Relay device and relay processing method
A technology of a processing device and an information processing device, which is applied in the field of relay processing devices, and can solve problems such as loopholes, inability to apply communication content inspection and access control, and inability to check communication content, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 Embodiment approach
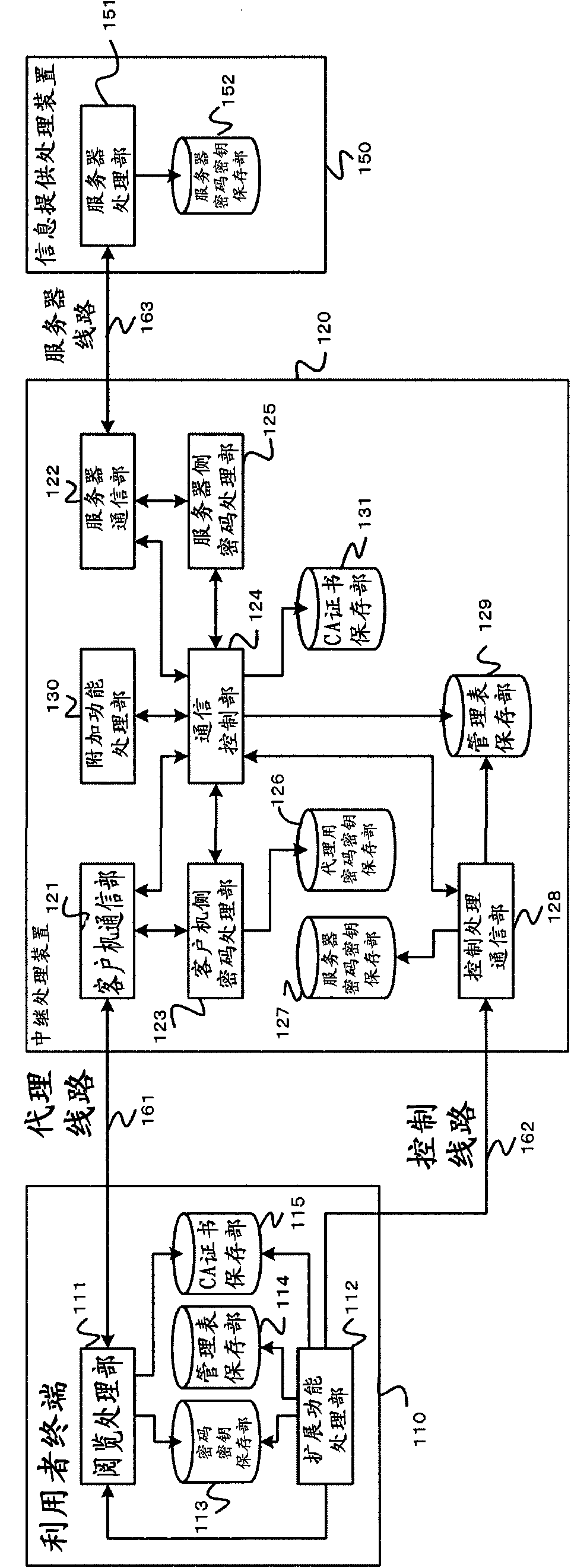
[0053] (system structure and management table)
[0054] figure 1 It is a figure which shows the structure of the relay processing system in embodiment of this invention.
[0055] In addition, in figure 1 The configuration of various terminals and various devices connected to the network is an example, and of course there are various configuration examples depending on the use and purpose.
[0056] The relay processing system includes a user terminal 110 , a relay processing device 120 , and an information provision processing device 150 . The user terminal 110 and the relay processing device 120, and the relay processing device 120 and the information provision processing device 150 are communicably connected to each other via a network.
[0057] The user terminal 110 is an application example of the client terminal of the present invention. In addition, the relay processing device 120 is an application example of the relay processing device of the present invention. In a...
no. 2 Embodiment approach
[0471] In the first embodiment, in HTTPS (HTTP over SSL (including TLS)) communication, the user terminal 110 is connected to the relay processing device 120 (proxy server) by the CONNECT method, and the information provision processing device 150 ( A structure in which the communication of a Web server) is tunnelled, a method of decrypting encrypted communication information to create additional functions, and a method of effectively functioning entity authentication even in this case are described. However, since the relay protocol realized based on the CONNECT method is not limited to a general-purpose transmission communication tunneling method of HTTP communication, even if for example using IMAP overSSL (including TLS), POP3over SSL (including TLS), and SMTP over SSL (including TLS) and other SSL (including TLS) communication protocols can also be applied with the same structure.
[0472] For example, when applied to IMAP over SSL (including TLS), the browsing processing...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com