Method for protecting 1+1 single sub-network connection and communication network using the method
一种通信网络、单向的技术,应用在通信网络领域,达到增强可靠性的效果
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
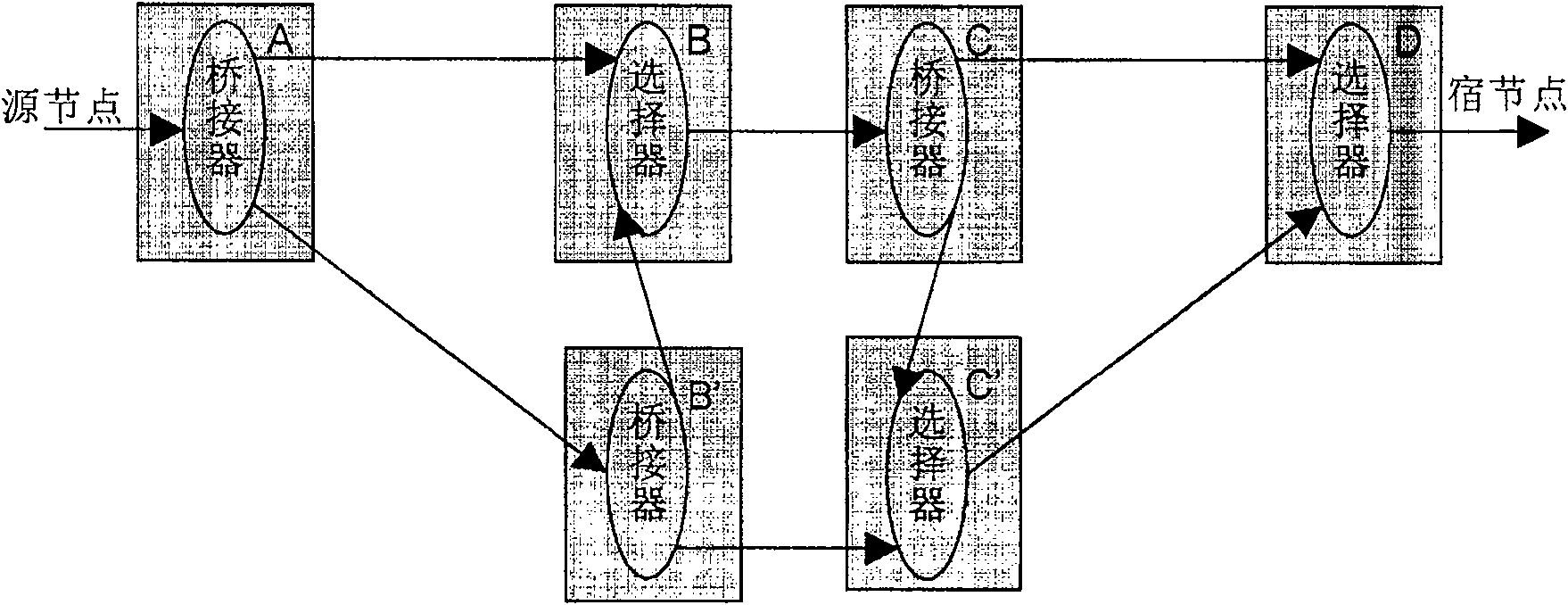
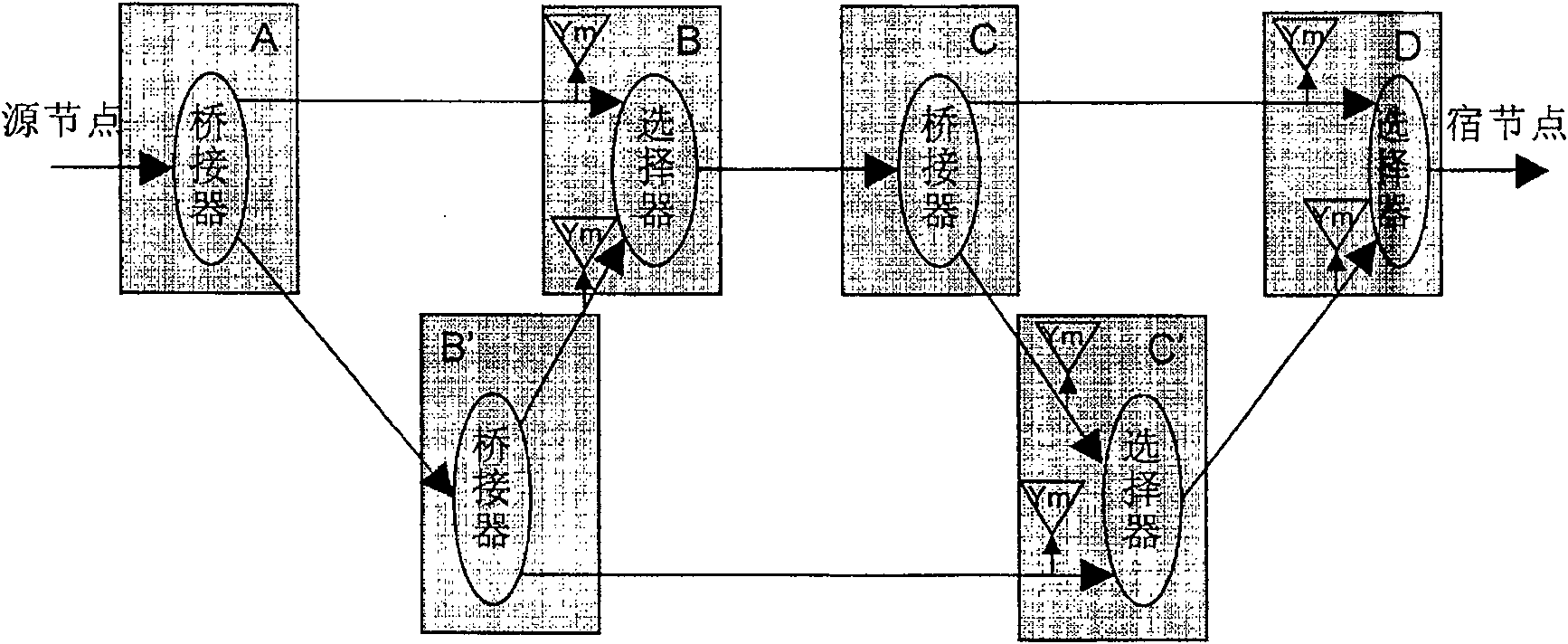
[0023] figure 2 is the protection framework according to the first embodiment of the present invention. like figure 2 As shown, the bridge at the source node A duplicates the input signal into two copies and sends them to the two downstream nodes respectively. For example, node B' copies the signal from node A and sends it to B and C'. The selector completes the selection of signals. For example, node B needs to select one of the two signals from A and B' and send it downstream. How to select is related to the specific mode, which will be described in detail below.
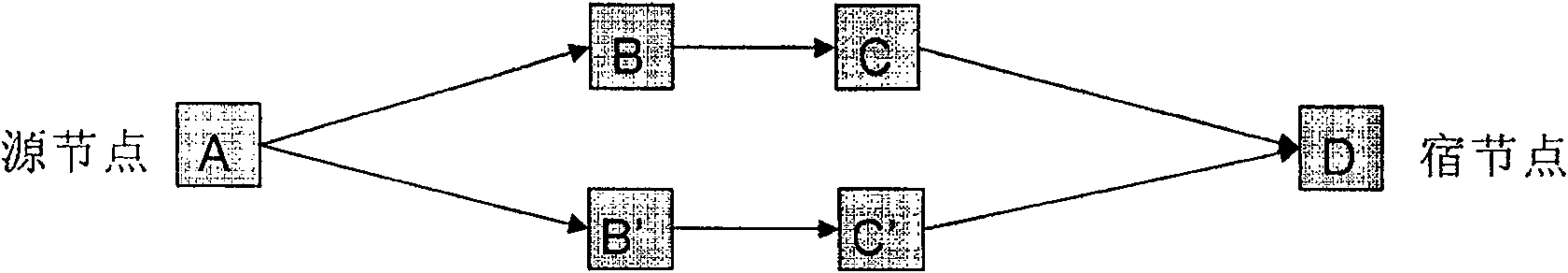
[0024] It should be noted that the connection between two nodes in the figure can be through an intermediate node, and whether there is an intermediate node does not affect the integrity of the architecture description and the feasibility of implementation. In addition, the source node and sink node in the figure are not the source and sink of services, but the source and sink of subnet connections. That i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com