Method for verifying SMS and transmitting reliability classification based on cipher technology mark
A cryptographic technology and short message technology, which is applied in the field of identity-based cryptographic technology to authenticate short message senders and realize reliable classified delivery, which can solve problems such as normal short message congestion and failure to receive, and achieve reduced processing pressure and a good business model And management mode, high efficiency effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
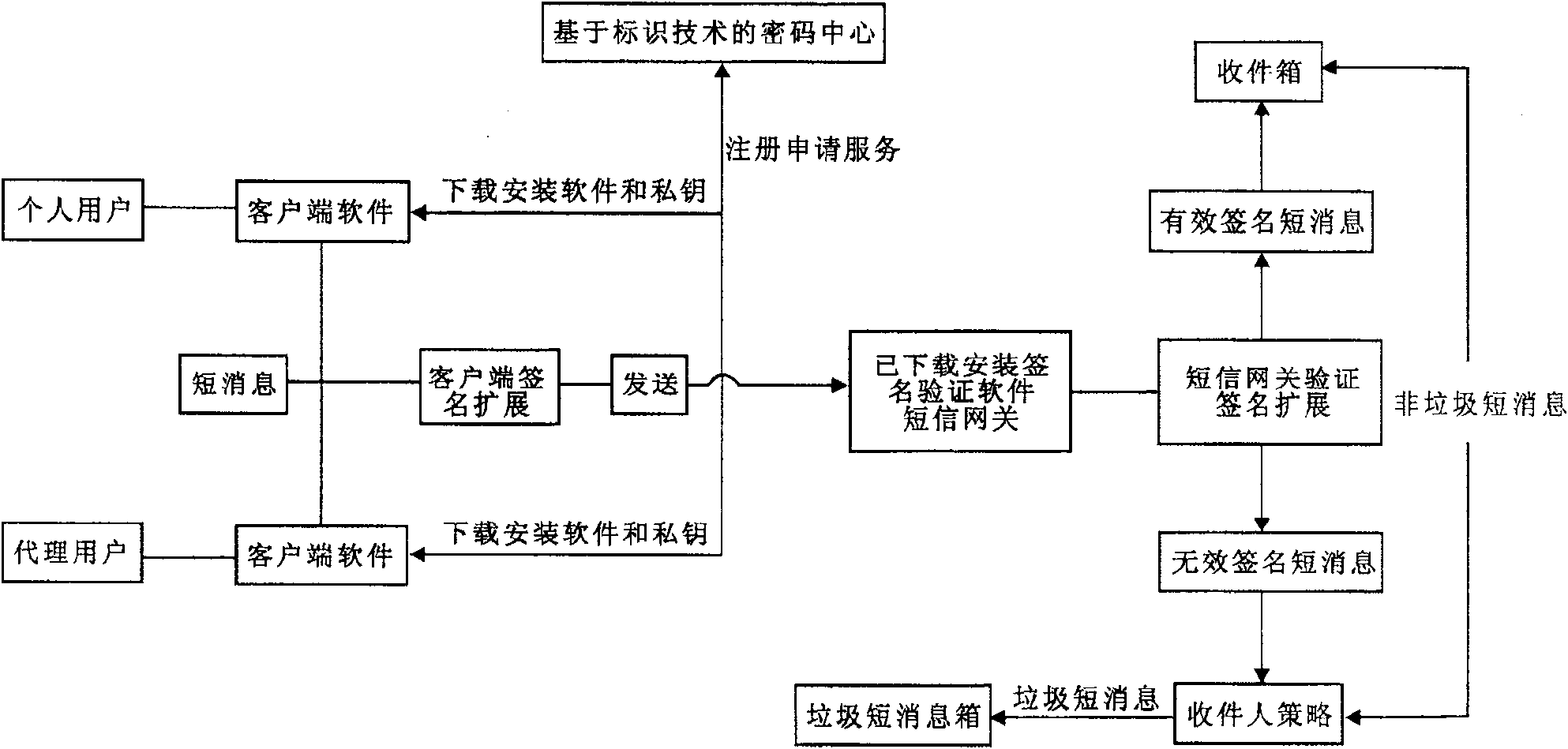
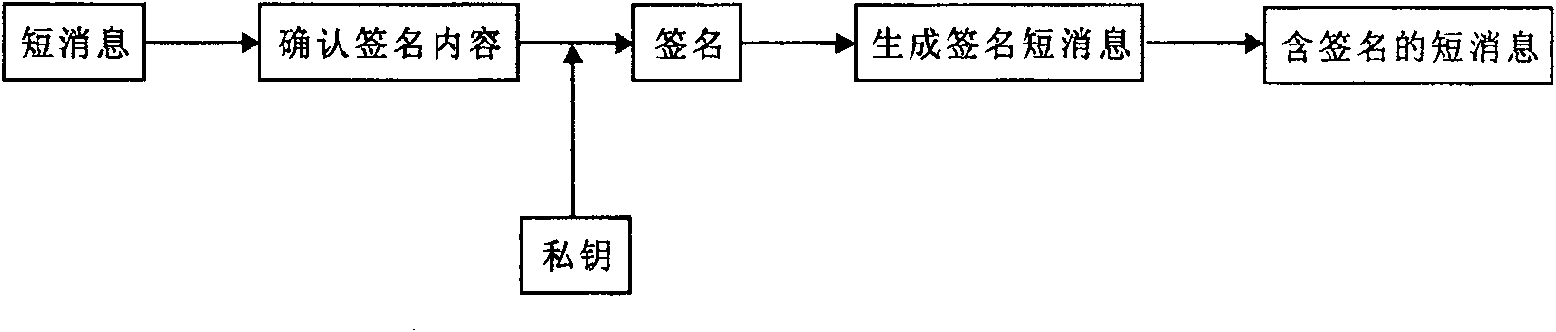
[0077] The cryptographic center of the present invention is established by the identification-based cryptographic technology, (1) to determine the use of an identification signature algorithm, such as the IBS-2 algorithm in the prior art 1; (2) to generate system parameters (including the master key). See the appendix in Technique 1 for an example.
[0078] User application service process. First of all, the user should apply to the password center for registration. Individual users generally use their short message address as their identification. Other users can use their own legal identification as their registration identification, such as IP address, domain name, etc., or short message address, password center. Any registration authentication method can be used, such as "a method for authentication of user identity of public network security communication service based on identity cryptography" disclosed in CN1697379, as long as it can effectively prove that the identity ...
Embodiment approach
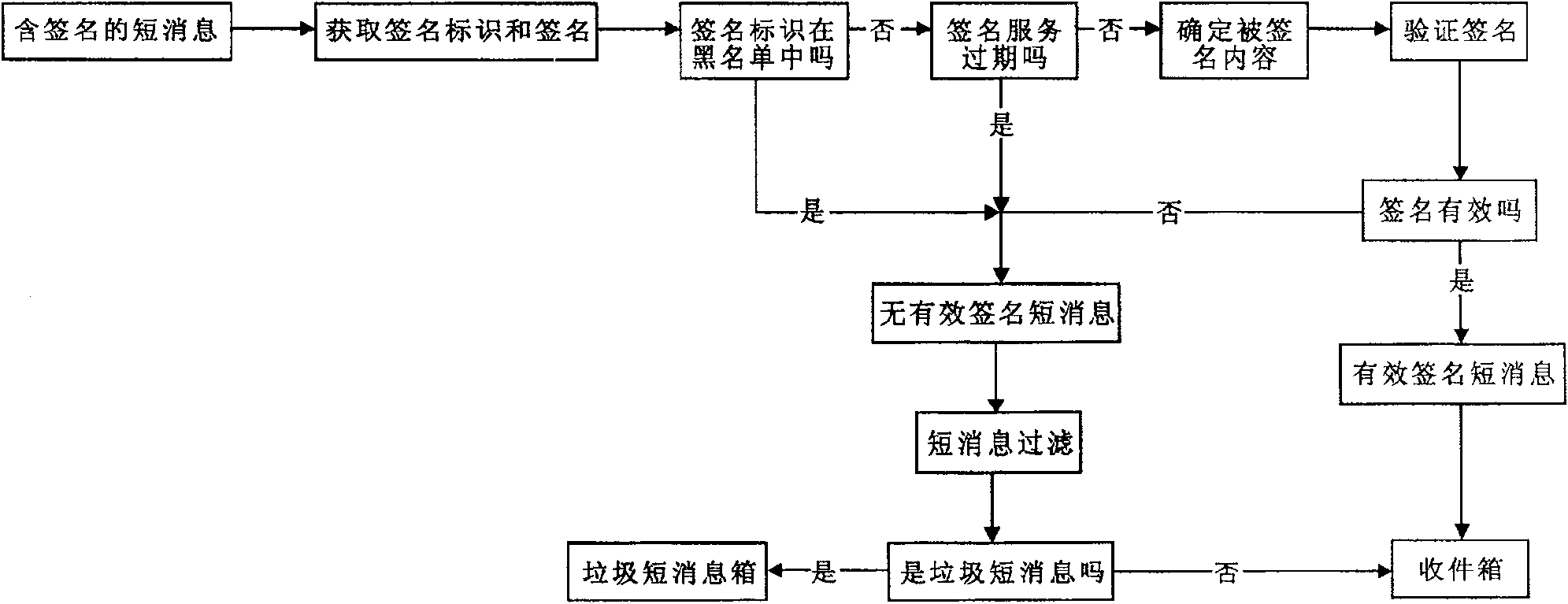
[0083] When processing a signed short message, verify whether the user's identification is in the identification blacklist, and if it is in the blacklist, it will be treated as a spam short message;
[0084] For short messages without signatures, short messages beyond the validity period of the service, and short messages whose signature validity has not passed the verification, the short messages are filtered according to ordinary short messages;
[0085] The present invention can also include the update process of identifying the blacklist: the user thinks that a short message that has passed the signature authentication is a spam short message, and can send the entire short message to the password center to report the short message; the password center verifies the reported short message After verifying the authenticity of the signature, determine whether the reported short message is a spam short message according to known rules, and determine whether to blacklist its user ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com