Method for crossing NAT-PT by IPSec
A technology of NAT-PT and both parties, applied in the direction of data exchange through path configuration, digital transmission system, electrical components, etc., can solve the problem of not being able to detect the existence of NAT-PT
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] An example of the present invention is given below.
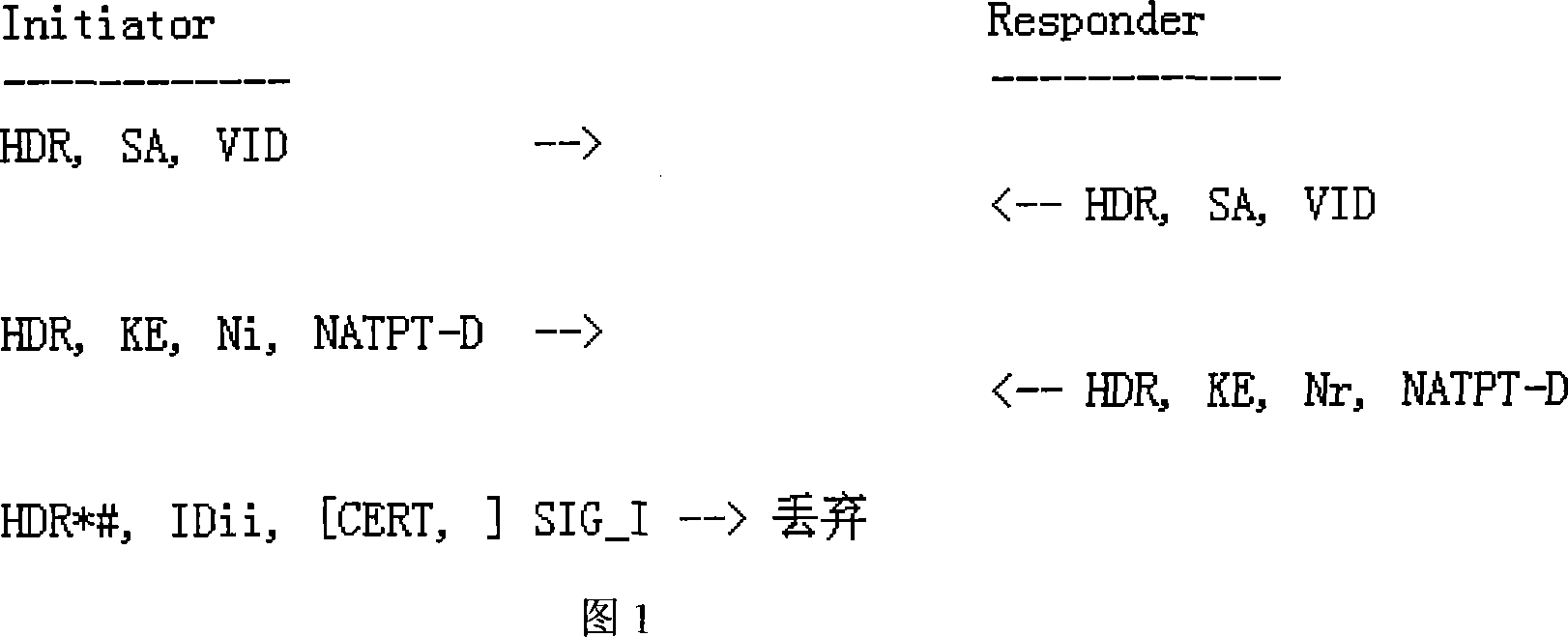
[0047] 1. IKE negotiation phase
[0048] In order to solve the compatibility problem of above-mentioned IPSec and NAT-PT, the present invention has made some improvements to the IKE negotiation process at first, and concrete process is as follows:
[0049] In step 1, add a vendor ID payload (Vendor id payload, VID), which contains a constant value defined by the vendor, and this constant value is used to identify the protocol implementation of the communication peer.
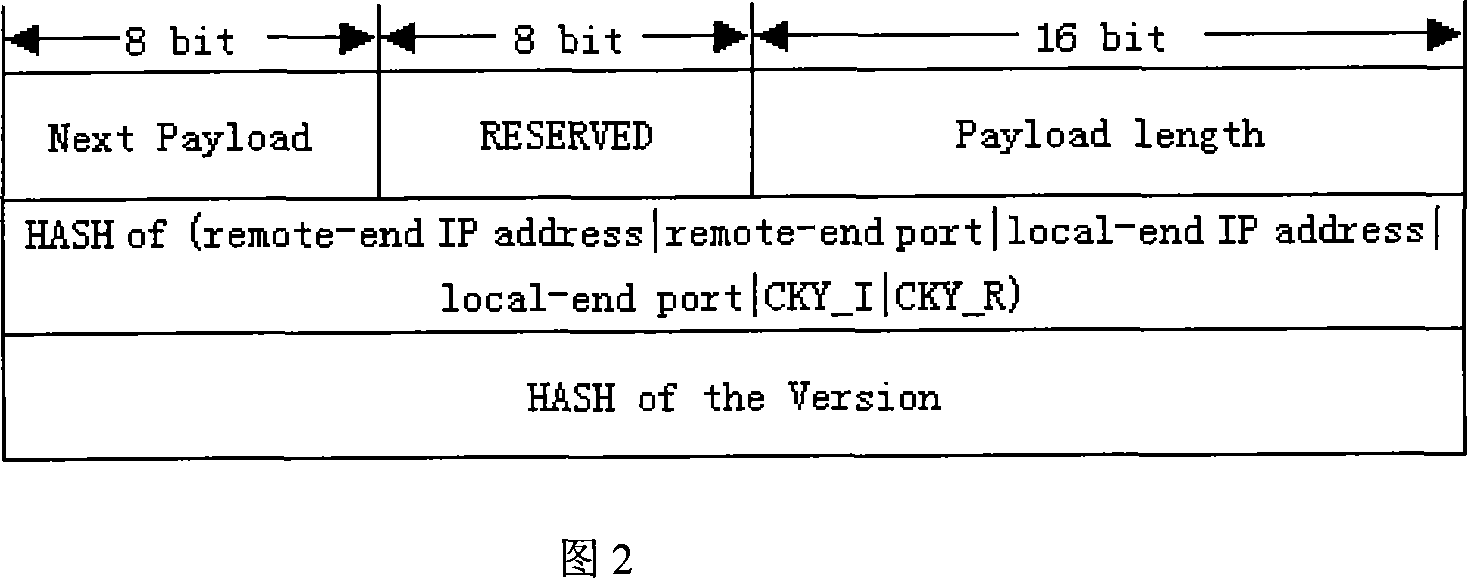
[0050] Step 2, add a NATPT-D payload, as shown in Figure 2, to determine whether there is a NAT-PT gateway between the communication parties. That is, a NAT-PT discovery mechanism is added in the main mode phase of IKE negotiation.
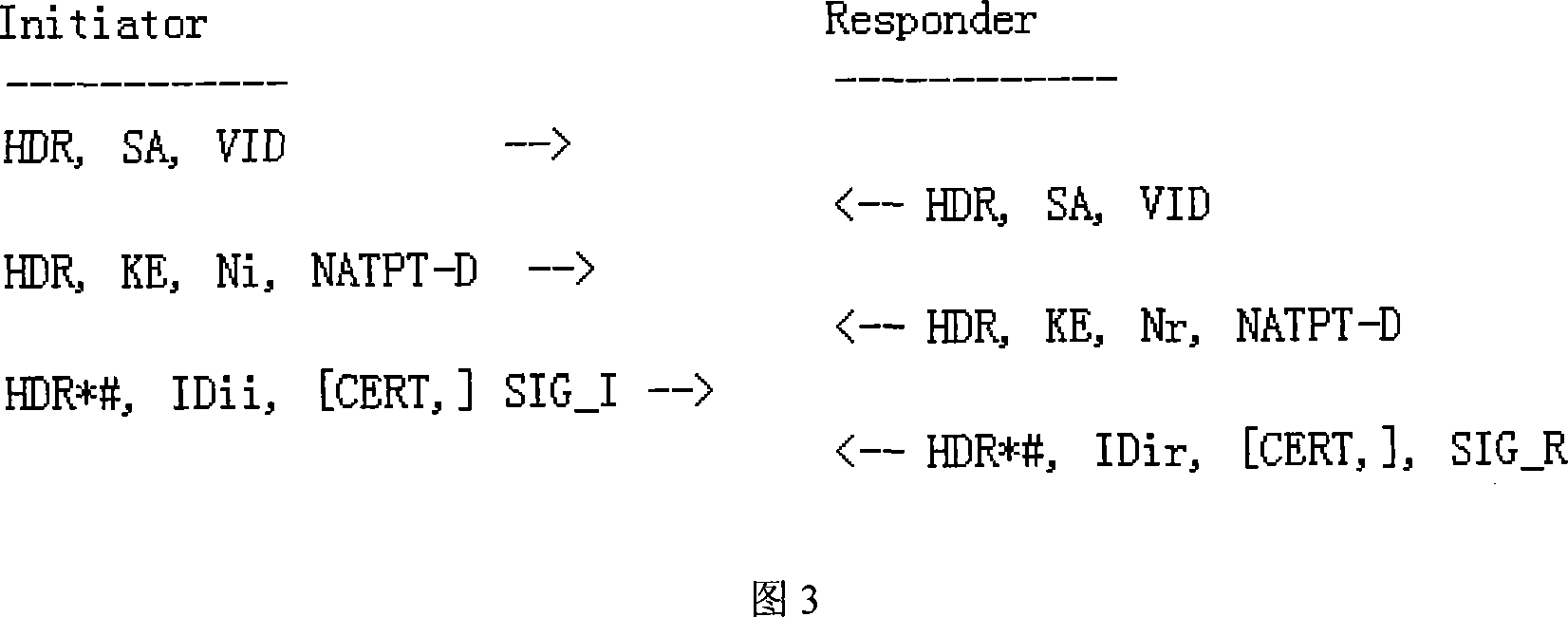
[0051] The specific process is shown in Figure 3, where the VID payload is used to identify the support for the improved IKE protocol. The NATPT-D payload includes the remote host address, the remote host port, the loca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com