Remote de-locking method of information safety device
A technology for information security and remote unlocking, which is applied in the field of remote unlocking of information security device firmware, which can solve problems such as inability to unlock, troublesome information security devices, inability to complete unlocking or restore PIN codes, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
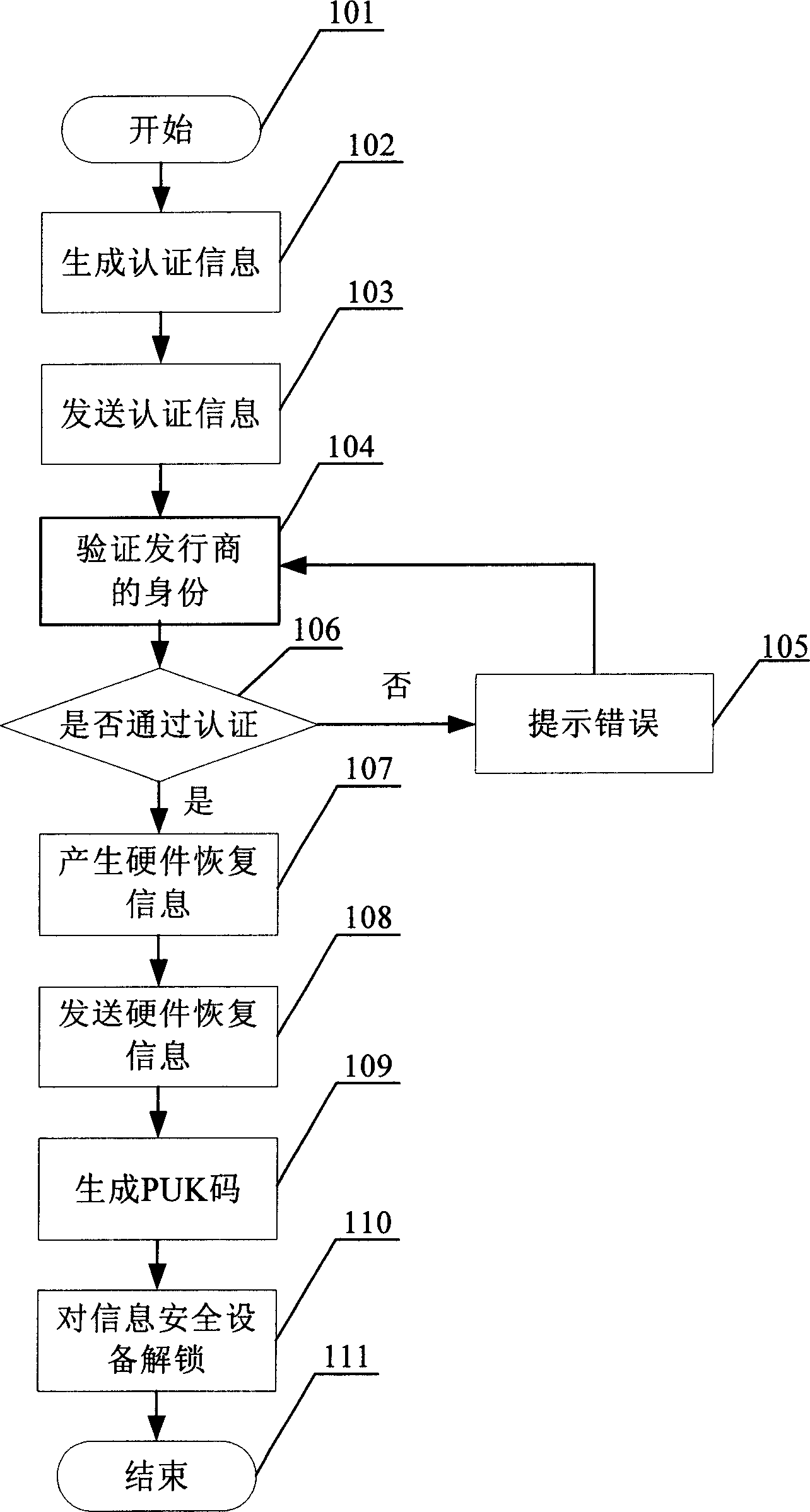
[0031] In this embodiment, the information security equipment holder is an information security equipment issuer, and the hardware recovery information generation device is in the hands of the hardware manufacturer.
[0032] Such as figure 1 As shown, after step 101 starts, in step 102, the issuer of the information security device obtains relevant hardware information from the information security device and generates authentication information. The authentication information includes hardware information and characteristic information of the issuer. is visible. The hardware information can use the serial number of the information security device, which ensures that each information security device corresponds to unique authentication information. The characteristic information of the issuer is the information used by the information security equipment manufacturer to verify the identity of the issuer.
[0033] Step 103, the information security equipment issuer sends the a...
Embodiment 2
[0050] In this embodiment, the holder of the information security device is the user who uses the information security device, and the remote unlocking process is implemented by the user himself through the hardware device and upper-layer software in hand. At this time, the user no longer needs to go to the issuer to unlock, but directly contact the information security equipment manufacturer, provide the authentication information to the information security equipment manufacturer, and obtain the unlocking information provided by the information security equipment manufacturer after passing the identity verification, realizing Unlocking of information security equipment.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com