Two-dimensional information encryption method and device, and two-dimensional information authenticating method and server
A technology of two-dimensional information and encryption method, applied in the field of communication, can solve the problems of vulnerability to attack, low security of information authentication process, low security of information encryption method, etc., to increase difficulty, improve security, and prevent large-scale automatic The effect of information theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
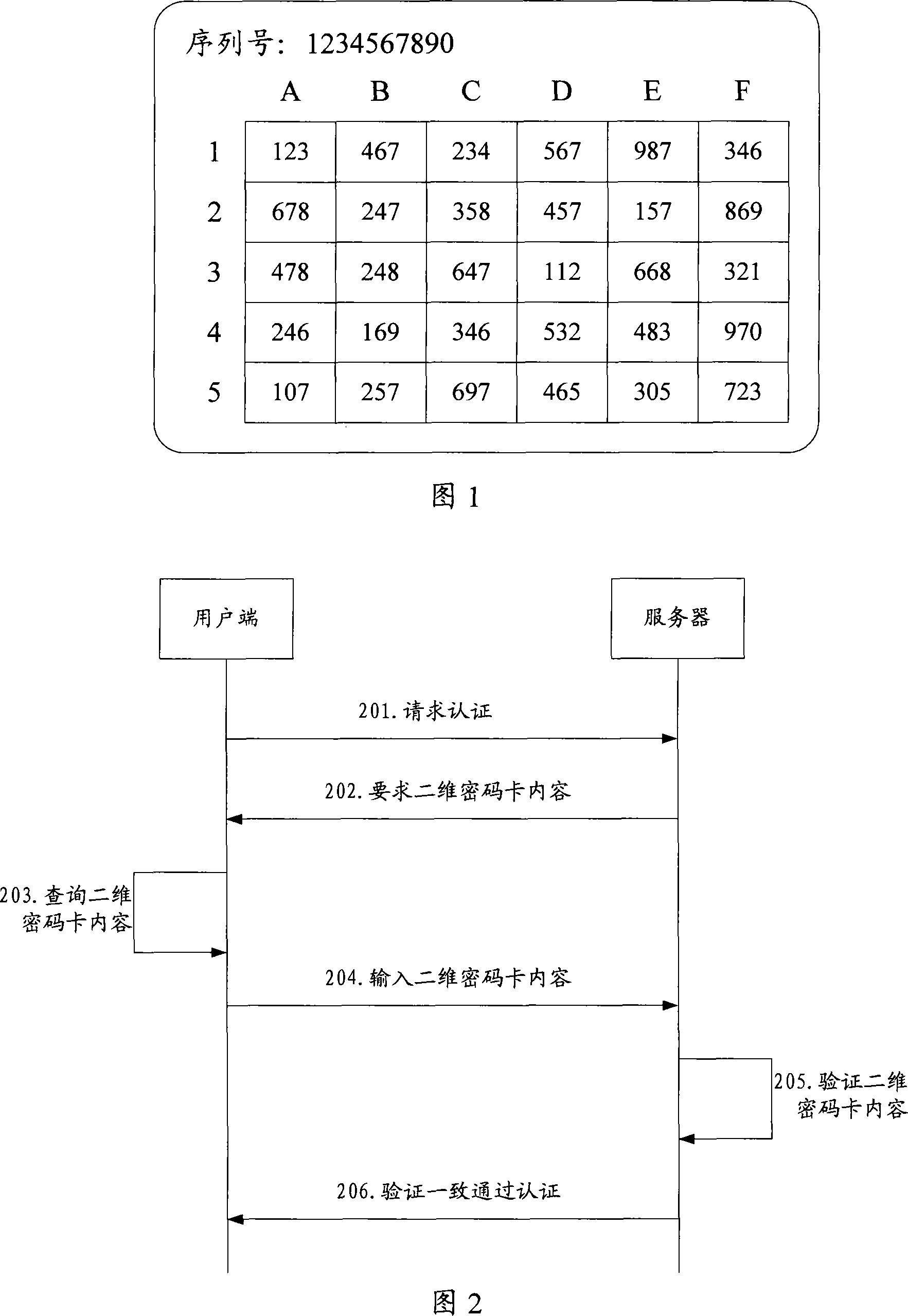
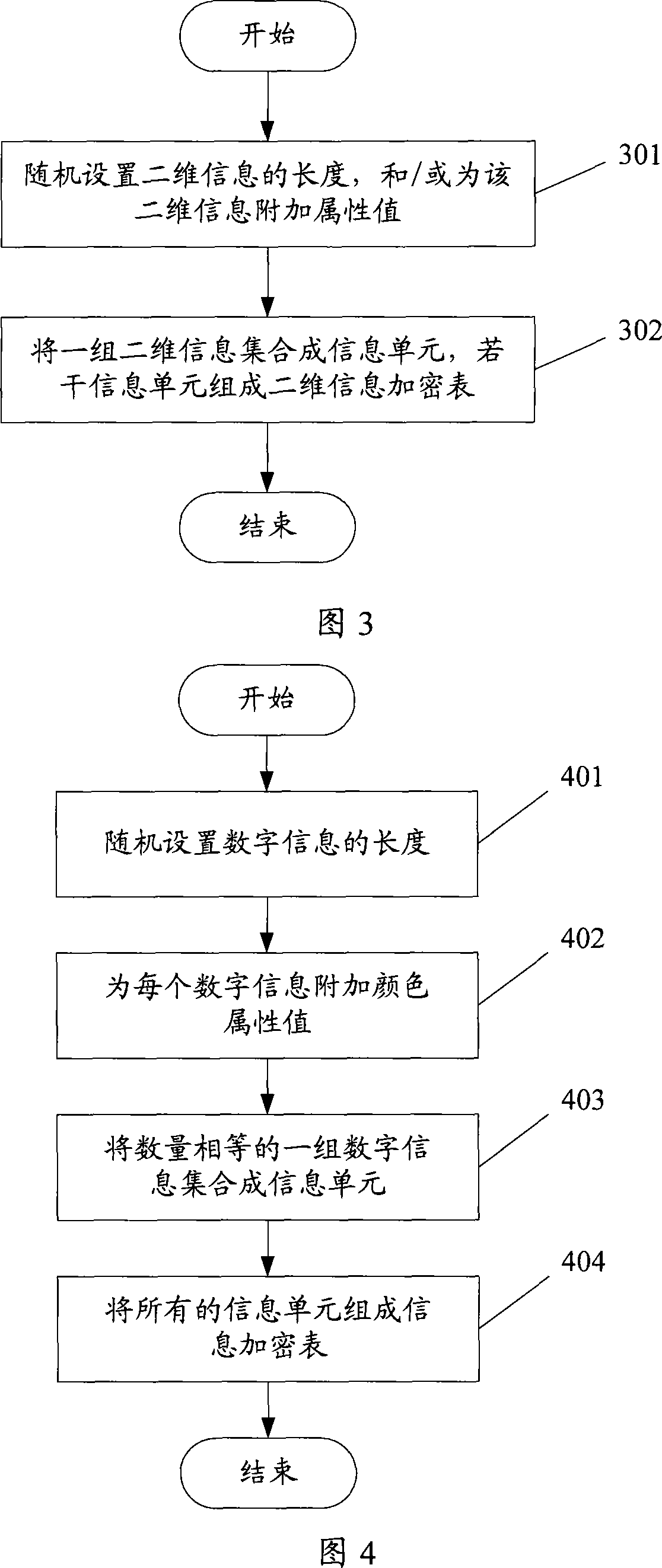
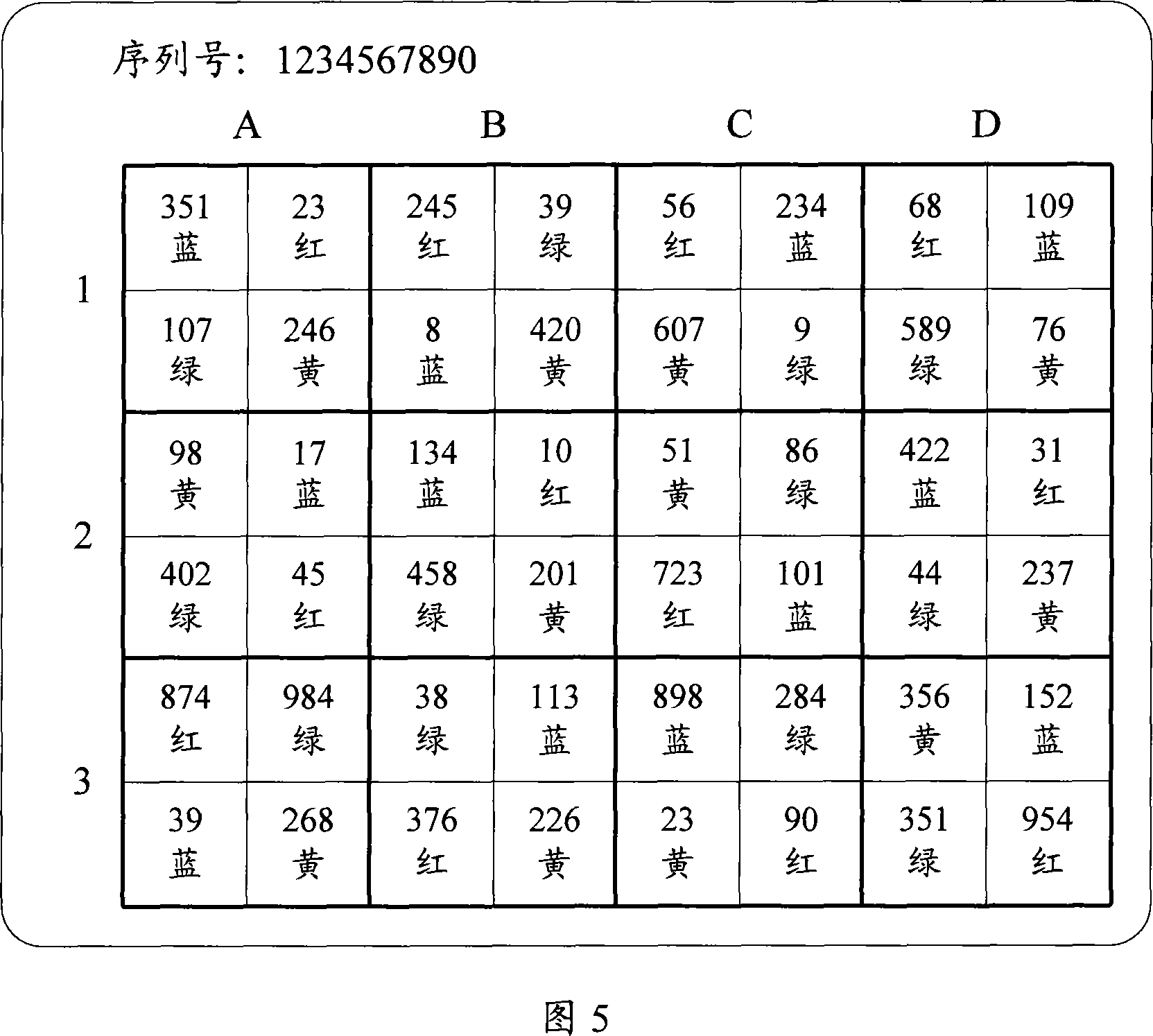
[0051] The present invention respectively provides a two-dimensional information encryption method, the method randomly sets the length of the two-dimensional information, and / or sets attribute values for the two-dimensional information, and then sets a set of length and / or additional attribute values The two-dimensional information of the two-dimensional information is set into an information unit, and several information units form a two-dimensional information encryption table; and a two-dimensional information authentication method, which stores the two-dimensional information encryption table, and then displays the information of several information units in the two-dimensional information encryption table position, and / or the attribute value corresponding to at least one two-dimensional information in each information unit, obtain the two-dimensional information input by the user, and combine the two-dimensional information with the corresponding position and / or attribut...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com