Method for implementing network access authentication
A network access and network technology, applied in the field of network access authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The present invention will be described in further detail below in conjunction with the accompanying drawings.
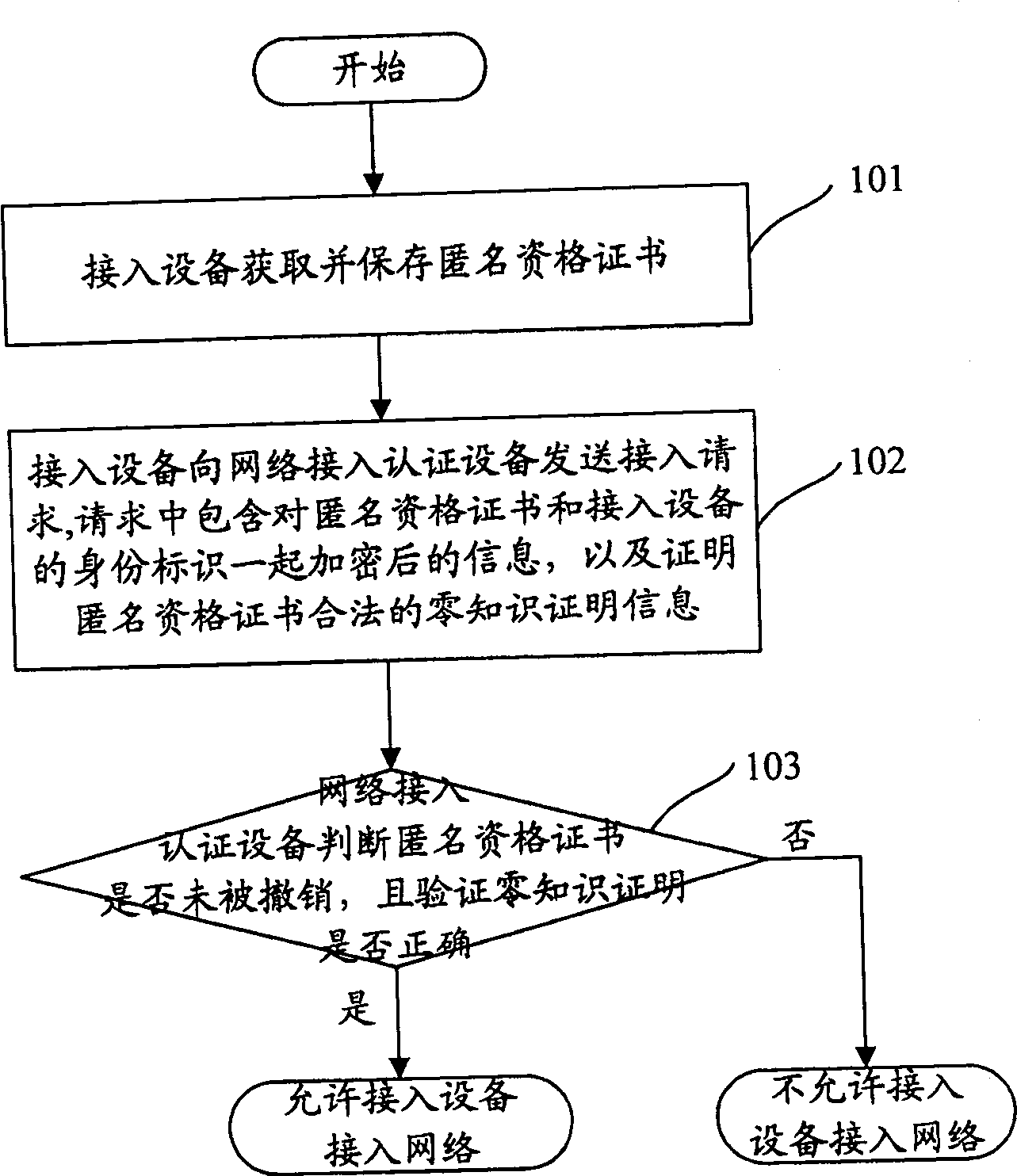
[0033] There are certificate issuing entities, certificate revocation entities, access devices and network access authentication devices in the network. Among them, the certificate issuing entity has an issuing module responsible for issuing anonymous qualification certificates to legal access devices; the certificate revocation entity has a revocation module for revoking the legal qualification of access devices; A certification module used to prove the legality of the self-identity; a verification module used to verify whether the access device is legal exists in the network access authentication device used to verify the legality of the access device. The above-mentioned certificate issuing entity and certificate revocation entity may be the same physical entity or different physical entities.
[0034] figure 1 Shown is a schematic flow chart of implemen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com