Locking method and unlocking method
An unlocking and non-locking technology, applied in the field of communications, can solve the problems of complicated mobile phone hardware design and increased cost, and achieve the effect of solving after-sales maintenance problems, preventing illegal rewriting, and guaranteeing legitimate rights and interests.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
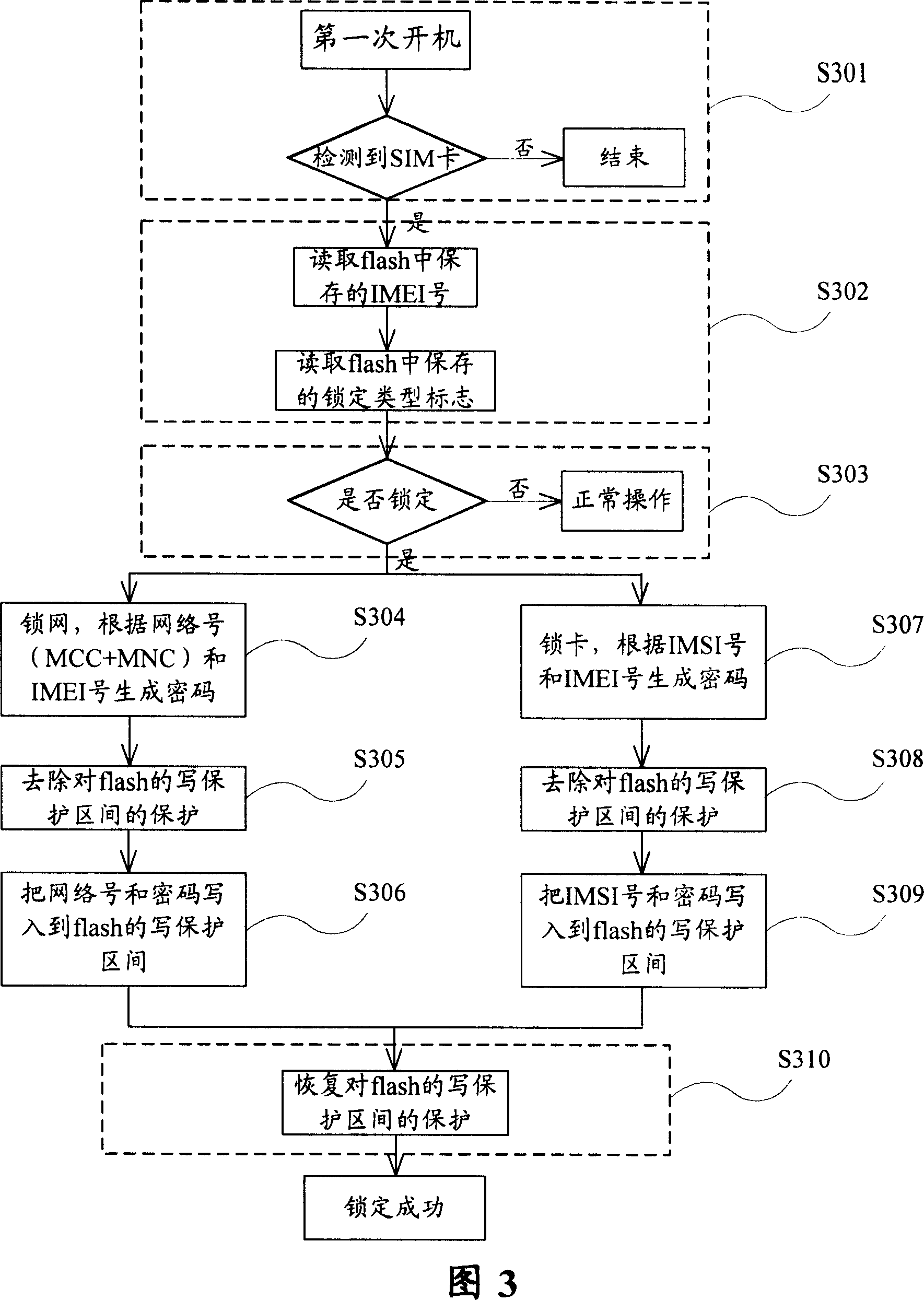
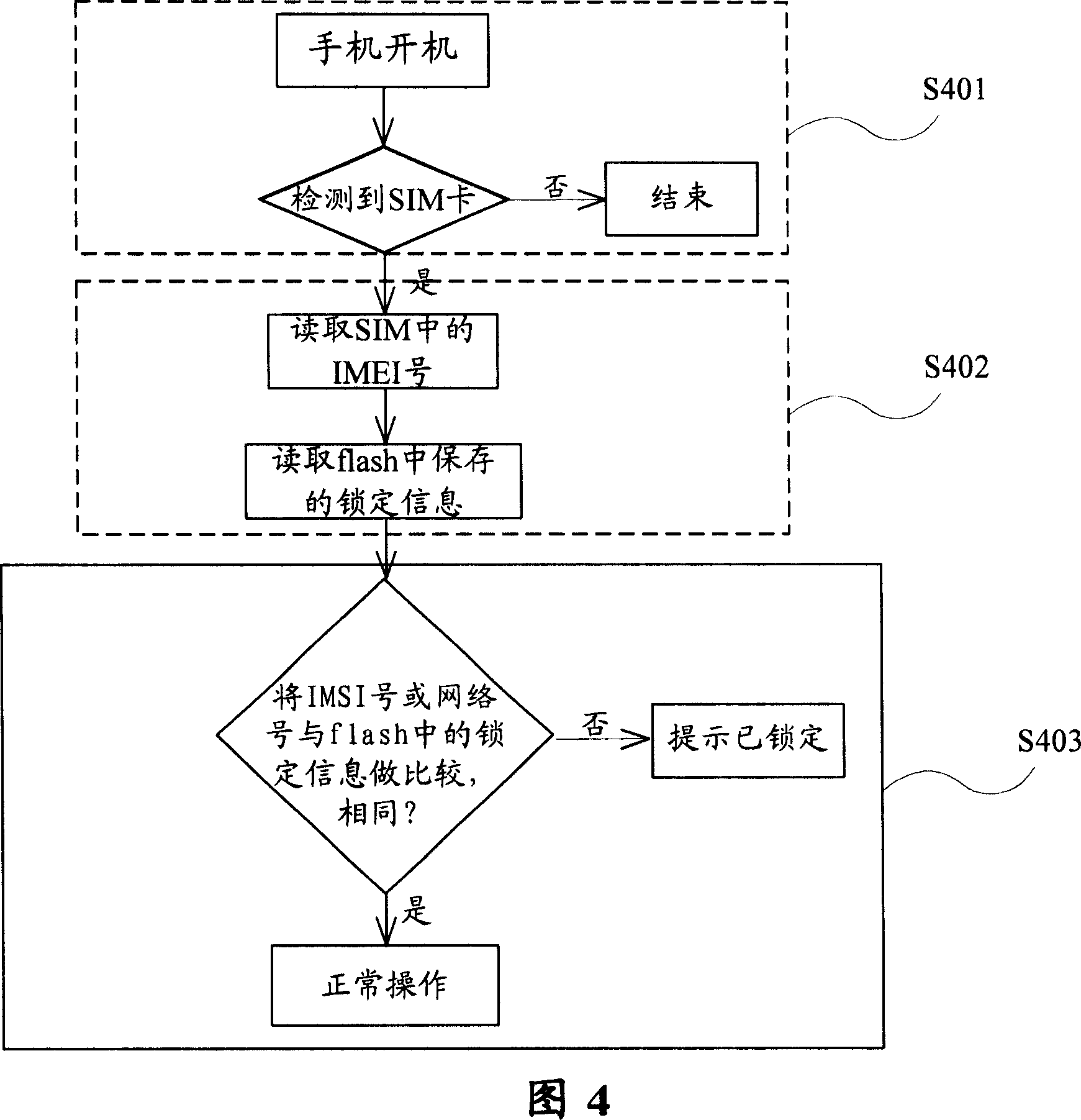
[0023] The preferred embodiments of the present invention will be described below in conjunction with the accompanying drawings. It should be understood that the preferred embodiments described here are only used to illustrate and explain the present invention, and are not intended to limit the present invention.
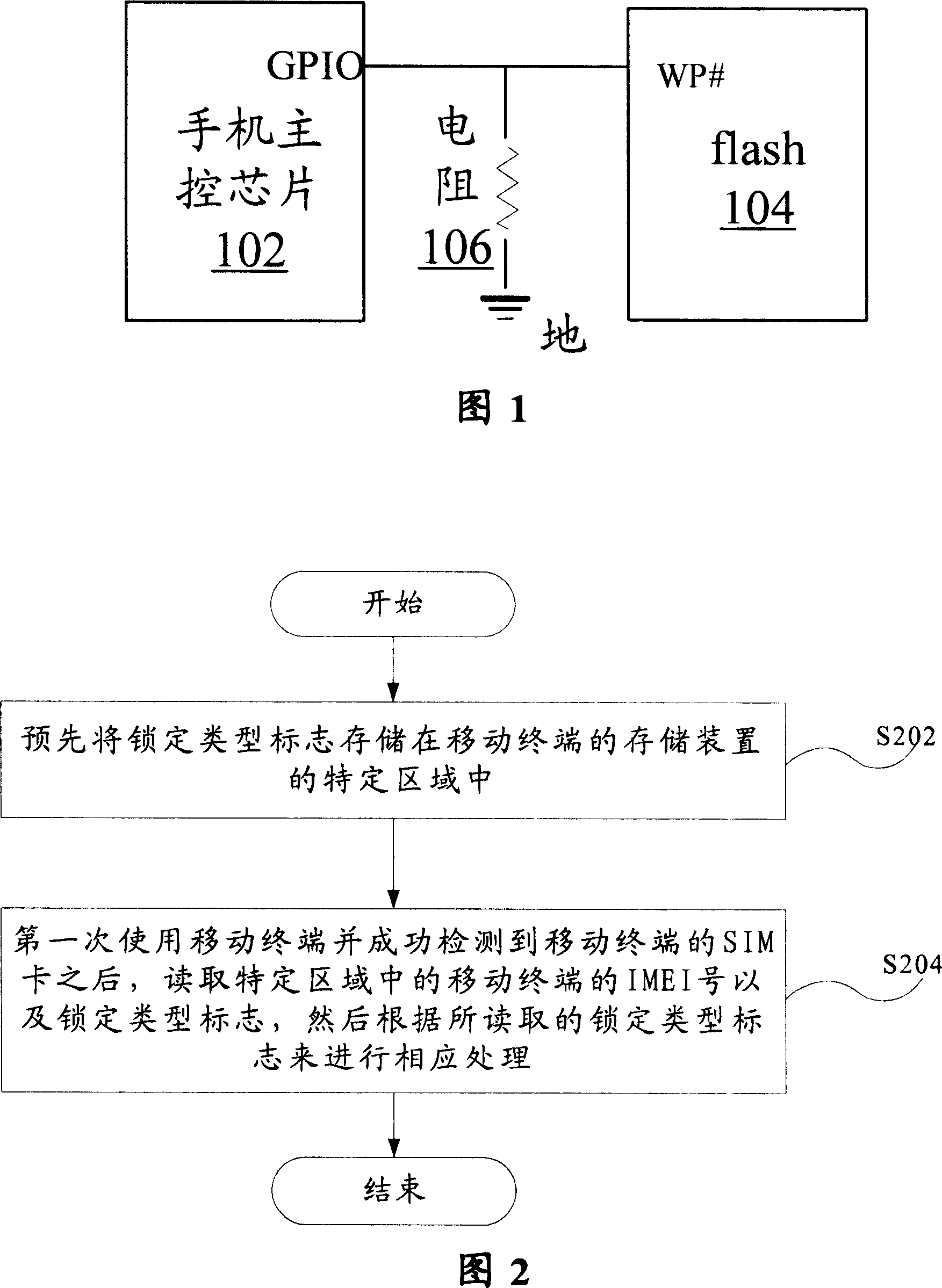
[0024] To complete the network lock, card lock and unlocking functions of the present invention, both hardware and software need to be processed together. The hardware aspect will be described below with reference to FIG. 1 .
[0025] Fig. 1 is the view according to the related hardware design that locking method of the present invention will use, as shown in Fig. 1, in hardware design, need to connect a GPIO (general purpose input and output) pin of mobile phone main control chip 102 to flash104 On the WP# pin, at the same time, connect a resistor 106 (its resistance value is selected according to the specific situation, generally about 100K ohms) to the ground lev...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com