Method for identifying meassage source address real or not
A technology of message source and source address, applied in the field of network communication, can solve the problems of unable to support high-speed forwarding performance requirements, consume interface bandwidth processor processing time, etc., achieve the effect of simplifying comparison and query, reducing consumption, and improving identification efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
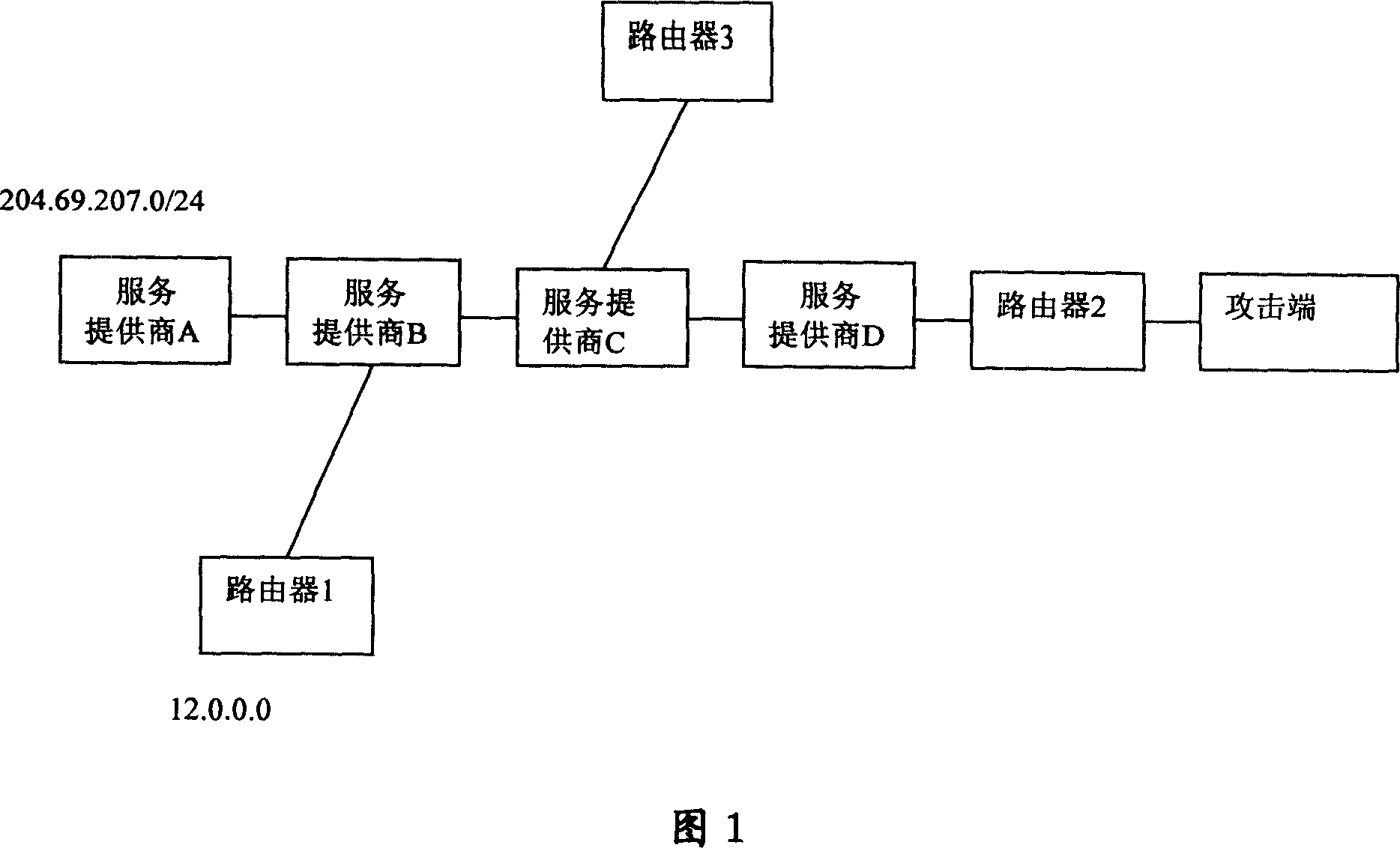
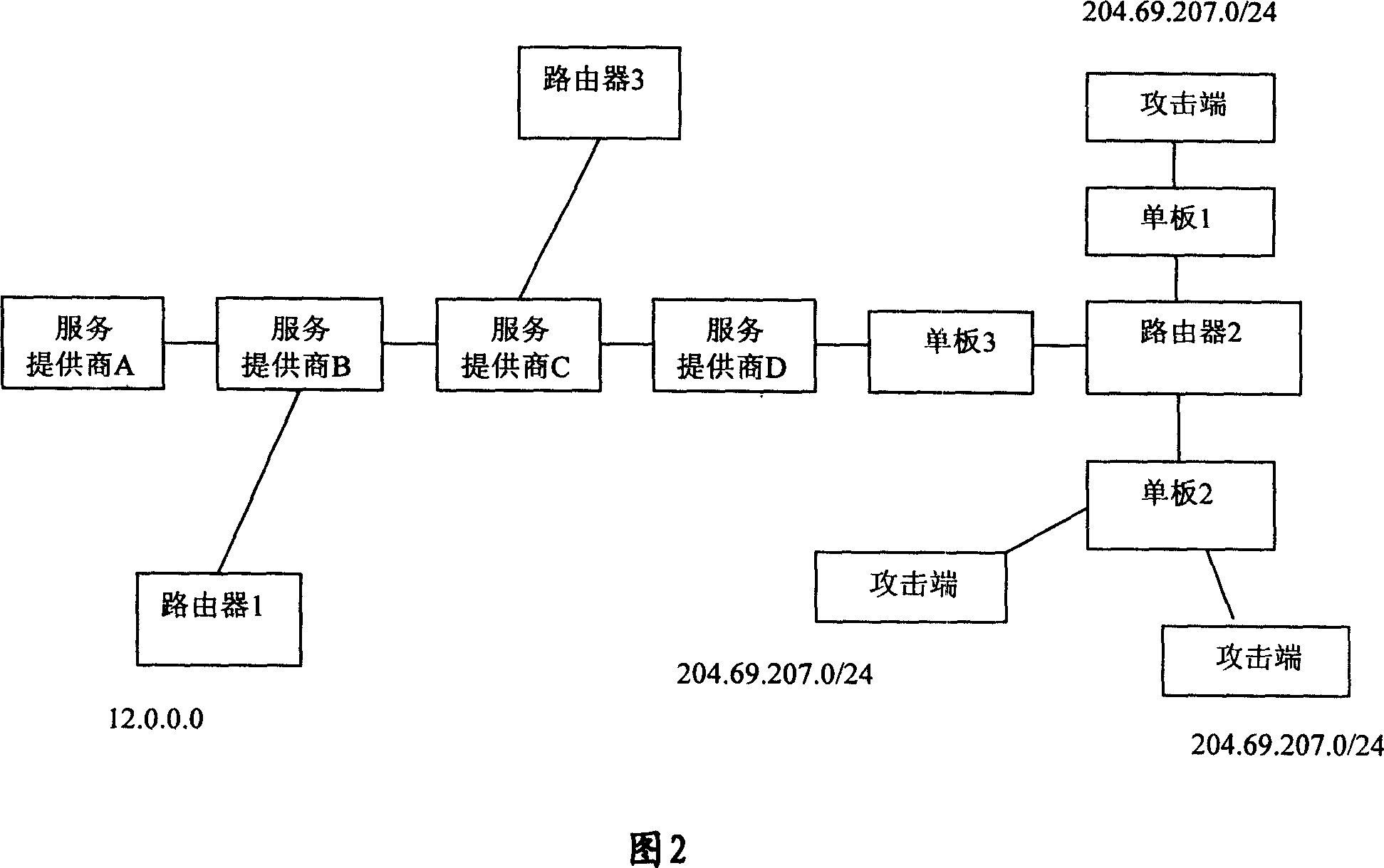
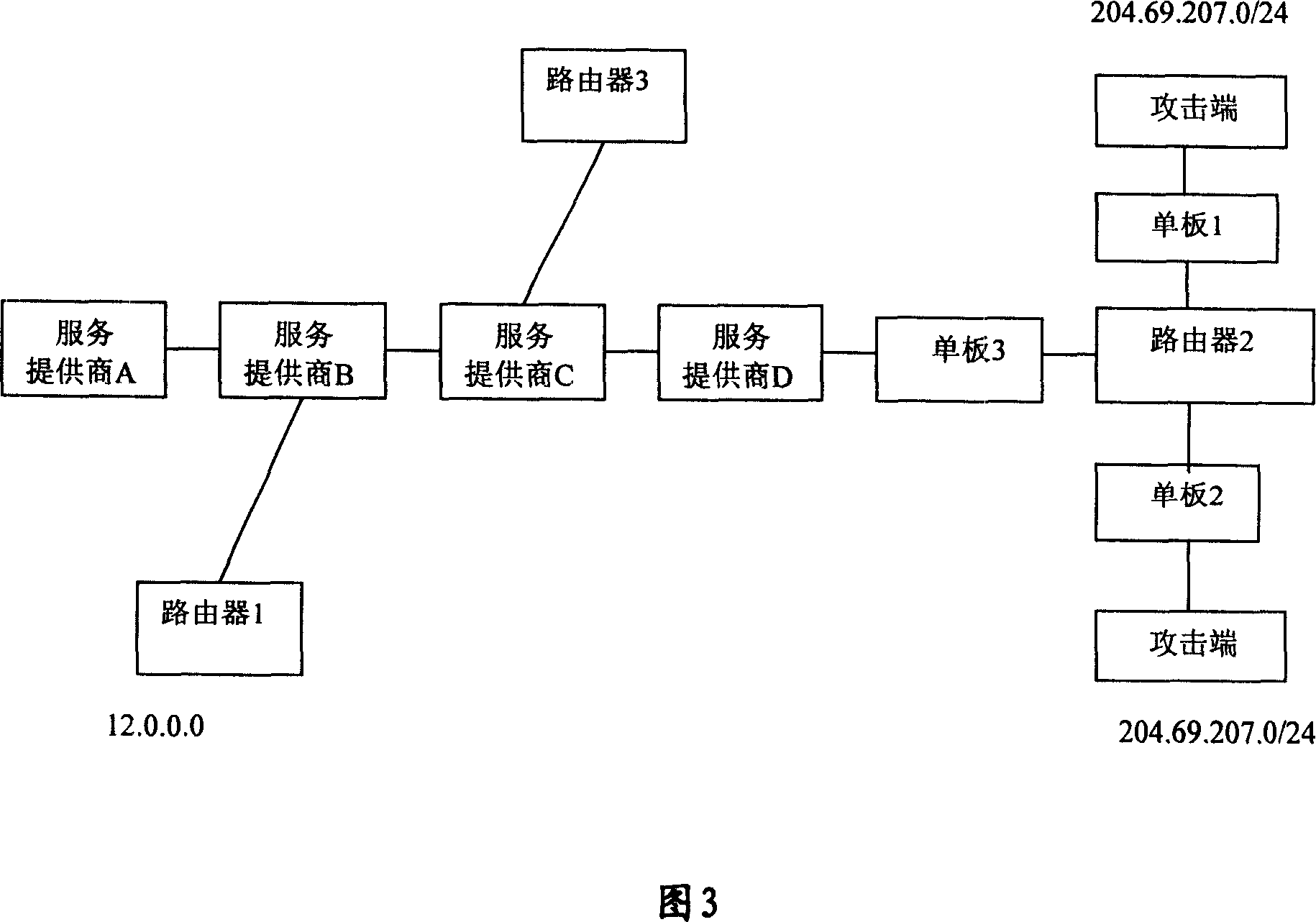
[0062] In Embodiment 1, the single board 2 has 8 ports, wherein port 0 and port 1 are connected to the destination address 204.69.207.0 / 24.
[0063] When a message with a destination address of 204.69.207.0 / 24 enters the router from port 1, according to the content of the routing table entry, the logical operation is performed on the port where the message enters the router, the bit of the port on the local board, and the bit mask of the port on the local board. The obtained result judges whether the source address of the packet is 204.69.207.0 / 24. If it is not a real address, the address is considered to be forged, the message is an attack message, and the message is not forwarded; if it is a real address, the message is considered to be a valid message, and it is normally forwarded.
[0064] The 8 ports in the board 2 are port 0-port 7, and when a message is received from port 1, port 1 is represented as 01000000;
[0065] Perform an AND operation on port 1 with the bit fie...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com