Method, system and equipment for controlling user networking
A user and device technology, applied in the field of network security, can solve the problems of low security, illegal users cannot pass identity verification, and cannot prevent the theft of internal network IP addresses, etc., to achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
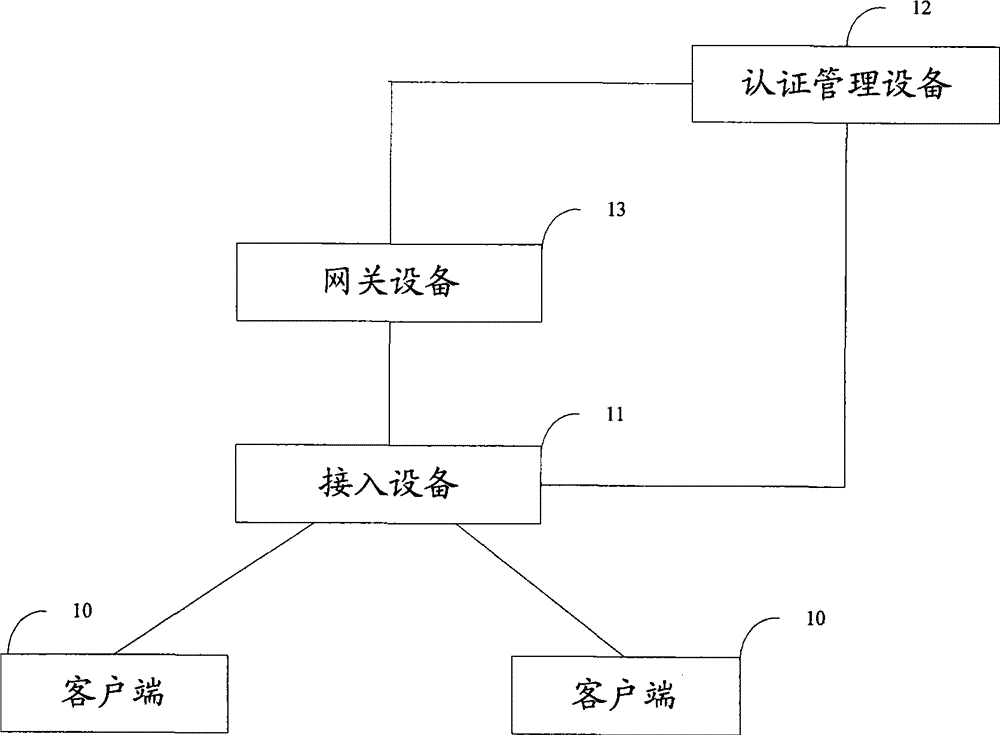
[0094] The specific system architecture in this embodiment is as Figure 7A As shown, it includes a gateway device accessing the network, a switch device accessing the gateway device, a client accessing the switch device, and an authentication management device located anywhere on the network. The switch device controls all connected clients, and all clients must pass the address authentication of the authentication management device before they can access the network. The specific process of the client accessing the network is as follows:
[0095] Step 701: After the user configures an IP address on the client terminal and enters authentication password information, the client sends an authentication request including the IP address, the client MAC address and authentication password information to the switch device;
[0096] Step 702: The switch device receives the authentication request, and sends the authentication request to the authentication management device;
[0097...
Embodiment 2
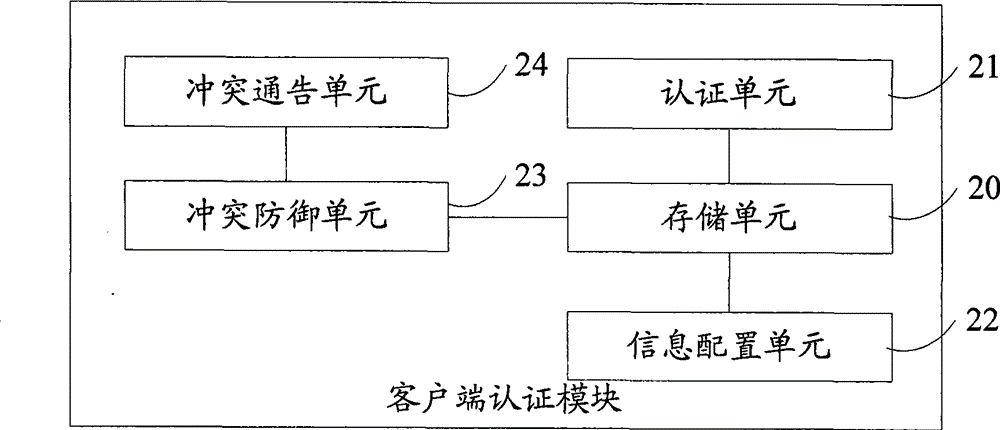
[0100] The specific system architecture in this embodiment is as Figure 7B As shown, it includes a gateway device connected to the network, a switch device connected to the gateway device, a client connected to the switch device, other hubs or non-network management switches connected to the switch device, and authentication management devices located anywhere on the network. The switch device controls all connected clients, and all clients must pass the address authentication of the authentication management device before they can access the network. Clients are also connected to other HUBs or non-network management switches. In this way, there may be IP conflicts caused by illegal users stealing IP addresses. In order to avoid such IP conflicts, the clients have the function of filtering ARP packets. The specific process of the client accessing the network is as follows:
[0101] Step 711: After the illegal user configures the stolen IP address A on client 1 and enters wro...
Embodiment 3
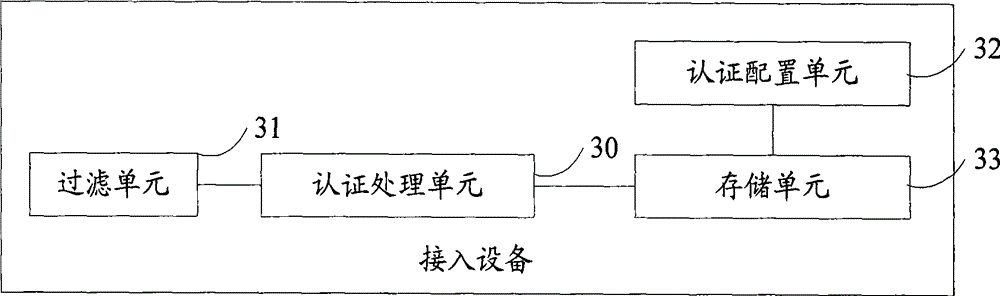
[0108] The specific system architecture in this embodiment is as Figure 7C As shown, it includes the gateway device accessing the network, the switch device accessing the gateway device, the client accessing the switch device, other HUBs accessing the gateway device or switches not of the present invention, etc., and the authentication management device located anywhere in the network . The switch device controls all connected clients, and all clients must pass the address authentication of the authentication management device before they can access the network. Clients are also connected under other HUBs or non-invention switches. This method may cause IP conflicts caused by illegal users' stolen IP addresses to access the Internet and cause adverse effects on legitimate users (such as intermittent messages). In order to avoid this As a bad effect, the authentication management device has the function of setting the static ARP information of the authenticated client on the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com