System for using an authorization token to separate authentication and authorization services
a technology of authorization tokens and authorization services, applied in the field of telecommunications, can solve the problems of inability to provide authorization, approach is obviously subject to a number of security concerns, and the revenue margin of access providers tends to decreas
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030]The following discussion is presented to enable a person skilled in the art to make and use the invention. The general principles described herein may be applied to embodiments and applications other than those detailed below without departing from the spirit and scope of the present invention as defined herein. The present invention is not intended to be limited to the embodiments shown, but is to be accorded the widest scope consistent with the principles and features disclosed herein.
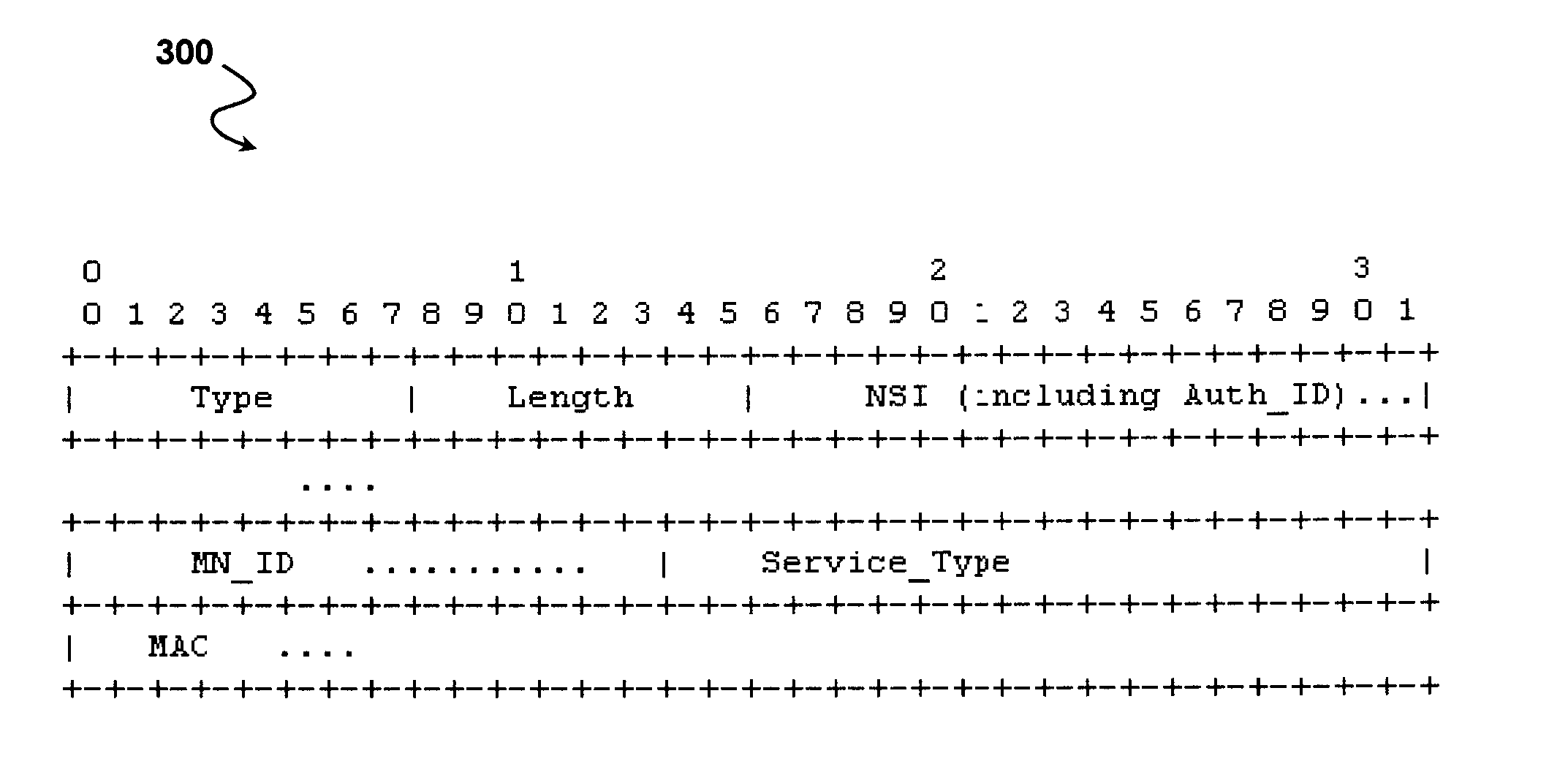
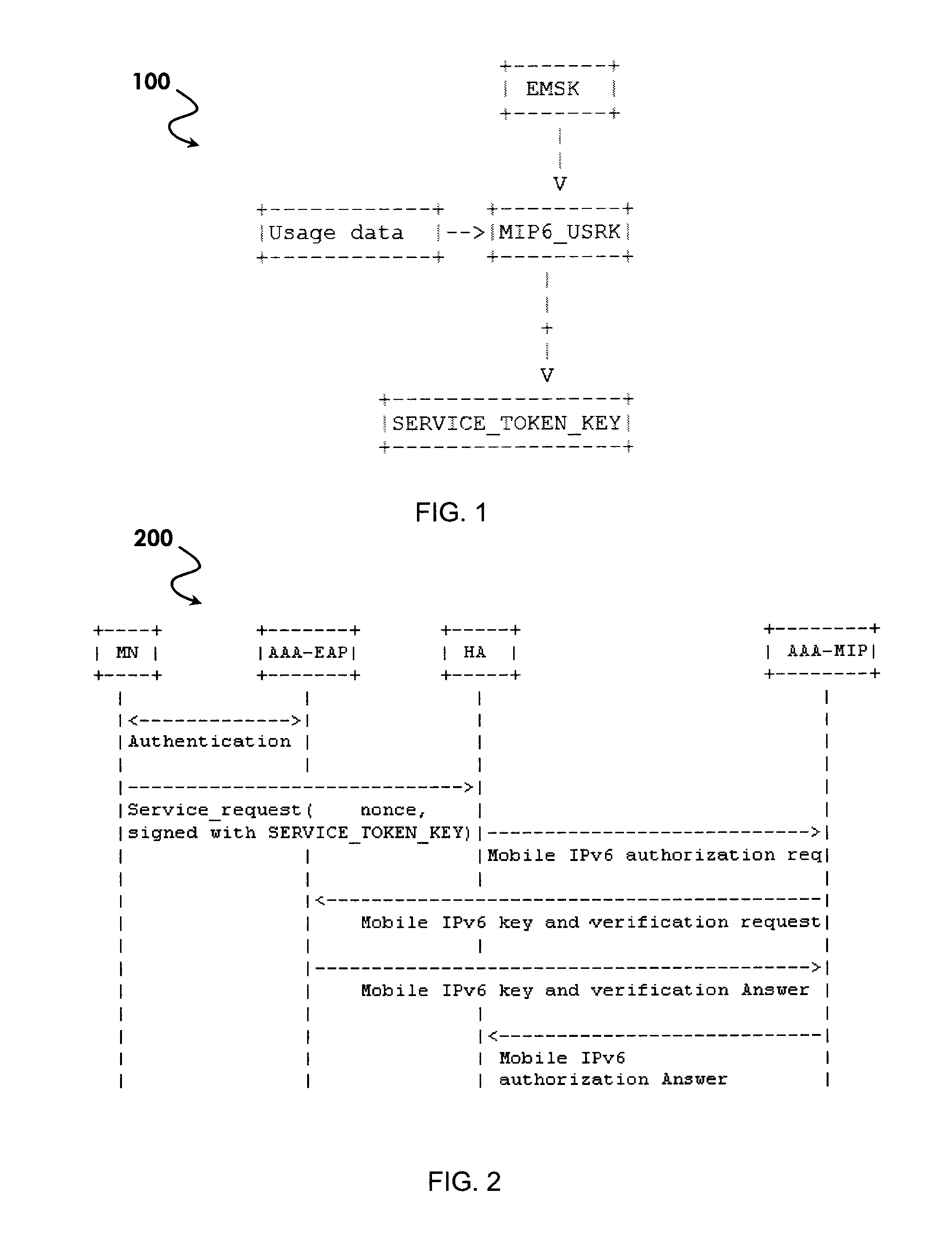
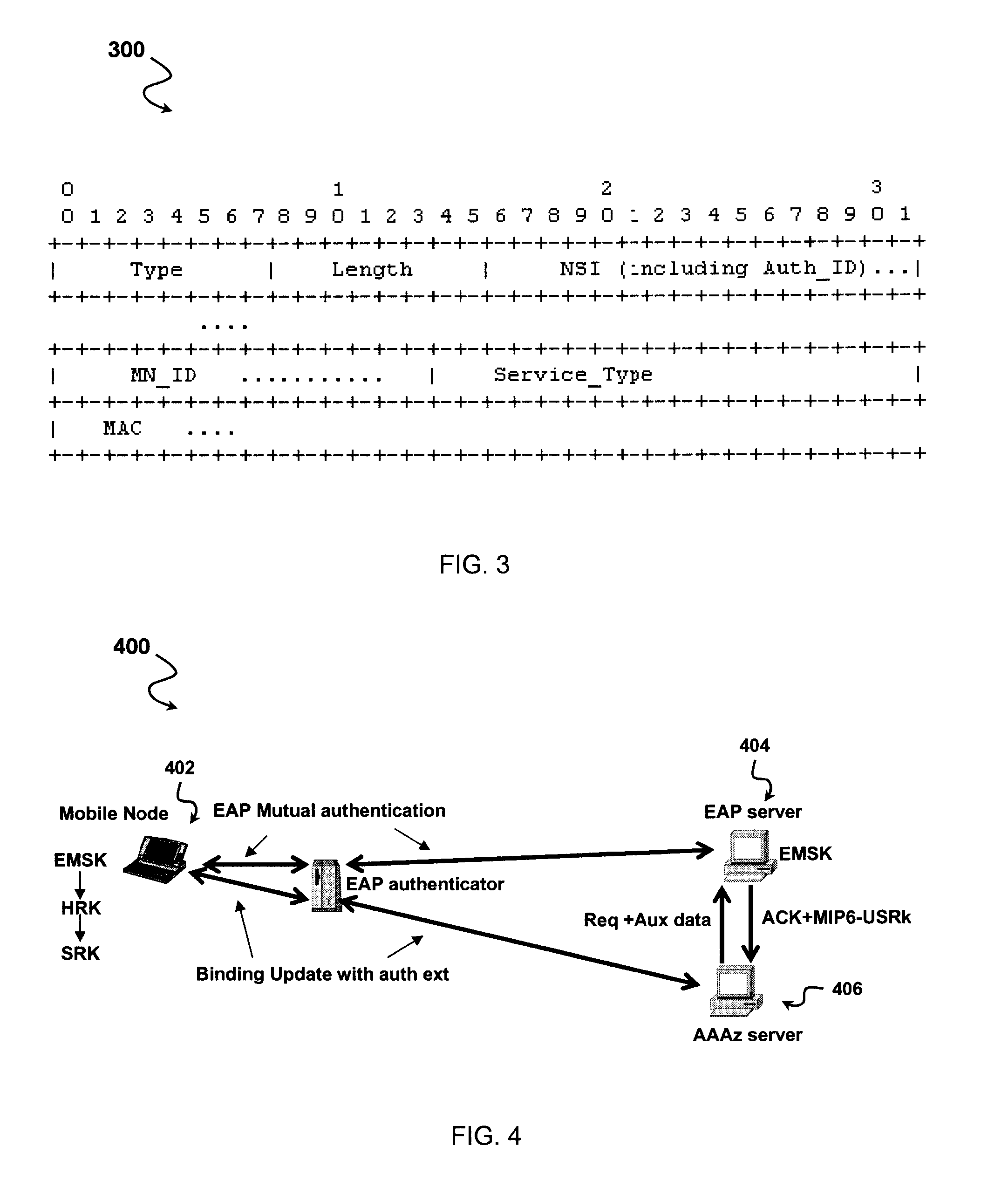
[0031]The present invention provides a system for using an authorization token to separate authentication and authorization services. The system separates the act of authentication from the act of authorization, and performs authentication or authorization through separate Authentication Authorization and Accounting (AAA) servers. A client may first authenticate to an authenticating AAA (AAAN) server, create an authorization token, and then later present the token to a different authorizing AAA...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap