Method and system for on-line distributing authentication information
A technology of authorization information and signature information, which is applied in transmission systems, wireless communications, and broadcast-related systems. It can solve problems such as heavy computing loads, limited computing resources, and decryption of ciphertexts, so as to reduce computing loads, reduce costs, and ensure security. sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
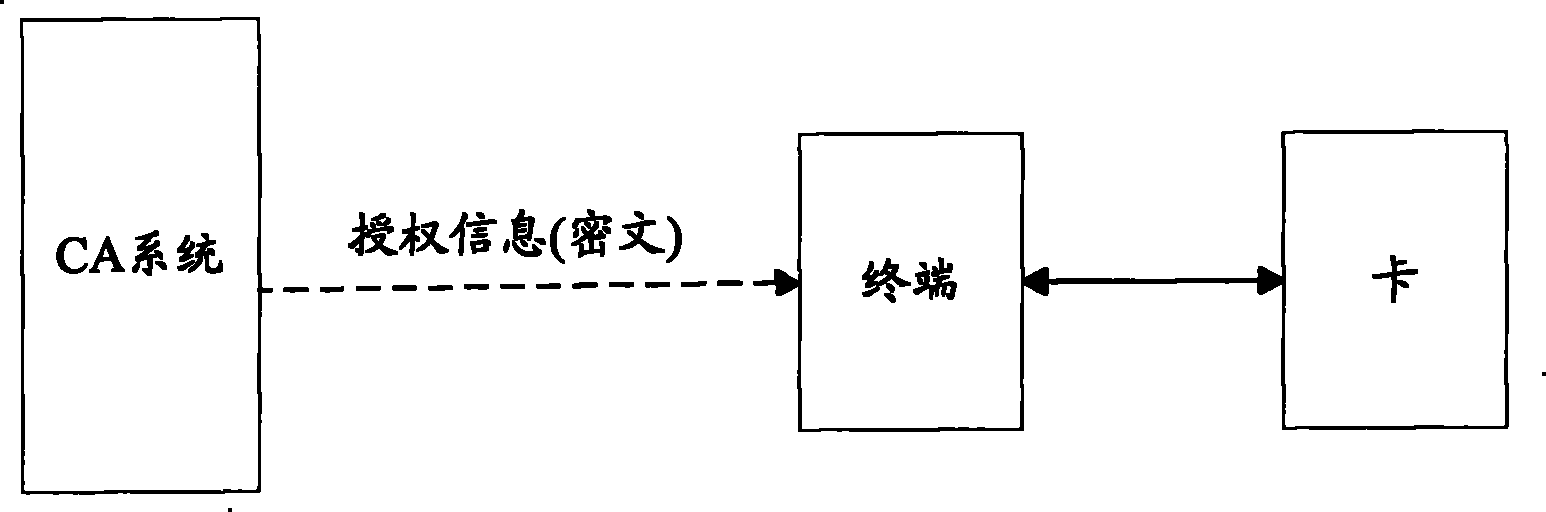
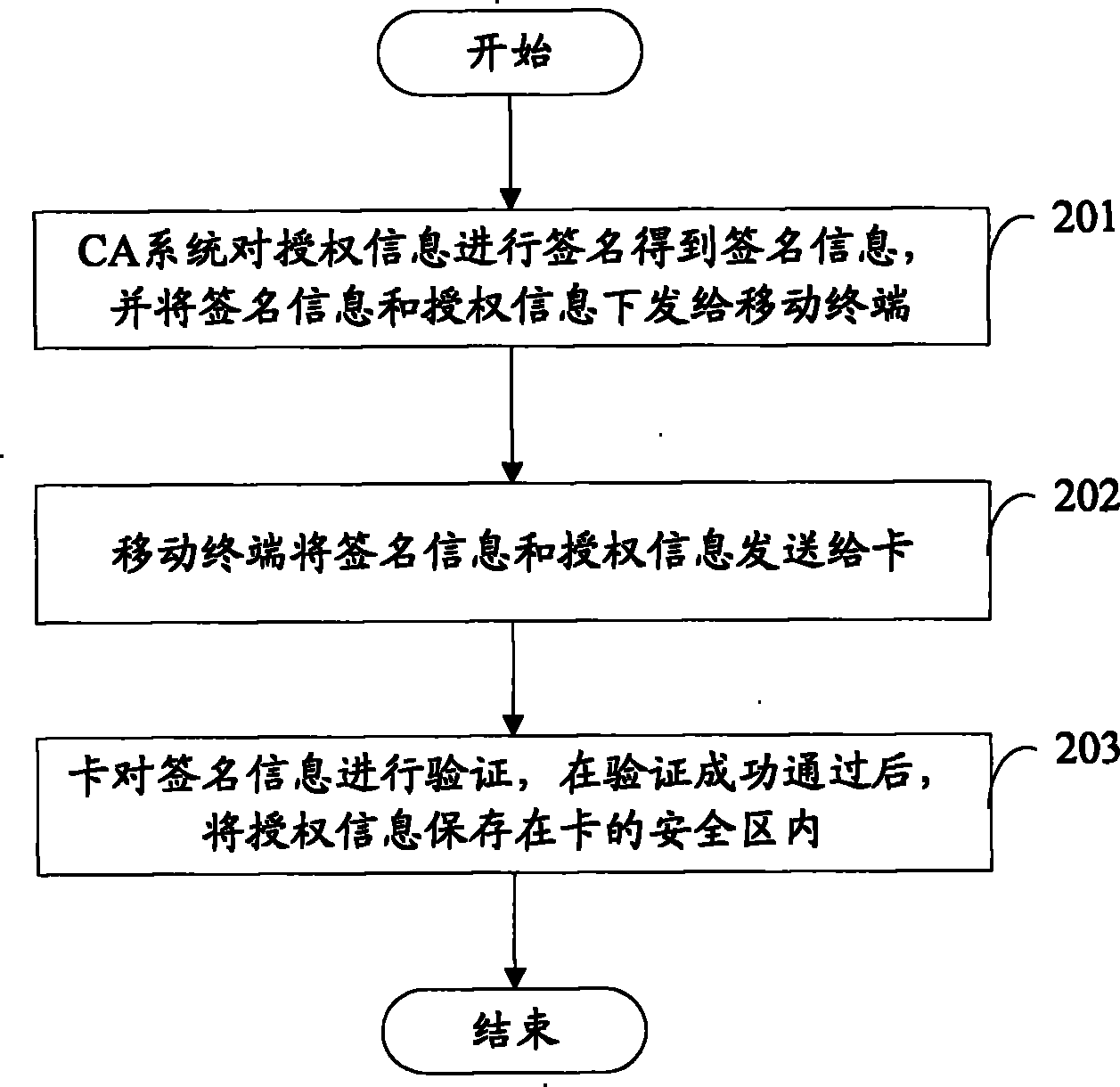
[0072] The operator has a pair of keys: a public key and a private key. The operator stores the public key in the smart memory card and sends it to legitimate users. The operator uses its own private key to sign the authorization information, and sends it to the user's mobile terminal through the broadcast channel, and the mobile terminal sends the signed authorization information to the smart memory card. The smart memory card uses the internally stored public key to verify the integrity of the signature authorization information. If the authentication is passed, the authorization information is considered safe and complete, and the authorization information can be written into the card; if the authentication fails, the information will not be verified. deal with,.
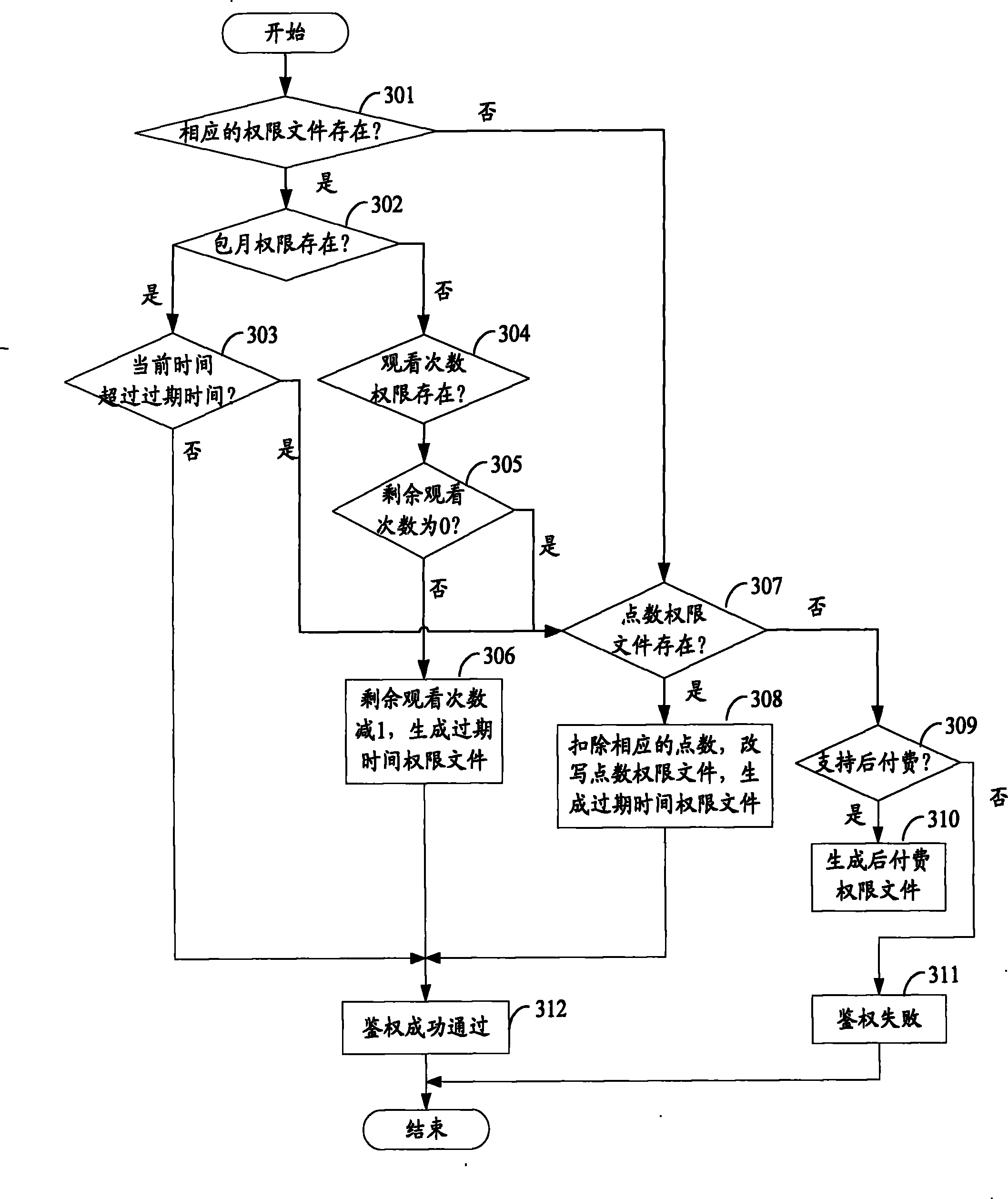
[0073] On the basis of the above technical solution, in order to realize charging, a service authentication process can be introduced. Specifically, after the smart memory card receives the conditional access in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com