Authority configuring method and apparatus
A permission configuration and permission technology, applied in the network field, can solve the problems of not being able to batch grant a group of user permissions, heavy workload of user permissions, and low authorization efficiency, so as to achieve seamless integration, facilitate configuration and management, and improve settings efficiency effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
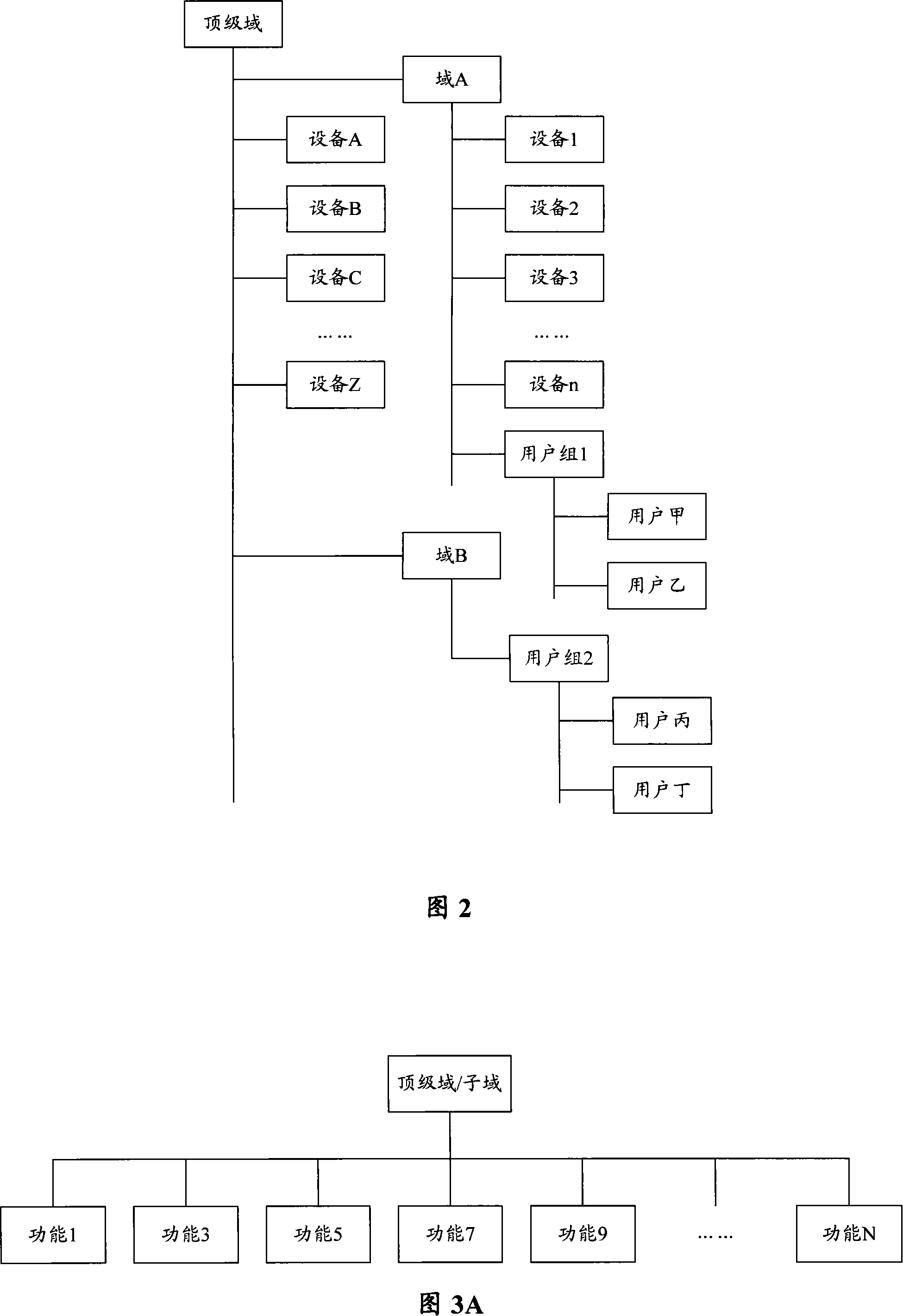
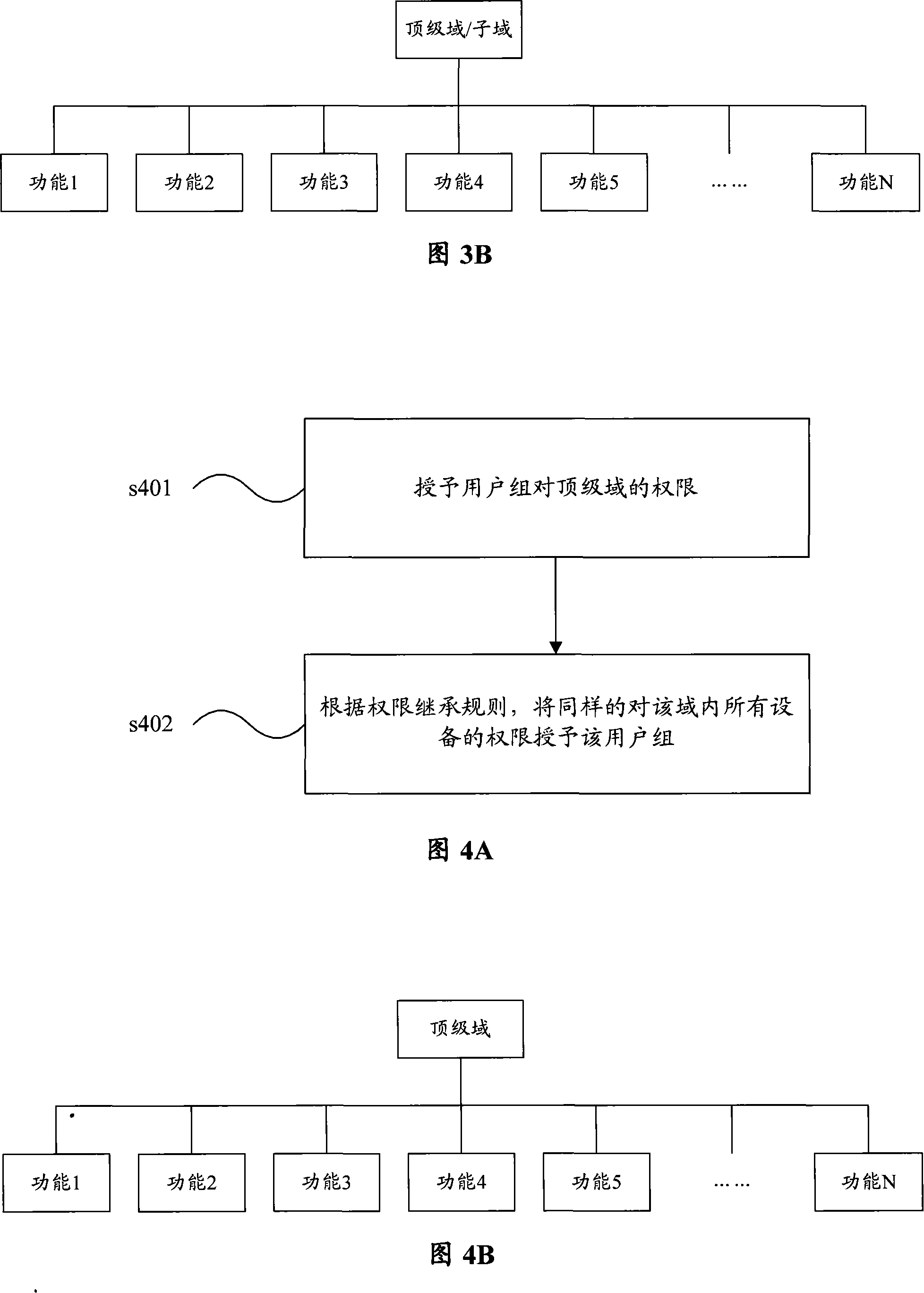
[0054] The core idea of a permission configuration method in the present invention is to establish a user group permission inheritance mechanism, grant the user group domain permissions and carry out permission inheritance, so that the user group has the permissions of all devices under this domain at the same time; Permissions, each user in the user group can inherit the permissions of the user group.
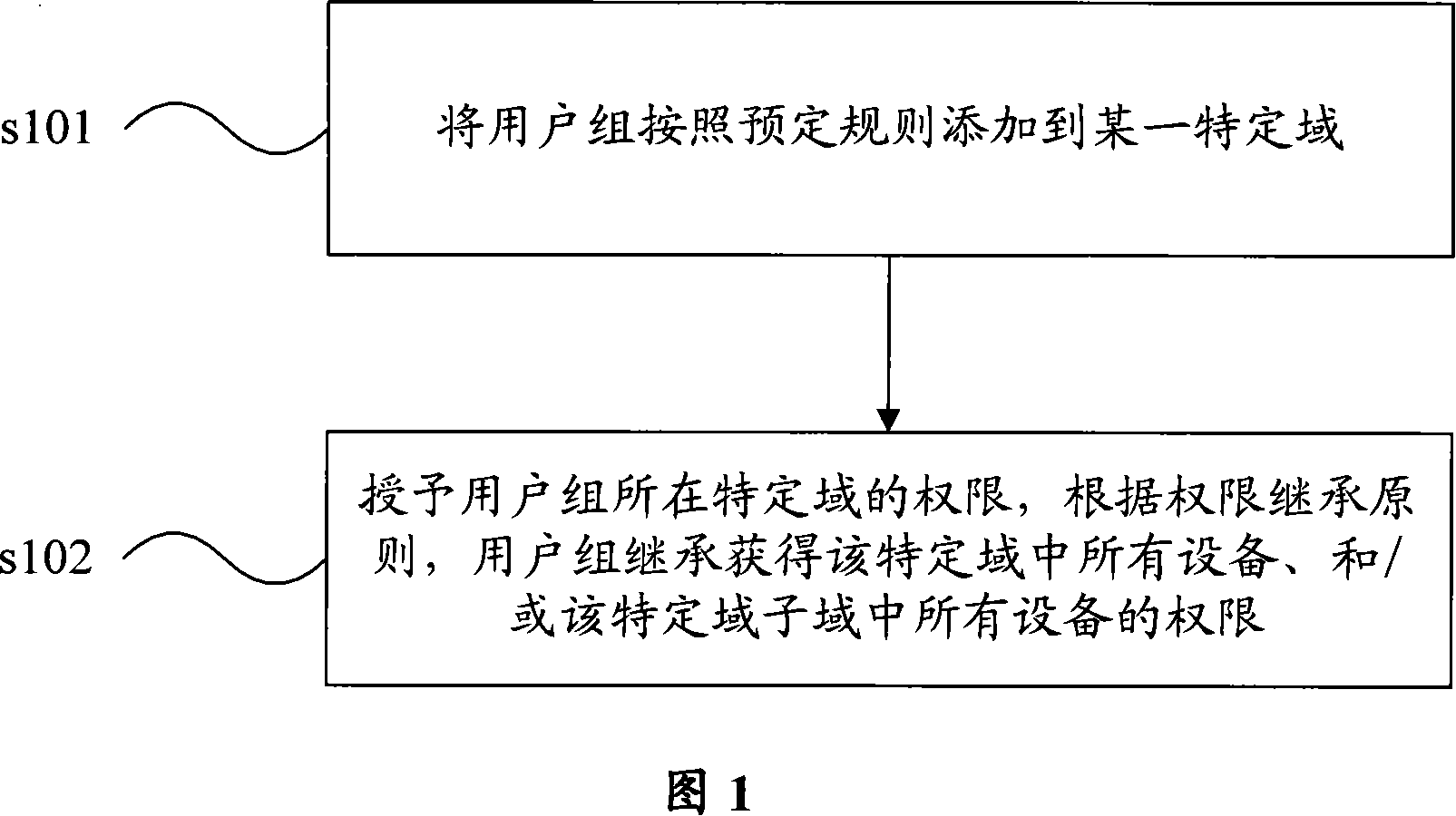
[0055] A permission configuration method among the present invention is shown in Figure 1, comprises the following steps:
[0056] Step s101, adding a user group to a specific domain according to predetermined rules.
[0057] Step s102 , granting the authority of the specific domain where the user group is located. According to the principle of authority inheritance, the user group inherits the authority of all devices in the specific domain and / or all devices in the subdomains of the specific domain.
[0058] The user group referred to here refers to a collection of specif...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com