Method and computer system for coding a message
A message coding and computer technology, applied in the direction of secure communication device, usage of multiple keys/algorithms, digital transmission system, etc., can solve the problems that CMIP cannot consider the failure of production, etc., and achieve fast executable and improved security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
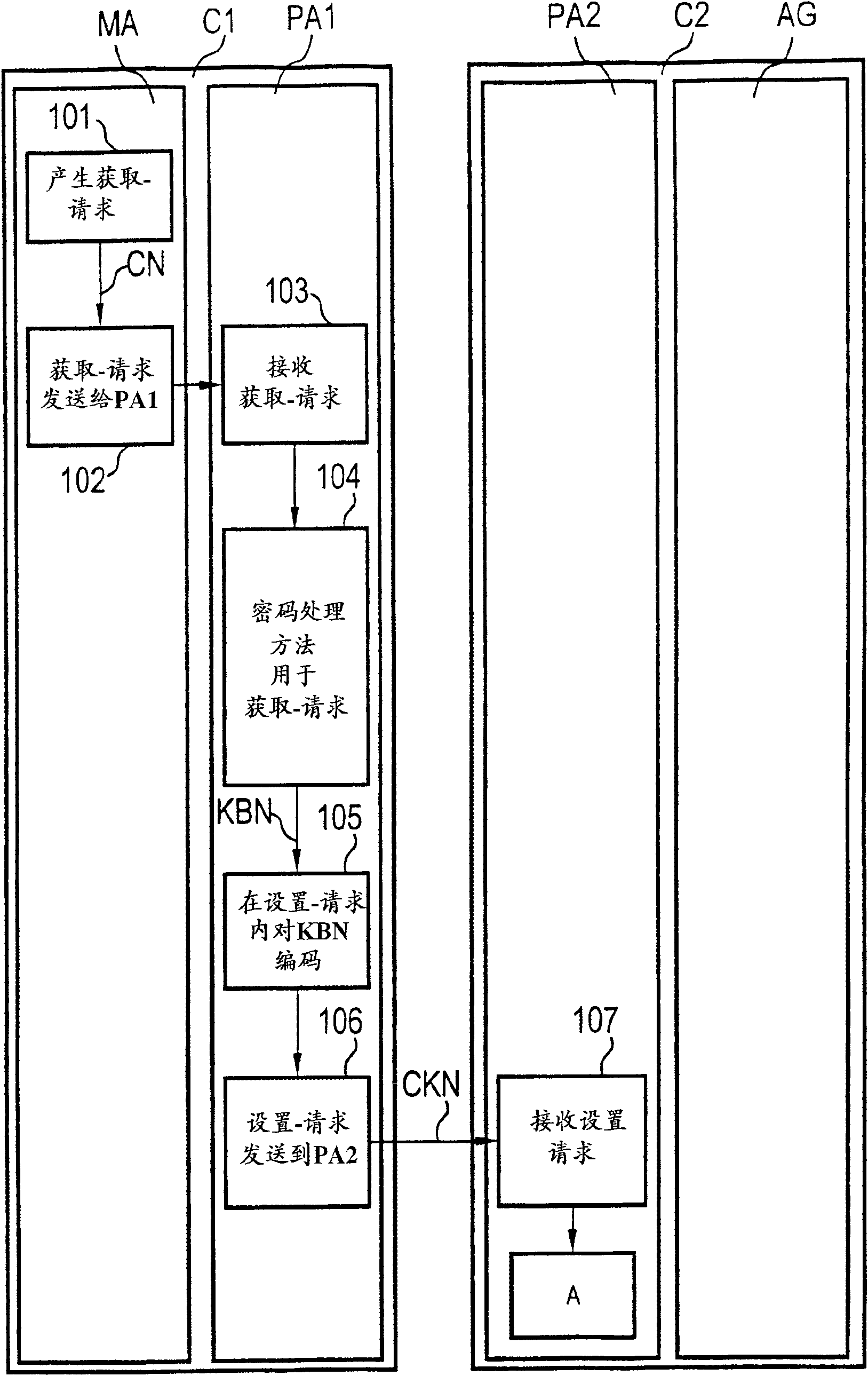
[0067] get-request
[0068] Fig. 1 schematically depicts a first computer unit C1 and a second computer unit C2. The first computer unit C1 has an SNMPv1 management operator MA and a first agent agent PA1.
[0069] The second computer unit C2 has an SNMPv1 agent AQ and a second agent agent PA2 on the side of the second computer unit C2.
[0070] In a first step 101, an acquisition request is formed in the first computer unit C1. Formation of a get request is understood to mean the encoding of an encoded digital message into an encoded message using the encoding format of the SNMPv1 network protocol. This takes place in the first device 101 of the first computer unit C1 for encoding digital messages using the Internet protocol encoding format.
[0071] In a second step 102, a get-request, ie a coded message CN, is sent from the first device N1 to the first agent-intermediary PA1 on the part of the first computer C1.
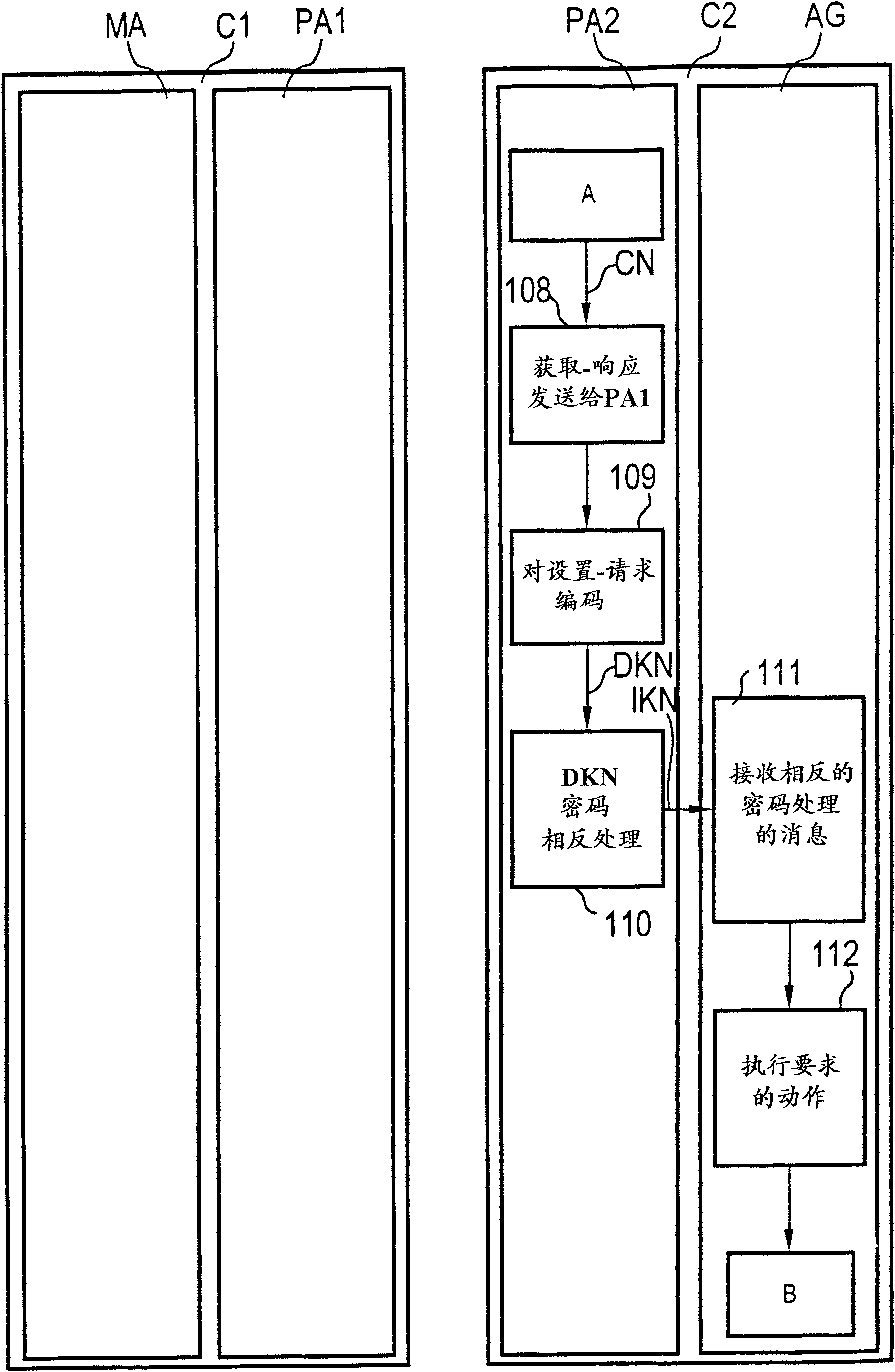
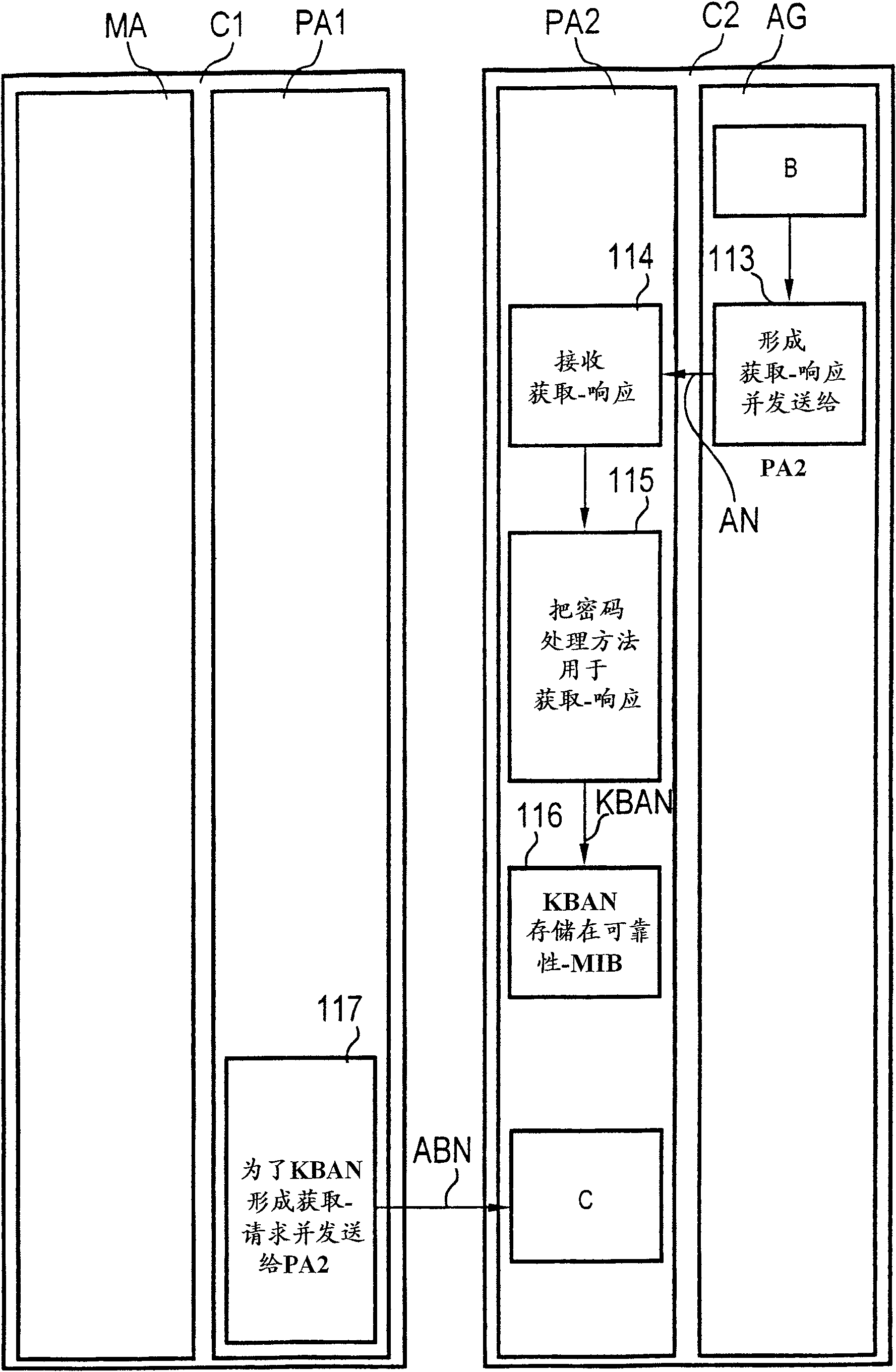
[0072] In a third step 103 the encoded message CN is rec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com