Methods and systems for managing virtual identities in the internet
a virtual identity and internet technology, applied in the field of methods and systems for managing virtual identities in the internet, can solve the problems of system insufficient data to generate indications, harming people's reputation, etc., and achieve the effect of negative icredi
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
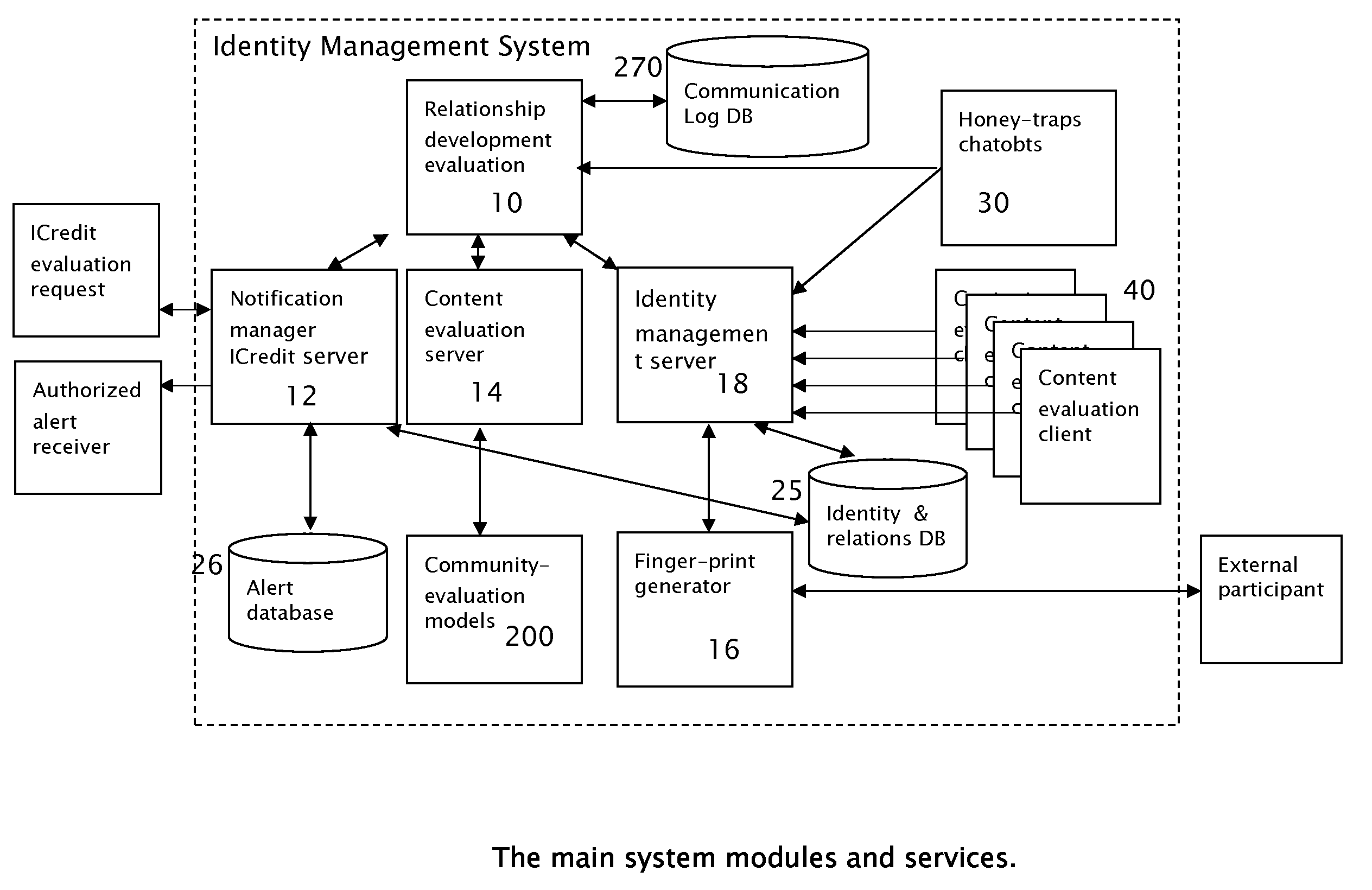
[0060]The present invention relates to methods and systems for managing identities, including anonymous identities within the Internet. The principles and operation for such methods and systems, according to the present invention, may be better understood with reference to the accompanying description and the drawings.
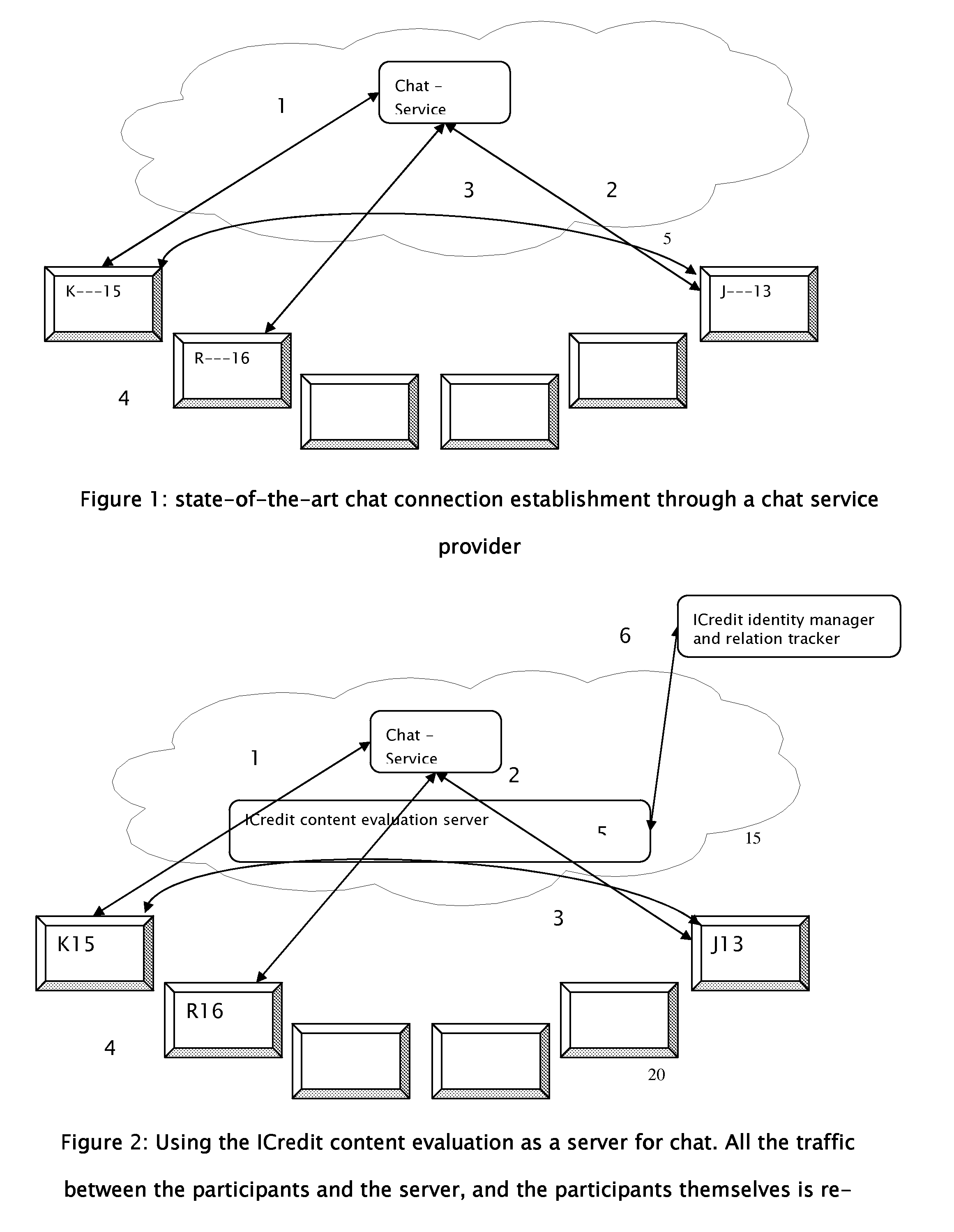
[0061]Referring now to the drawings, FIG. 1 shows the current situation: three chat partners, J13, K15 and R16 access a chat service. Once J13 and K15 are authenticated with the chat service provider by the communication indicated by numbers 1 and 2, J13 and K15 establish a direct chat session marked by the number 3.
[0062]In another possible scenario—R16 may either not be socially related to the other two participants, or they have not authorized him to view their status. In yet another scenario—the chat occurs in a ‘public room’ in which case all the communication can be hosted by the chat provider.
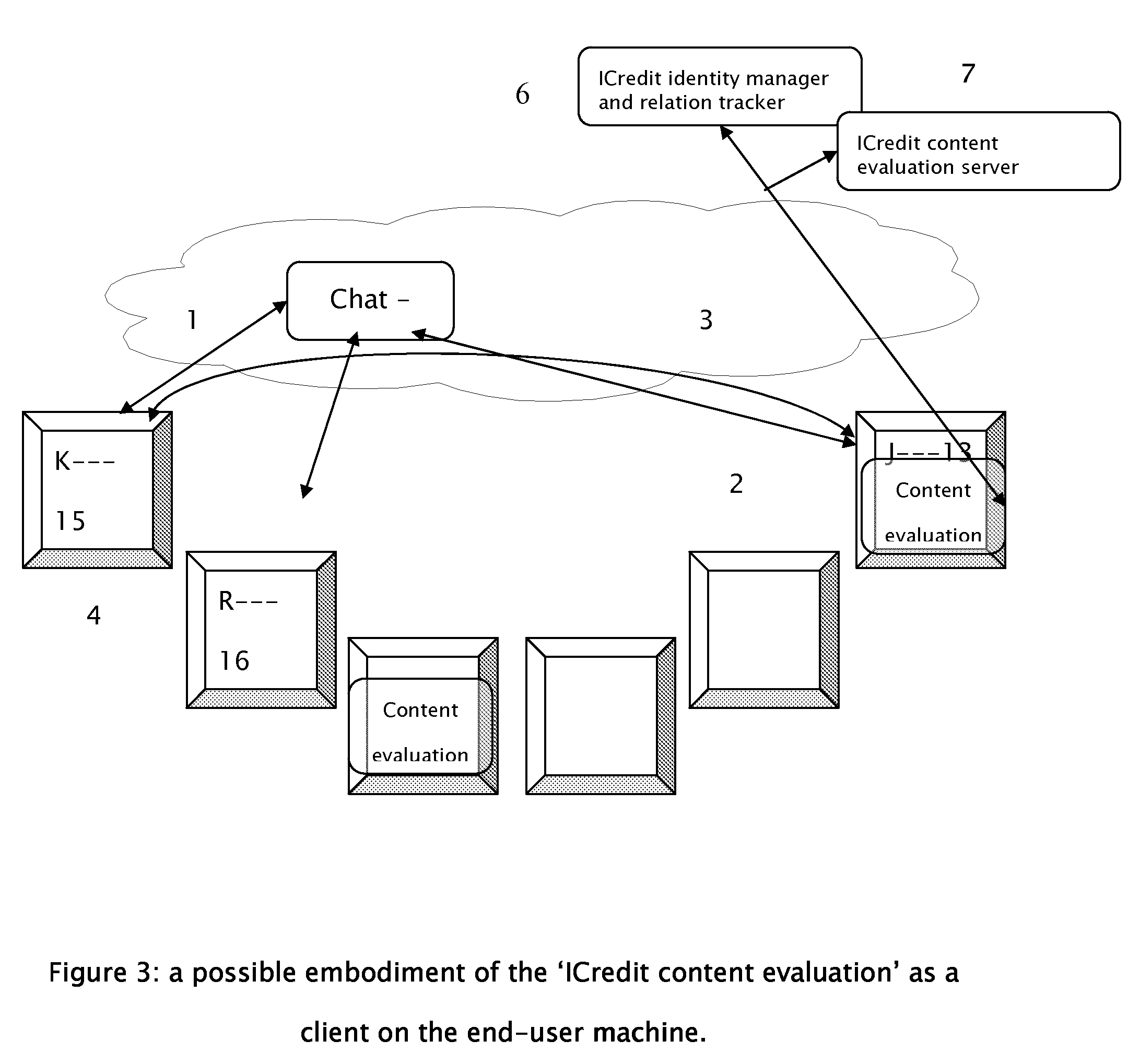
[0063]Using the current invention, as depicted in FIG. 2, all the chat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com