Zernike moment based robust hashing image authentification method
A technology of image authentication and robust hashing, applied in instruments, character and pattern recognition, computer components, etc., can solve problems such as inapplicable images, unfeasible calculations, unpredictable information summaries, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
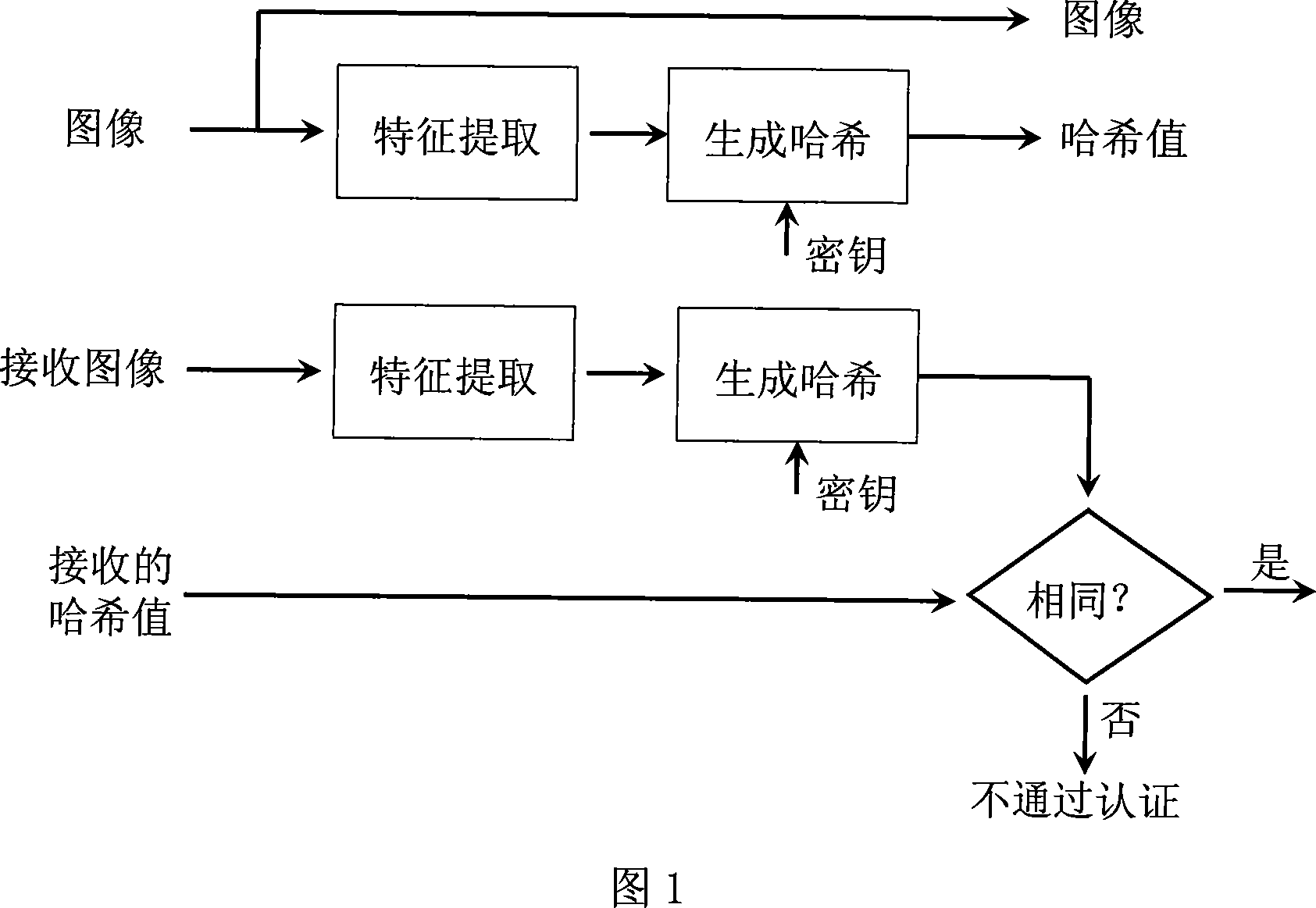
[0083] The method of the present invention will be further described below in conjunction with the accompanying drawings.
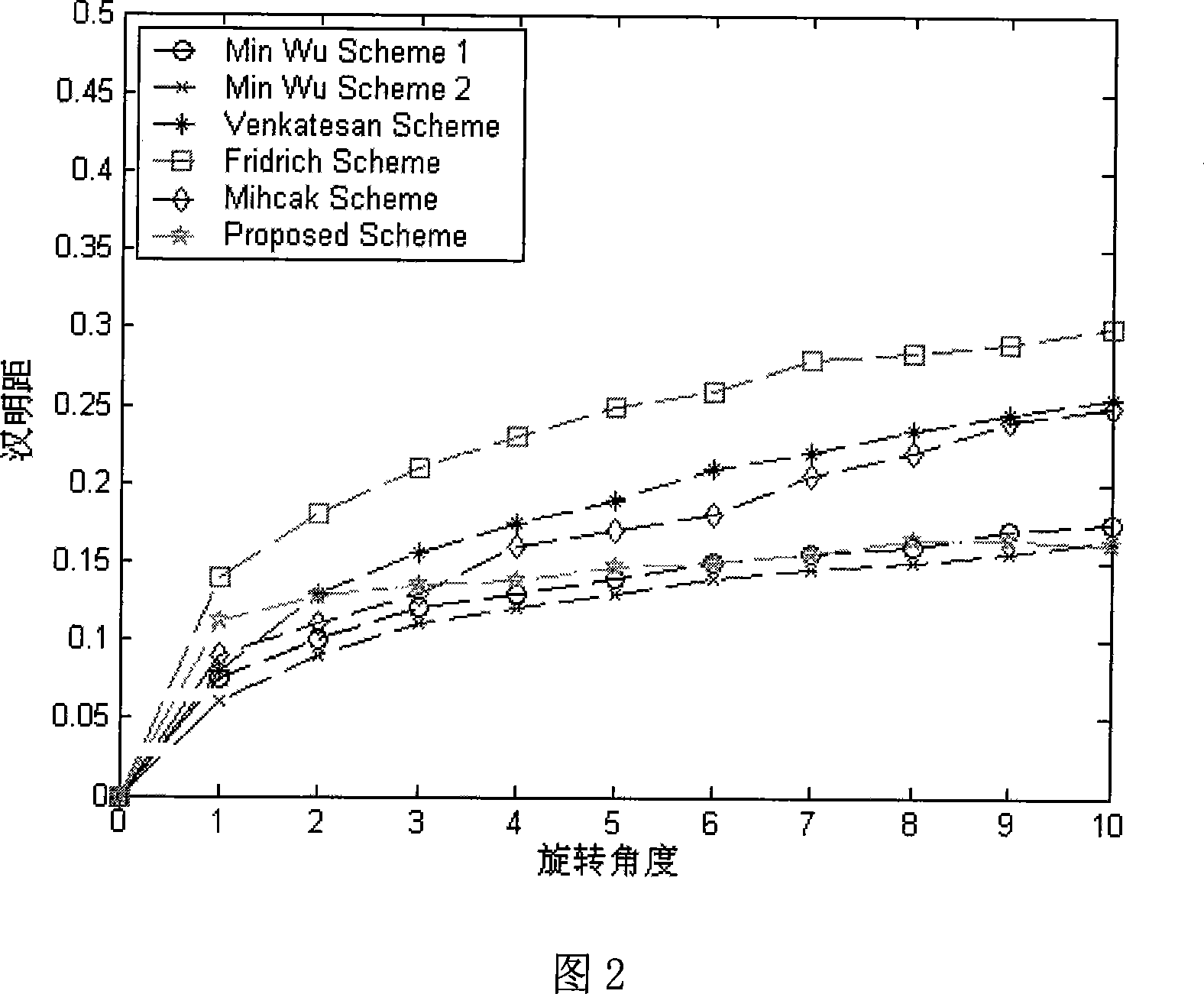
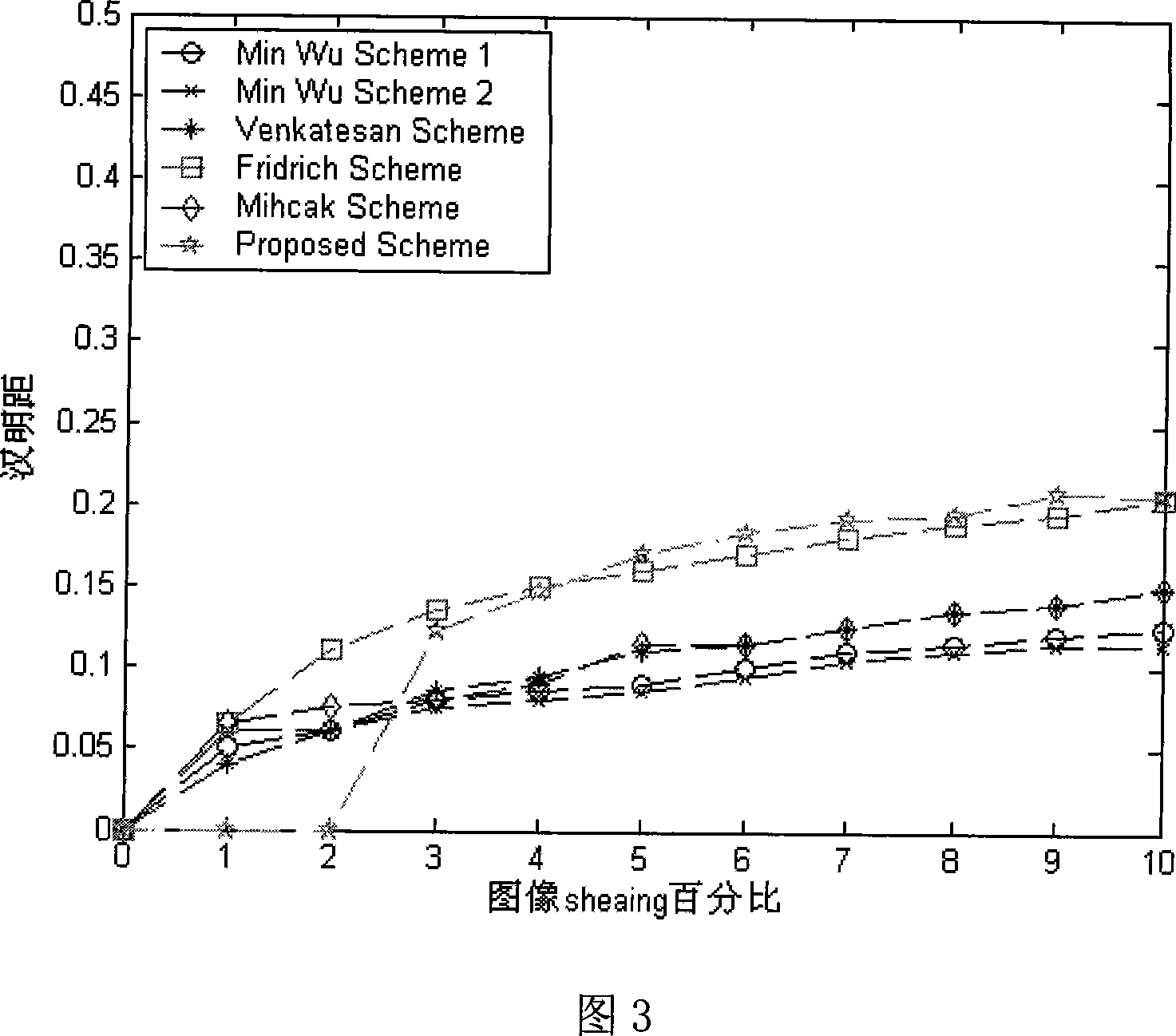
[0084] As shown in Figure 1, at first, before the image is transmitted or stored, the method of the present invention extracts the feature of the image (calculates the zernike moment of the image), then encrypts the zernike moment value to generate a hash sequence, as the basis for image authentication in the future . When image authentication is required, use the same method to extract the features of the image, encrypt and generate a hash sequence, compare the newly generated hash sequence with the original hash sequence stored or transmitted with the image, and calculate the Hamming distance between the two , if the Hamming distance between the two is lower than the set threshold, the image is considered to be authenticated, otherwise, the image is considered not to be authenticated.
[0085] The concrete steps of the inventive method are as follows: ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com