Method for realizing computer software intruder preventing edition based on confidence computation module chip
A technology of trusted computing and user computers, applied in computing, digital data processing parts, instruments, etc., can solve the problem that software products cannot be completely prevented from piracy, and achieve the effect of preventing piracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] Various specific implementations of the software anti-piracy method of the present invention will be described in detail below in conjunction with the accompanying drawings.
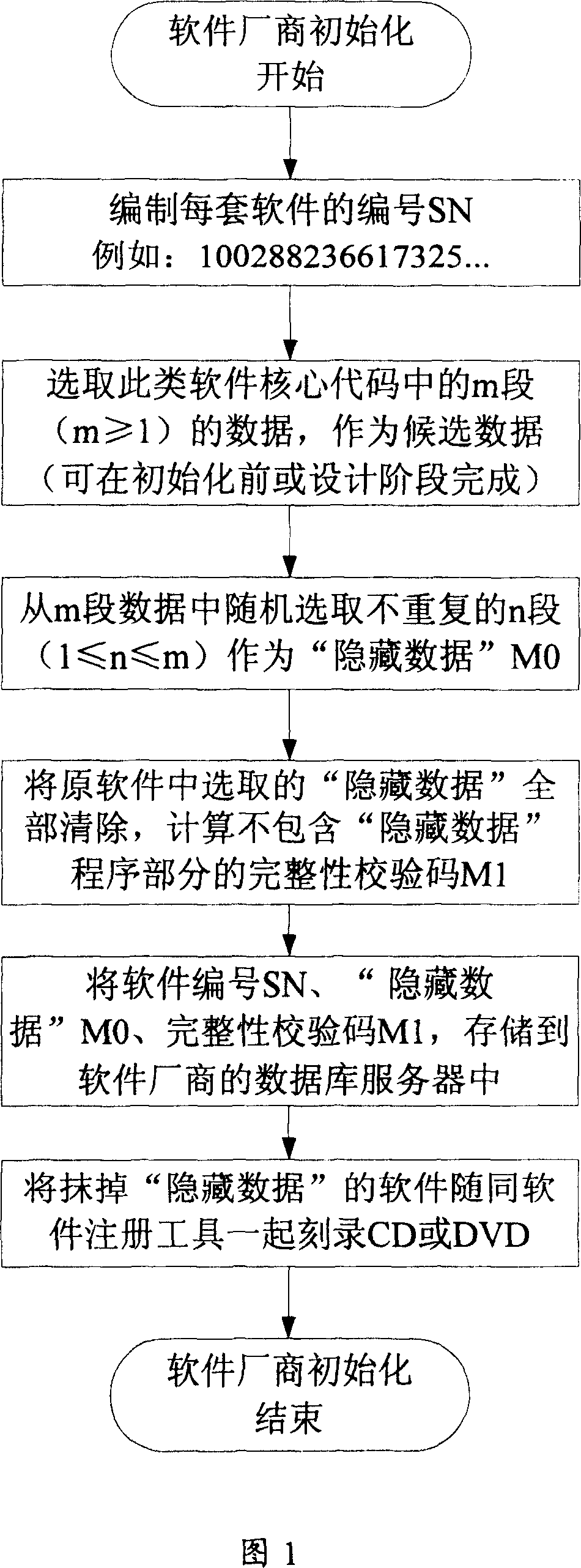
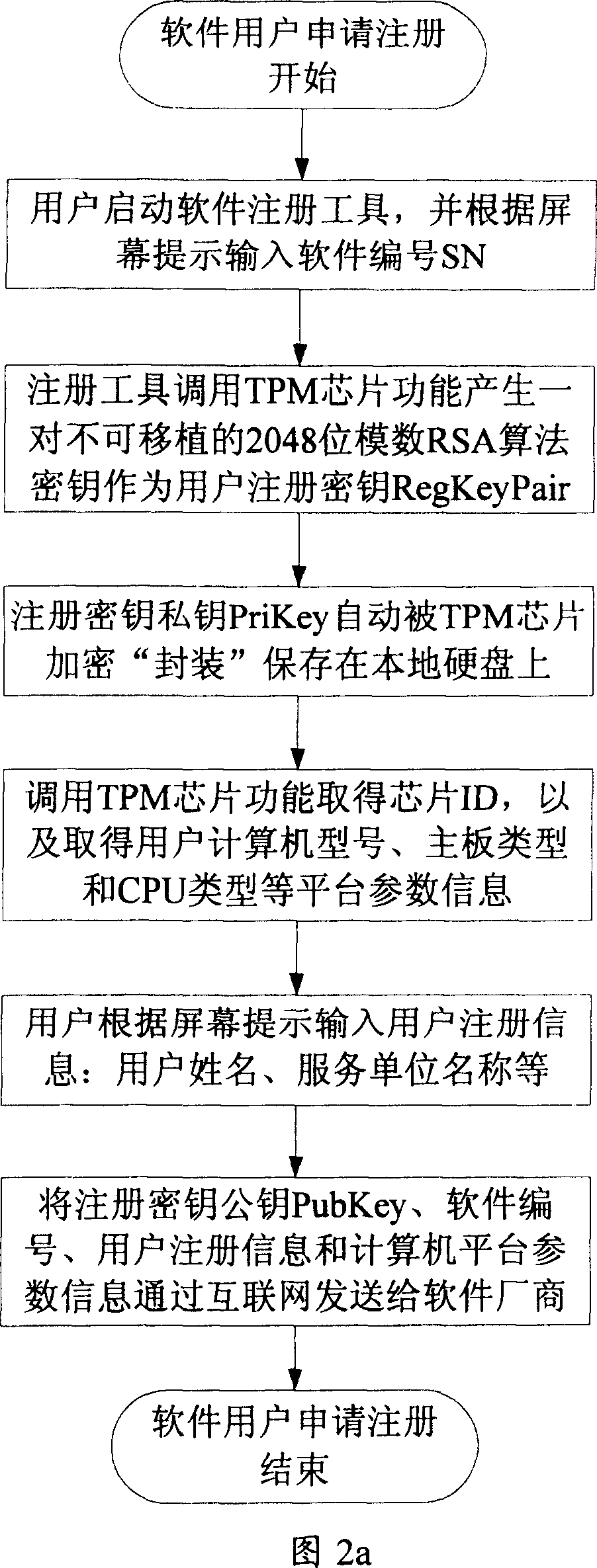
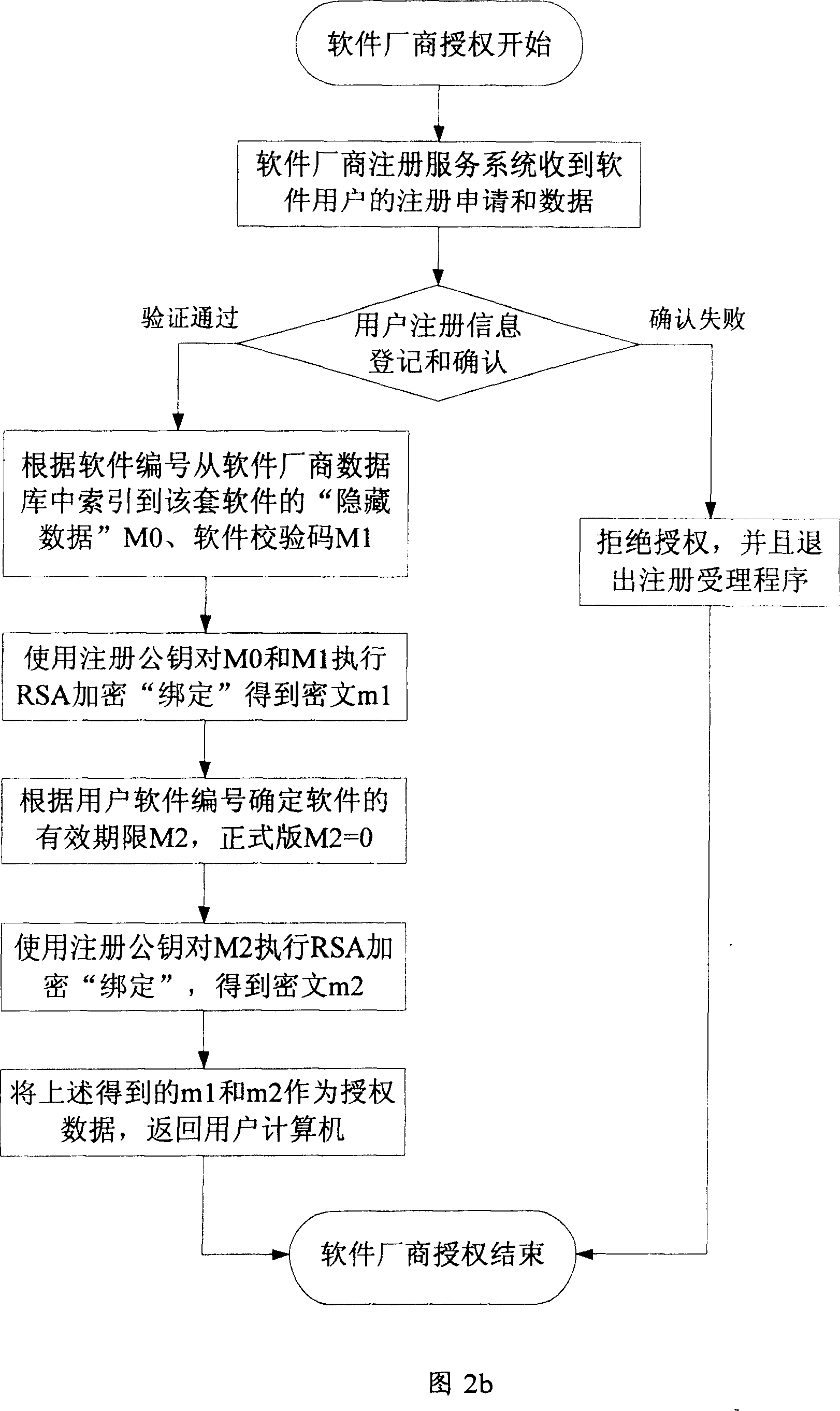
[0037] A method for realizing software anti-piracy based on a trusted computing module chip provided by the present invention is realized by using cryptographic technology and the functions of a trusted computing module chip (hereinafter referred to as TPM chip), which includes the following basic steps: a. Install the trusted computing module chip on the computer of the software user and complete the initialization of the chip; b. The software copyright owner will select the key data in the software product protected by this method for interception to form hidden data, and will not include software products with hidden data Sell or pass on to users who legally obtain the software, and provide a set of software registration tool software at the same time; c. Users need to register with the softwa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com