Method and apparatus for improving information input safety
A technology of information input and security, applied in the field of information security, can solve problems such as economic loss of users, damage to legal user rights and weaknesses, etc., and achieve the effect of improving information security and information input security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
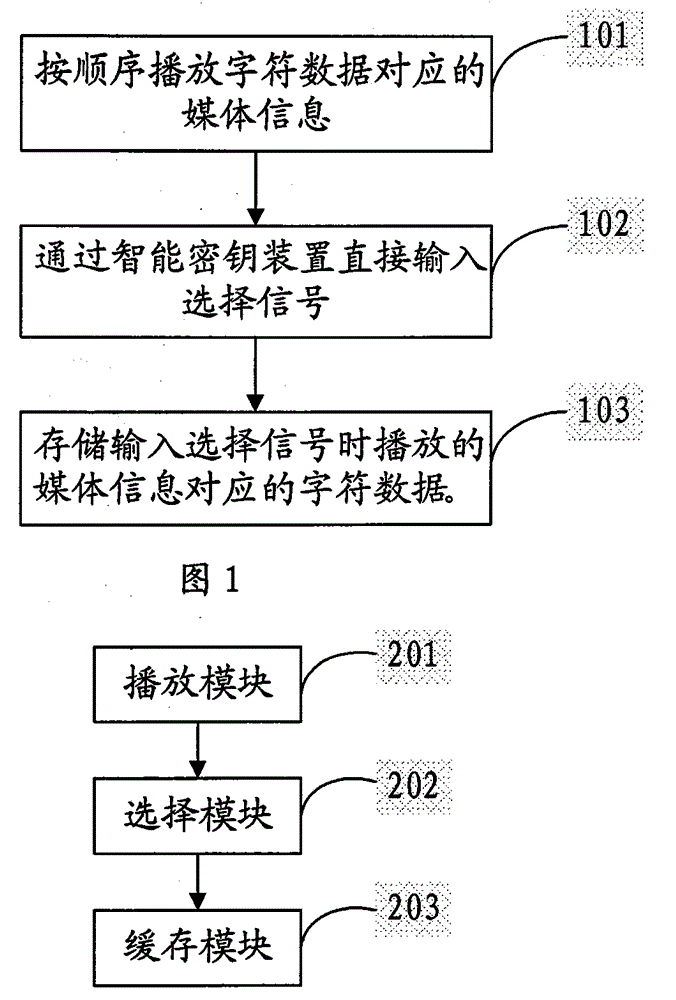
[0024] This embodiment discloses an input method for improving the security of information input. When the user inputs authentication information to the smart key device, as shown in FIG. 1, the method includes:
[0025] 101. When authentication information needs to be input to the smart key device, generally after the smart key device establishes a connection with the terminal, the smart key device plays the media information corresponding to each character in sequence. The played media information includes authentication information for user identification.
[0026] 102. The authentication information is generally a string of character data. During the playback of media information, when the character data corresponding to the played media information is the same as the character data in the authentication information and the order in the authentication information is also the same, the smart key The device inputs a selection signal to select the media information.
[0027]...
Embodiment 2
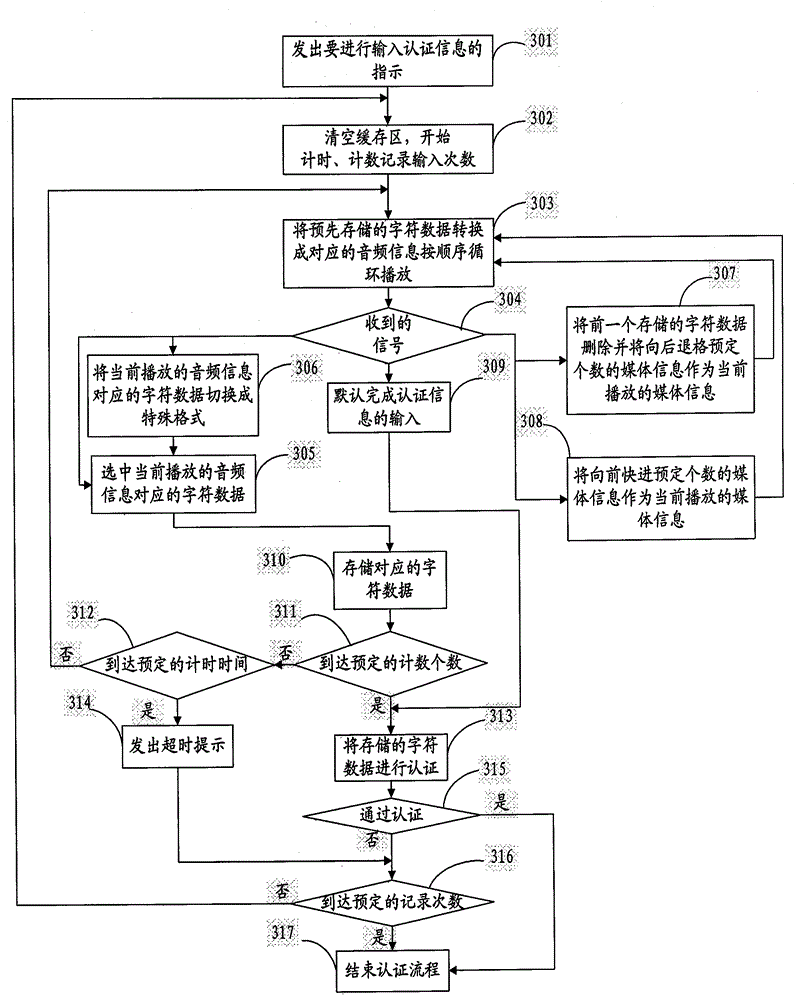
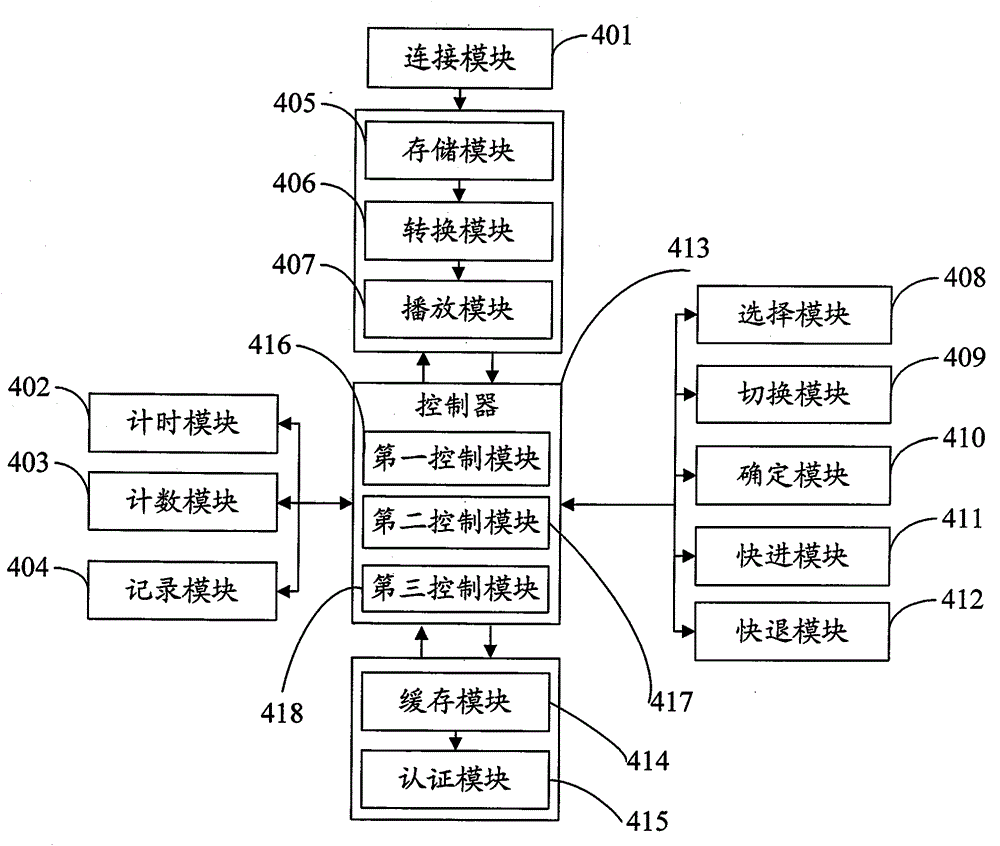
[0032] This embodiment specifically describes the method for improving the security of information input when the user inputs authentication information to the smart key device, such as image 3 As shown, the method includes the following steps:
[0033] 301. Step 302 is executed when the smart key device receives an instruction requiring identity authentication, generally after the smart key device establishes a connection with the terminal.
[0034] The connection to the terminal can be established through a USB interface to connect to the terminal, or through an extended serial advanced technology attachment (eSATA) interface, an extended secure digital (SDIO) interface, or the definition of the Personal Computer Memory Card International Association (PCMCIA) PCMCIA interface, etc.
[0035] 302. The smart key device clears the buffer area used to store the authentication information input by the user, and starts counting the number of character data of the input authentica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com