Computer system safety protection setting method and its device
A computer system and computer security technology, applied in computer security devices, computing, instruments, etc., can solve the problem that users cannot use programs, and achieve the effect of improving the security protection level
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
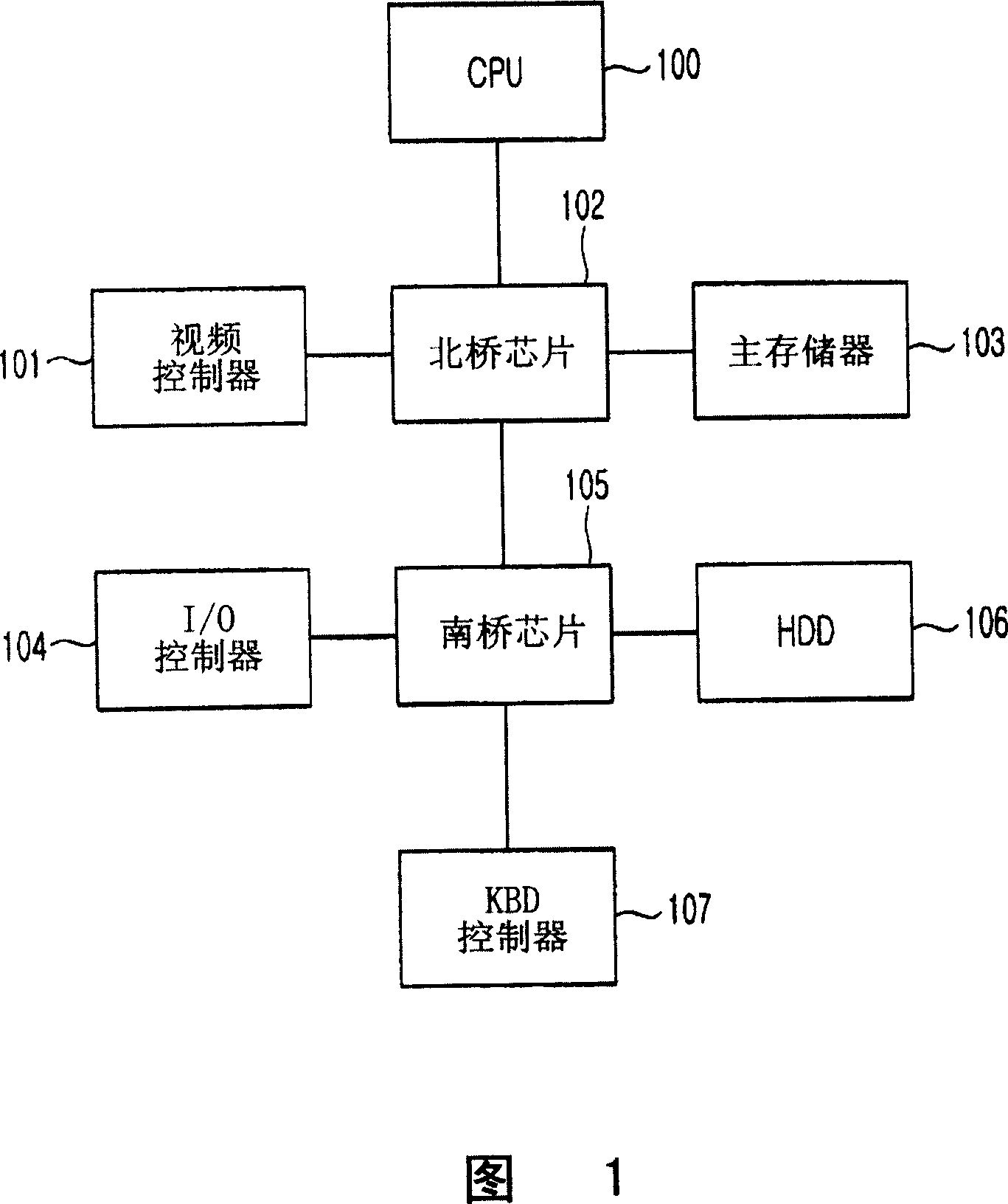
[0038] In the following, implementations of the computer system security protection setting method and equipment thereof according to the present invention will be described in detail with reference to the accompanying drawings.
[0039] Before the description, several terms used in the present invention are defined.
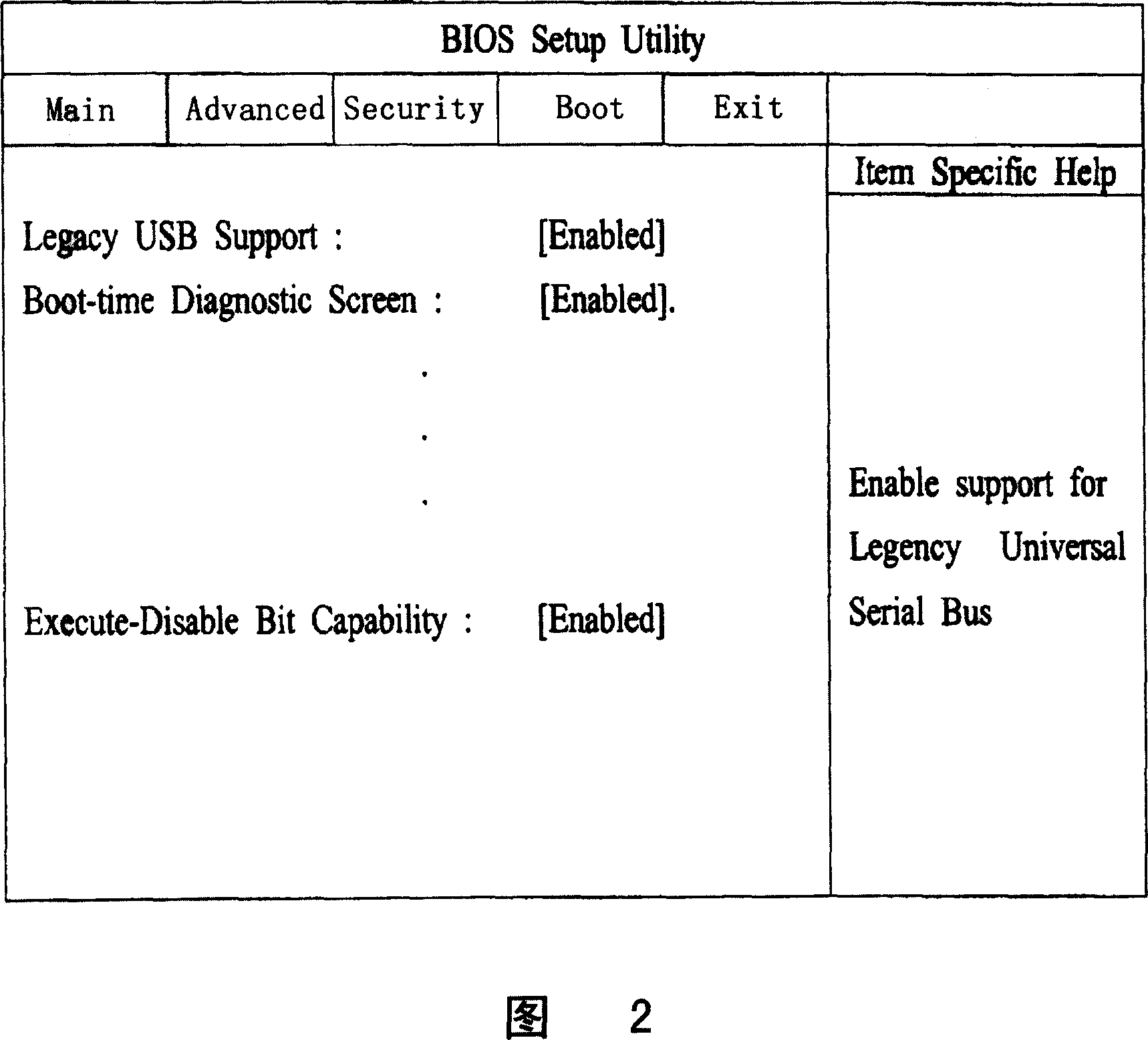
[0040] The "whether to execute display bit" in the present invention refers to the identification of whether the code stored in the page can be executed in the page table of the memory of the computer operating system. Each company names the "whether to execute the display bit" differently. For example, Intel Corporation refers to "whether to execute the display bit" as "Execute Disable Bit".
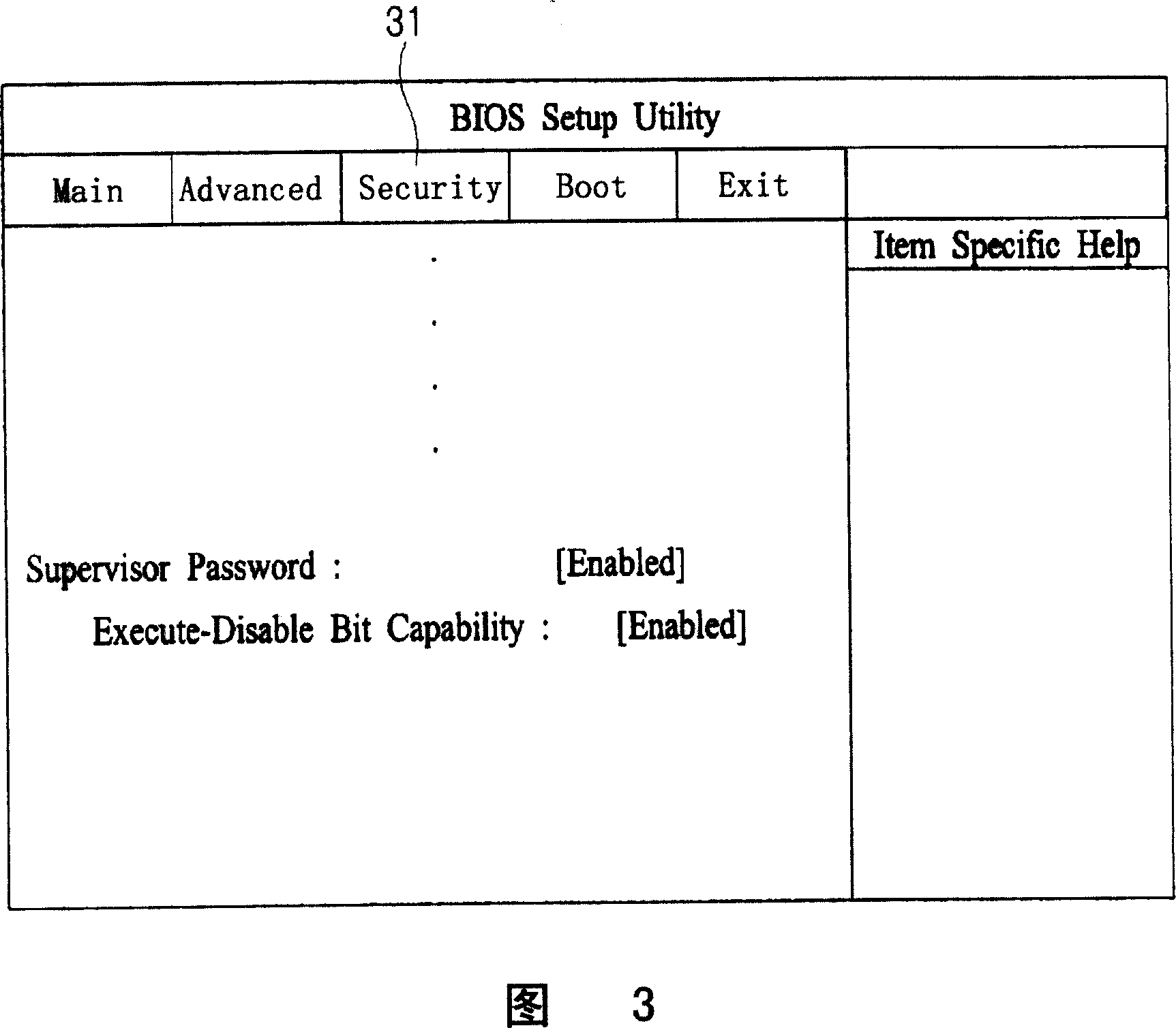
[0041] The "supervisor password" in the present invention refers to specifying the password related to the security protection operation (Security Option) item of the BIOS features setup (BIOS features setup) of the computer system. During the BIOS setup process, if a pa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com