Terminal access trusted PDA method and access system
A terminal access and access system technology, applied in the direction of instruments, calculations, electrical digital data processing, etc., can solve the problems of PDA private information and key data leakage, unreliable terminal operating environment, PDA privacy data leakage, etc., to prevent Effects of identity forgery, theft prevention, and tamper prevention
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
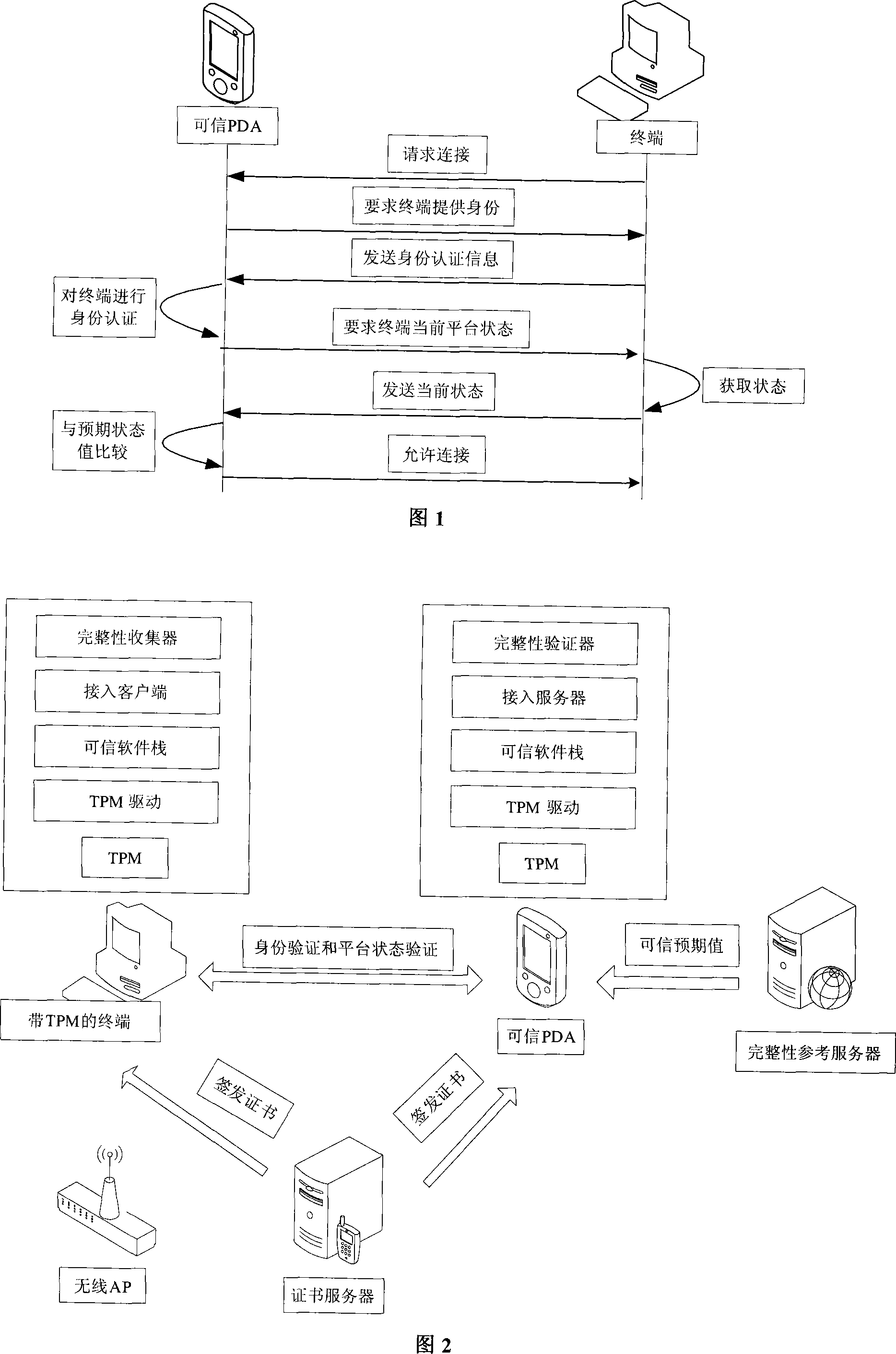
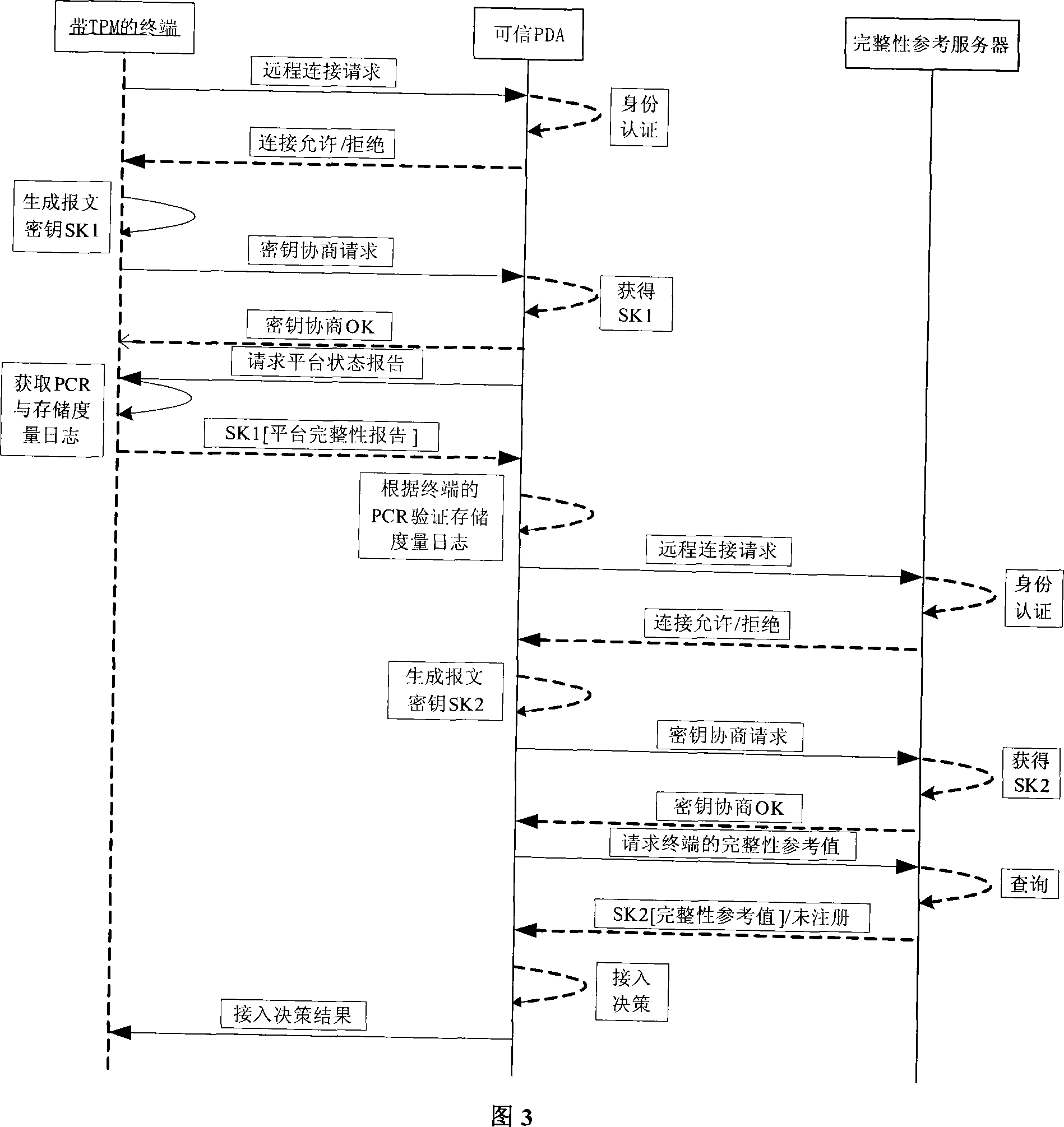
[0019] The method for a terminal accessing a trusted PDA provided by the present invention is specifically: before the terminal accesses the trusted PDA, at first the identity of the terminal is authenticated to ensure that only a specific terminal can be connected to the trusted PDA; After passing, the terminal is required to report its current platform status to the trusted PDA. The trusted PDA compares and verifies the platform status of the terminal with the pre-saved platform trusted status value of the terminal. If it conforms to the trusted PDA platform status access If required, the terminal is allowed to establish a connection with the trusted PDA. The access and connection here refer to the protocol connection based on the physical connection between the terminal and the trusted PDA.
[0020] The present invention provides an access system capable of realizing the above-mentioned method for a terminal to access a trusted PDA, which enables a terminal to access a trust...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com