Single broadcast reverse path repeating method
A technology of reverse path forwarding and unicast, which is applied in the field of network communication, can solve the problems of unsafe inspection and the inability to strictly prevent source IP address spoofing attacks, and achieve the effect of ensuring security and improving inspection speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
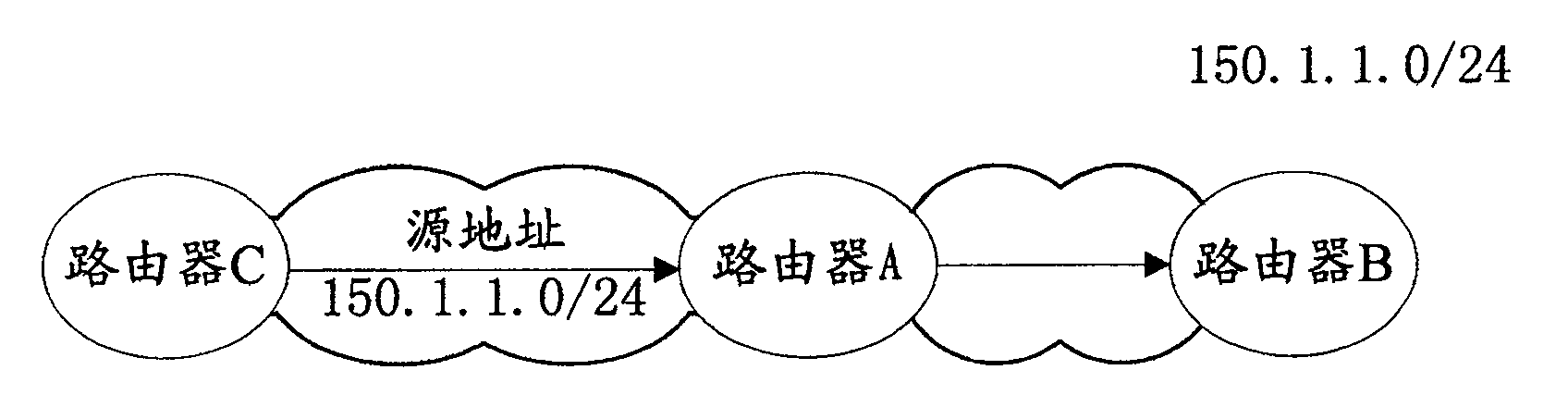
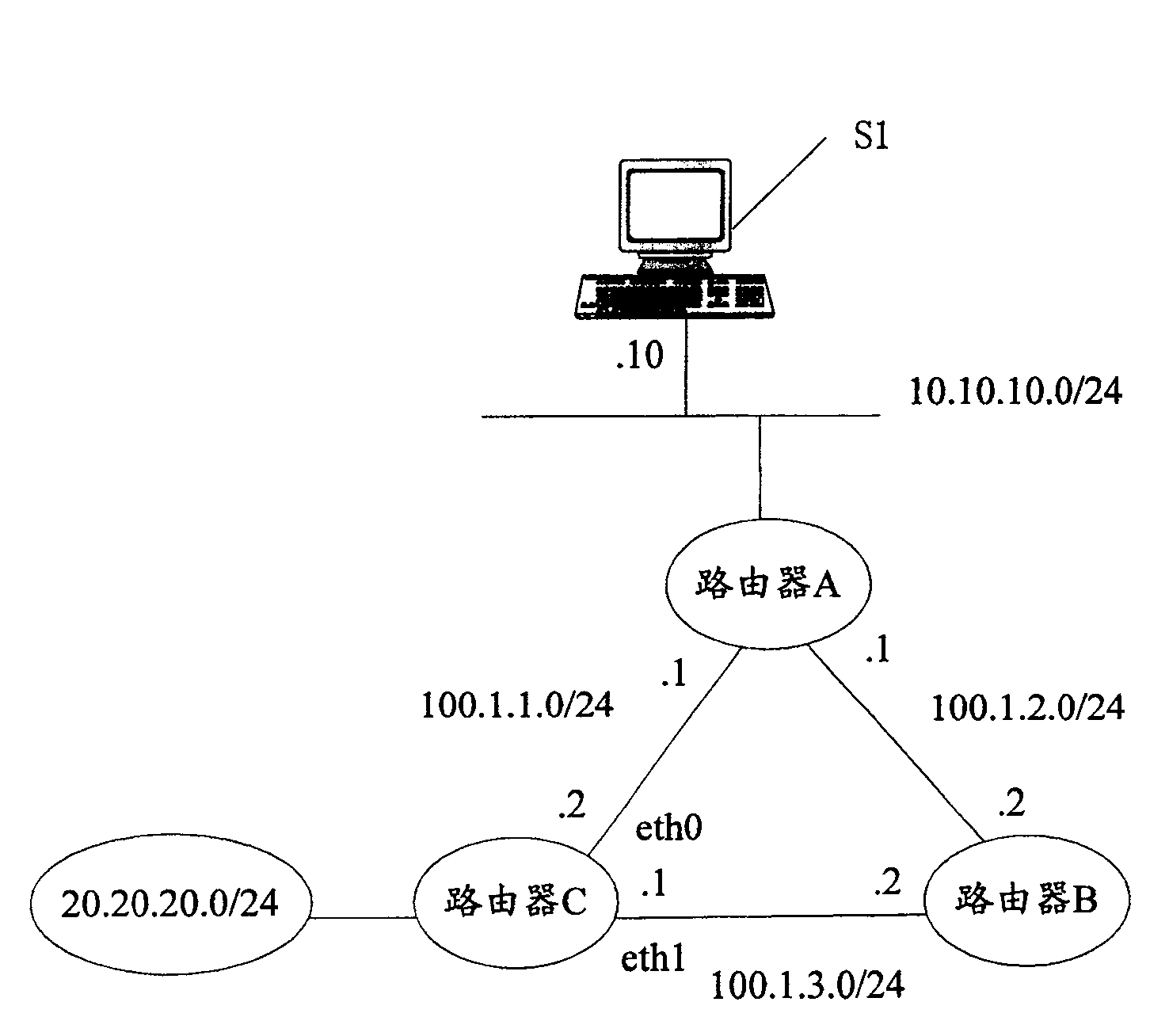
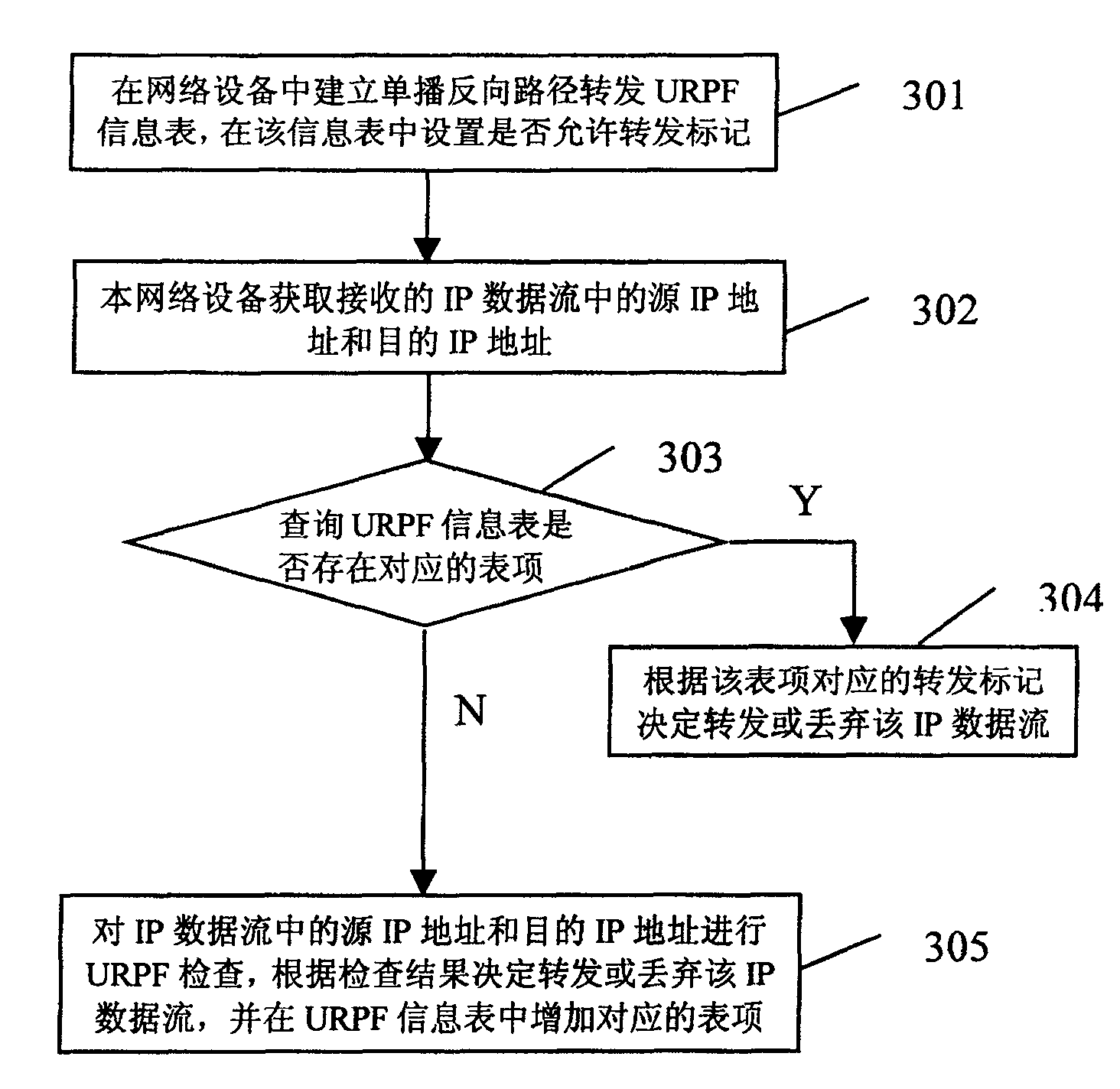
[0055] The core of the present invention is to set up URPF (Unicast Reverse Path Forwarding) information table in network equipment, set whether to allow forwarding mark in this information table; After the interface of network equipment receives IP data stream, according to IP data stream Query the URPF information table for the source IP address and destination IP address; if there is a corresponding entry in the URPF information table, decide to forward or discard the IP data flow according to the forwarding flag corresponding to the entry; if there is no corresponding entry in the URPF information table URPF checks the source IP address in the IP data flow, decides to forward or discard the IP data flow according to the inspection result, and adds the corresponding entry in the URPF information table.
[0056] In the present invention, a URPF (Unicast Reverse Path Forwarding) information table needs to be established in the network equipment. This table can be stored in ha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com