Systems and methods for prevention of peer-to-peer file sharing
a technology of peer-to-peer file sharing and prevention methods, applied in the field of content distribution, can solve the problems of easy unauthorized copying of digital content, large amount of digital content transmission, and costing the legitimate owners of digital content millions or even billions of dollars in lost revenu
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
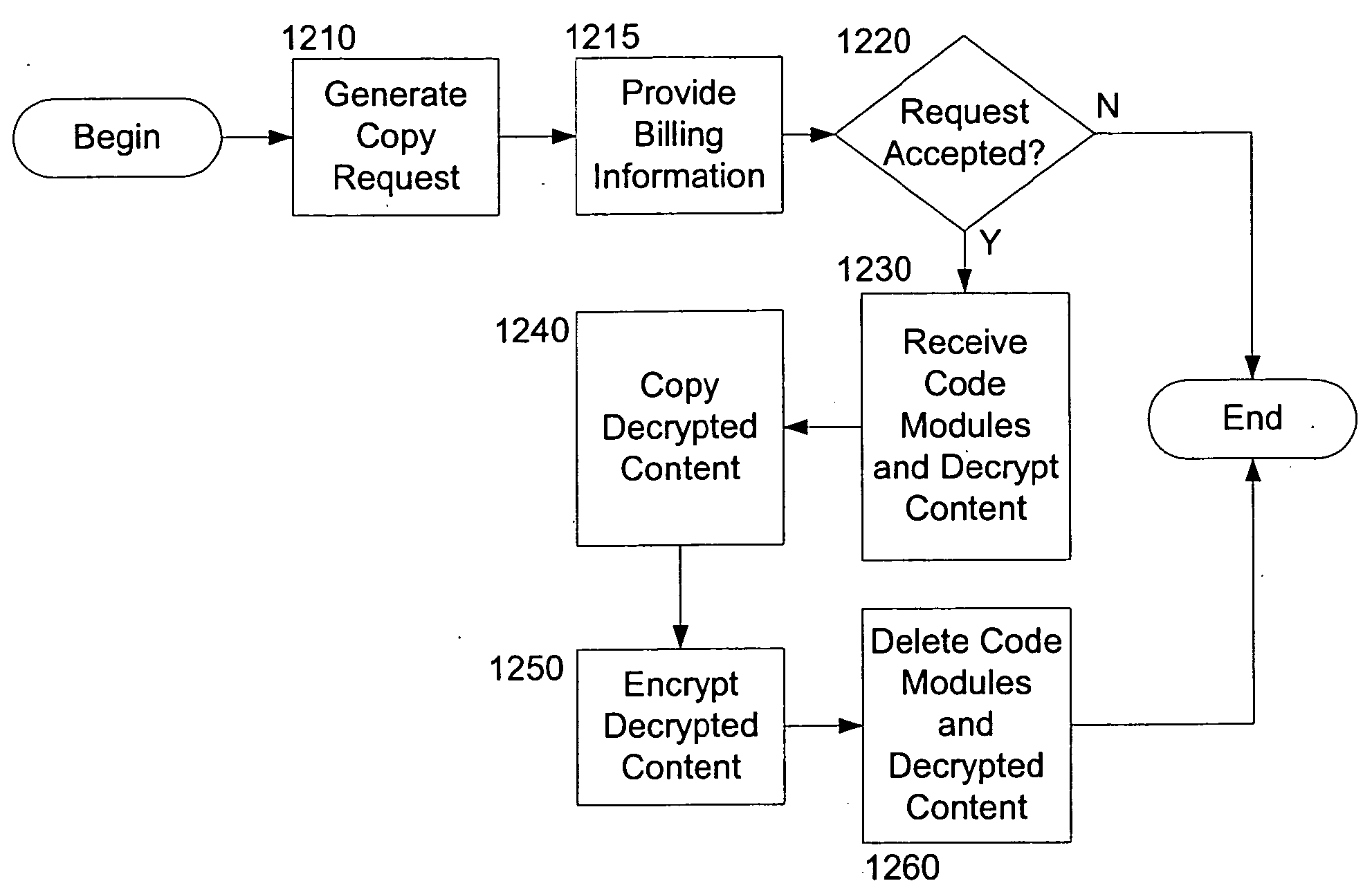
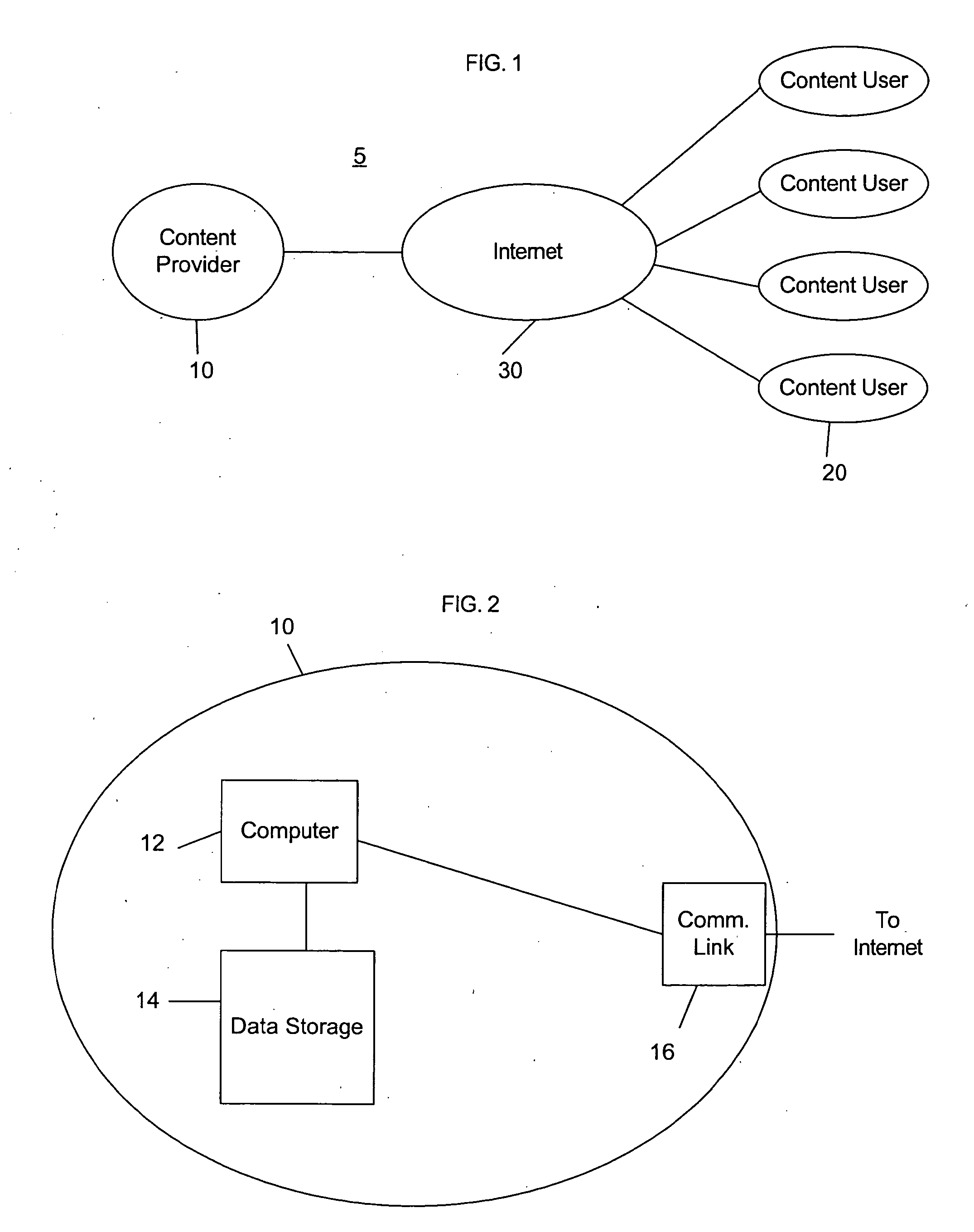
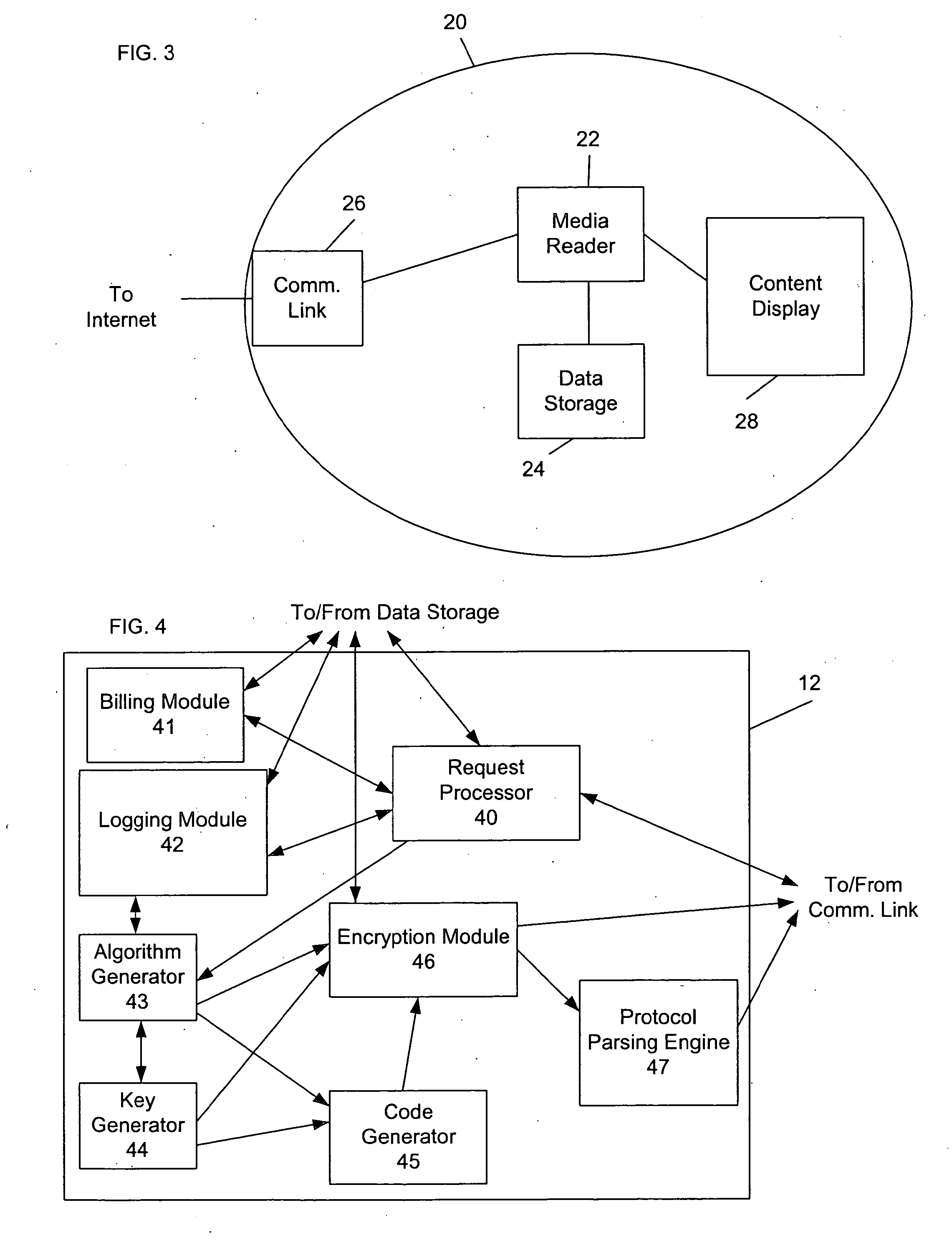
[0031]Turning to FIG. 1, in accordance with an embodiment, a system 5 for securely distributing digital content includes a content provider 10, one or more content users 20, and a network 30. The content provider 10 may be any provider of digital content who wishes to keep that content secure. For example, the content provider 10 may be a record company, a movie distribution company, a computer software company, a video rental company, or the like. The content provider 10 may also be a computer or other similar electronic device or collection of devices operated by any of the above enumerated entities. The content user 20 may be any user of digital content, including both natural persons and electronic devices, either being operated by natural persons or operating independently. The network 30 may be any means of establishing communications between the content provider 10 and the content user 20, for the purpose of transferring content between the content provider 10 and the content...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com