Harmless information deletion method and system
A deletion method and non-destructive technology, applied in the field of communication, can solve problems such as members cannot be deleted, state deadlock, strong network management dependence, etc., and achieve the effect of solving the problem of sink deletion and non-destructive business
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] The specific implementation manners of the present invention will be described in detail below with reference to the accompanying drawings.
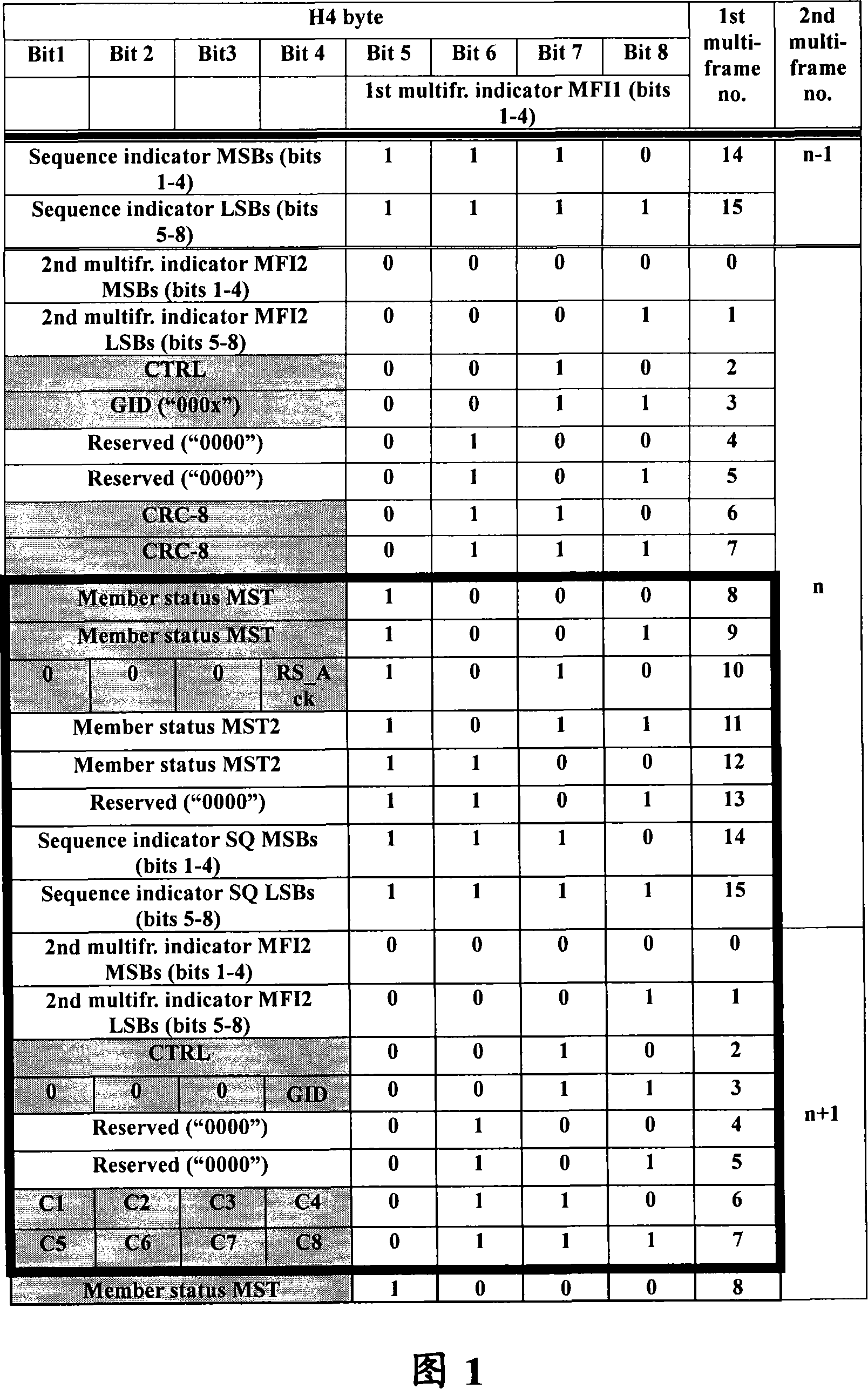
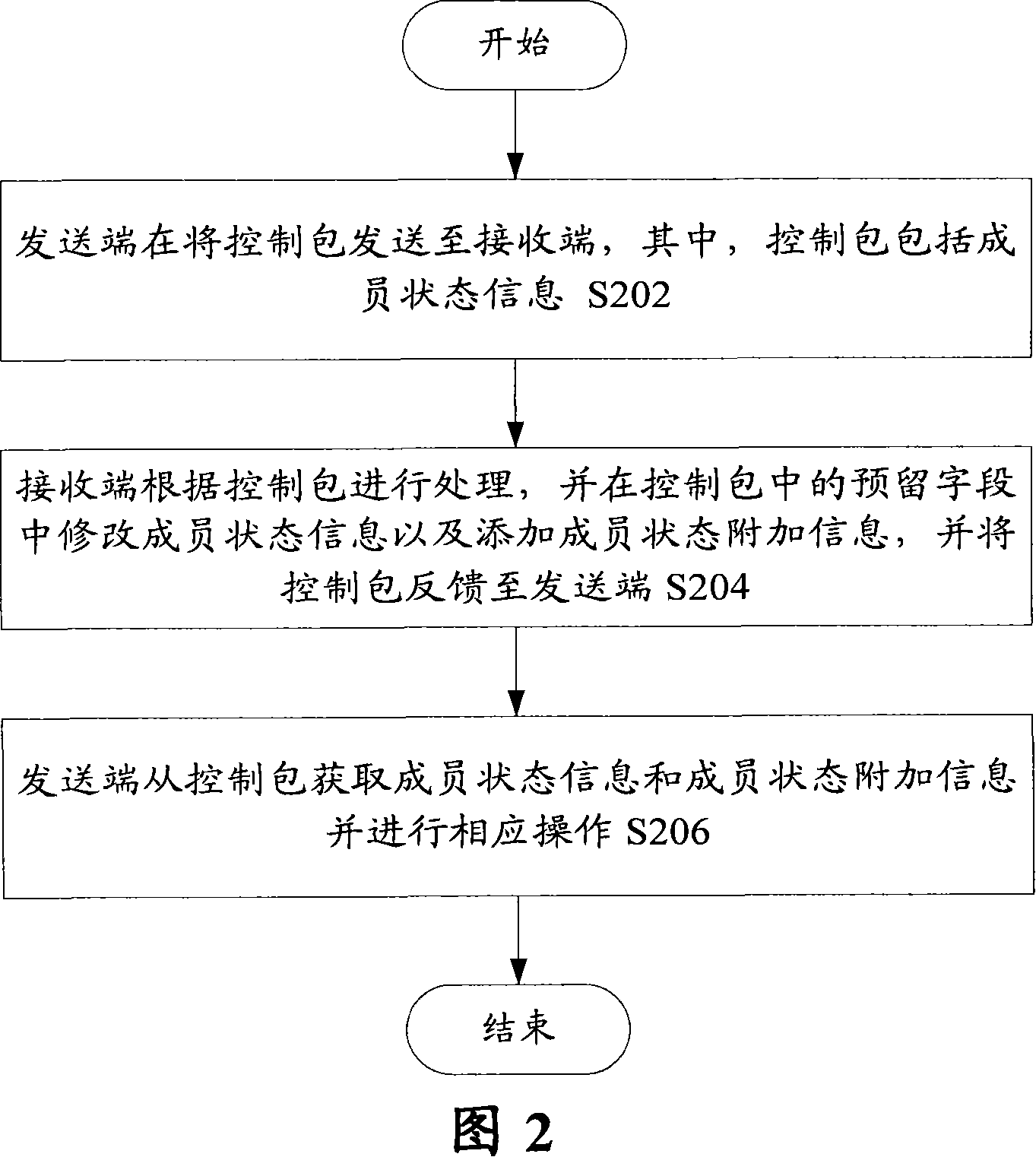
[0061] Referring to FIG. 2 , a method for deleting information without damage according to an embodiment of the present invention is illustrated. As shown in Figure 2, the method for deleting information without damage includes the following steps: S202, the sending end sends a control packet to the receiving end, wherein the control packet includes member state information; S204, the receiving end processes according to the control packet, and Modify member state information and add member state additional information in the reserved field in the control packet, and feed back the control packet to the sender; and S206, the sender obtains member state information and member state additional information from the control packet and performs corresponding operations.
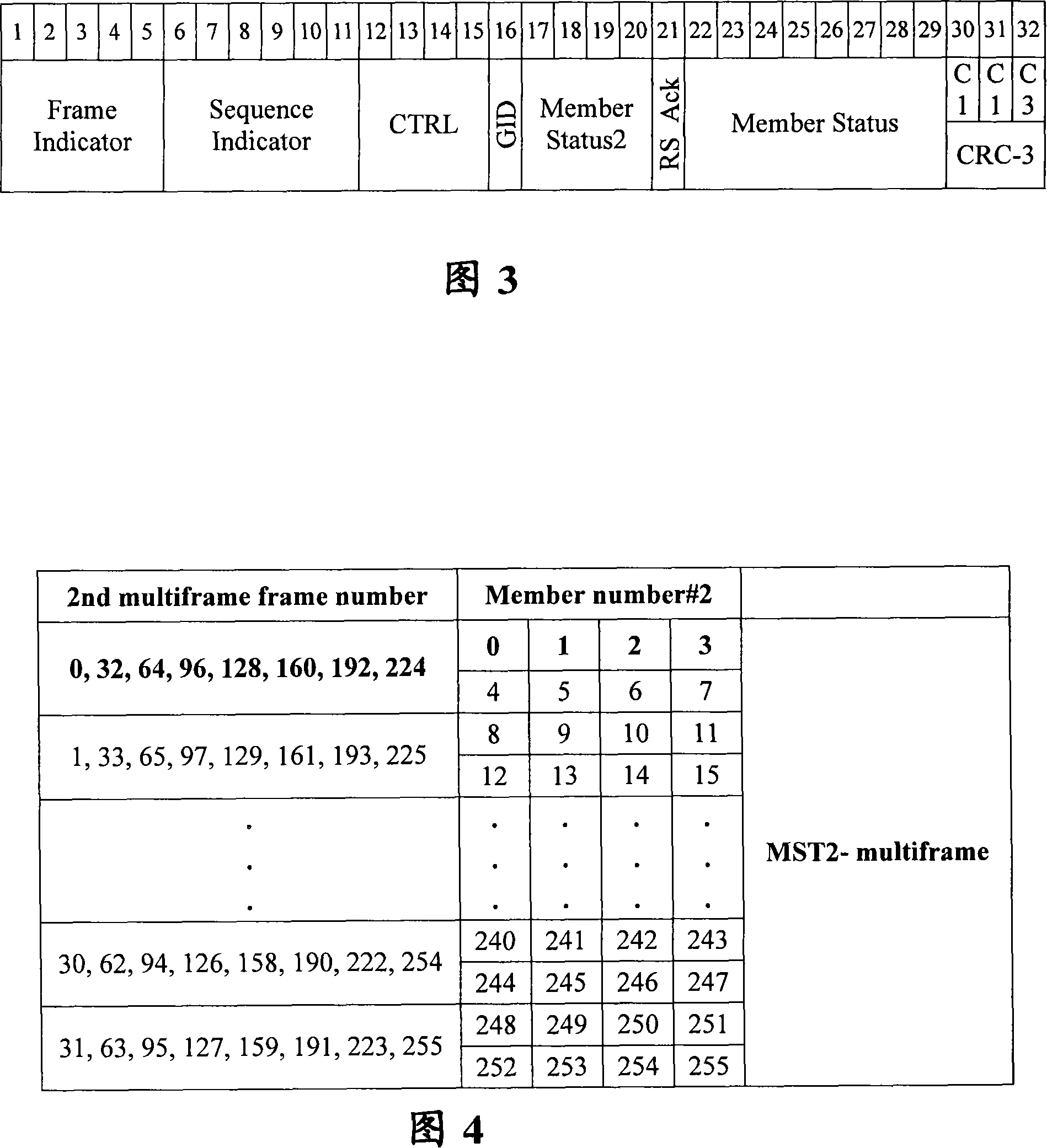
[0062] Wherein, the control packet further includes at least one ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com