Public Key Infrastructure based on the Public Certificates Ledger
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
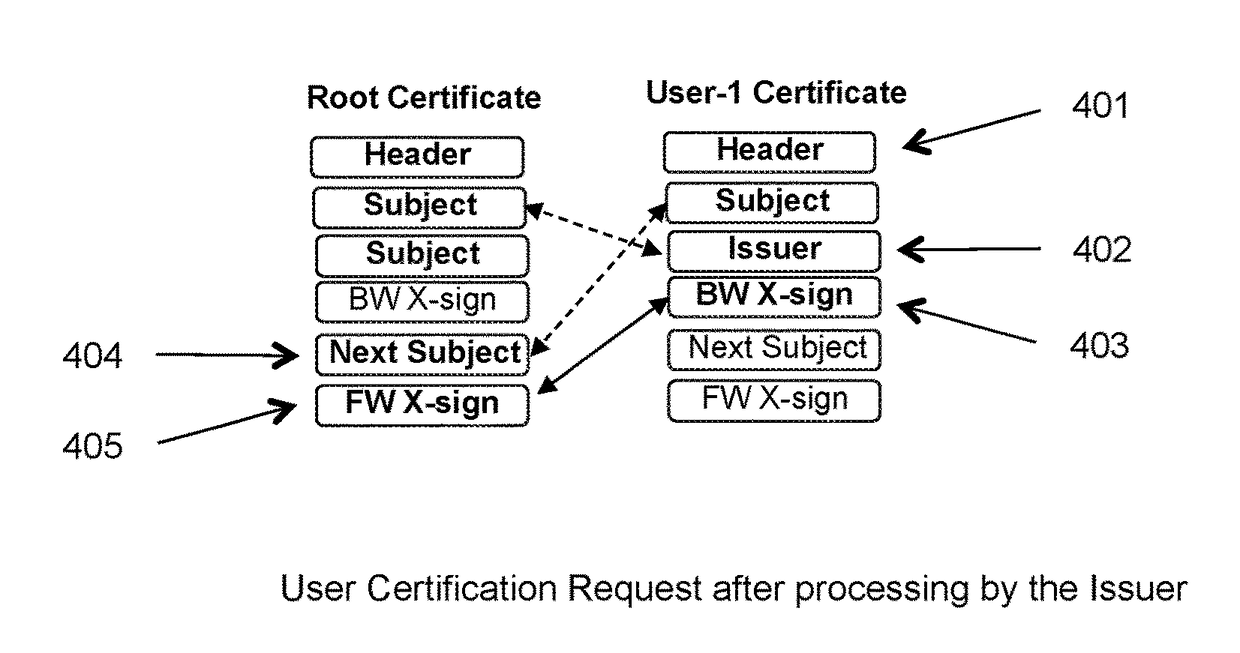
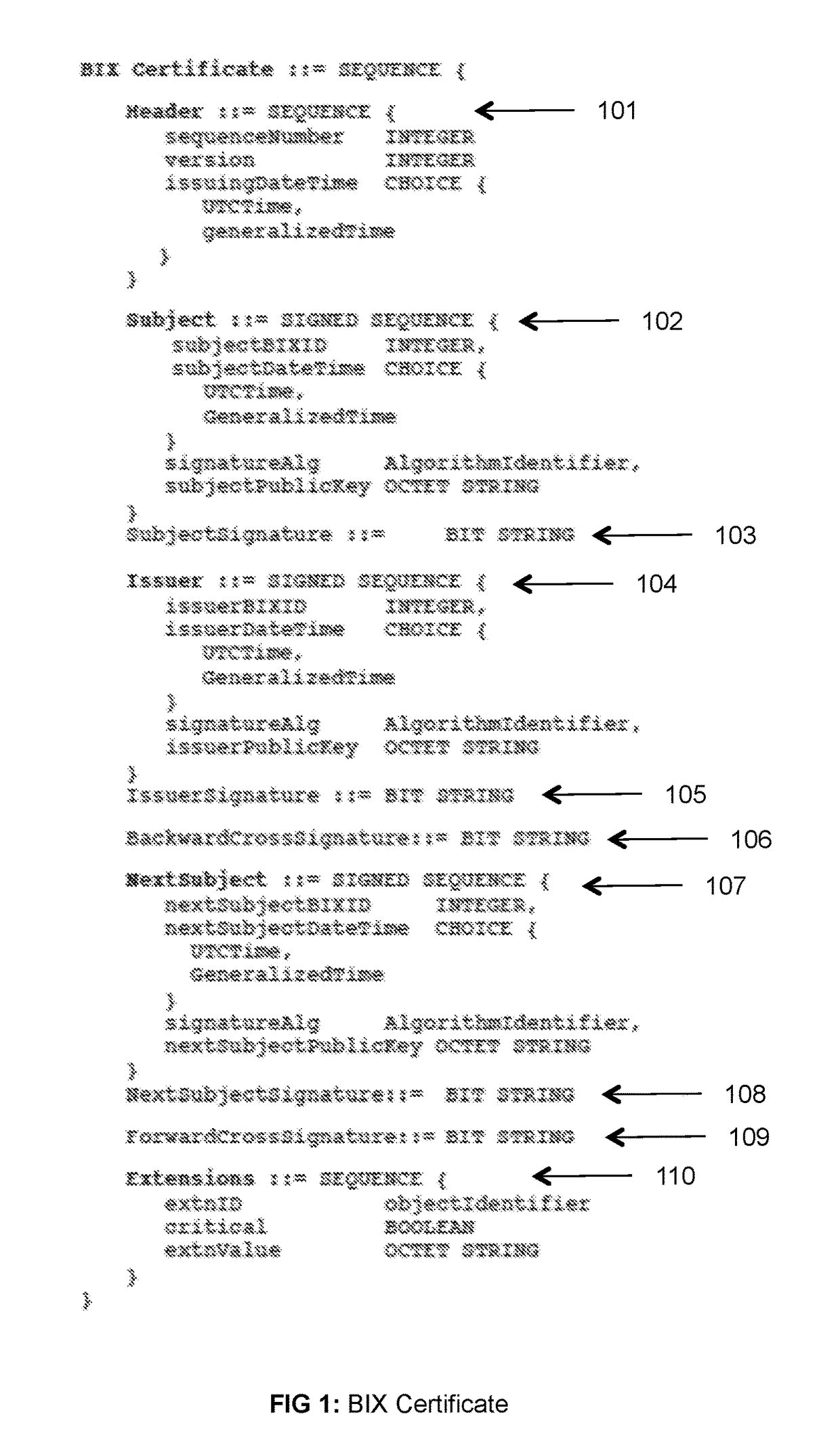
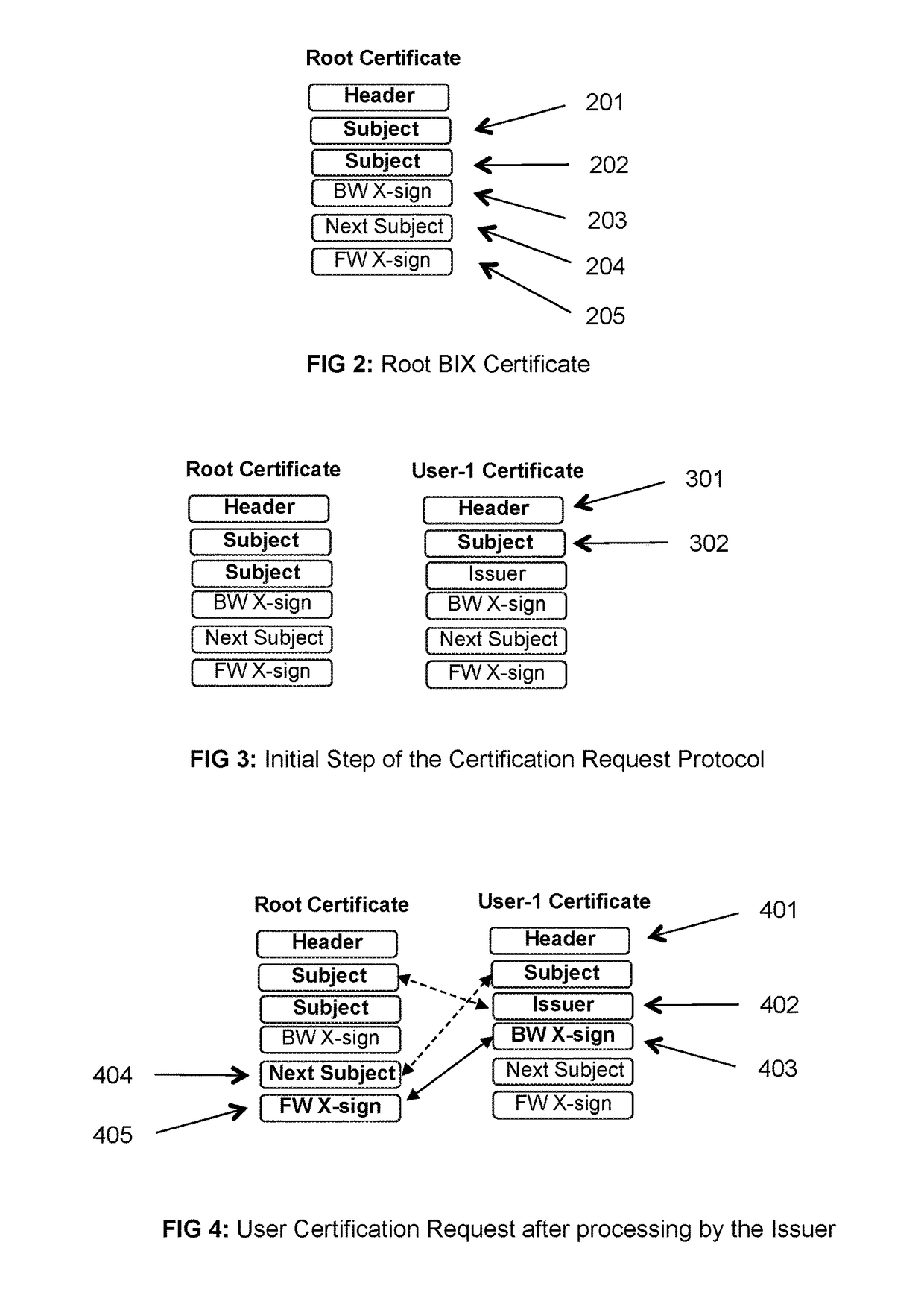
[0064]The Structure and Attributes of BIX Certificates
[0065]BIX certificates are cryptographically encapsulated objects that provide binding between identities of their owners and their public keys, provide cryptographic mechanism (digital signature) to verify that binding and correctness of certificate attribute values and in that way enable distribution of identities and cryptographic keys to transaction partners and verification of the binding and correctness of attribute values by those partners. These features with BIX certificates are achieved with the full anonymity of all BIX system members.
[0066]The structure and attributes of BIX certificates and protocols for their creation, distribution, and verification support the three main purposes of these certificates: (1) reliably distributing and using the correct and legal identities and correct cryptographic keys of BIX system members, (2) verification of user identities and cryptographic keys, and (3) binding of identities to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com