RSA ciphering method for realizing quick big prime generation
An encryption method and prime number generation technology, applied in key distribution, can solve the problems of long operation time, slow system running speed, long time, etc., and achieve the effect of improving processing speed and stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] Various preferred embodiments of the present invention will be described in more detail below in conjunction with the accompanying drawings.
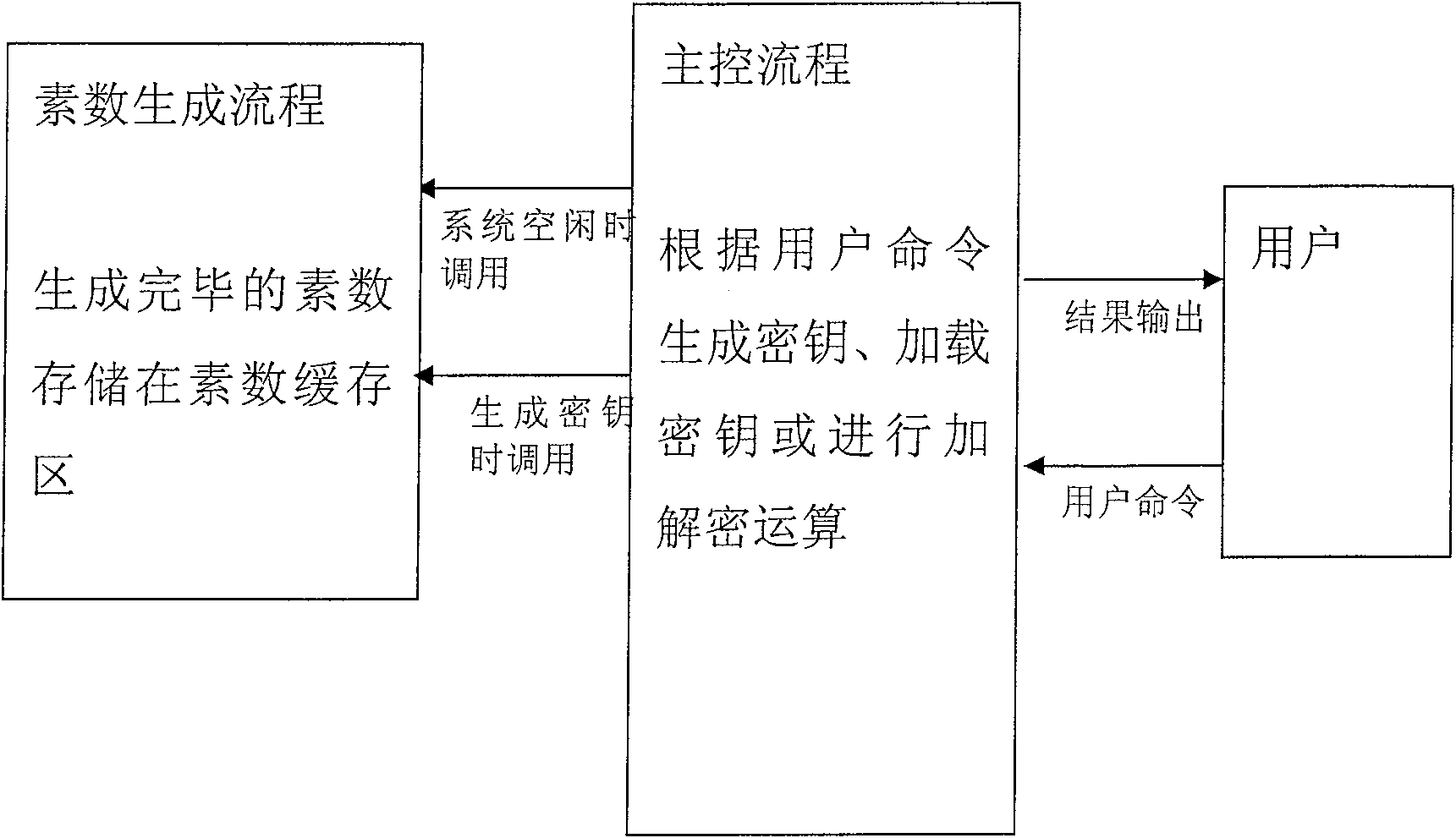
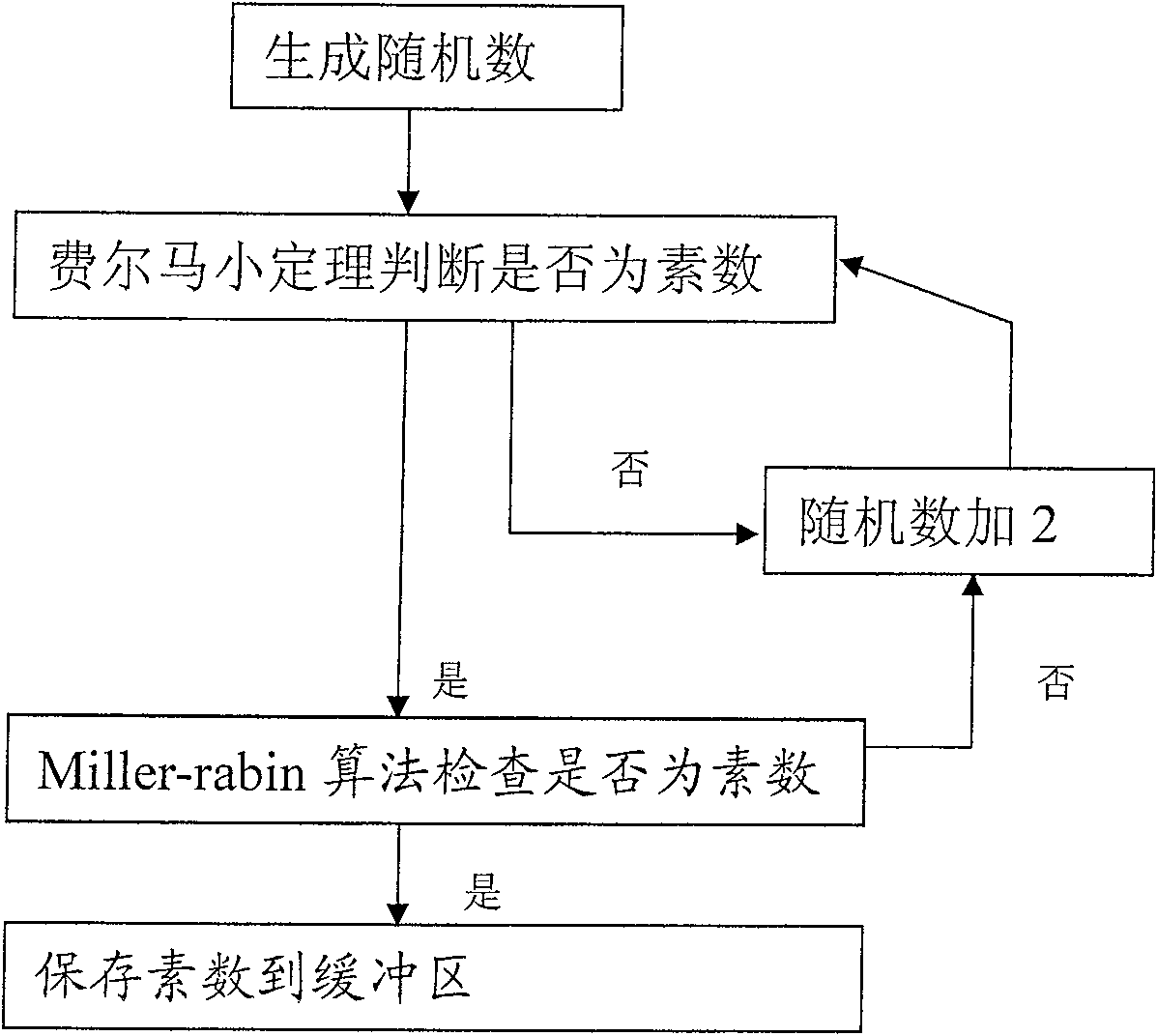
[0025] The cryptographic calculation implementation process of the present invention includes: the system automatically calculates when idle, generates more than two prime numbers, and stores them in the prime number buffer; Prime numbers p and q, and use these two prime numbers to generate an RSA key, for example, calculate the RSA public key n=p*q; generate a random number e, so that e and (p-1)(q-1) are mutually prime, and e is also public key; calculate RSA private key d=e -1 mod(p-1)(q-1), and then output the key to the user; the user invokes the function of loading the key of the system, and the system stores the key input by the user in the key buffer; the user invokes the encryption function of the system, The system takes out the key from the key cache, encrypts and calculates the plaintext input by the user, and output...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com