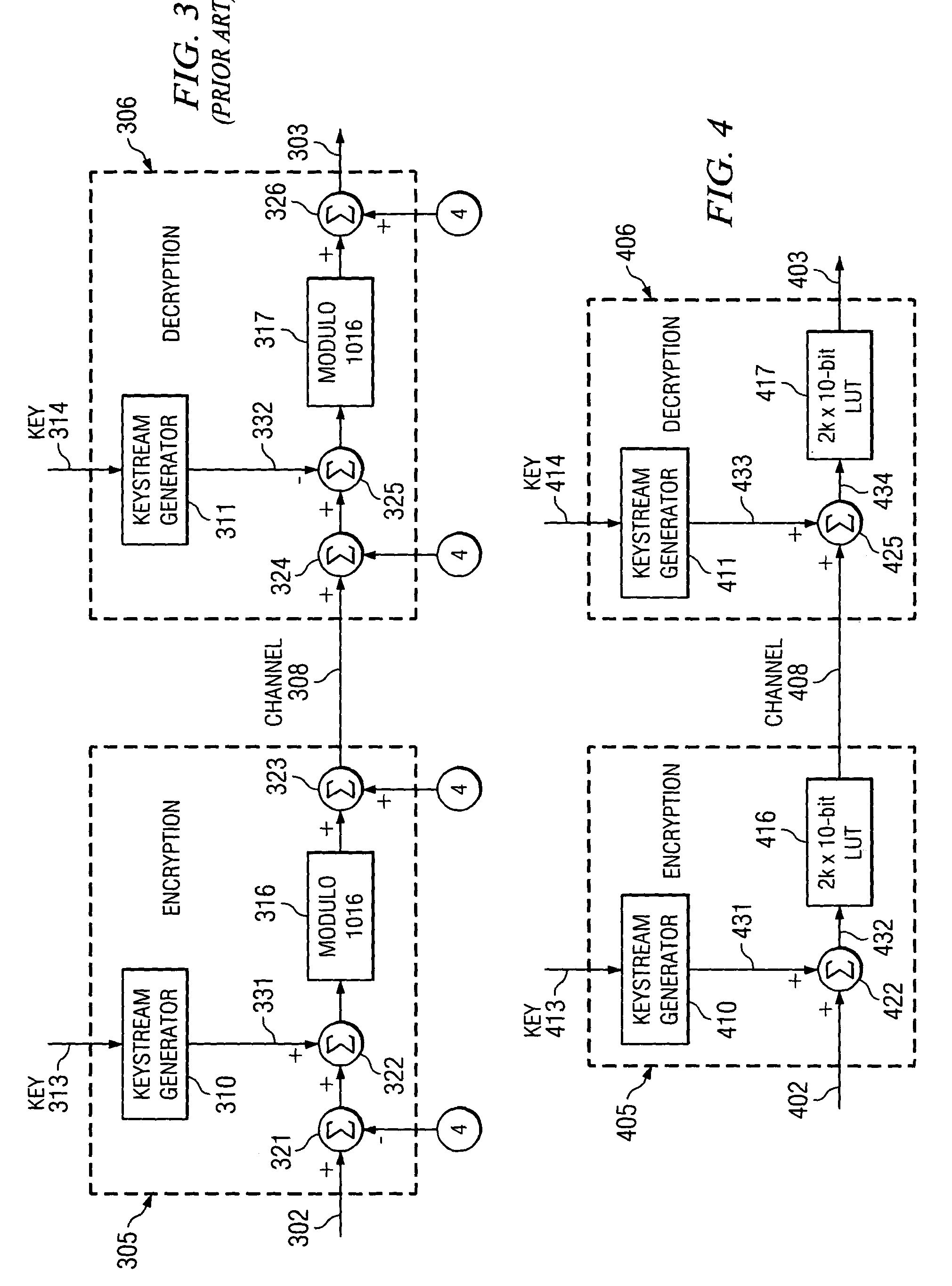
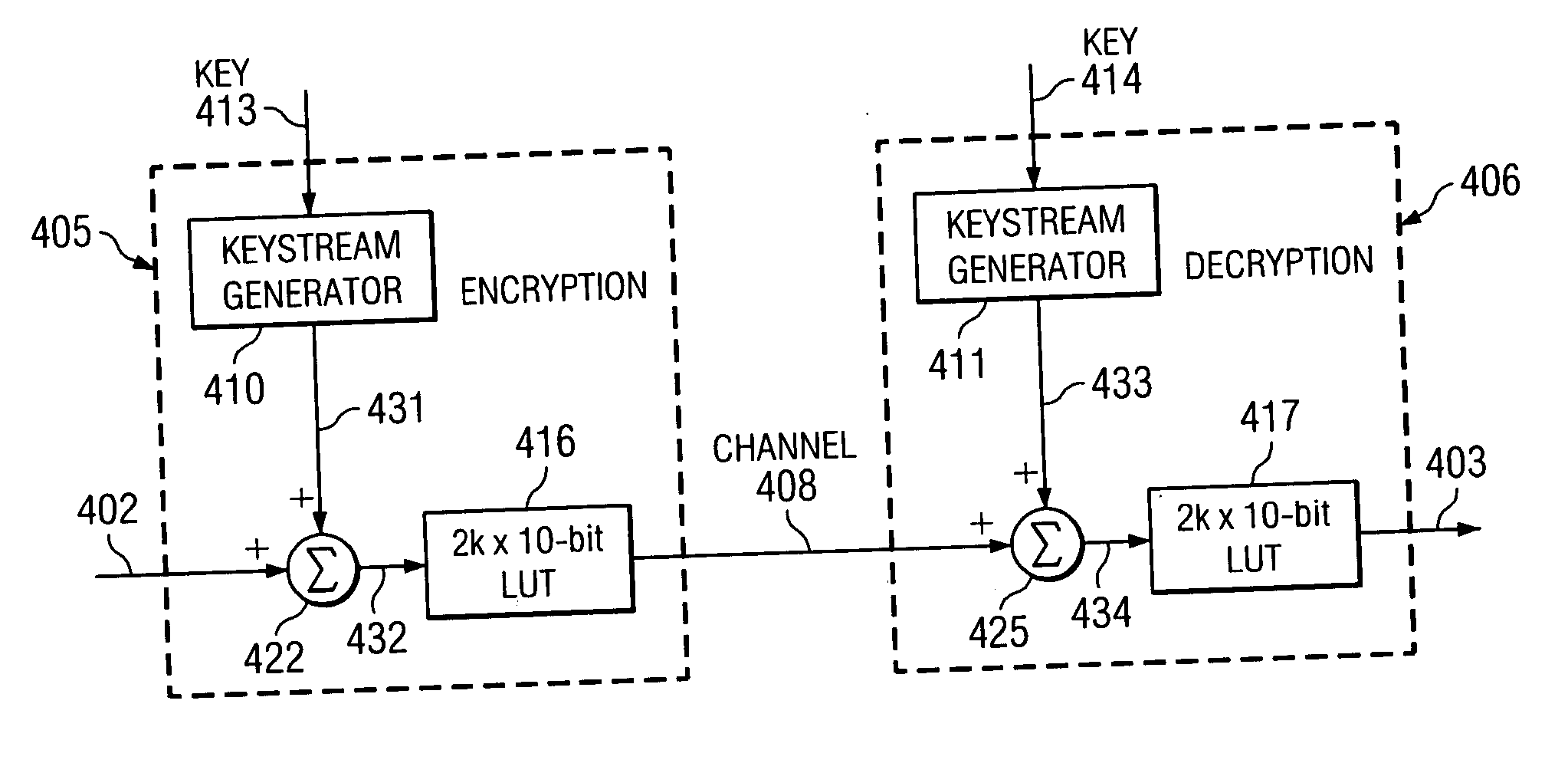
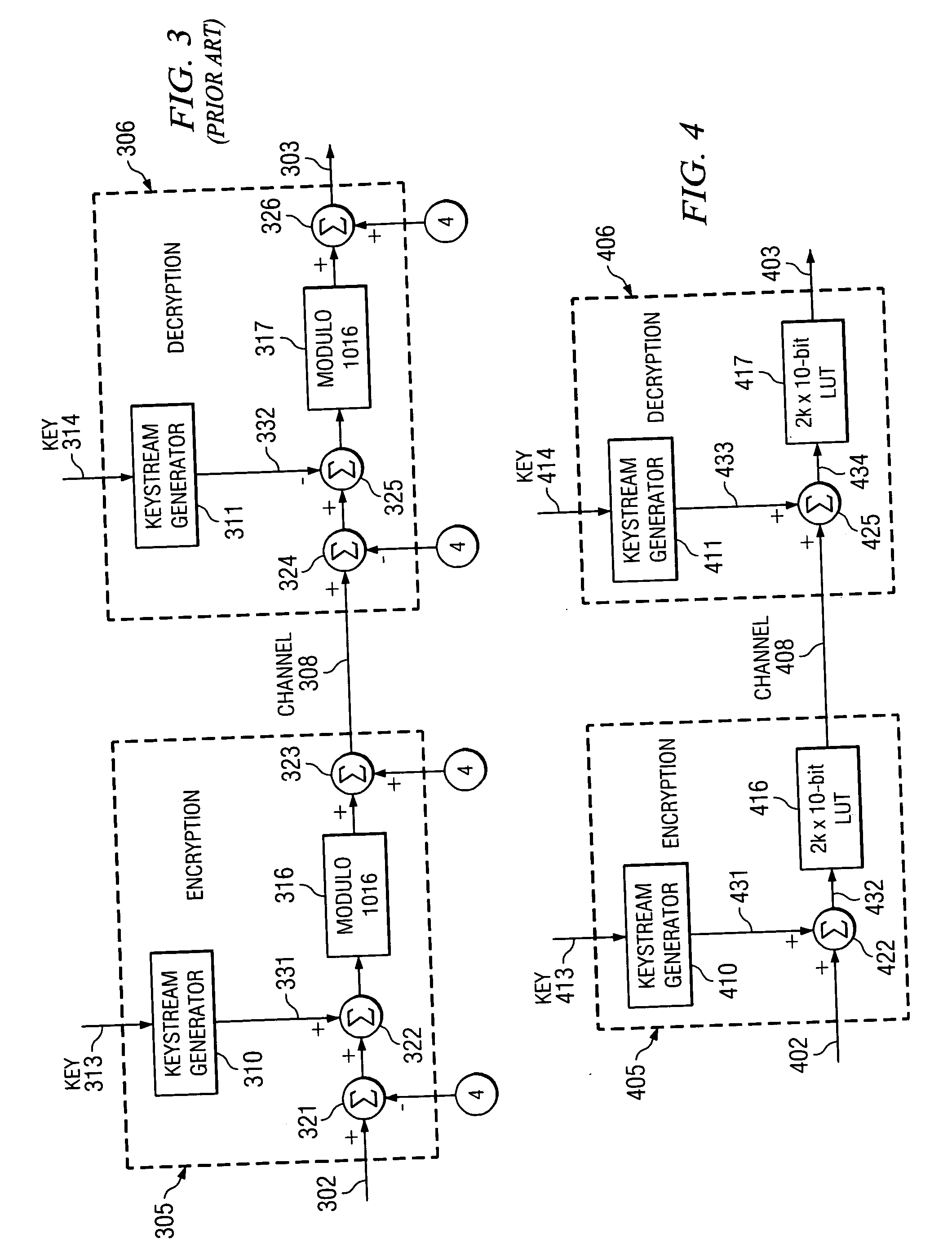
ActiveUS7734044B2User identity/authority verificationSecret communicationComputer hardwareKeystream generator
A method and apparatus for a signal encryption device constructed to perform synchronous stream cipher encryption for a sequence of input words with restricted codes. The encryption device includes a keystream generator for producing a sequence of pseudorandom words from a key, and an adder that is used to sum the output of the keystream generator and the input words. A lookup table of size substantially twice the number of possible input words provides encrypted codes excluding restricted codes from the summed signal. A signal encryption and decryption system is constructed by including a second keystream generator for producing a second sequence of pseudorandom words from the key, and a second adder to produce a second summed signal from the output of the second keystream generator and the encrypted codes. A corresponding lookup table provides decrypted codes excluding restricted codes from the second summed signal.
Owner:TEXAS INSTR INC
Method and apparatus for synchronous stream cipher encryption with reserved codes
ActiveUS20080019513A1User identity/authority verificationSecret communicationComputer hardwareKeystream generator
A method and apparatus for a signal encryption device constructed to perform synchronous stream cipher encryption for a sequence of input words with restricted codes. The encryption device includes a keystream generator for producing a sequence of pseudorandom words from a key, and an adder that is used to sum the output of the keystream generator and the input words. A lookup table of size substantially twice the number of possible input words provides encrypted codes excluding restricted codes from the summed signal. A signal encryption and decryption system is constructed by including a second keystream generator for producing a second sequence of pseudorandom words from the key, and a second adder to produce a second summed signal from the output of the second keystream generator and the encrypted codes. A corresponding lookup table provides decrypted codes excluding restricted codes from the second summed signal.
Owner:TEXAS INSTR INC
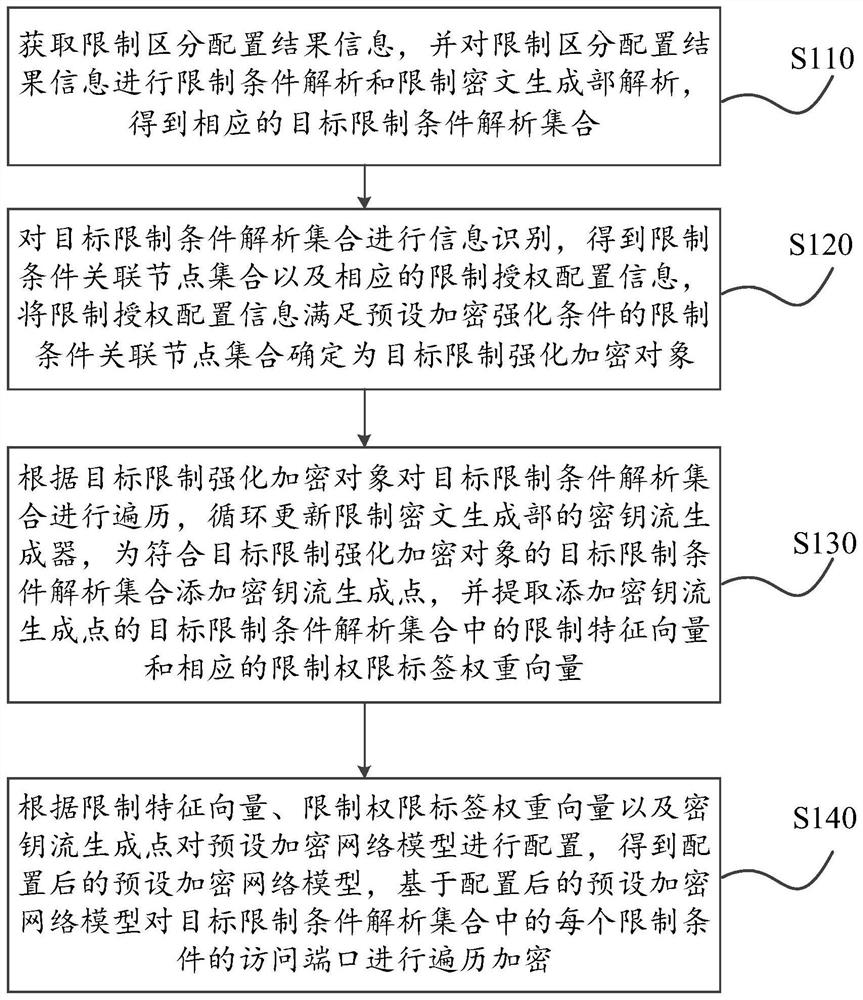
Information protection method based on cloud computing and blockchain service and artificial intelligence platform
The embodiment of the invention provides an information protection method based on cloud computing and blockchain service and an artificial intelligence platform, wherein the method comprises the steps: carrying out iterative calibration of a limiting ciphertext generation part for a limiting lock object in limiting and distinguishing configuration result information, and achieving the continuousupdating of a key stream generator of the limiting ciphertext generation part; and fusing a limiting feature vector and a corresponding limiting authority label weight vector to configure a preset encryption network model, so as to enable the configured preset encryption network model to have higher encryption reliability when traversing and encrypting the access port of each limiting condition inthe target limiting condition analysis set, thereby enhancing the restrictive distinguishing configuration effect.
Owner:TOP LEARNING BEIJING EDUCATION TECH CO LTD
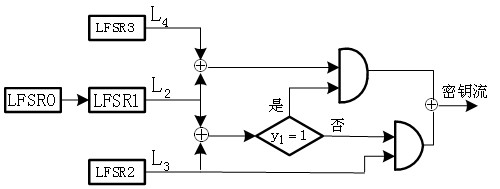
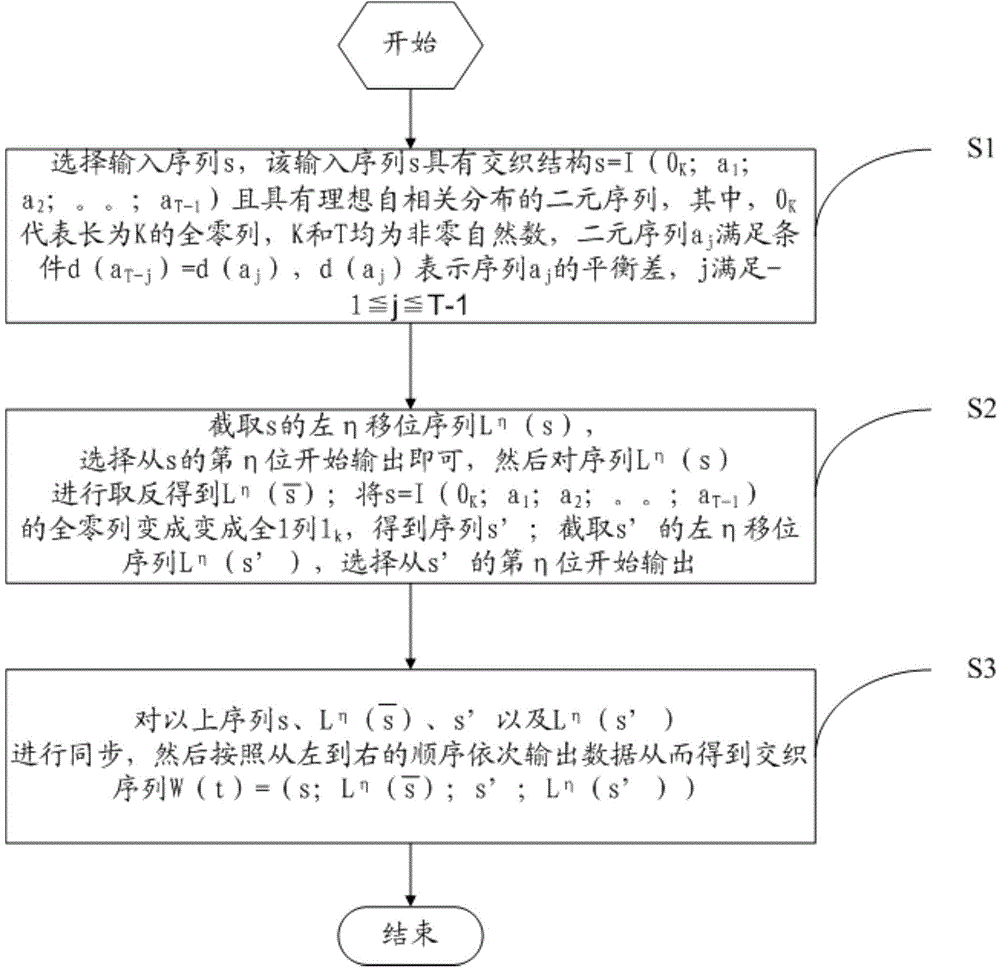
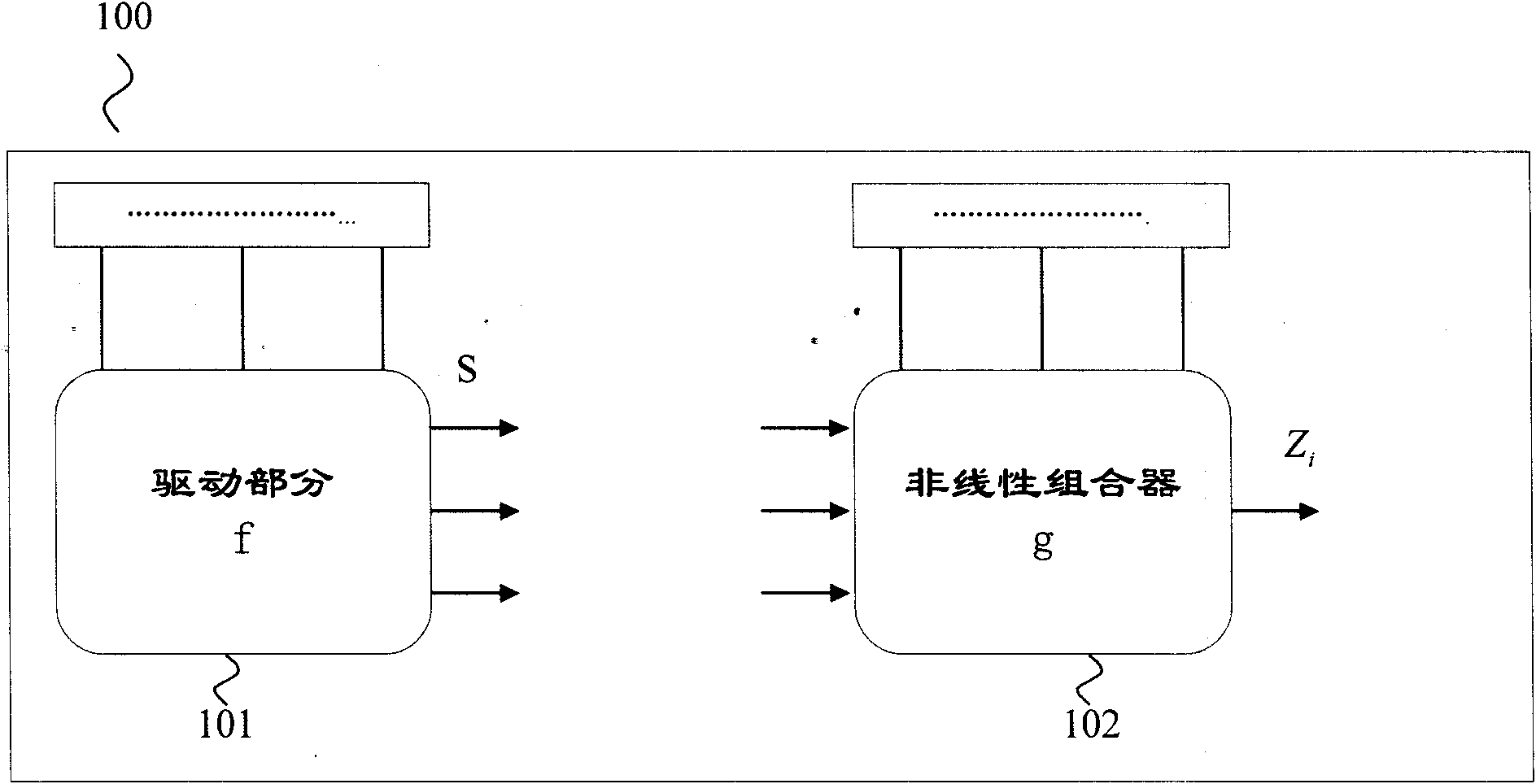
Interweaving technology-based key stream generation method and device
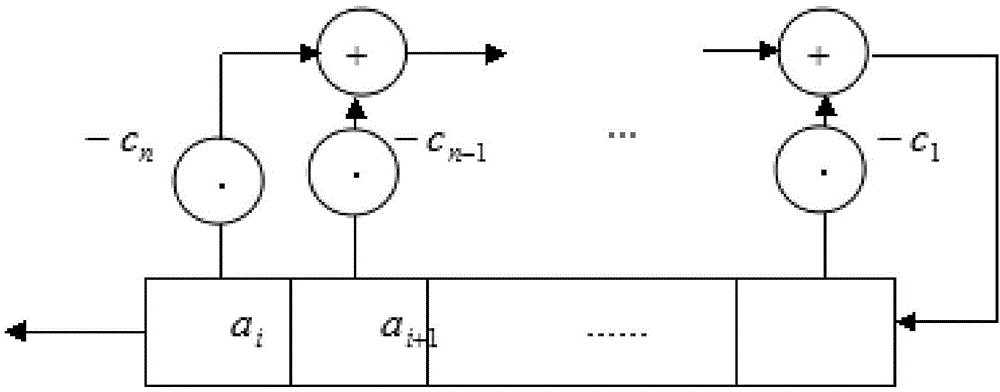
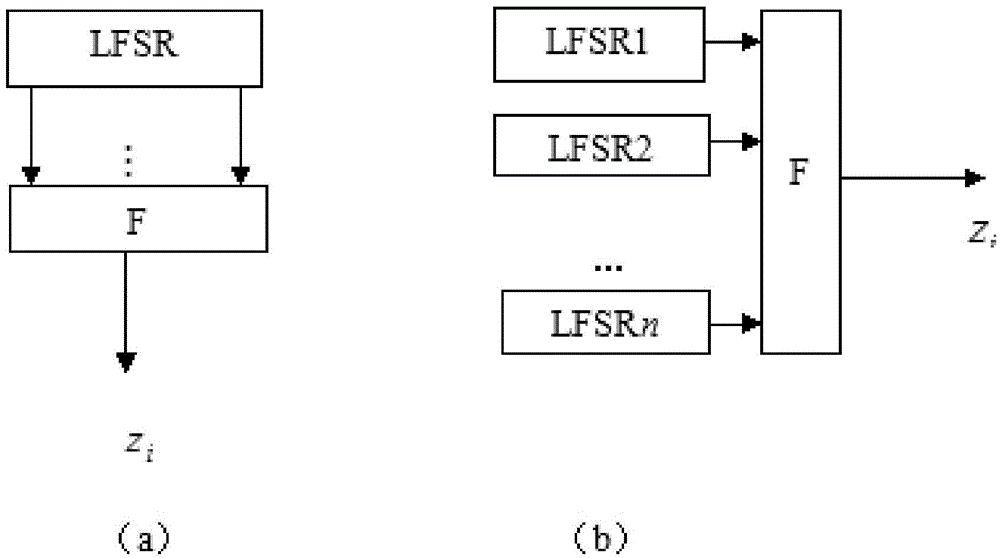
ActiveCN104158654AIncrease the number of levelsGood autocorrelation propertyKey distribution for secure communicationSelf correlationKeystream generator
The invention provides an interweaving technology-based key stream generation method and device. A conventional key stream generator is transformed, non-linear combination assemblies are added, and data is output by using a plurality of taps of an original key stream generator to perform organic combination and interweaving, so that the period of a new sequence is increased by 4 times. Through adoption of the method and the device, the period is increased by 4 times under the condition of not increasing the storage space, and meanwhile the good self-correlation property of an original sequence is kept.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
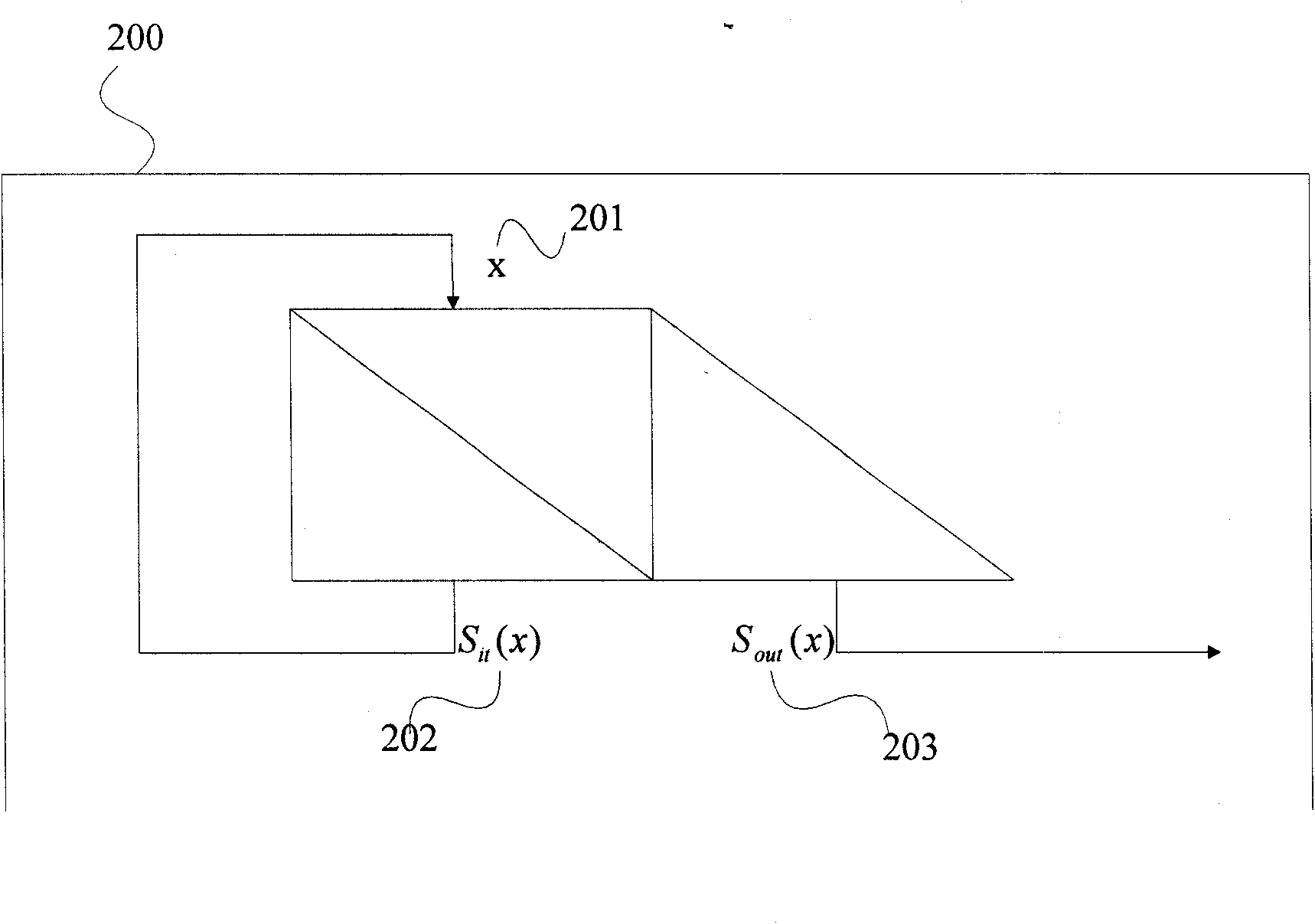
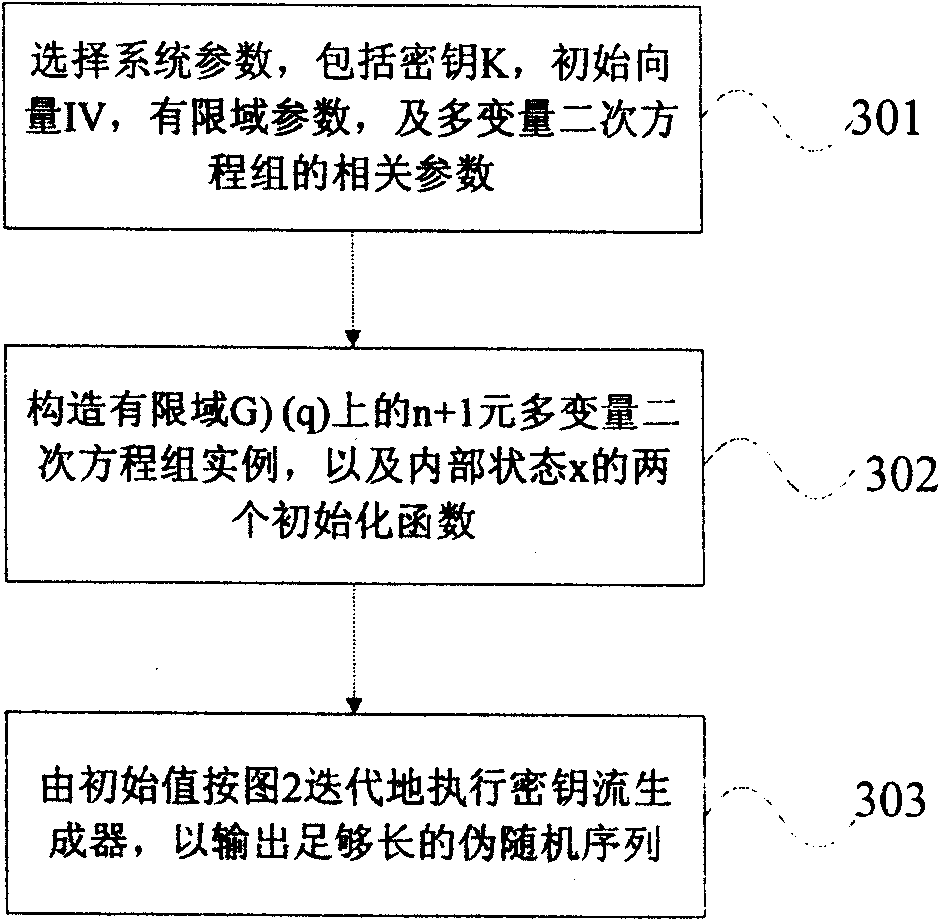
Approved safe key stream generator based on multivariate quadratic equation
The invention designs a key stream generator which can be used for computing the output pseudo-random sequence with random length under the condition of low resource consumption, and the generating algorithm of the key stream generator can be approved to be safe; the safety of the key stream generator is based on the difficulty of solving multivariate quadratic equation set within a finite field and can meet the design demand of the approved safe key stream generator, so that the key stream generator can be applied to the field with higher requirement for the safety. In one instance, the key stream generator is defined by multivariate multinomial set on one GF (q), and the q is large prime number. By selecting proper parameter, key stream with random bit can be generated at higher speed according to the length of plaintext, and the safety level of 2<80> can be reached, so that the key stream generator can meet the application need of most current passwords.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Method and system for implementing the GEA3 encryption algorithm for GPRS compliant handsets
InactiveUS7627115B2Data stream serial/continuous modificationSecret communicationComputer hardwareCommunications system
In a wireless communication system, a method and system for implementing the GEA3 encryption algorithm for GPRS compliant handsets are provided. An intermediate value may be generated based on initialized input variables, a cipher key and a key modifier. A first processing block of output bits may be generated by a keystream generator from the intermediate value, the cipher key, and an indication of the processing block of output bits being processed. Additional processing blocks of output bits may also be generated by the keystream generator based on an immediately previous processing block of output bits, the intermediate value, the cipher key, and an indication of the processing block of output bits being processed. A restart signal may indicate that subsequent processing blocks of output bits may be generated by the keystream generator by utilizing the same cipher key and the generated intermediate value.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
System for scrambling and methods for use therewith
ActiveUS10439802B2Key distribution for secure communicationEncryption apparatus with shift registers/memoriesCryptographic key generationComputer hardware
Processing circuitry includes key store hardware that stores a plurality of encryption keys. Key stream generator hardware generates a plurality of key streams from the plurality of encryption keys, wherein each key stream comprises a repeating stream of key data. Key river generator hardware generates a key river by parallelizing the plurality of key streams as key river symbols, wherein bits from each key river symbol are selected from each key stream as individual bits from differing ones of the plurality of encryption keys. Binary processor hardware generates a key path as a sequence of binary digits generated from at least one binary function of the key river.
Owner:HUANG LAWRENCE P
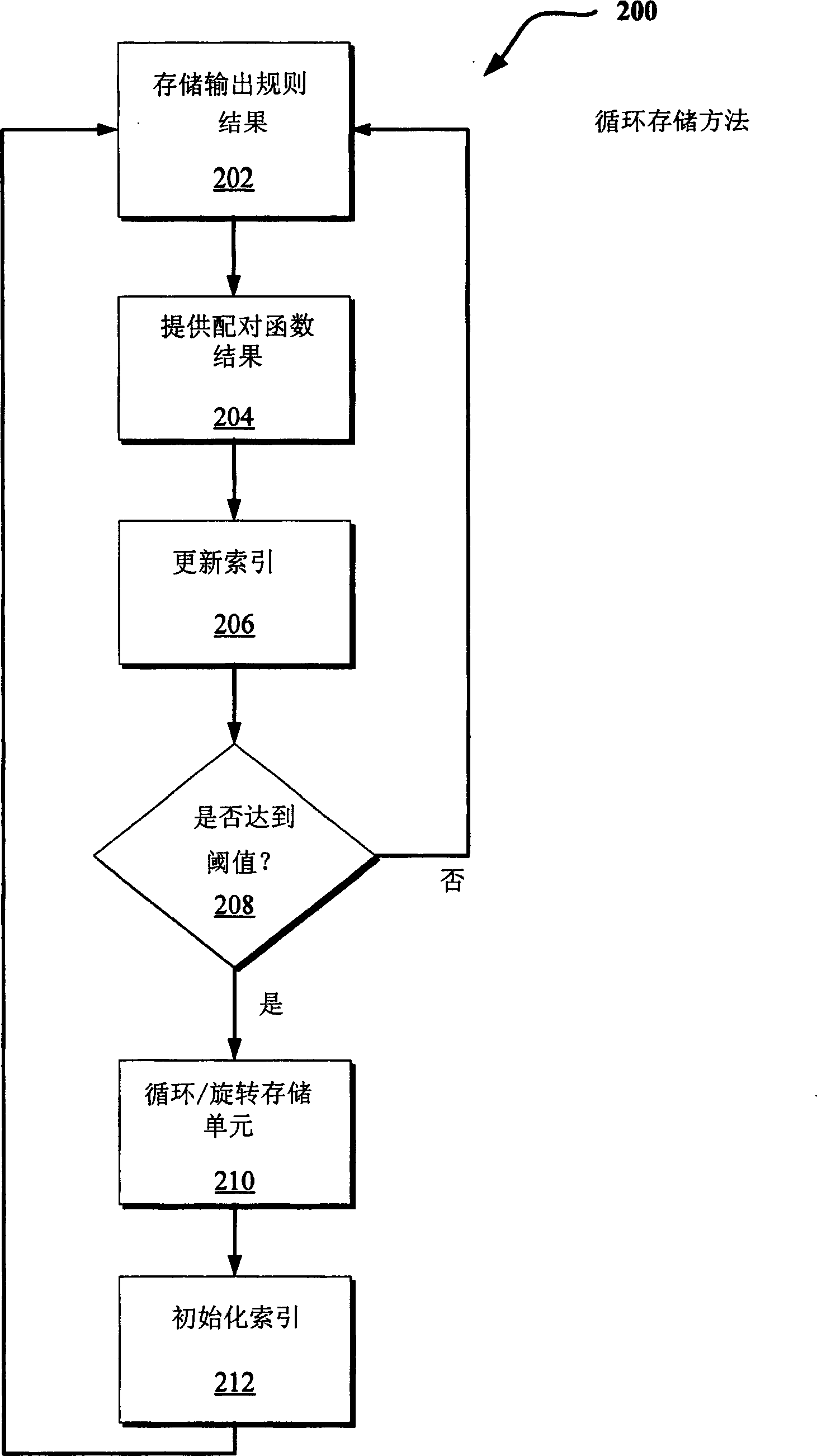
Stream cipher design with revolving buffers
InactiveCN1677917AData stream serial/continuous modificationRollersParallel computingKeystream generator
Techniques are disclosed to limit short-term correlations associated with outputs of stream cipher keystream generators. Output values of a generator are paired such that the paired outputs are sufficiently far apart to be considered independent. In one described implementation, a method includes sequentially storing a plurality of results provided by a stream cipher output rule in a first, second, and third storage units. A pairing function pairs individual values from the first and third storage units that are at least a threshold value apart. Upon reaching the threshold value of the output rule results, the contents of the first, second, and third storage units are rotated serially.
Owner:MICROSOFT CORP
A key stream generation method and device based on interleaving technology
ActiveCN104158654BIncrease the number of levelsGood autocorrelation propertyKey distribution for secure communicationSelf correlationKeystream generator
The invention provides an interweaving technology-based key stream generation method and device. A conventional key stream generator is transformed, non-linear combination assemblies are added, and data is output by using a plurality of taps of an original key stream generator to perform organic combination and interweaving, so that the period of a new sequence is increased by 4 times. Through adoption of the method and the device, the period is increased by 4 times under the condition of not increasing the storage space, and meanwhile the good self-correlation property of an original sequence is kept.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
Method and system for implementing the A5/3 encryption algorithm for GSM and EDGE compliant handsets
InactiveUS7623658B2Data stream serial/continuous modificationSecret communicationComputer hardwareCommunications system
In a wireless communication system, a method and system for implementing the A5 / 3 encryption algorithm for GSM and EDGE compliant handsets are provided. Input variables may be initialized in a keystream generator and an intermediate value may be generated with a cipher key parameter and a key modifier. A number of processing blocks of output bits may be determined based on a number of bits in an output keystream. The processing blocks of output bits may be generated utilizing a KASUMI operation and may be based on an immediately previous processing block of output bits, the intermediate value, and an indication of the processing block of output bits being processed. The processing blocks of output bits may be generated after an indication that an immediately previous processing block of output bits is available and may be grouped into two final blocks of output bits in the output keystream.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Image encryption method and device, key stream generation method, and key stream generator
ActiveCN106407824BReduce computational complexityImprove encryption securityDigital data protectionSecuring communicationComputer hardwareComputation complexity
The invention relates to an image encryption method, an image encryption device, a key stream generation method and a key stream generator. The image encryption method comprises following steps of constructing a coupling image grid sequence based on the initial value, processing the coupling image grid sequence to be a first key stream by means of symmetric matrix transformation, replacing the first key stream through a password displacement box to obtain a second key stream, scrambling the original image by means of the first key stream, carrying out block encoding to the scrambled image by means of the second key stream, and obtaining the encrypted image data. According to the invention, the scrambling operation encryption method and the block encoding encryption method are combined, the encryption safety is improved, and the computation complexity of the encryption operation is well reduced; different key streams are used in the scrambling operation and the block encoding; compared with a method that a single key stream is used, the image encryption method is advantaged in that the encryption safety is higher.
Owner:CHONGQING UNIV OF EDUCATION
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com