Random binding software installing method
A technology of bundling software and installation methods, applied to program control devices, digital data processing components, instruments, etc., to achieve the effects of increasing difficulty, reducing risks, and effectively protecting copyrights
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
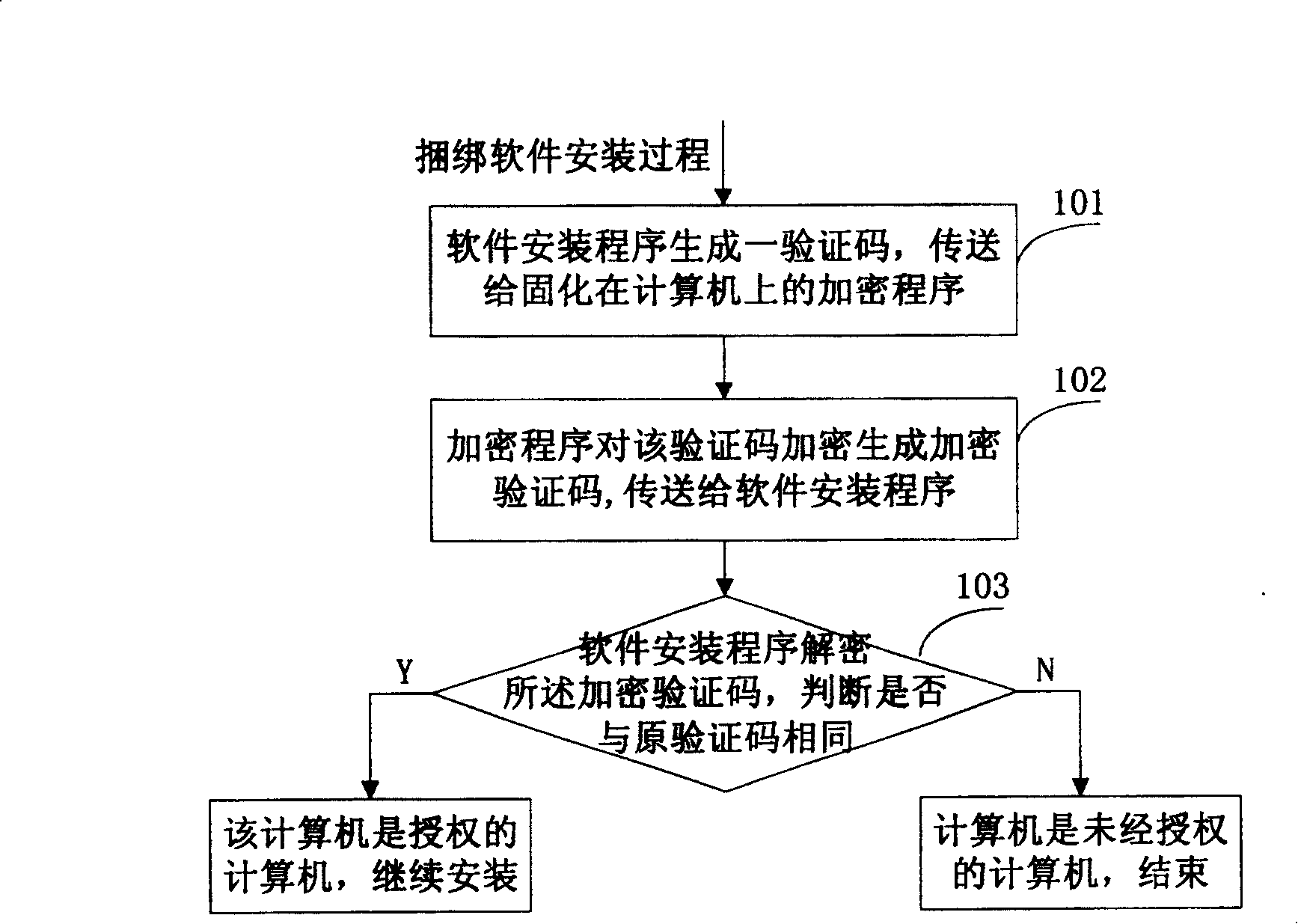
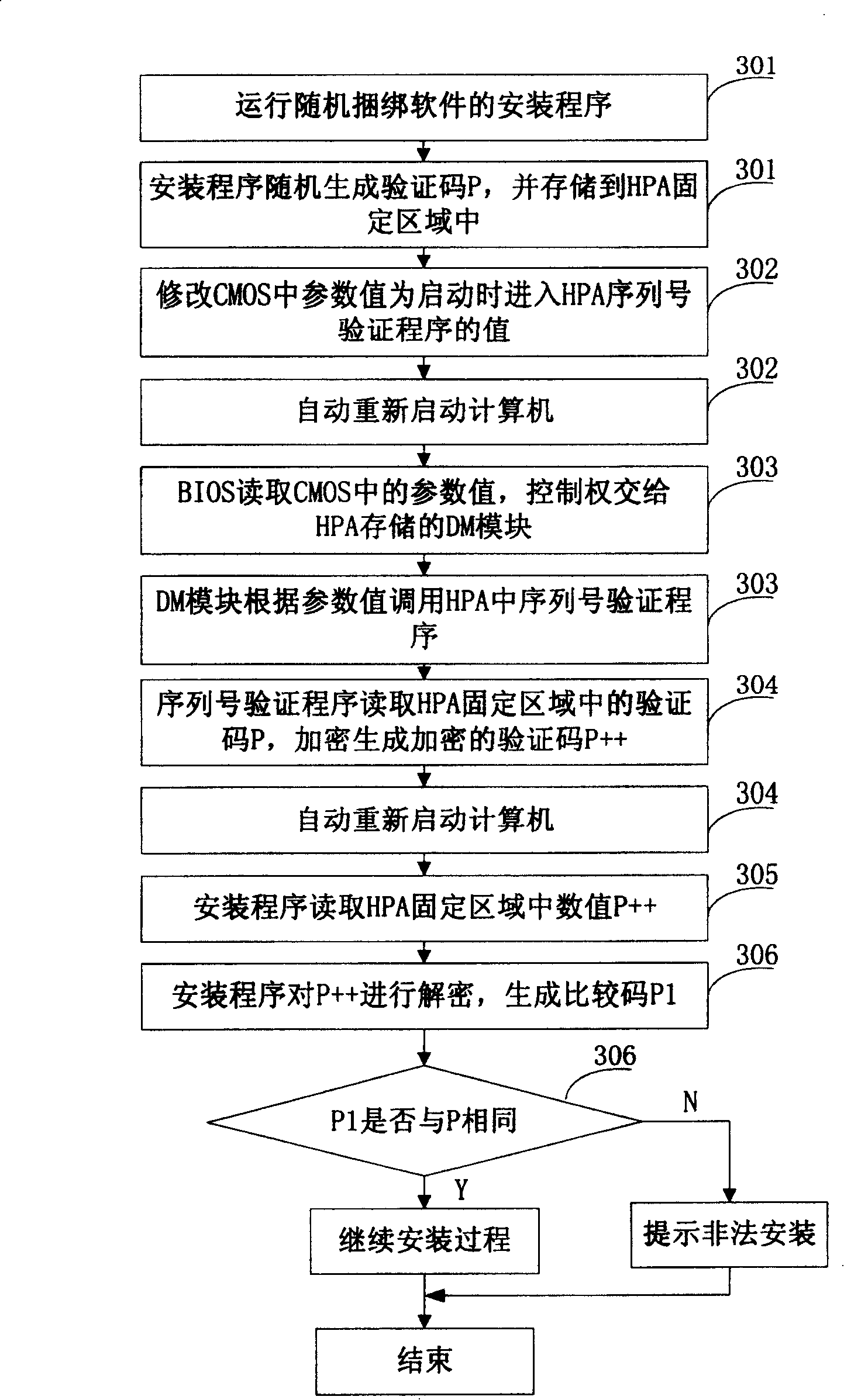
[0030] The invention discloses a method for installing random bundled software by using an embedded system and cryptographic technology. The method can identify whether a computer is a legally authorized computer during the installation process of the random bundled software.
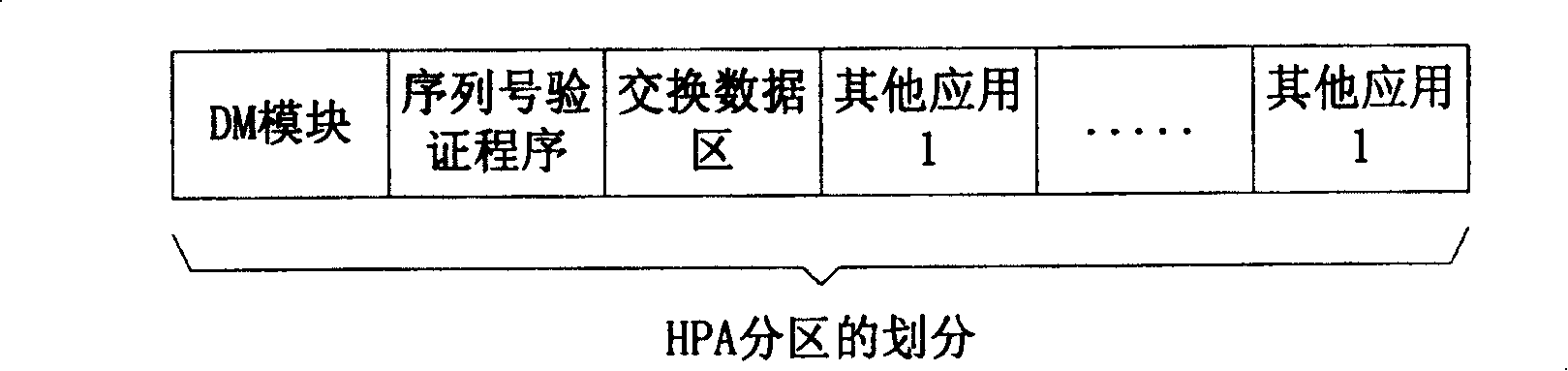
[0031] The present invention solidifies an encryption program on the computer, and this encryption program can be located on the device integrated with the computer, for example, can be located on a storage device (such as BIOS) on the computer motherboard, or be located on the hard disk etc.; The corresponding decryption program is embedded in the bundled software. The encryption and decryption algorithms are provided by the random bundled software provider. see figure 1 As shown in the flow chart, the random bundled software installation method of the present invention includes the following steps:
[0032] Step 101: Generate a verification code during the running of the random bundled software inst...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com