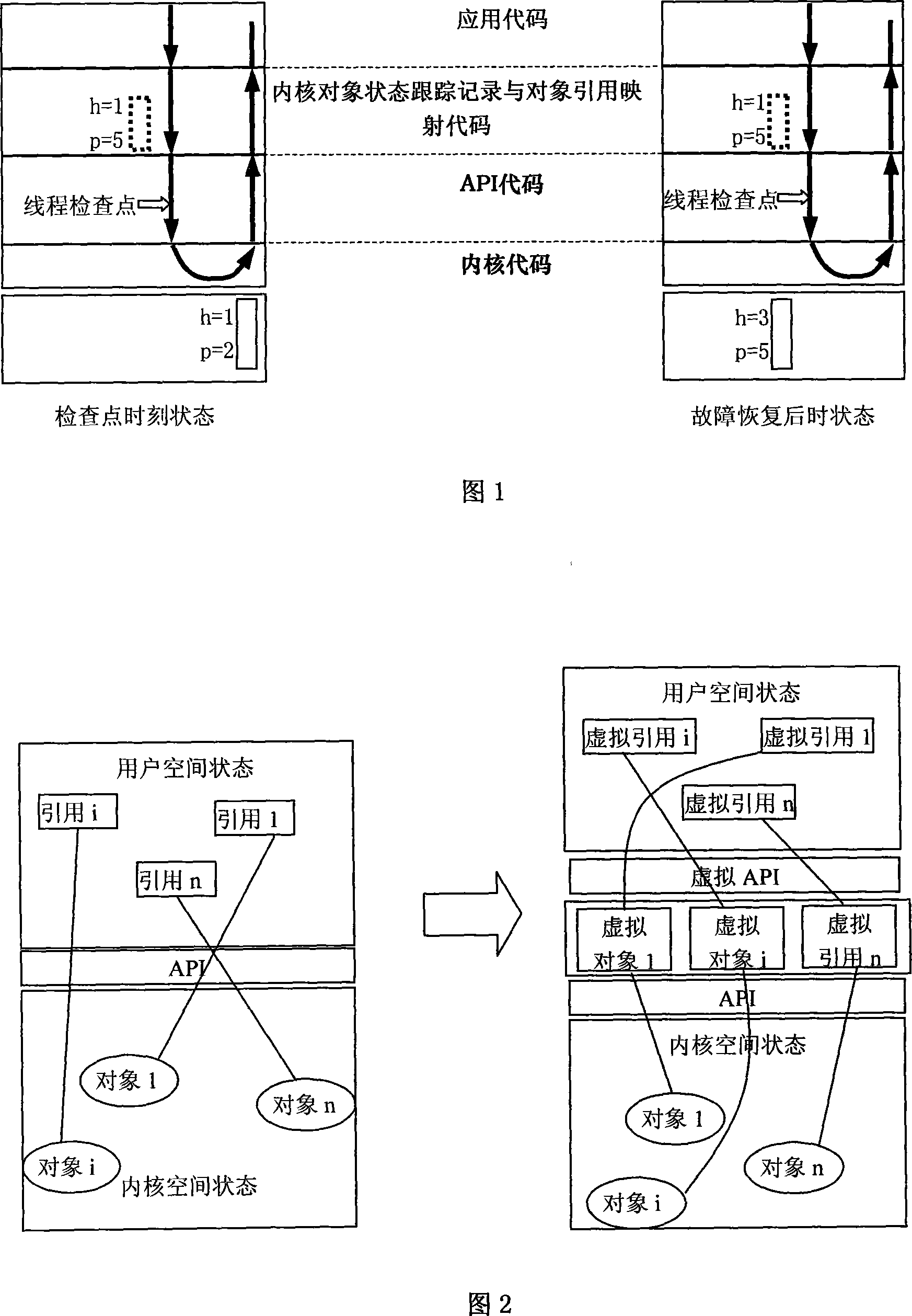
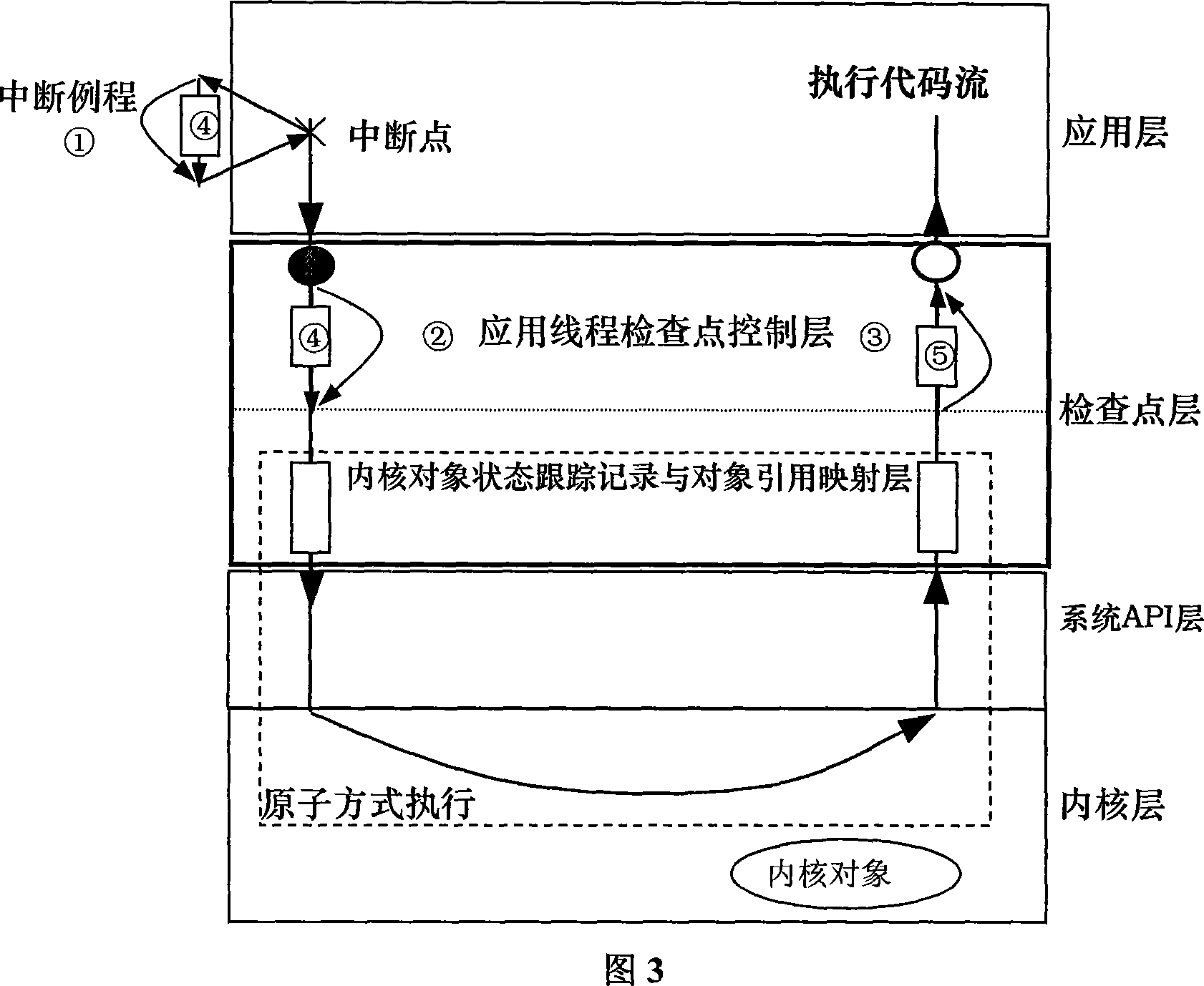
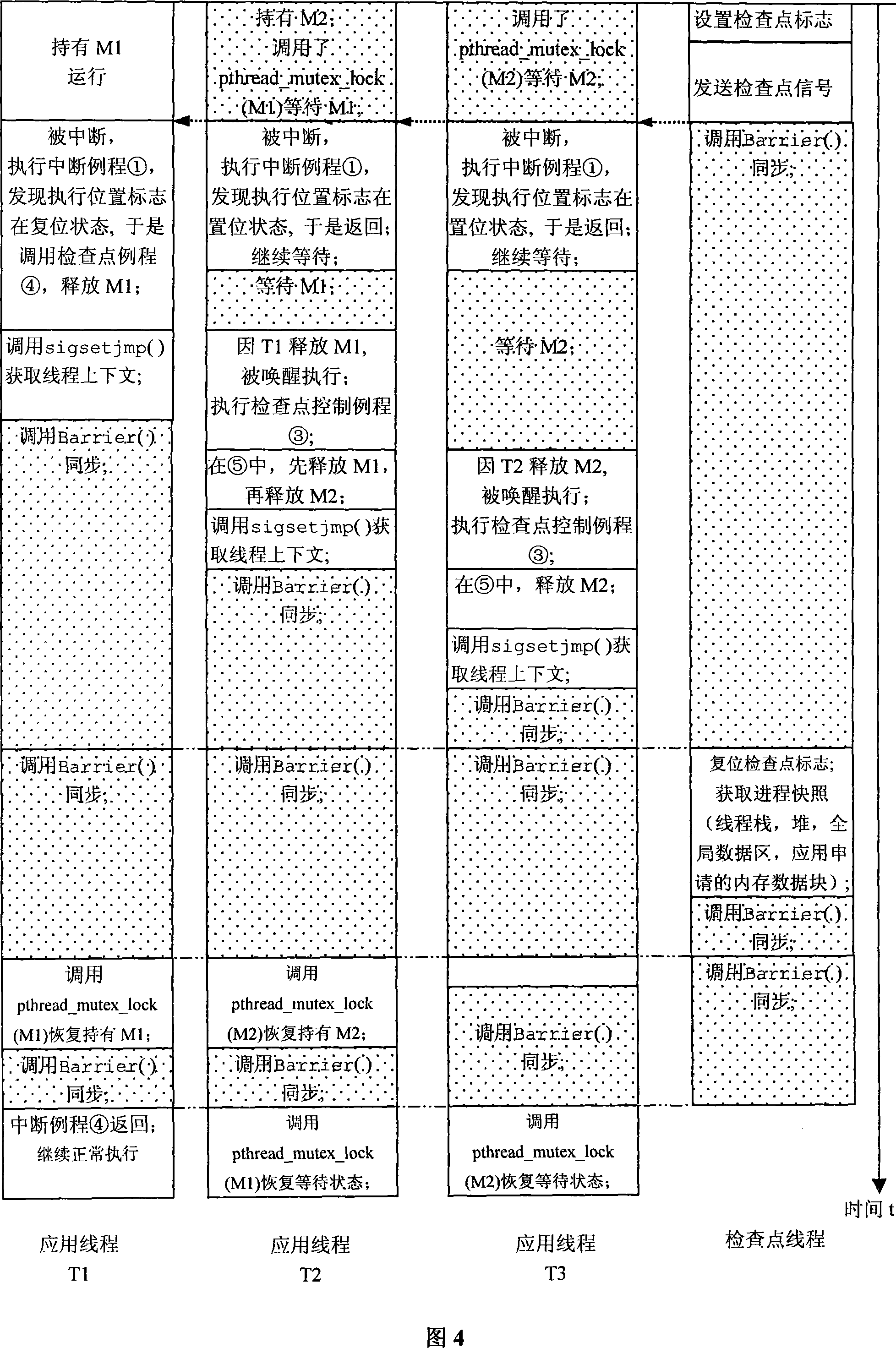
Method for implementing checkpoint of Linux program at user level based on virtual kernel object
A technology of kernel objects and implementation methods, applied in multi-programming devices, software testing/debugging, etc., can solve problems such as execution failure, inability to recover strictly and consistently, logic errors, etc., and achieve the effect of efficient software debugging
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] Refer to Figure 4. In this embodiment: at the time of the checkpoint, there are three threads in the process: T1, T2, T3, and there are two synchronization objects: mutexes M1, M2. Thread T1 holds M1 and is in the execution state; thread T2 holds M2, which calls the pthread_mutex_lock() system API, and is in the waiting state to further wait for M1; thread T3 calls the pthread_mutex_lock() system API and is in the waiting state, waiting for M2. At the checkpoint moment, the checkpoint thread sets the checkpoint flag, and calls signal() to send checkpoint interrupt signals to threads T1, T2, and T3. T1, T2, and T3 are interrupted and go to the checkpoint interrupt routine. In the checkpoint interrupt routine (see Figure 3①), T1 checks that the checkpoint flag is set and its own execution position flag is in the reset state, so it calls the checkpoint routine ④ (see Figure 3④). In the checkpoint routine ④, T1 releases M1, calls the sigsetjmp() system API to obtain the t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com