System and method for electronic transactions
a technology of electronic transactions and system and method, applied in the field of electronic transactions, can solve the problems of not being practical, and the vendor cannot reveal very much from the redemption left, and achieve the effect of simplifying the blinding schem
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
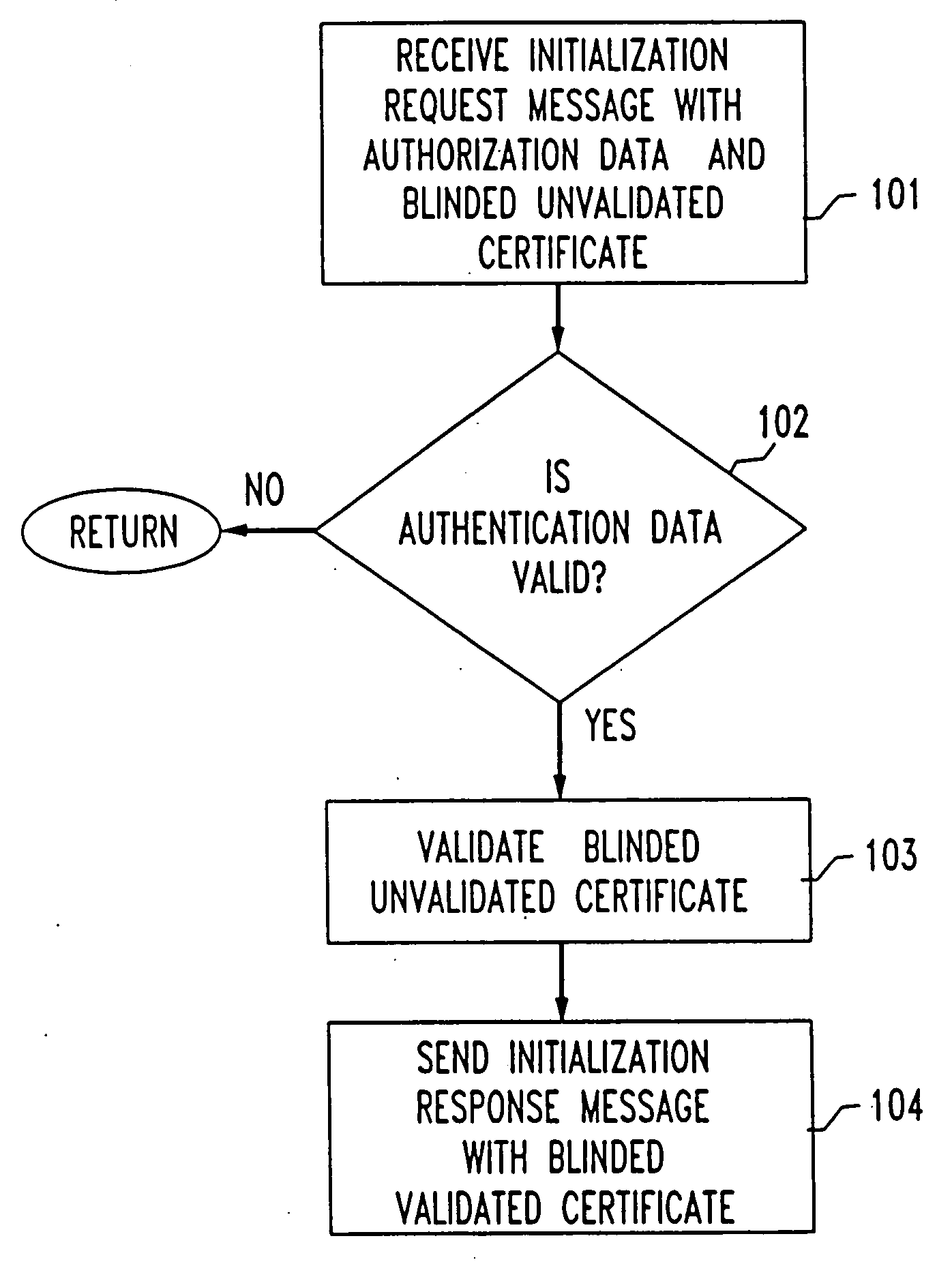
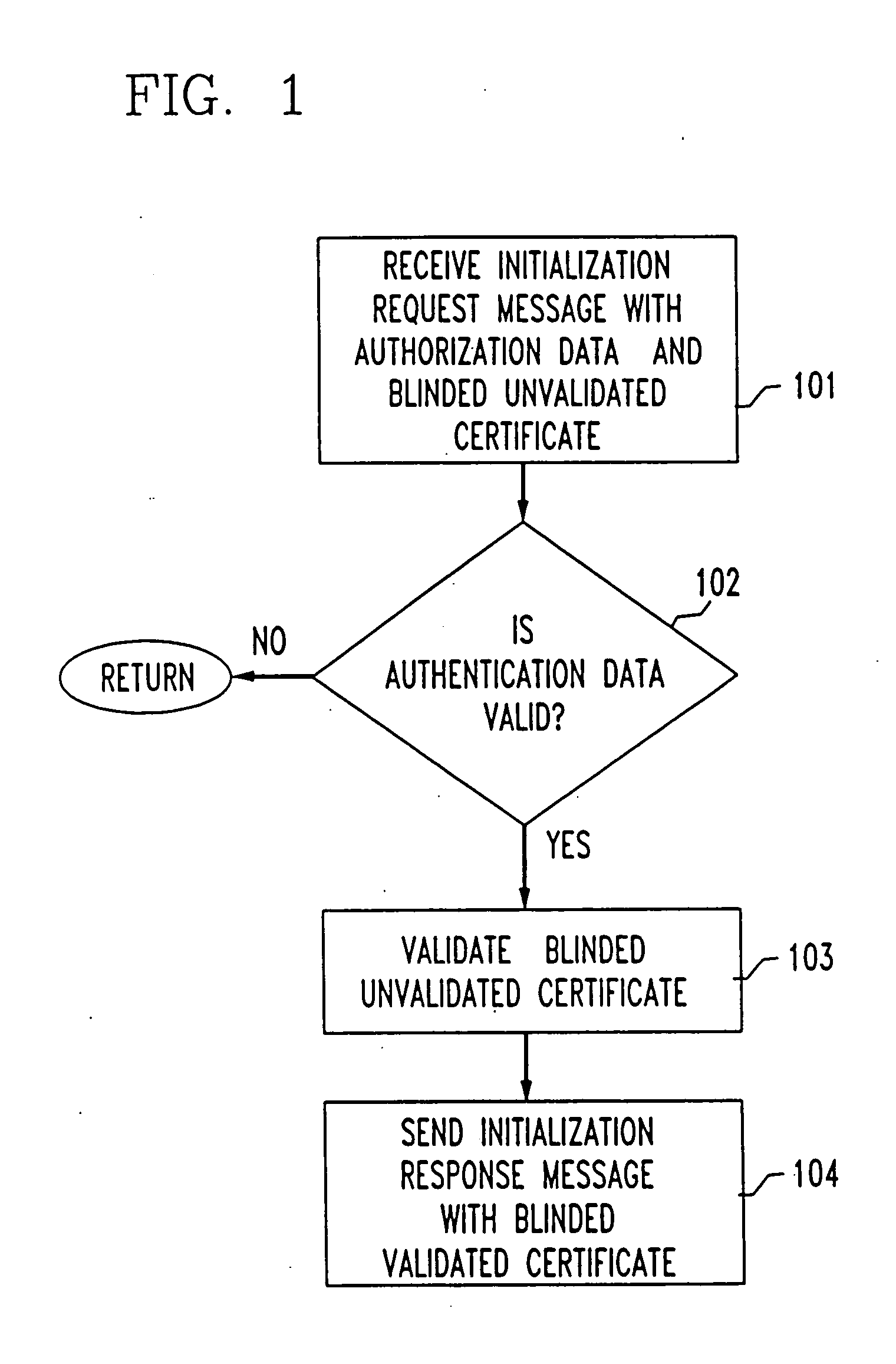
[0023] An embodiment of the registration method in accordance with the present invention is shown in FIG. 1. A registrar receives an initialization request message that atomically binds authorization data with a blinded unvalidated certificate to be validated, step 101. In one embodiment of the present invention, the registrar is a vendor. In another embodiment, the registrar is a third party.
[0024] An example of authorization data is a payment. Another example of authorization data is access permission (e.g., an access code, one-time password, etc.) An example of a blinded unvalidated certificate is a hashed nonce combined with a blinding factor.
[0025] The registrar determines if the authorization data is valid, step 102. If it is determined to be valid, then the blinded unvalidated certificate is validated to obtain a blinded validated certificate, step 103. For example, the registrar signs the blinded unvalidated certificate to validate it. The registrar party then sends an ini...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com