Remote unlocking method and system
A remote unlocking and algorithm technology, applied in the field of information security, can solve problems such as time-consuming, troublesome, and economic loss of users, and achieve the effects of reducing trouble, improving security, and saving time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
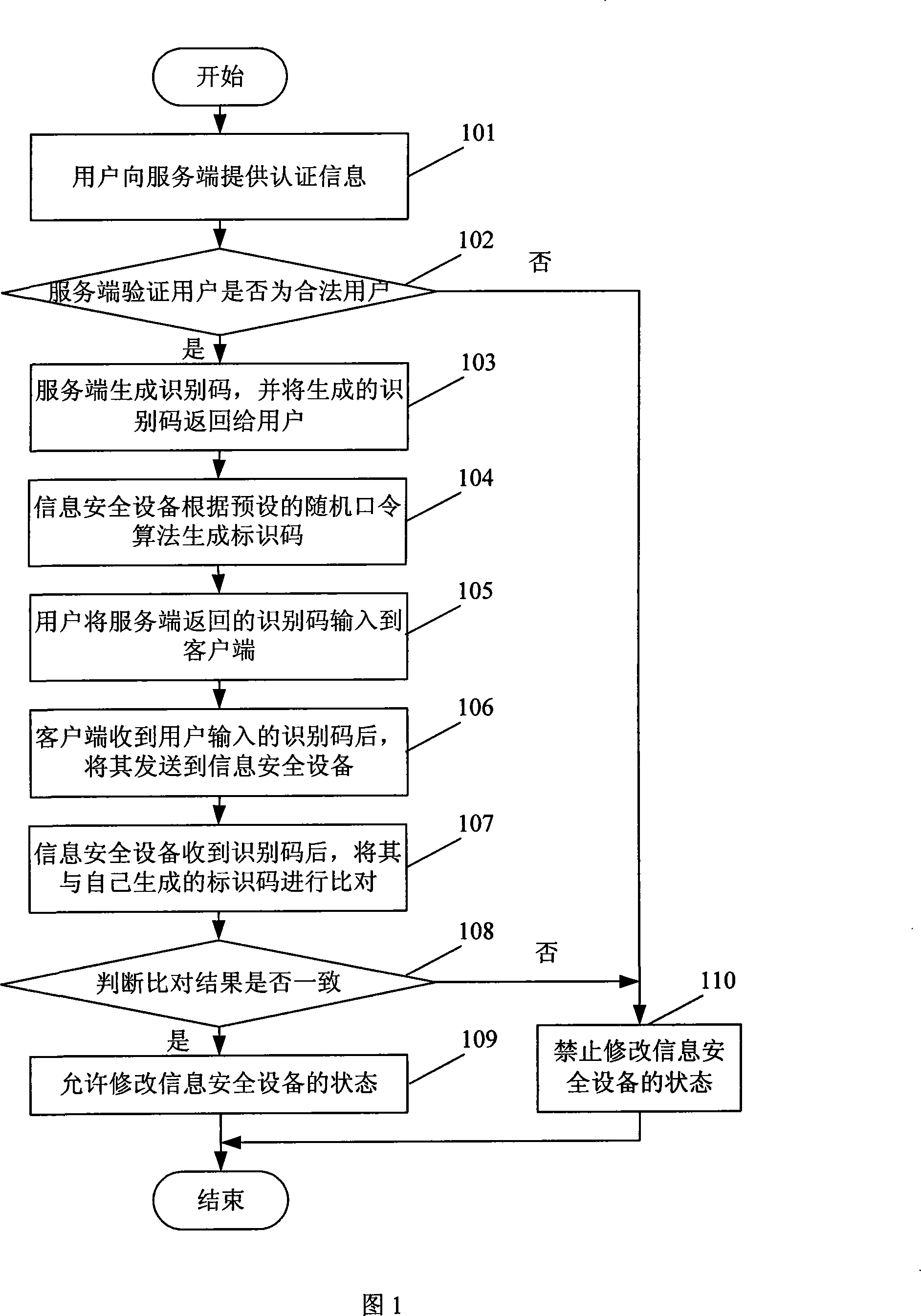
[0090] In this embodiment, the server and the information security device are preset with the same generation elements. Referring to FIG. 1, the embodiment of the present invention provides a remote unlocking method, which specifically includes the following steps:
[0091] Step 101: the user provides authentication information to the server.
[0092] When purchasing information security equipment, users are required to provide their own valid certificates, which will be stored in the server as authentication information for later unlocking. For example, if users provide their own ID cards when purchasing information security equipment, then Its ID number will be stored in the server.
[0093] The authentication information provided by the user may also include the hardware identifier of the information security device. After receiving the authentication information, the server can find the random password algorithm corresponding to the information security device according to...
Embodiment 2
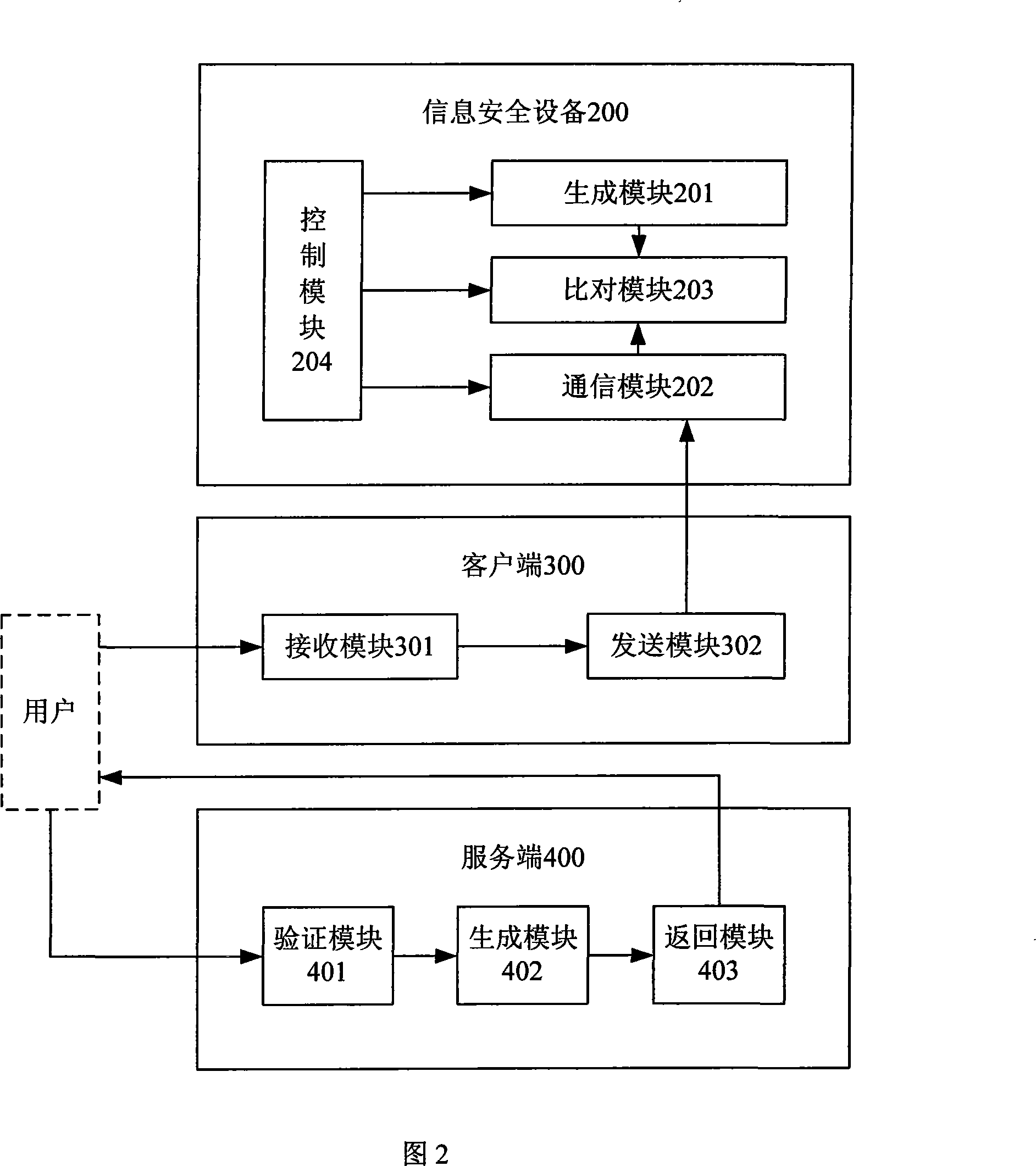
[0124] Referring to FIG. 2 , an embodiment of the present invention provides a remote unlocking system, including an information security device 200, a client 300 and a server 400,
[0125] The information security device 200 includes a generation module 201, a communication module 202, a comparison module 203 and a control module 204:
[0126] The generating module 201 is used to generate an identification code according to a preset random password algorithm under the control of the control module 204, and send the identification code to the comparison module 203;
[0127] The communication module 202 is used to receive the identification code input by the user through the client terminal 300 under the control of the control module 204, and send the received identification code to the comparison module 203;
[0128] The comparison module 203 is used to compare whether the identification code sent by the communication module 202 is consistent with the identification code sent ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com