Authentication method between proximity terminals, and method and terminal for delivering secret information
一种认证方法、终端间的技术,应用在接近的终端间的认证、隐匿信息的配送以及终端领域,能够解决加密处理大负担等问题
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
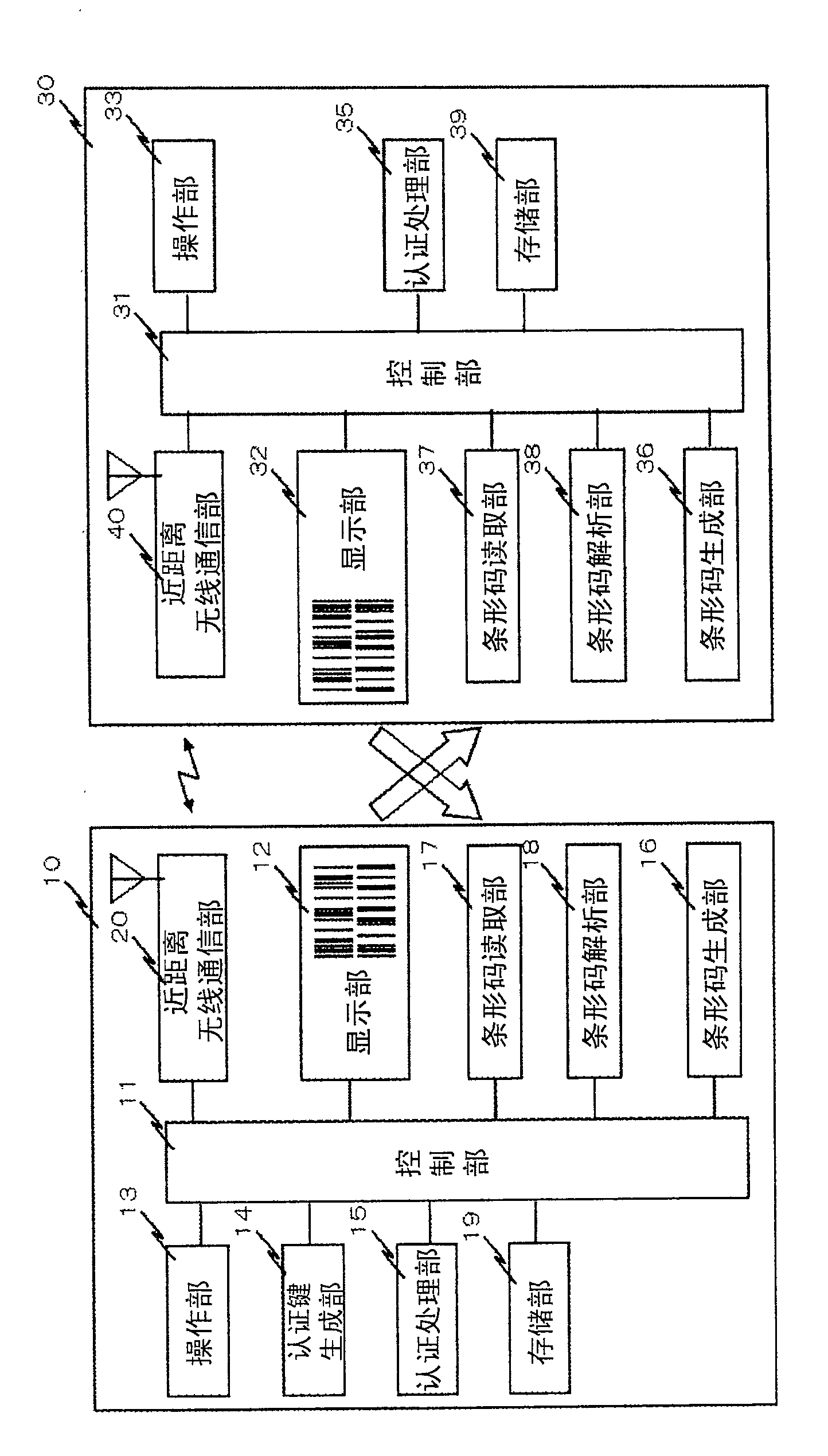
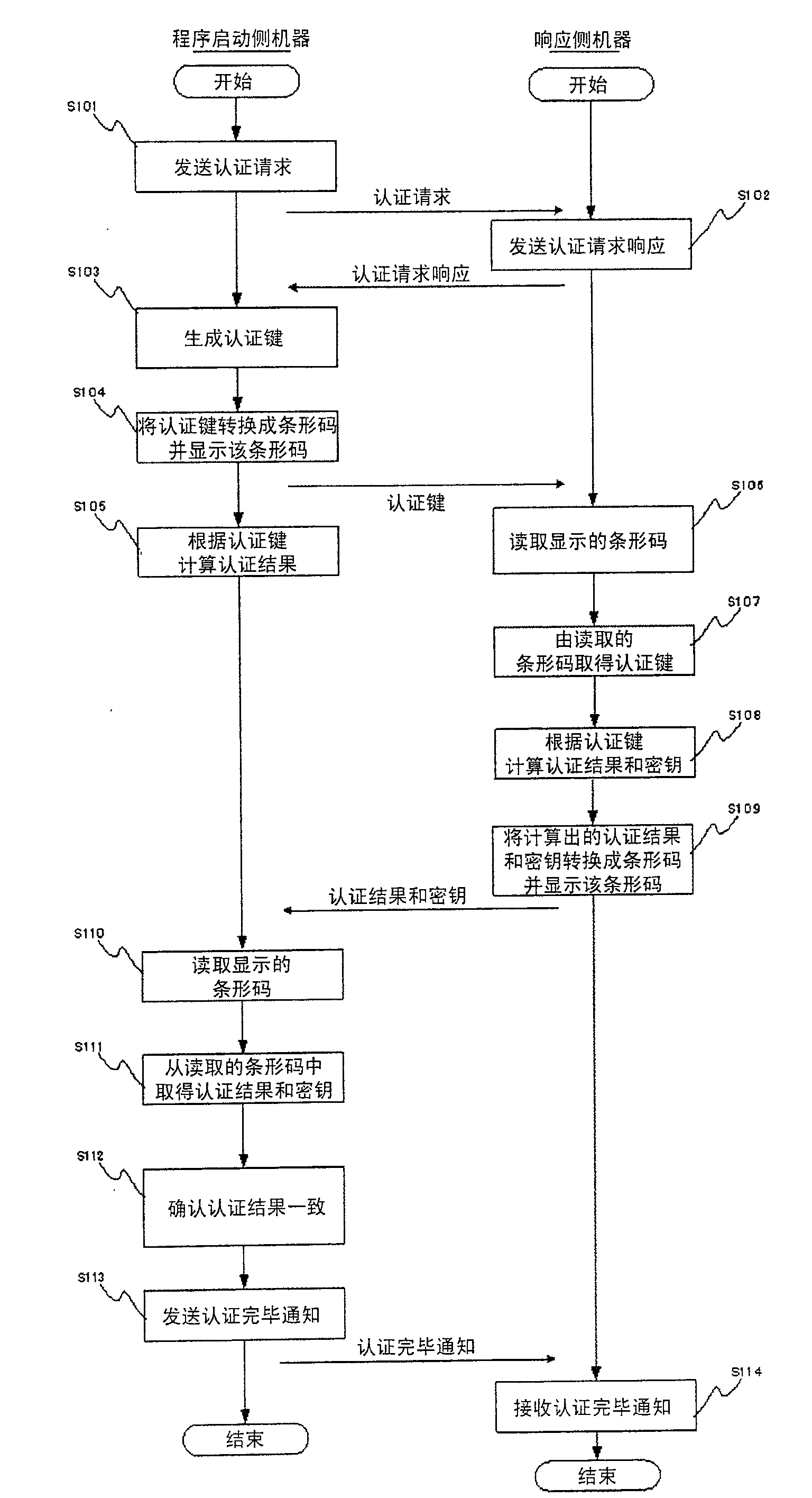
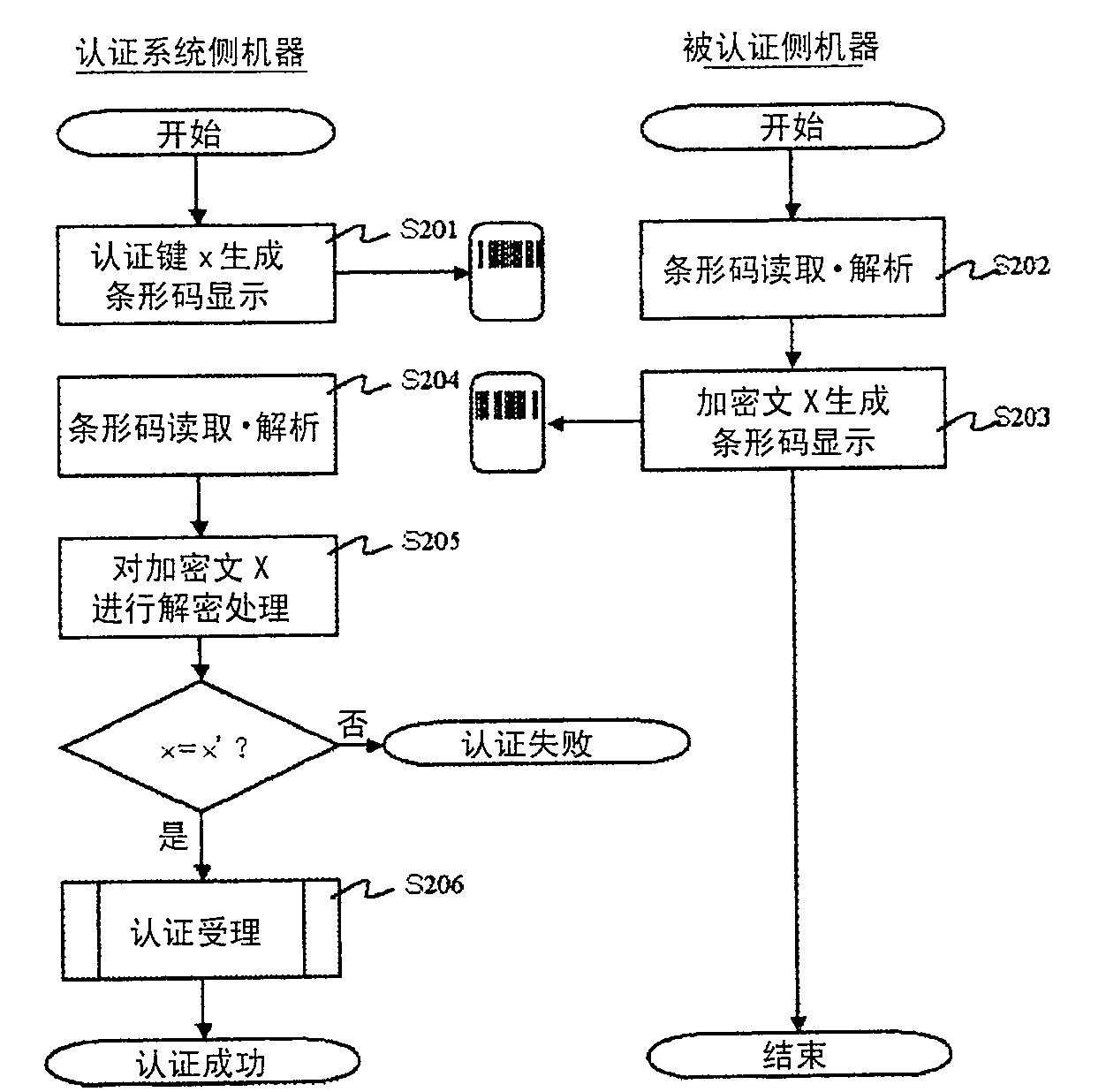
[0038] Next, the best mode for carrying out the present invention will be described. In this embodiment, when devices equipped with short-range wireless communication technologies such as Bluetooth (registered trademark) and wireless LAN are connected to each other by short-range wireless communication, information related to security such as an authentication key and a secret key is converted into a barcode, and By exchanging information through this barcode (visible symbol), object authentication is performed, and at the same time, the encryption key used in the future short-range wireless communication is transmitted as confidential information.
[0039] Next, start the side machine for the program ( figure 1 10) and the response side machine ( figure 1 30) The case where a short-range wireless communication connection is performed will be described. First, the program starts the side machine ( figure 1 10) Use the authentication key generation part (key generator; figu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com