Method for multiplexing residual bandwidth and network equipment
A technology of network equipment and bandwidth, applied in the field of communication, can solve the problems of not supporting flow queue cascading, complexity and cost increase, and achieve the effect of orderly multiplexing, low bandwidth limitation and multiplexing, and flexible cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
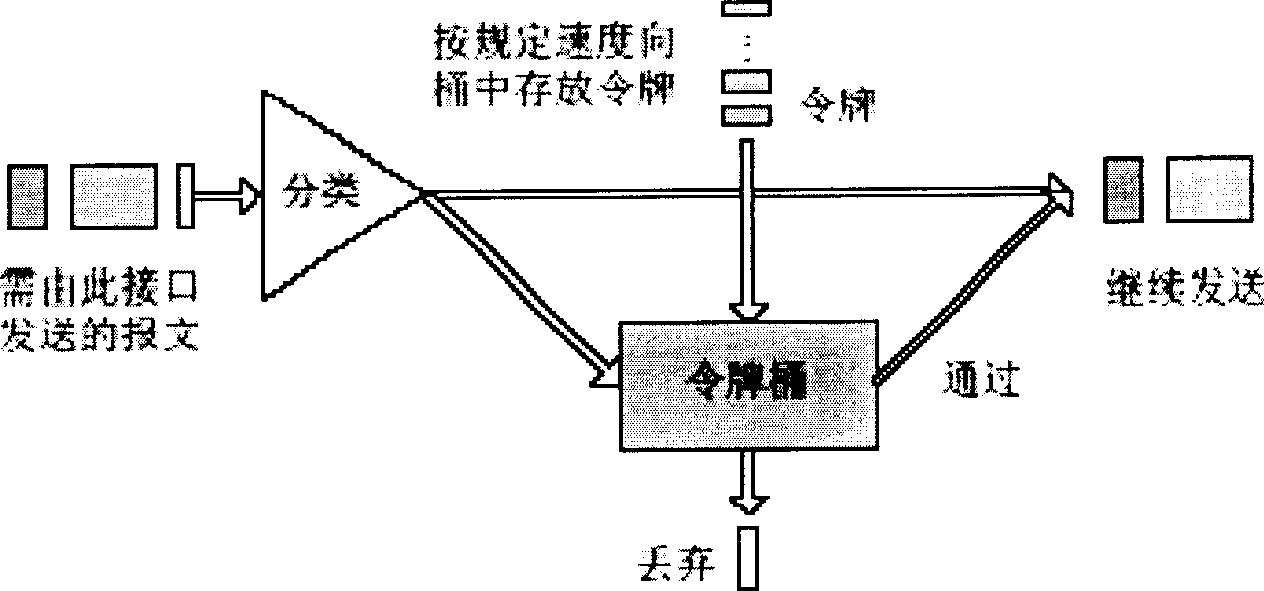
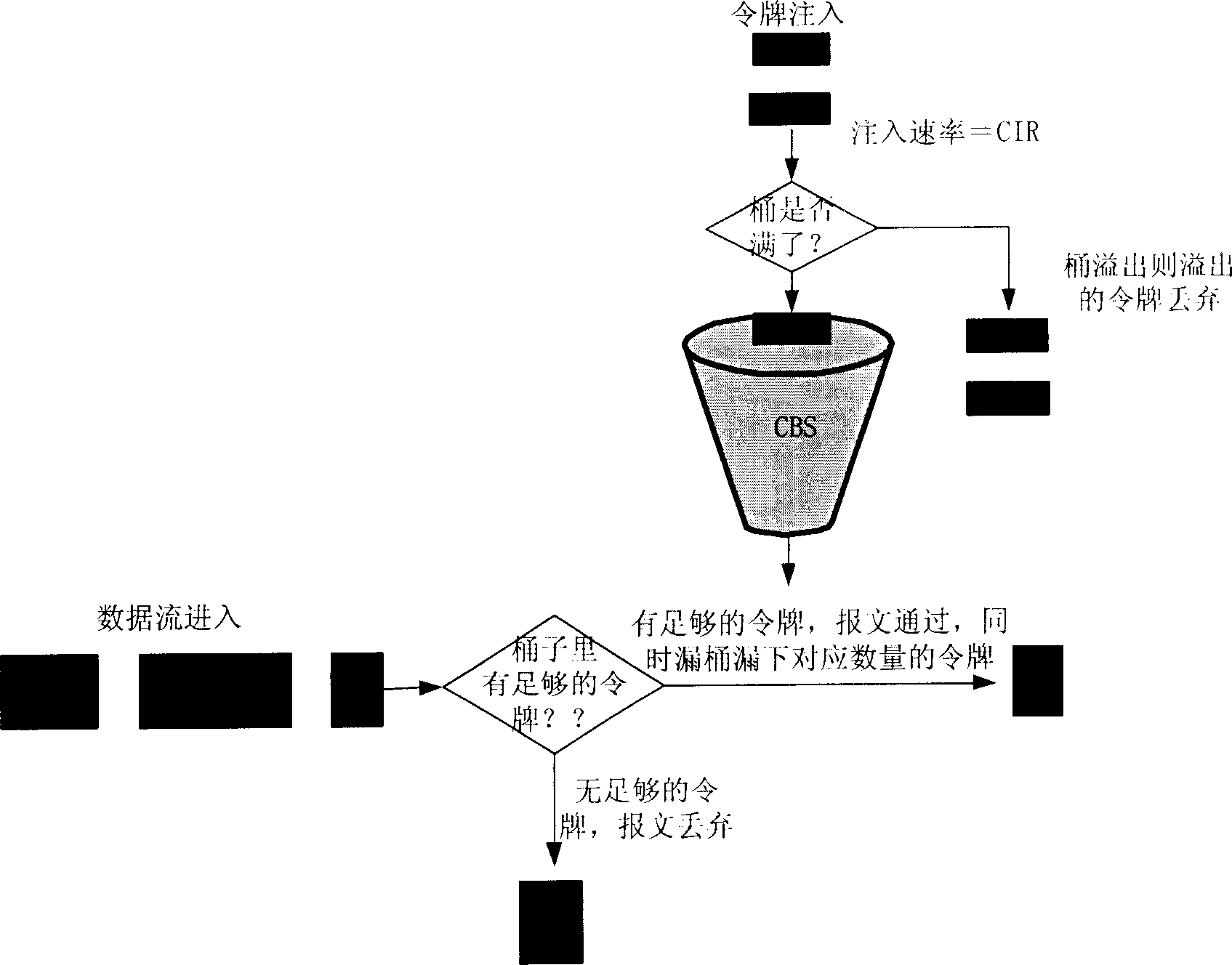
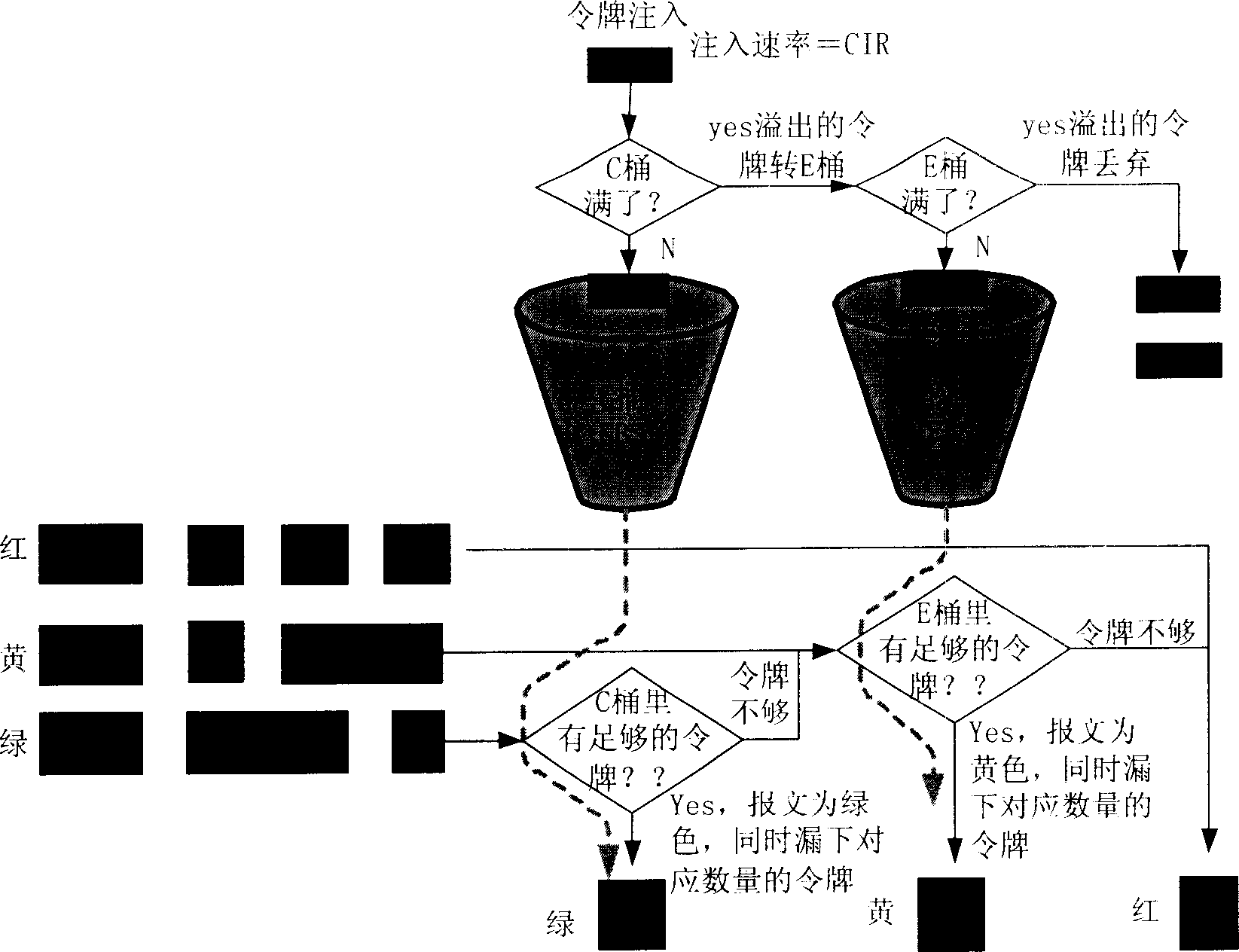
[0040] The present invention distinguishes the priority levels of the traffic of multiple services, and on the basis of limiting the bandwidth respectively, uses the leaky bucket technology to provide the remaining bandwidth to other services exceeding the limited bandwidth in sequence, thereby realizing different Orderly statistical multiplexing between business flows. In the present invention, the remaining bandwidth can be set to be used sequentially by the services of the next level exceeding the limited bandwidth, or set to be used by the services of the previous level exceeding the limited bandwidth in sequence, mainly depending on the agreement signed between the user and the operator. SLAs. In the following embodiments, the technical solution of the present invention is described in detail by taking the example that the remaining bandwidth of high-level services is sequentially used by low-level services exceeding the limited bandwidth.
[0041] Figure 4 Shown is a ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com